Chapter 18 IP Security IPSec Virtual Private Network
- Slides: 20

Chapter 18 IP Security (IPSec) Virtual Private Network (VPN) CNLab/University of Ulsan 1

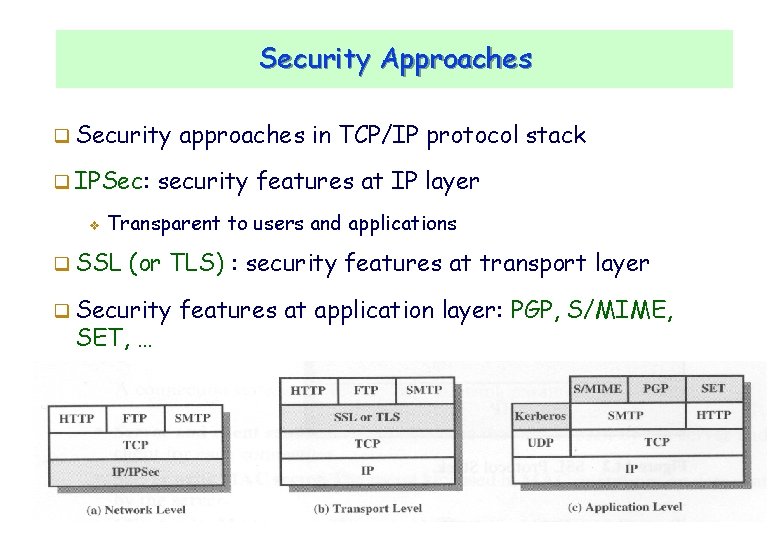
Security Approaches Security IPSec: v approaches in TCP/IP protocol stack security features at IP layer Transparent to users and applications SSL (or TLS) : security features at transport layer Security SET, … features at application layer: PGP, S/MIME, CNLab/University of Ulsan 2

IP Security Overview IP security (IPSec) v RFC 1636, 1994 : An implementation of IP-layer security v Confidentiality service v Authentication service v Key management Application of IPSec v VPN over Internet v Secure remote access over Internet v Enhancing e-Commerce security v Secure routing info exchange among routers CNLab/University of Ulsan 3

IPSec (IP Security) IPSec protocols v IP Authentication Header (AH) v IP Encapsulating Security Payload (ESP) v Internet Key Exchange (IKE) CNLab/University of Ulsan 4

IPSec (IP Security) ESP and AH assume the peers using the protocol have a shared key -> needs a protocol for distributing keys called Internet Key Exchange (IKE). IPSec was designed as two protocols to encourage wide deployment, even where there are import, export, and usage restrictions on encryption. CNLab/University of Ulsan 5

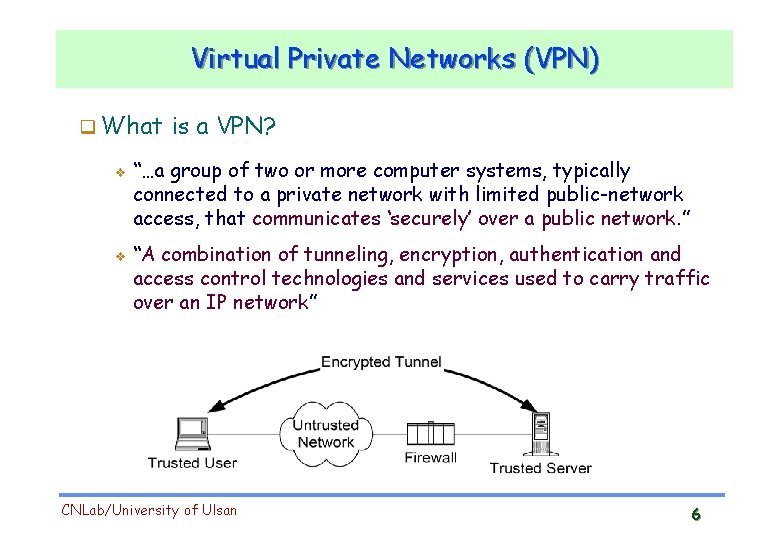
Virtual Private Networks (VPN) What v v is a VPN? “…a group of two or more computer systems, typically connected to a private network with limited public-network access, that communicates ‘securely’ over a public network. ” “A combination of tunneling, encryption, authentication and access control technologies and services used to carry traffic over an IP network” CNLab/University of Ulsan 6

