Chapter 15 16 LAN Local Area Network Topologies










- Slides: 61

Chapter 15 & 16 LAN (Local Area Network)

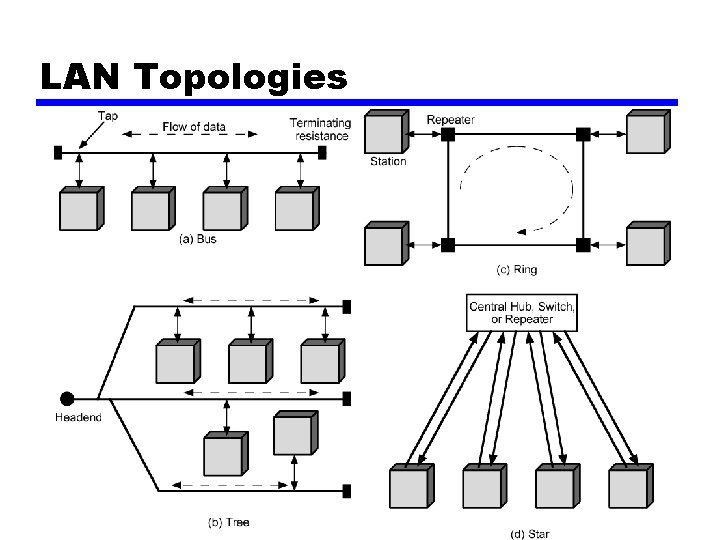
Topologies • Tree • Bus —Special case of tree • One trunk, no branches • Ring • Star

LAN Topologies

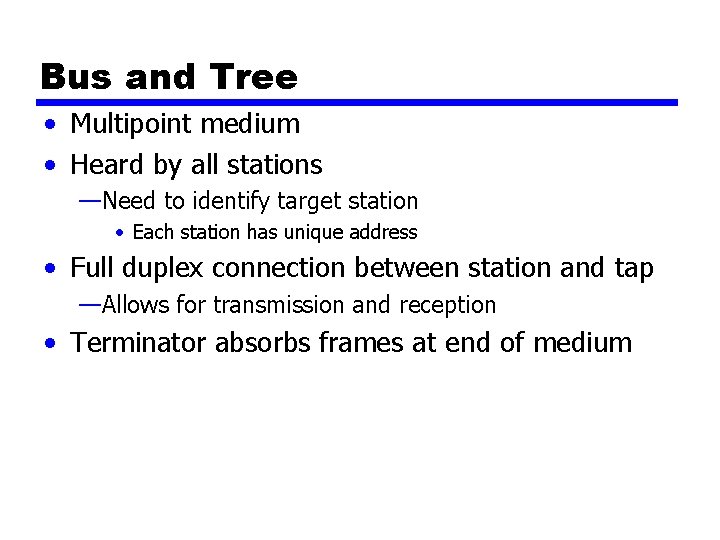
Bus and Tree • Multipoint medium • Heard by all stations —Need to identify target station • Each station has unique address • Full duplex connection between station and tap —Allows for transmission and reception • Terminator absorbs frames at end of medium

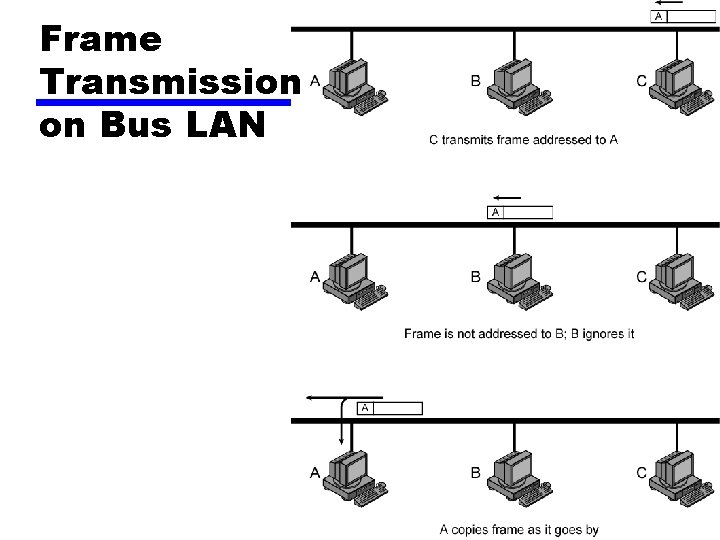
Frame Transmission on Bus LAN

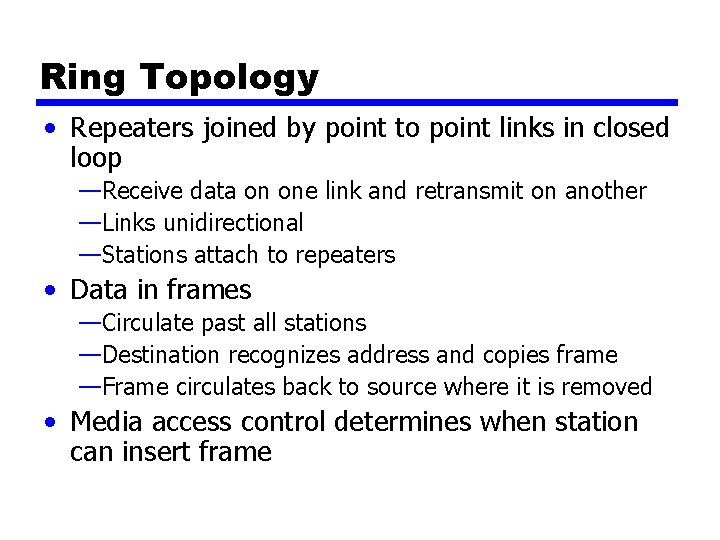
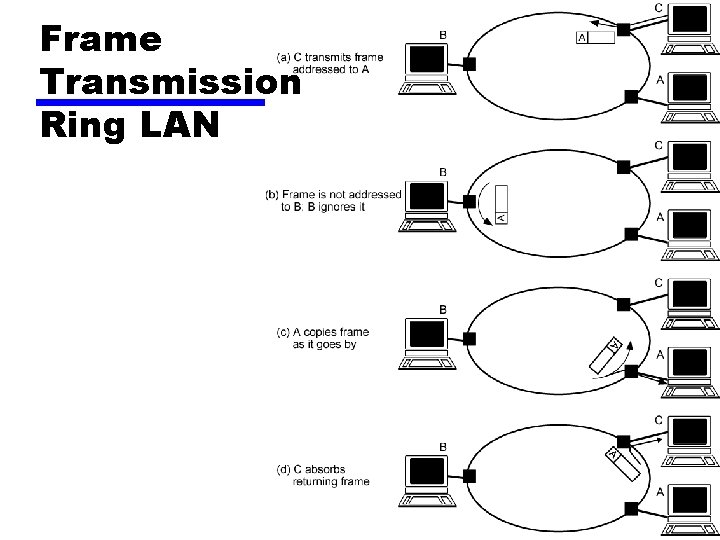
Ring Topology • Repeaters joined by point to point links in closed loop —Receive data on one link and retransmit on another —Links unidirectional —Stations attach to repeaters • Data in frames —Circulate past all stations —Destination recognizes address and copies frame —Frame circulates back to source where it is removed • Media access control determines when station can insert frame

