Chapter 19 Security Integrity Security Control computerbased noncomputerbased

Chapter 19 Security • Integrity • Security • Control – computer-based – non-computer-based • • PC security DBMS and Web security Risk Analysis Data protection and privacy laws

Integrity • Definition – Consistent with constraints • Types – Entity – Referential or existence – Domain – Enterprise

Security • Threats – Theft & fraud – Loss of confidentiality – Loss of privacy – Loss of integrity – Loss of availability
Countermeasures • Computer-based controls • Non-computer-based controls

Computer-based Controls - 1 • Authorization & authentication – Password – Account number – Relations, users & right (CRUD) table • Subschema – Create views

Computer-based Controls - 2 • Logs – Transaction logs – Violation logs (time, terminal, violation) • Check points • Backup (redundant array of independent disks - RAID) & recovery • Audit

Computer-based Controls - 3 • Encryption or cryptosystem – Encryption key – Encryption algorithm – Decryption key – Decryption algorithm – Symmetric encryption (Data Encryption Standard (DES) – Asymmetric encryption (RSA)

Example of Encryption - I • Divide text into groups of 8 characters. Pad with blank at end as necessary • Select an 8 -characters key • Rearrange text by interchanging adjacent characters • Translate each character into an ordinal number with blank as 0, A as 1, B as 2… • Add the ordinal number of the key to the results • Divide the total by 27 and retain the remainder • Translate the remainder back into a character to yield the cipher text
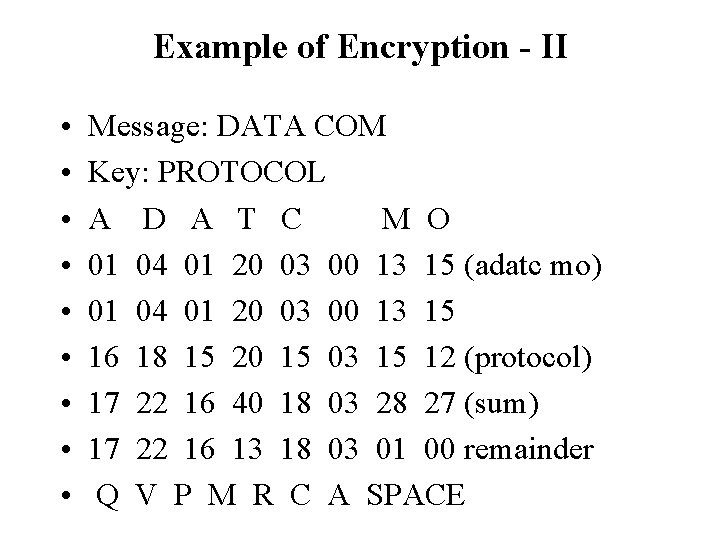
Example of Encryption - II • • • Message: DATA COM Key: PROTOCOL A D A T C M O 01 04 01 20 03 00 13 15 (adatc mo) 01 04 01 20 03 00 13 15 16 18 15 20 15 03 15 12 (protocol) 17 22 16 40 18 03 28 27 (sum) 17 22 16 13 18 03 01 00 remainder Q V P M R C A SPACE

Example of Decryption - I • Divide cipher text into groups of eight characters. Pad with blanks at end as necessary • Translate each cipher text alphabetic character and the encryption key into an ordinal number • For each group, subtract the ordinal number of the key value from the ordinal number of the cipher text • Add 27 to any negative number • Translate the number back to alphabetic equivalents • Rearrange the text by interchanging adjacent characters
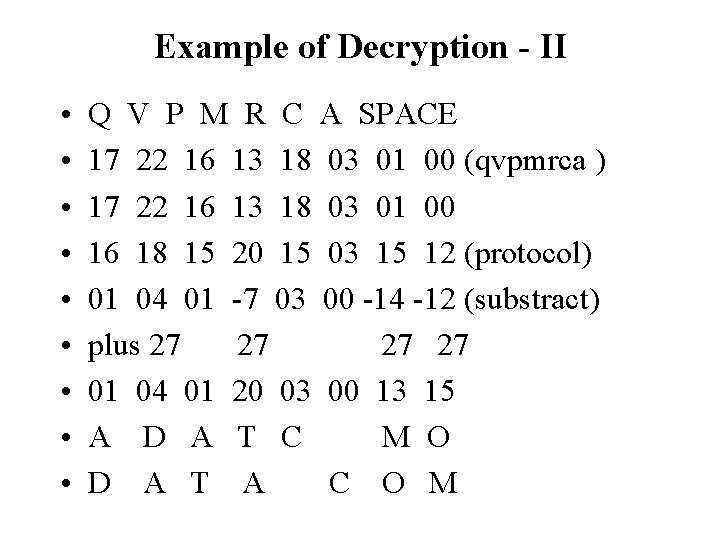
Example of Decryption - II • • • Q V P M R C A SPACE 17 22 16 13 18 03 01 00 (qvpmrca ) 17 22 16 13 18 03 01 00 16 18 15 20 15 03 15 12 (protocol) 01 04 01 -7 03 00 -14 -12 (substract) plus 27 27 01 04 01 20 03 00 13 15 A D A T C M O D A T A C O M

Non-Computer-based Controls • Security policy • Contingency plan – Person, phone no. , procedures – Site (cold, warm, or hot) • Personnel control – – Reference Termination Training Balance of duty • Escrow & maintenance agreements • Physical

PC Security • • Policy & procedure Physical Logical Virus
DBMS and Web Security • Proxy server: performance & filtering • Firewall: packet filter, application gateway, circuit level gateway, & proxy server • Digital signatures & Certificate Authority (CA) • Message digest algorithms and digital signature • Kerberos: centralized security server (certificate server • Secure Sockets Layer (SSL) for data & Secure HTTP for individual message • Secure Electronic Transaction (SET) for credit card & Secure Transaction Technology (STT) for bank payment

Risk Analysis • • • Assets Threats and risks Countermeasures Cost/benefit analysis Testing

Data Protection & Privacy Law

Assignment • Review chapters 5 -6, 11 -13, and 18 • Read chapter 19 • Exam 3 – Date: 12/9/04 • Project – Normalization and Corrected EER diagram due date: 12/2/04 – SQL, corrected normalization, and EER diagram due date: 12/15/04 (MIS Department Office)
- Slides: 17