Virtual Private Networks (VPN) What makes a VPN secure? v Encryption v Strong authentication of remote users and hosts. v Mechanisms for hiding or masking information about the private network topology from potential attackers Three basic types: v Hardware-based v Firewall-based v Standalone/Software-based CNLab/University of Ulsan 7

Security Association One-way relationship b/w sender and receiver that affords security services to the traffic on it Defined v by: Security parameter index (SPI): the index used to select SA under which a received packet will be processed v IP destination address v Security protocol identifier: identifies AH or ESP CNLab/University of Ulsan 8

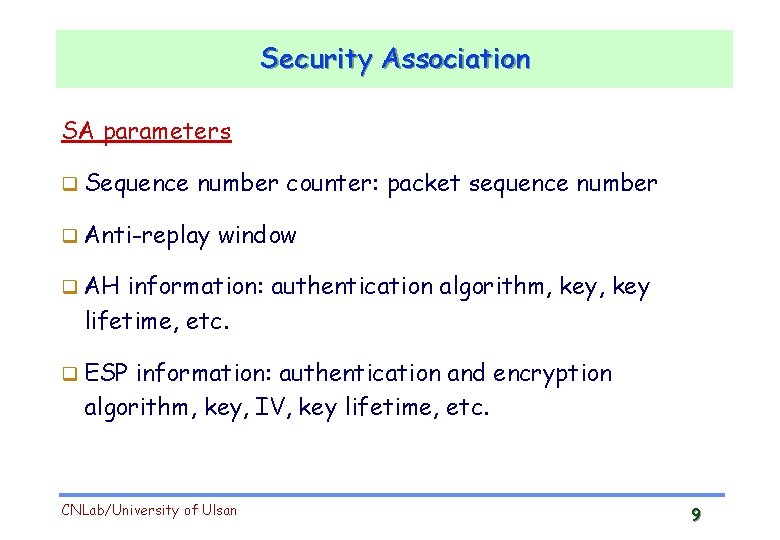
Security Association SA parameters Sequence number counter: packet sequence number Anti-replay window AH information: authentication algorithm, key lifetime, etc. ESP information: authentication and encryption algorithm, key, IV, key lifetime, etc. CNLab/University of Ulsan 9

Security Association SA parameters SA lifetime: after this lifetime, SA must be replaced with a new SA IPSec Path protocol mode: tunnel or transport mode MTU CNLab/University of Ulsan 10

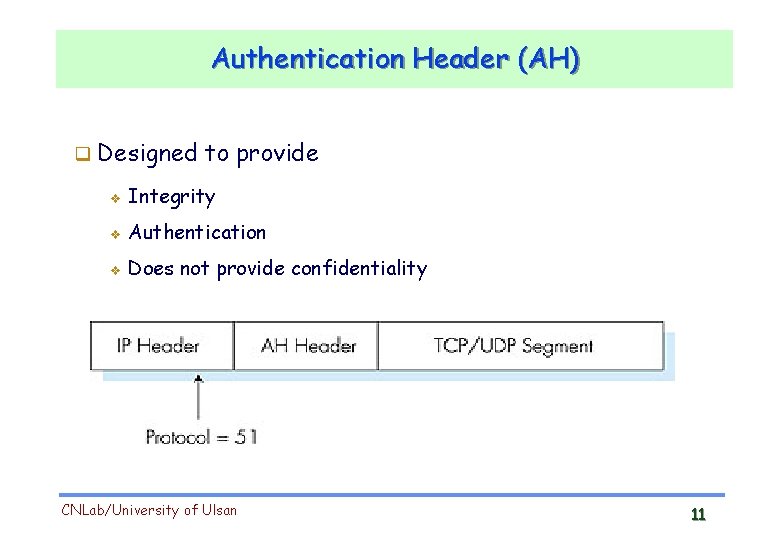
Authentication Header (AH) Designed to provide v Integrity v Authentication v Does not provide confidentiality CNLab/University of Ulsan 11