Frame Transmission Ring LAN

Star Topology • Each station connected directly to central node —Usually via two point to point links • Central node can broadcast —Physical star, logical bus —Only one station can transmit at a time • Central node can act as frame switch

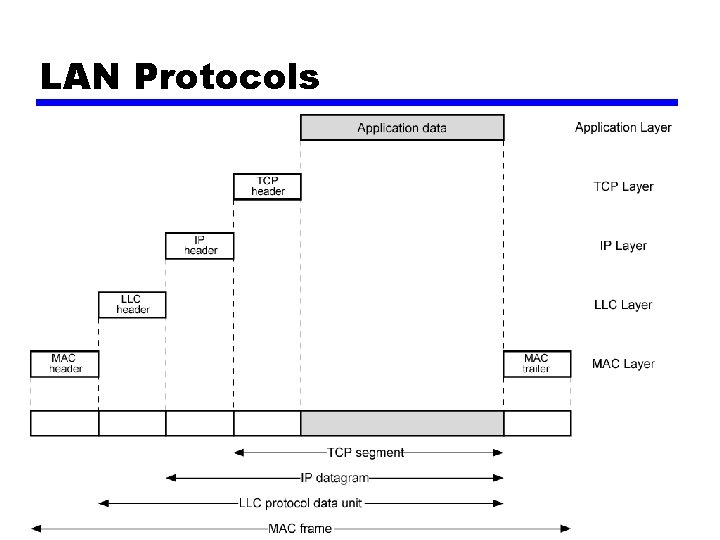
LAN Protocol Architecture • • Lower layers of OSI model IEEE 802 reference model Physical Data link —Logical link control (LLC) —Media access control (MAC)

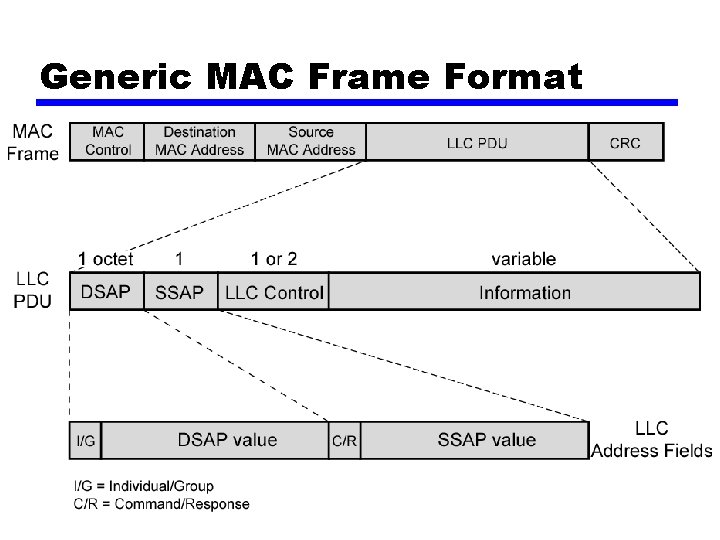
Logical Link Control • Flow and error control —Based on HDLC —Three types • Unacknowledged connectionless service • Connection mode service • Acknowledged connectionless service • Addressing (De/Multiplexing) —Specifying source and destination LLC users —Referred to as service access points (SAP) —Typically higher level protocol

Media Access Control • Govern access to transmission medium • Resource sharing methods • Centralized & Distributed — Centralized • Greater control • Simple access logic at station — Distributed • Synchronous & Asynchronous — Synchronous • Specific capacity dedicated to connection — Asynchronous • In response to demand

MAC Methods • Round robin —Order stations and allocate the right to use resources in turn • Reservation —First get exclusive use of resources before access • Contention —Access without explicit co-ordination —Retransmit in case of collision —Good for bursty traffic

LAN Protocols

Generic MAC Frame Format

Ethernet • • • Contention Aloha Slotted Aloha CSMA(Carrier Sense Multiple Access) CSMA/CD(Collision Detection) Splitting

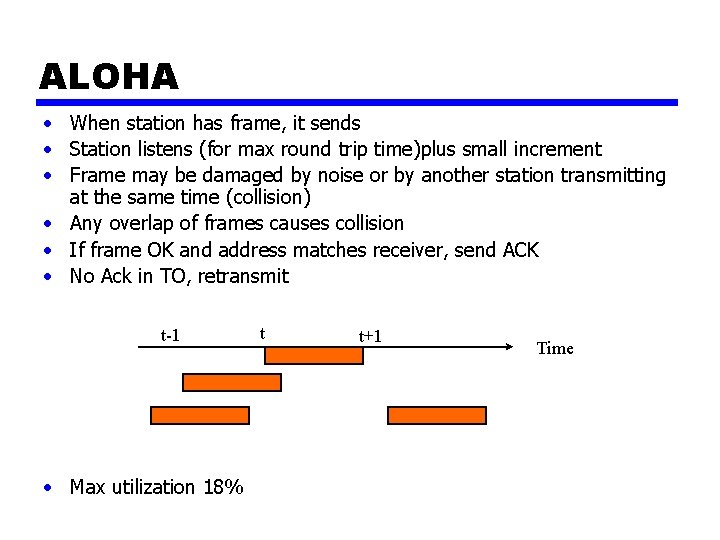
ALOHA • When station has frame, it sends • Station listens (for max round trip time)plus small increment • Frame may be damaged by noise or by another station transmitting at the same time (collision) • Any overlap of frames causes collision • If frame OK and address matches receiver, send ACK • No Ack in TO, retransmit t-1 • Max utilization 18% t t+1 Time

