Chapter 15 Electronic Mail Security Part I PGP
























- Slides: 33

Chapter 15 Electronic Mail Security – Part I: PGP Data & Network Security Spring 2006 Dr. Jalili

Agenda In this session, we’ll study PGP. In the next session, other email security standards will be studied. n PGP History n PGP Building Blocks n Web of Trust n PGP Key Management n 2

New lords, new laws… n PGP (Pretty Good Privacy) was Phil R. Zimmermann’s (PRZ) answer to the US government 1991 Senate Bill 266: …force manufacturers of secure communications equipment to insert special "trap doors" in their products… 3

He that never climbed never fell… PRZ gave PGP to some friends of his, and they gave it to their friends, and so on. Kelly Goen posted it on several BBS networks… n Somehow, PGP leaked outside the US. n The USG began investigating PRZ for alleged aiding with ITAR violation. n (ITAR: International Traffic in Arms Regulations) 4

The wind cannot be caught in a net… n The USG investigation of Zimmermann went on for 5 years, but was eventually dropped: PRZ was not the one who uploaded PGP to BBS’. n People were nervous about their privacy. n 5

Necessity knows no law… PGP was using RSA & IDEA encryption algorithms. n The company holding the RSA patent, RSA Security, Inc. , alleged that PGP's use of the RSA algorithm infringed on its patent. n PRZ has the same problem with IDEA’s patent. n 6

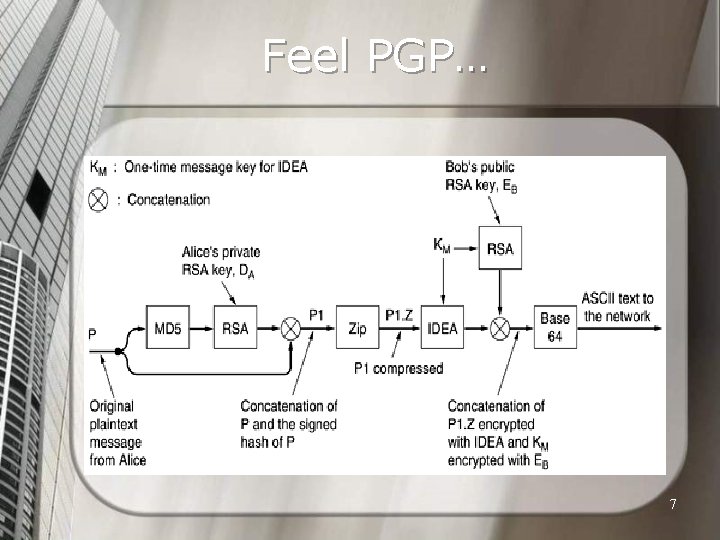
Feel PGP… 7

Base 64? Described in RFC 3548, Base 64 is a way of encoding any stream of bits into a set of alphanumeric characters (a-z, A-Z, 09 and two/three other characters). n Example: n 111100100011010001010110 8 j. RW n Good for RFC 822 compliance, but increases e-mail size by about 33%. 8

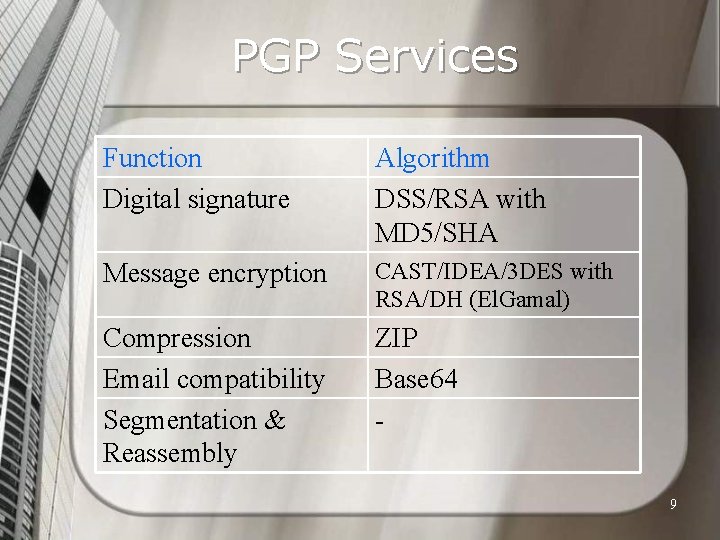
PGP Services Function Digital signature Algorithm DSS/RSA with MD 5/SHA Message encryption CAST/IDEA/3 DES with RSA/DH (El. Gamal) Compression Email compatibility Segmentation & Reassembly ZIP Base 64 9