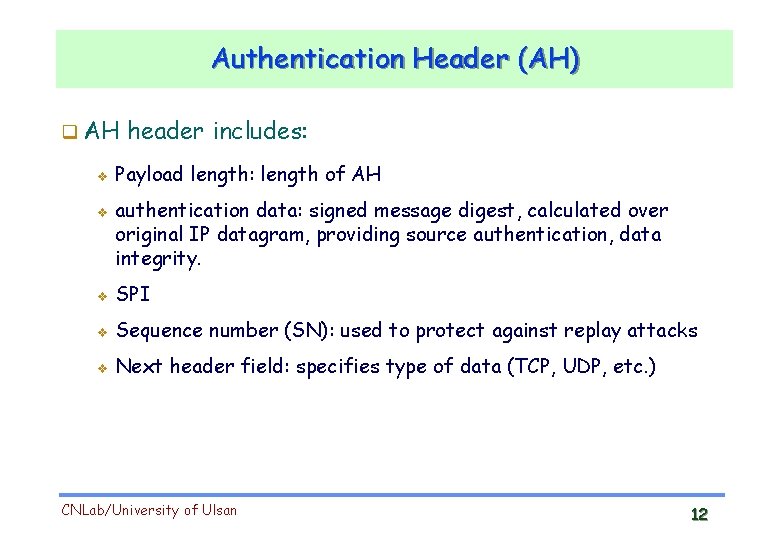
Authentication Header (AH) AH v v header includes: Payload length: length of AH authentication data: signed message digest, calculated over original IP datagram, providing source authentication, data integrity. v SPI v Sequence number (SN): used to protect against replay attacks v Next header field: specifies type of data (TCP, UDP, etc. ) CNLab/University of Ulsan 12

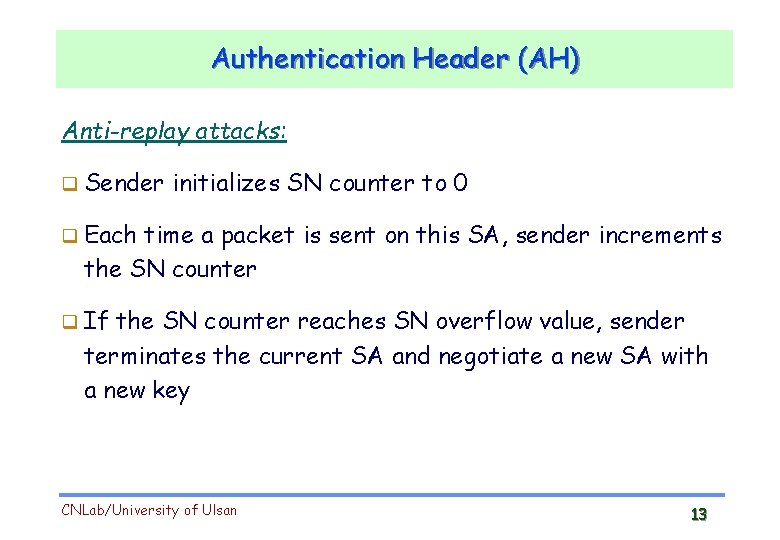
Authentication Header (AH) Anti-replay attacks: Sender initializes SN counter to 0 Each time a packet is sent on this SA, sender increments the SN counter If the SN counter reaches SN overflow value, sender terminates the current SA and negotiate a new SA with a new key CNLab/University of Ulsan 13