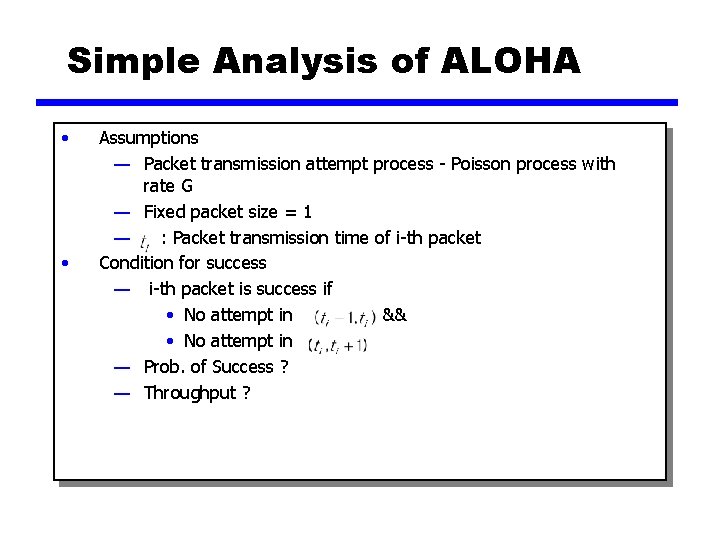
Simple Analysis of ALOHA • • Assumptions — Packet transmission attempt process - Poisson process with rate G — Fixed packet size = 1 — : Packet transmission time of i-th packet Condition for success — i-th packet is success if • No attempt in && • No attempt in — Prob. of Success ? — Throughput ?

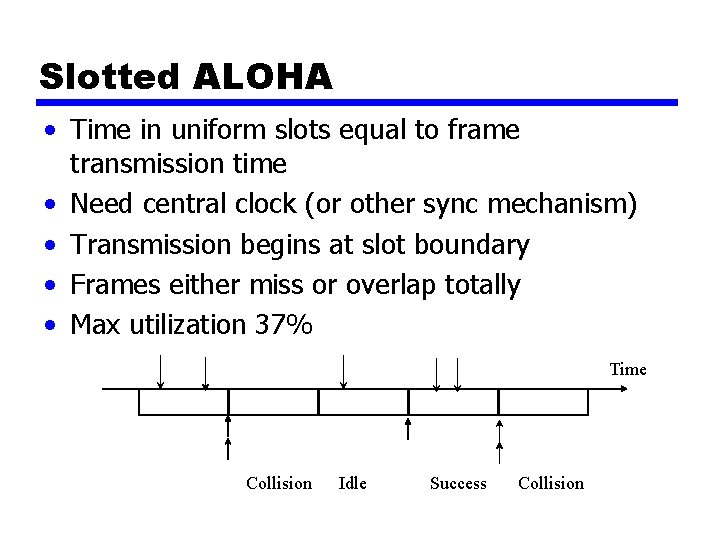
Slotted ALOHA • Time in uniform slots equal to frame transmission time • Need central clock (or other sync mechanism) • Transmission begins at slot boundary • Frames either miss or overlap totally • Max utilization 37% Time Collision Idle Success Collision

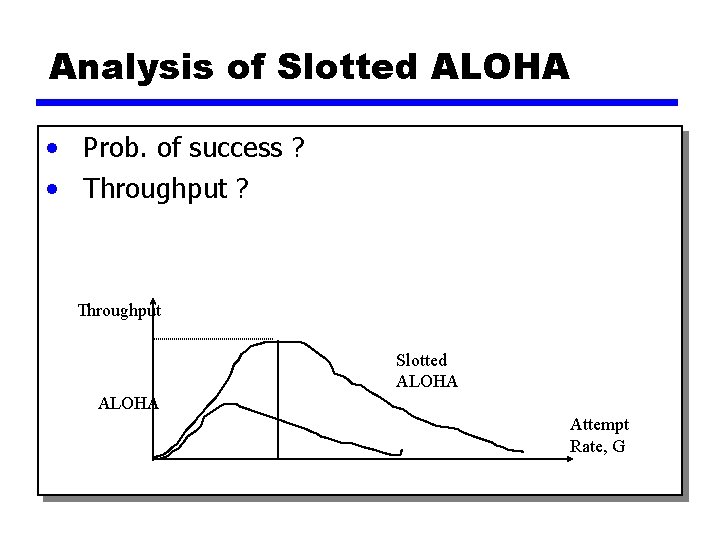
Analysis of Slotted ALOHA • Prob. of success ? • Throughput ? Throughput Slotted ALOHA Attempt Rate, G

CSMA • Problems of slotted ALOHA • Carrier Sense —Probe if the carrier is busy before transmit • If idle, transmit with some probability —Effects ? —Collision ? • If Propagation time << Transmission time, CSMA improves performance • Three CSMA schemes —Nonpersistent CSMA — 1 -persistent CSMA —p-persistent CSMA

Nonpersistent CSMA 1. If medium is idle, transmit; otherwise, go to 2 2. If medium is busy, wait amount of time drawn from probability distribution (retransmission delay) and repeat 1 • Random delays reduces probability of collisions — Consider two stations become ready to transmit at same time — If both stations delay same time before retrying, then collision • Capacity is wasted because medium will remain idle following end of transmission — Even if one or more stations waiting

1 -persistent CSMA 1. If medium idle, transmit; otherwise, go to step 2 2. If medium busy, listen until idle; then transmit immediately • If two or more stations waiting, collision guaranteed

P-persistent CSMA • Compromise that attempts to reduce collisions — Like nonpersistent • And reduce idle time — Like 1 -persistent • Rules: 1. If medium idle, transmit with probability p, and delay one time unit with probability (1 – p) — Time unit typically maximum propagation delay 2. If medium busy, listen until idle and repeat step 1 3. If transmission is delayed one time unit, repeat step 1 • What is an effective value of p?