What makes PGP “pretty good” 1. 2. 3. 4. The best available cryptographic algorithms as building blocks. A general-purpose application that is independent of operating system and processor and that is based on a small set of easy-to-use commands. Well-documented, free, open-source, widely available. Good support, low-cost commercial versions available, too. 10

Digging a bit deeper PRZ’s art was not to use the best building blocks, but also to “glue” them in the best way. n Let’s see how sticky his glue was! n 11

Compression Compensates for 33% increase of Base 64 encoding. n Statistical analysis shows that, on average, ZIP compression ratio is 50%. n Typical messages are shrunk by 66% (ZIP+Base 64). n 12

Compression (cont’d) n Why sign before compression? 1. 2. n Why use compression before encryption? 1. 2. n People are likely to store uncompressed messages; Re-compression not deterministic. To reduce encryption time; To remove redundancy, thus making cryptanalysis harder. Bruce Schneier’s “Decryption Oracle” 13

Encryption Process 1. 2. The sender generates a message and a random 128/168 -bit number to be used as a session key for this message only. The random number generation is based on ANSI X 12. 17. The message is encrypted, using CAST-128 (or IDEA or 3 DES) with the session key. Encryption is done in 64 bit CFB (Cipher Feedback) mode. 14

Encryption Process (cont’d) 3. 4. 5. The session key is encrypted with RSA/El. Gamal, using the recipient's public key, and is appended to the message. The receiver uses RSA/El. Gamal with its private key to decrypt and recover the session key. The session key is used to decrypt the message. 15

Types of Keys n How many keys are used in PGP? 1. 2. 3. 4. one-time session conventional keys; public keys; private keys; passphrase-based conventional keys (more on this later). 16

Key Requirements 1. 2. A means of generating unpredictable session key. A user must be allowed to have multiple public-key/private-key pairs. n 3. Why? Each PGP entity must maintain a file of its own public/private key pairs as well as a file of public keys of correspondents. 17

Session Keys One-to-one relationship between messages & session keys. n Session keys are random numbers seeded with user’s keystrokes. n Both keystroke timing & the actual keys struck are used. n The conventional algorithm itself is used to derive the random number from input. n 18

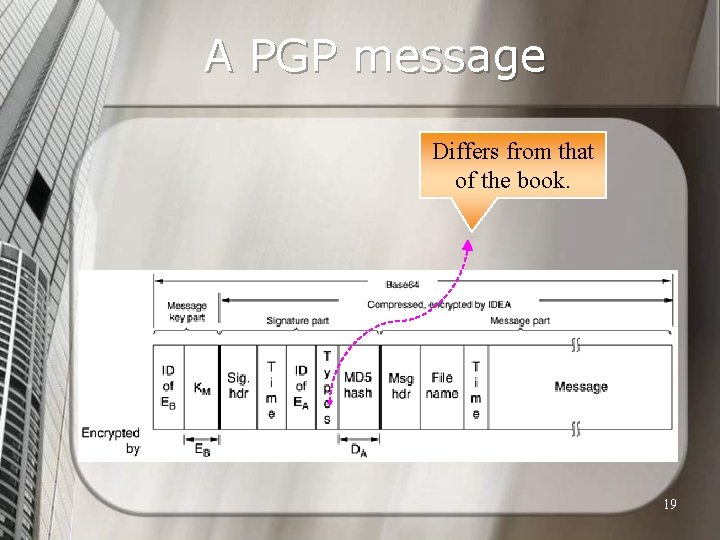
A PGP message Differs from that of the book. 19