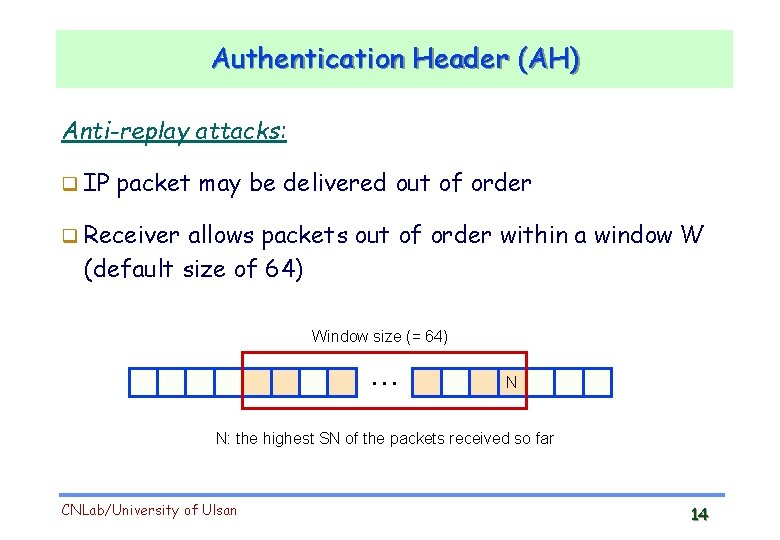
Authentication Header (AH) Anti-replay attacks: IP packet may be delivered out of order Receiver allows packets out of order within a window W (default size of 64) Window size (= 64) … N N: the highest SN of the packets received so far CNLab/University of Ulsan 14

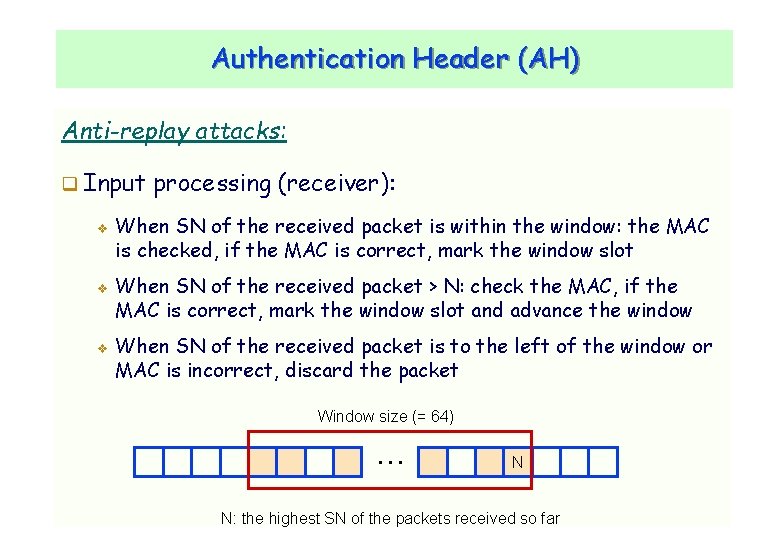
Authentication Header (AH) Anti-replay attacks: Input v v v processing (receiver): When SN of the received packet is within the window: the MAC is checked, if the MAC is correct, mark the window slot When SN of the received packet > N: check the MAC, if the MAC is correct, mark the window slot and advance the window When SN of the received packet is to the left of the window or MAC is incorrect, discard the packet Window size (= 64) … CNLab/University of Ulsan N N: the highest SN of the packets received so far 15