Value of p • • • Avoid instability under heavy load n stations waiting to send (backlogged station) End of transmission, expected number of stations attempting to transmit is number of stations ready times probability of transmitting — np • • If np > 1 on average there will be a collision Repeated attempts to transmit almost guaranteeing more collisions Retries compete with new transmissions Eventually, all stations trying to send — Continuous collisions; zero throughput • • So np < 1 for expected peaks of n If heavy load expected, p small However, as p made smaller, stations wait longer At low loads, this gives very long delays

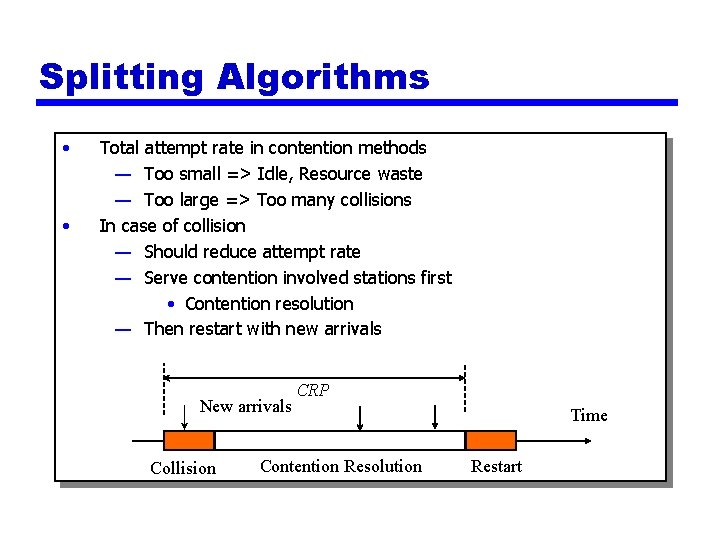
Splitting Algorithms • • Total attempt rate in contention methods — Too small => Idle, Resource waste — Too large => Too many collisions In case of collision — Should reduce attempt rate — Serve contention involved stations first • Contention resolution — Then restart with new arrivals New arrivals Collision CRP Contention Resolution Time Restart

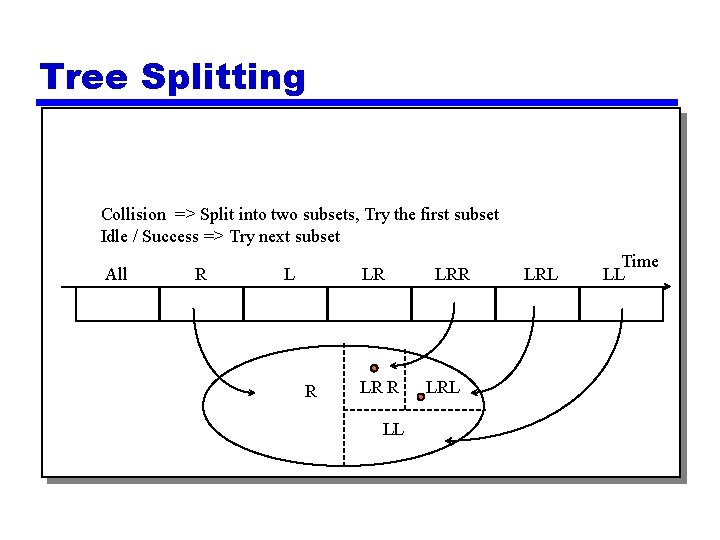
Tree Splitting Collision => Split into two subsets, Try the first subset Idle / Success => Try next subset All R L LR R LL LRR LRL Time LL

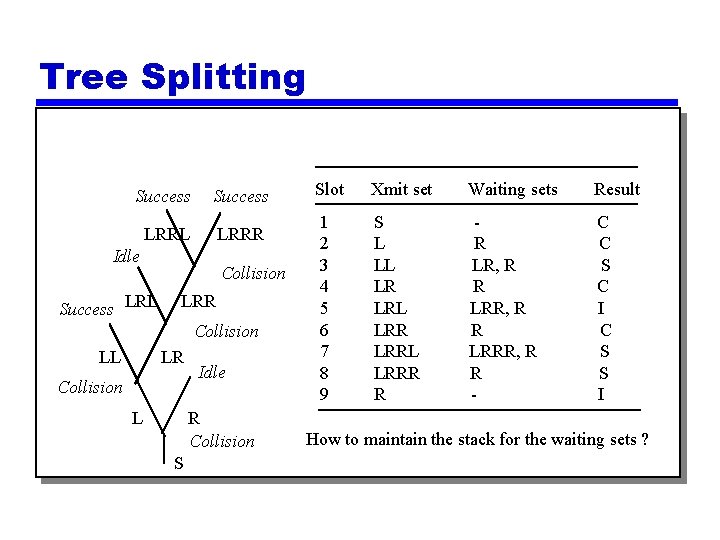
Tree Splitting Success LRRL LRRR Idle Success LRL Collision LRR Collision LL LR Collision L Idle R Collision S Slot Xmit set Waiting sets Result 1 2 3 4 5 6 7 8 9 S L LL LR LRL LRRL LRRR R R LR, R R LRRR, R R - C C S C I C S S I How to maintain the stack for the waiting sets ?

Improvements of Tree Algorithm • Arrival estimation — Spilt into k subsets • Collision -> Idle sequence • Collision -> Collision sequence

CSMA/CD • • With CSMA, collision occupies medium for duration of transmission Stations listen whilst transmitting (Listen while talk) to detect collision — On baseband bus, collision produces much higher signal voltage than non-collided signal — Since signal attenuated over distance, Limit the bus length to 500 m (10 Base 5) or 200 m (10 Base 2) 1. 2. 3. 4. If medium idle, transmit, otherwise, step 2 If busy, listen for idle, then transmit If collision detected, jam then cease transmission After jam, wait random time then start from step 1