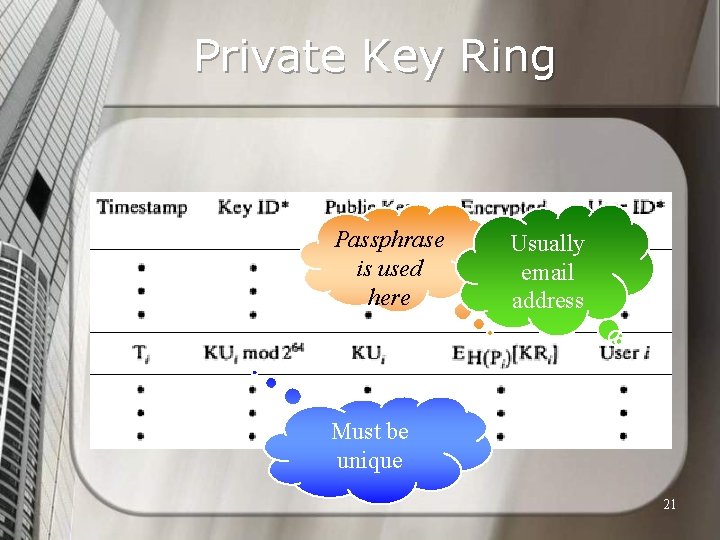
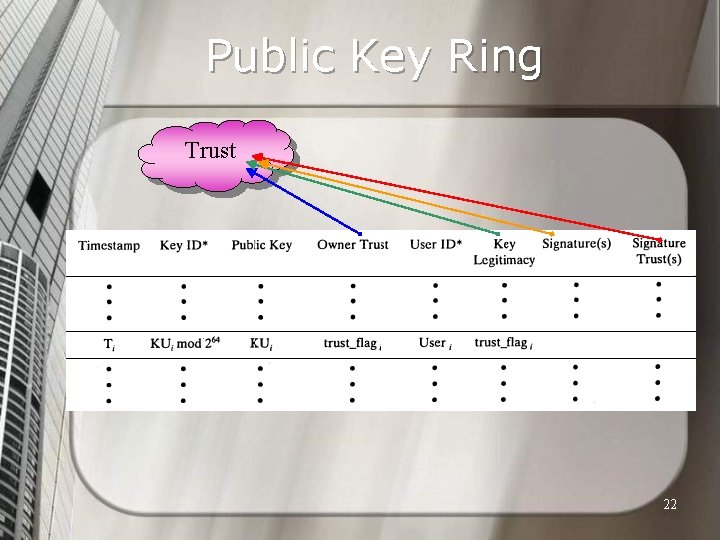
Key Rings Key management has received a large amount of attention in PGP as it is the Achilles heel of all security systems. n PGP provides two types of data structures for key management called Key Ring: Public Key Ring, and Private Key Ring. n 20

Private Key Ring Passphrase is used here Usually email address Must be unique 21

Public Key Ring Trust 22

Public Key Management: Trust The most important issue in public-key systems is how to distribute public keys, preventing man-in-the-middle / masquerade attacks. n This issue becomes a real pain in the neck when the parties don’t know each other, and don’t have physical access to each other. n Traditional approach: Using CAs. n 23

Trust (cont’d) PRZ didn’t believe in the USG, so he didn’t trust in the USG’s agents (CAs) either. n He introduced a new, governmentagnostic approach, called Web of Trust. n While, IMHO, Wo. T is the most elegant feature of PGP today, it’s also the source of every sin! n 24