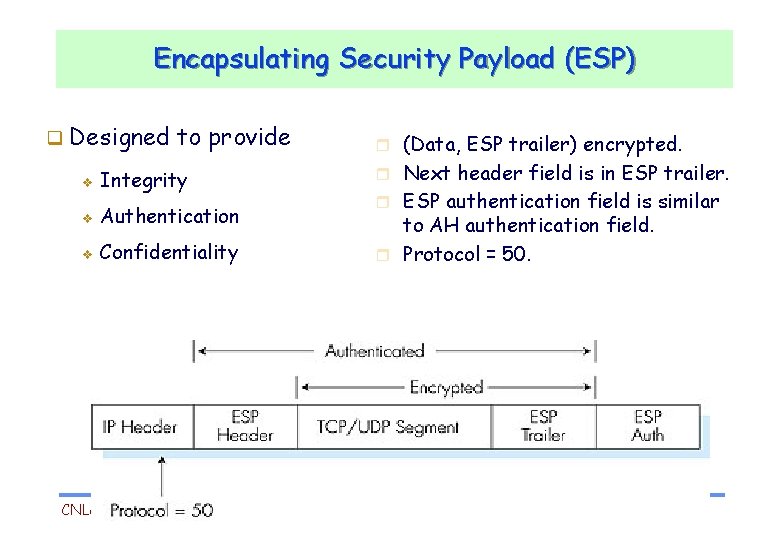
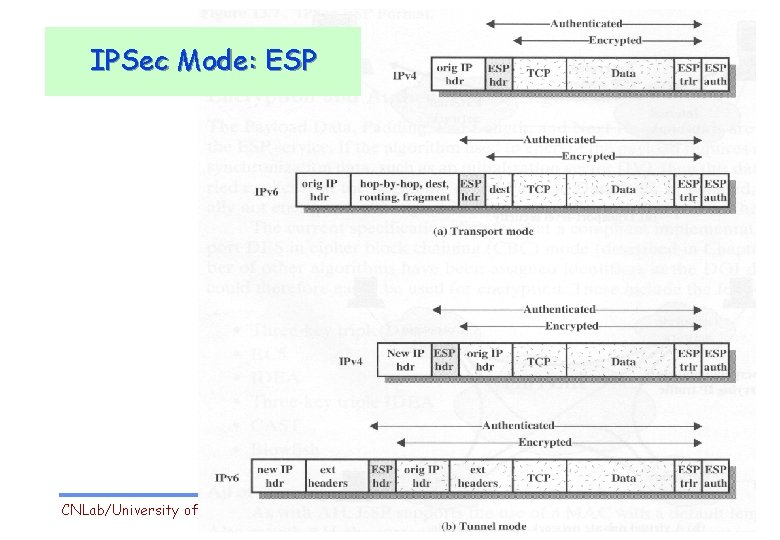
Encapsulating Security Payload (ESP) Designed to provide v Integrity v Authentication v Confidentiality CNLab/University of Ulsan r (Data, ESP trailer) encrypted. r Next header field is in ESP trailer. r ESP authentication field is similar to AH authentication field. r Protocol = 50. 16

IKE (Internet Key Exchange) A hybrid protocol designed to negotiate and provide authenticated keying material for security associations (SA) in a protected manner Based v v v on three previous protocols ISAKMP – A framework for authentication and key exchanges, define message types for key exchanges Oakley – A described series of key exchanges and the services provided by them SKEME – A versatile key exchange technique providing anonymity, non-repudiability, and quick key refreshment CNLab/University of Ulsan 17

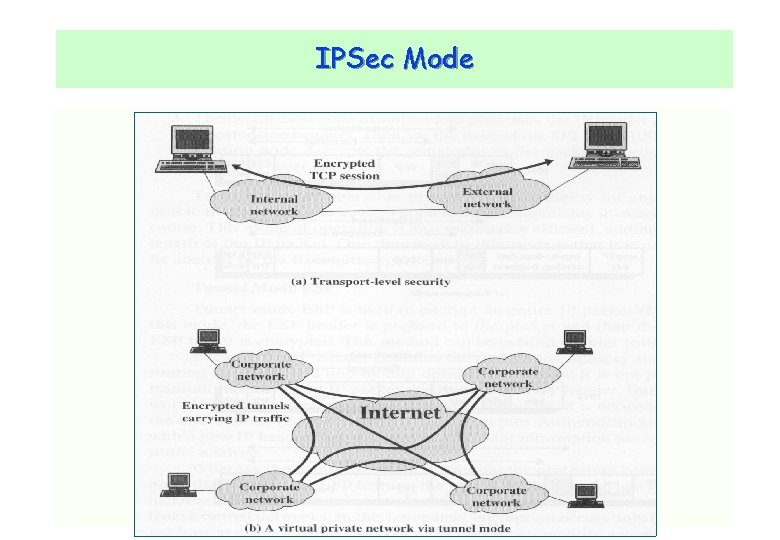
IPSec Mode Transport mode v Provides protection to the payload of IP packet v Used for end-to-end secure communication between two hosts Tunnel v v v mode Provides protection to the entire IP packet The original IP packet is encapsulated into new IP packet including AH or ESP header. Used for secure communications between two IPSec gateways CNLab/University of Ulsan 18

IPSec Mode CNLab/University of Ulsan 19

IPSec Mode: ESP CNLab/University of Ulsan 20