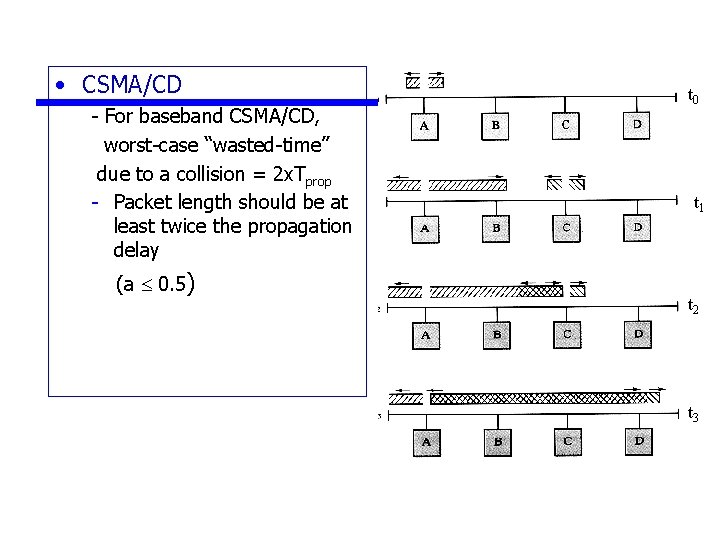
• CSMA/CD - For baseband CSMA/CD, worst-case “wasted-time” due to a collision = 2 x. Tprop - Packet length should be at least twice the propagation delay (a 0. 5) t 0 t 1 t 2 t 3

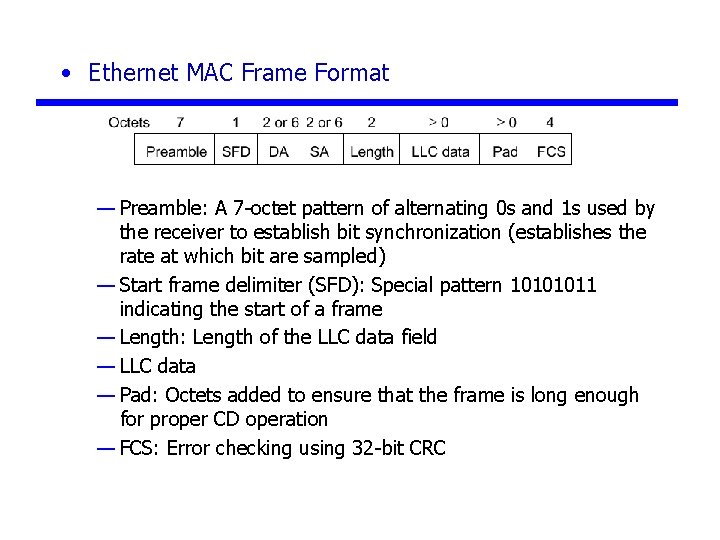
• Ethernet MAC Frame Format — Preamble: A 7 -octet pattern of alternating 0 s and 1 s used by the receiver to establish bit synchronization (establishes the rate at which bit are sampled) — Start frame delimiter (SFD): Special pattern 10101011 indicating the start of a frame — Length: Length of the LLC data field — LLC data — Pad: Octets added to ensure that the frame is long enough for proper CD operation — FCS: Error checking using 32 -bit CRC

IEEE 802. 3 BEB • IEEE 802. 3 and Ethernet use BEB(Binary Exponential Backoff) — If the medium is idle, send immediately, • 1 -persistent can yield higher utilization than non/p-persistent — If the medium is busy, pause for a random interval after the end of busy period — Backoff delay • Because the offered load fluctuates dynamically, it is best to adjust the attempt rate dynamically to optimize the system utilization • How do you guess the offered load? • How do you adjust the total attempt rate?

BEB • Guessing the number of backlogged stations — More backlogged station => More collisions • Adjustment of attempt rate — Change the backoff delay based on guessed offered load • BEB(Binary Exponential Backoff) — After each successive collision, double the backoff delay — Randomly select backoff delay (0, 2^n – 1) where n is number of trials • 1 -persistent algorithm with BEB is efficient — At low loads, 1 -persistence guarantees station can seize channel once idle — At high loads, at least as stable as other techniques • Backoff algorithm gives last-in, first-out effect • Stations with few collisions transmit first

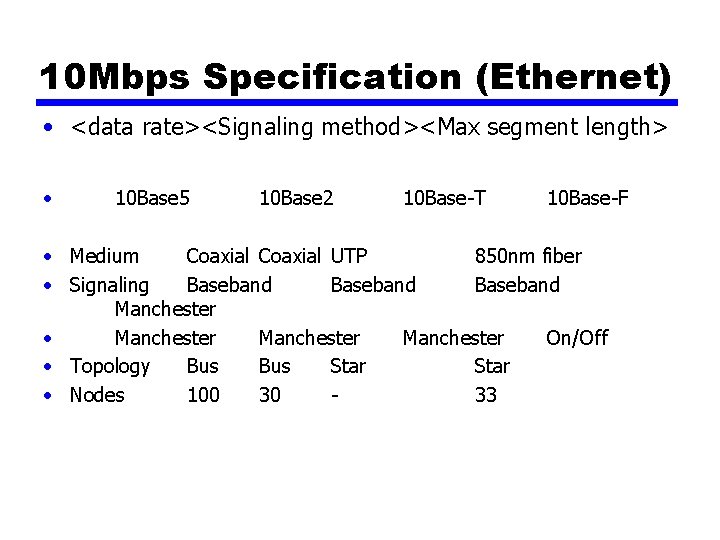
10 Mbps Specification (Ethernet) • <data rate><Signaling method><Max segment length> • 10 Base 5 10 Base 2 10 Base-T 10 Base-F • Medium Coaxial UTP 850 nm fiber • Signaling Baseband Manchester • Manchester On/Off • Topology Bus Star • Nodes 100 30 33

Repeater • A repeater connects two or more bus segments to build a longer bus • A signal received from one bus segment is repeated to all other segments

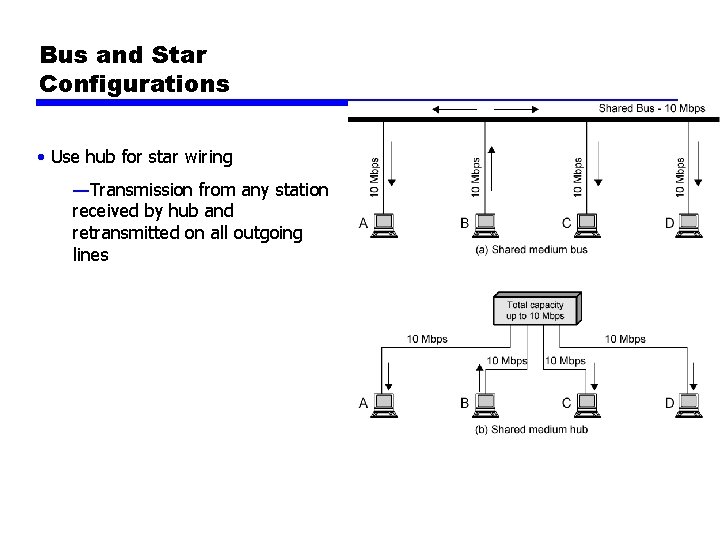
Bus and Star Configurations • Use hub for star wiring —Transmission from any station received by hub and retransmitted on all outgoing lines