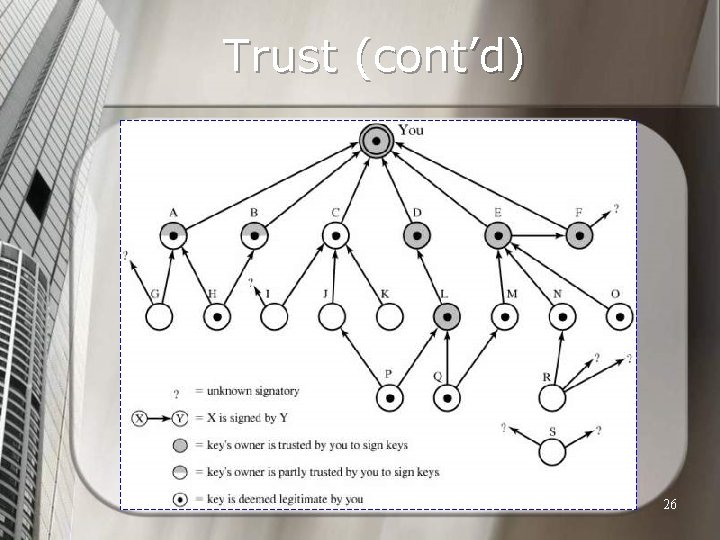
Trust (cont’d) To better understand the Wo. T, think you are lost in a small city, and want to find somewhere. Note that not all people can be trusted, and you’ll be in danger if you choose the wrong path n As a starting point, suppose you know a few people in the city, each of which knows a few of other citizens, but isn’t informative enough by his own to give you some hints. n 25

Trust (cont’d) 26

Trust (cont’d) n A Trust model consists of two parts: 1. A set of rule, e. g. : n n 2. I will trust everyone’s signature! I will trust everyone trusted by two distinct persons already trusted by me. A set of information: n n n Ali, Mohsen, and Reza are trusted by me; Mohsen trusts Hassan; Ali & Reza both trust Hossein. 27

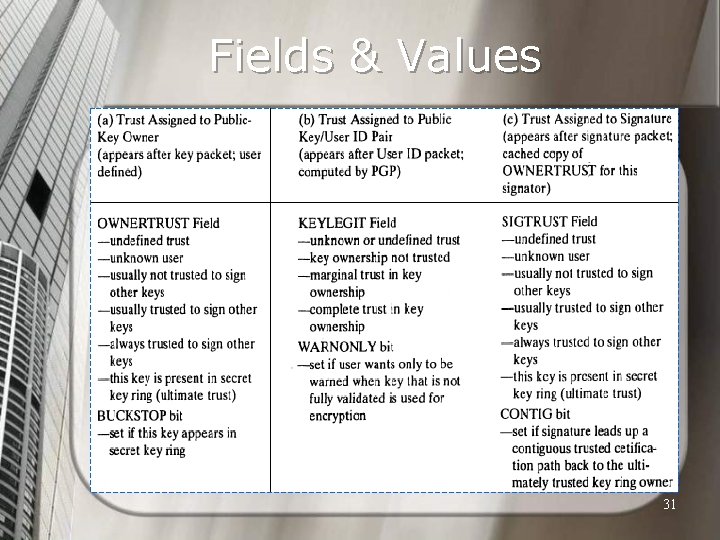
PGP Trust Model Each entry in the public-key ring is a public key certificate. n Associated with each entry are zero or more signatures that the key ring owner has collected that sign this certificate. n In turn, each signature has associated with it a signature trust field that indicates the degree to which this PGP user trusts the signer to certify public keys. n 28

PGP Trust Model (cont’d) An owner trust field indicates the degree to which this public key is trusted to sign other public-key certificates; this level of trust is assigned by the user. n The signature trust can be thought of the cached copy of this field. n 29

PGP Trust Model (cont’d) The key legitimacy field indicates the extent to which PGP will trust that this is a valid public key for this user; the higher the level of trust, the stronger is the binding of this user ID to this key. This field is computed by PGP. n The key legitimacy field is derived from the collection of signature trust fields in the entry. n 30

Fields & Values 31

Revoking Public Keys n n n A user may wish to revoke his or her current public key either because compromise is suspected or simply to avoid the use of the same key for an extended period. The convention for revoking a public key is for the owner to issue a key revocation certificate, signed by the owner. Any Problem with this approach? 32

If privacy is outlawed, only outlaws will have privacy. ---Phil Zimmermann 33