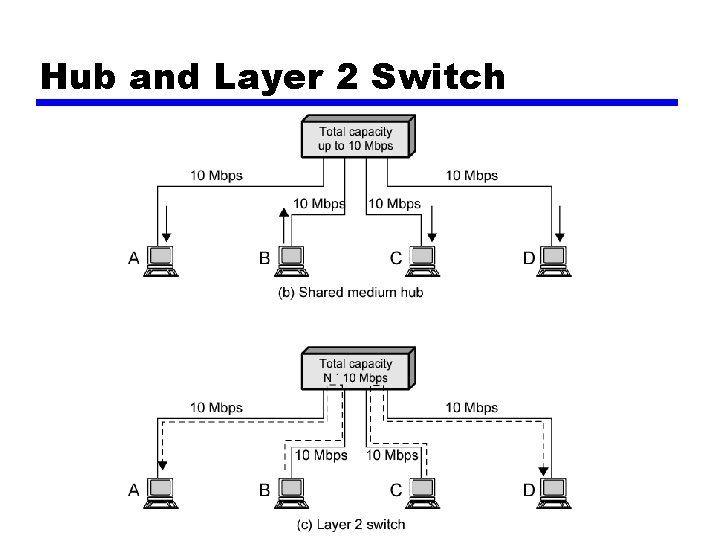
Hubs • Active central element of star layout • Each station connected to hub by two lines — Transmit and receive • Hub acts as a repeater • When single station transmits, hub repeats signal on outgoing line to each station • Line consists of two unshielded twisted pairs • Limited to about 100 m — High data rate and poor transmission qualities of UTP • Optical fiber may be used — Max about 500 m • Physically star, logically bus • Transmission from any station received by all other stations • If two stations transmit at the same time, collision

Hub Layouts • Multiple levels of hubs cascaded • Each hub may have a mixture of stations and other hubs attached to from below • Fits well with building wiring practices — Wiring closet on each floor — Hub can be placed in each one — Each hub services stations on its floor

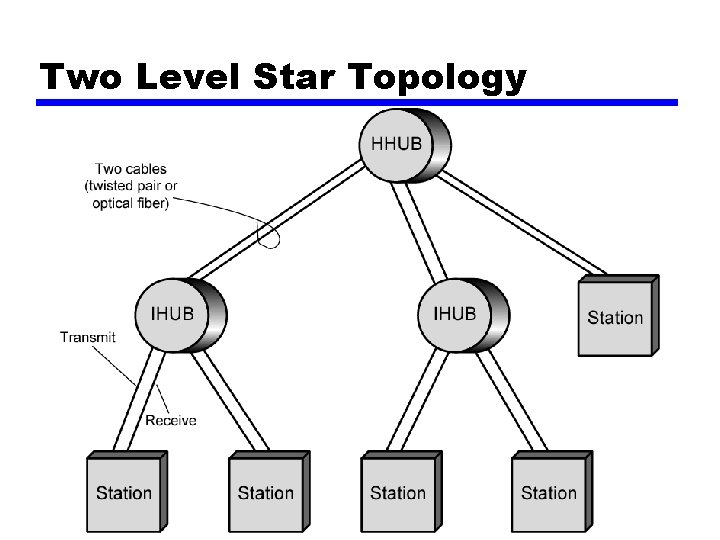
Two Level Star Topology

Hub and Layer 2 Switch

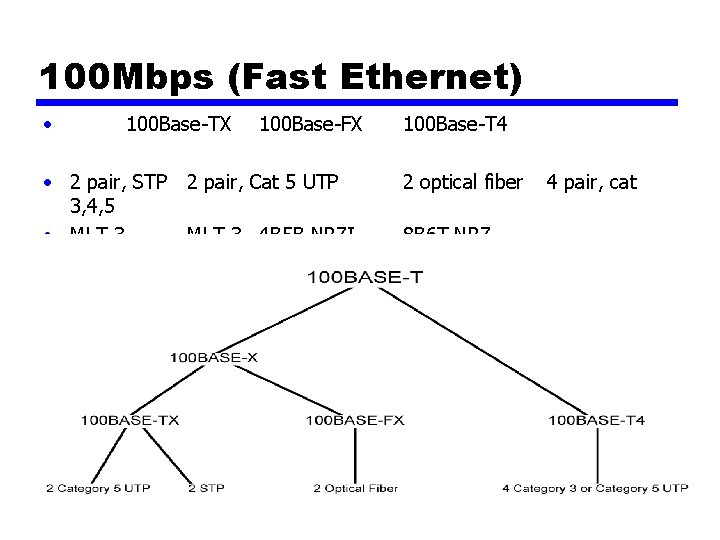
100 Mbps (Fast Ethernet) • 100 Base-TX 100 Base-FX • 2 pair, STP 2 pair, Cat 5 UTP 3, 4, 5 • MLT-3 4 B 5 B, NRZI 100 Base-T 4 2 optical fiber 8 B 6 T, NRZ 4 pair, cat

100 BASE-X • Bidirectional data rate 100 Mbps over two links • Encoding scheme same as FDDI — 4 B/5 B-NRZI — Modified for each option • 100 BASE-TX — Two pairs of twisted-pair cable — STP and Category 5 UTP allowed — The MTL-3 signaling scheme is used • 100 BASE-FX — Two optical fiber cables — Intensity modulation used to convert 4 B/5 B-NRZI code group stream into optical signals — 1 represented by pulse of light — 0 by either absence of pulse or very low intensity pulse

100 BASE-T 4 • 100 -Mbps over lower-quality Cat 3 UTP — Taking advantage of large installed base — Cat 5 optional — Does not transmit continuous signal between packets — Useful in battery-powered applications • Can not get 100 Mbps on single twisted pair — Data stream split into three separate streams • Each with an effective data rate of 33. 33 Mbps — Four twisted pairs used — Data transmitted and received using three pairs — Two pairs configured for bidirectional transmission • NRZ encoding not used — Would require signaling rate of 33 Mbps on each pair — Does not provide synchronization — Ternary signaling scheme (8 B 6 T)

Full Duplex Operation • Traditional Ethernet half duplex — Either transmit or receive but not both simultaneously • With full-duplex, station can transmit and receive simultaneously • 100 -Mbps Ethernet in full-duplex mode, theoretical transfer rate 200 Mbps • Attached stations must have full-duplex adapter cards • Must use switching hub — Each station constitutes separate collision domain — In fact, no collisions — CSMA/CD algorithm no longer needed — Ethernet MAC frame format used — Attached stations can continue CSMA/CD

Gigabit Ethernet - Differences • Carrier extension • At least 4096 bit-times long (512 for 10/100) • Frame bursting

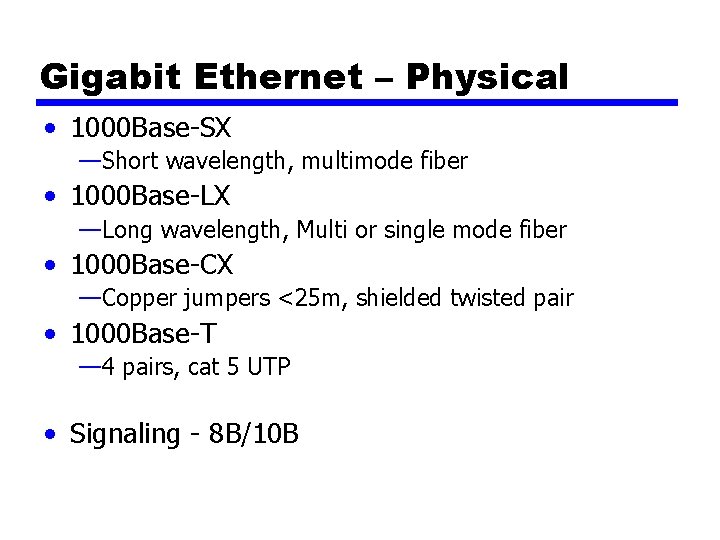
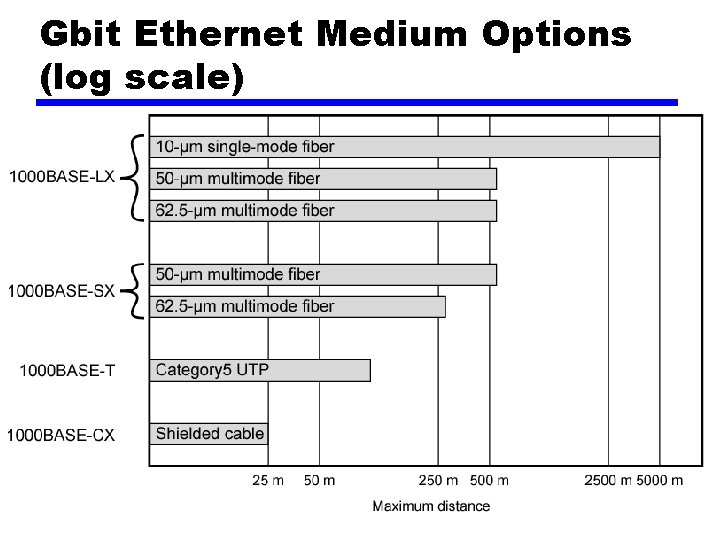
Gigabit Ethernet – Physical • 1000 Base-SX —Short wavelength, multimode fiber • 1000 Base-LX —Long wavelength, Multi or single mode fiber • 1000 Base-CX —Copper jumpers <25 m, shielded twisted pair • 1000 Base-T — 4 pairs, cat 5 UTP • Signaling - 8 B/10 B

Gbit Ethernet Medium Options (log scale)

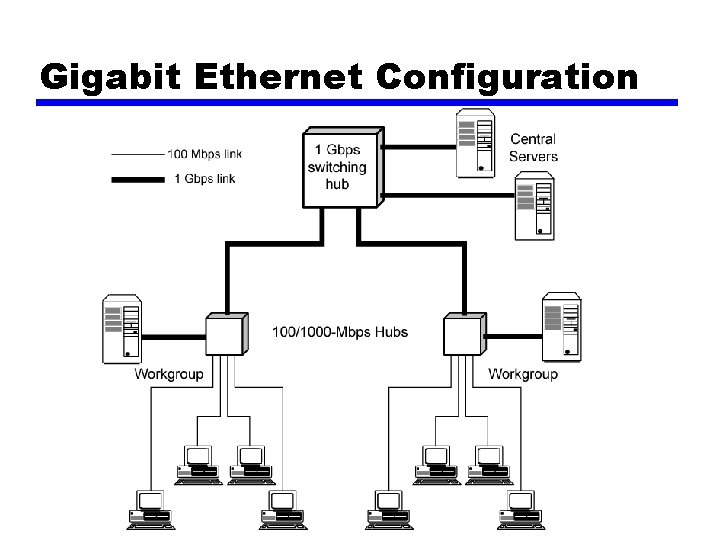
Gigabit Ethernet Configuration

10 Gbps Ethernet - Uses • High-speed, local backbone interconnection between large-capacity switches • Server farm • Campus wide connectivity • Enables Internet service providers (ISPs) and network service providers (NSPs) to create very high-speed links at very low cost • Allows construction of (MANs) and WANs — Connect geographically dispersed LANs between campuses or points of presence (Po. Ps) • Ethernet competes with ATM and other WAN technologies • 10 -Gbps Ethernet provides substantial value over ATM

10 Gbps Ethernet - Advantages • No expensive, bandwidth-consuming conversion between Ethernet packets and ATM cells • Network is Ethernet, end to end • IP and Ethernet together offers Qo. S and traffic policing approach ATM • Advanced traffic engineering technologies available to users and providers • Variety of standard optical interfaces (wavelengths and link distances) specified for 10 Gb Ethernet • Optimizing operation and cost for LAN, MAN, or WAN

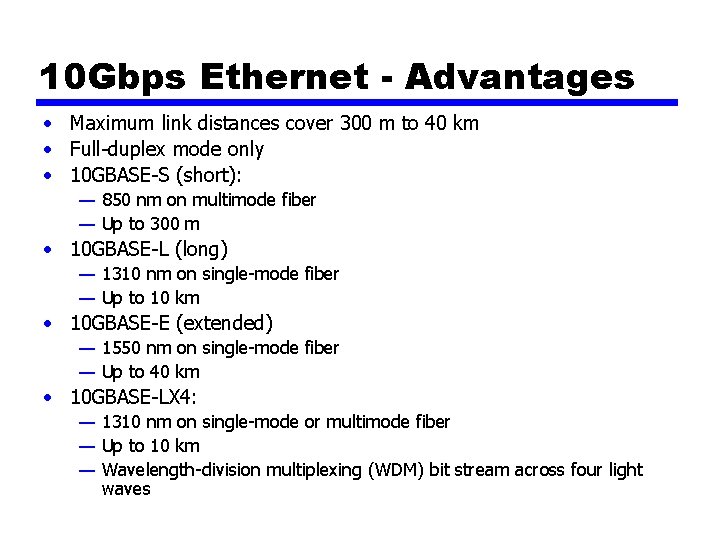
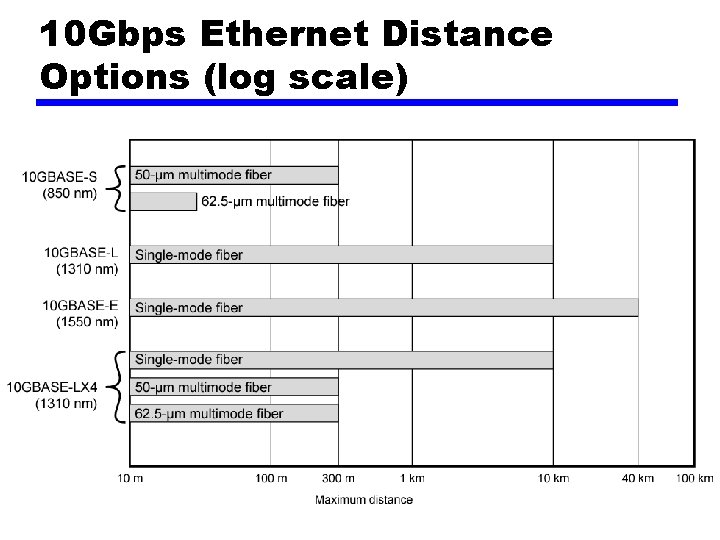
10 Gbps Ethernet - Advantages • Maximum link distances cover 300 m to 40 km • Full-duplex mode only • 10 GBASE-S (short): — 850 nm on multimode fiber — Up to 300 m • 10 GBASE-L (long) — 1310 nm on single-mode fiber — Up to 10 km • 10 GBASE-E (extended) — 1550 nm on single-mode fiber — Up to 40 km • 10 GBASE-LX 4: — 1310 nm on single-mode or multimode fiber — Up to 10 km — Wavelength-division multiplexing (WDM) bit stream across four light waves

10 Gbps Ethernet Distance Options (log scale)

Token Ring (802. 5) • Developed from IBM's commercial token ring • Because of IBM's presence, token ring has gained broad acceptance • Never achieved popularity of Ethernet • Market share likely to decline

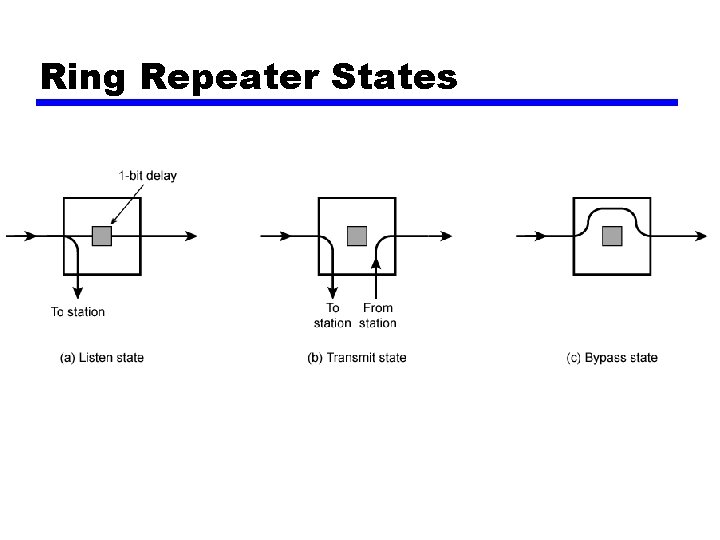
Ring Operation • Each repeater connects to two others via unidirectional transmission links • Single closed path • Data transferred bit by bit from one repeater to the next • Repeater regenerates and retransmits each bit • Repeater performs data insertion, data reception, data removal • Repeater acts as attachment point • Packet removed by transmitter after one trip round ring

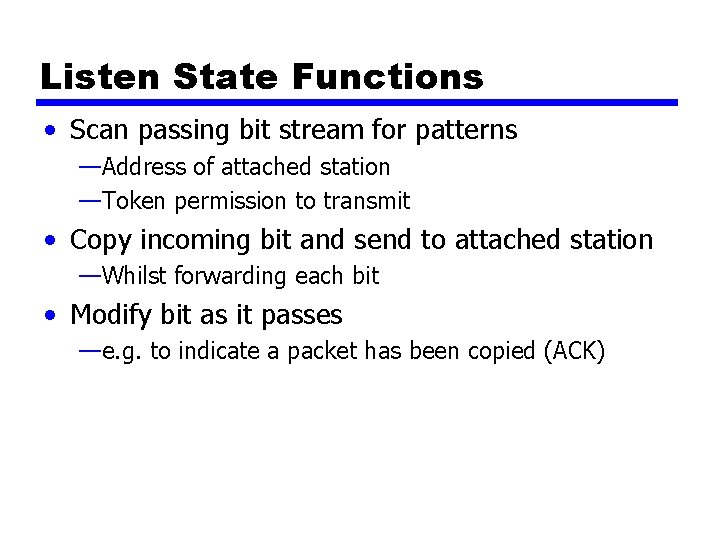
Listen State Functions • Scan passing bit stream for patterns —Address of attached station —Token permission to transmit • Copy incoming bit and send to attached station —Whilst forwarding each bit • Modify bit as it passes —e. g. to indicate a packet has been copied (ACK)

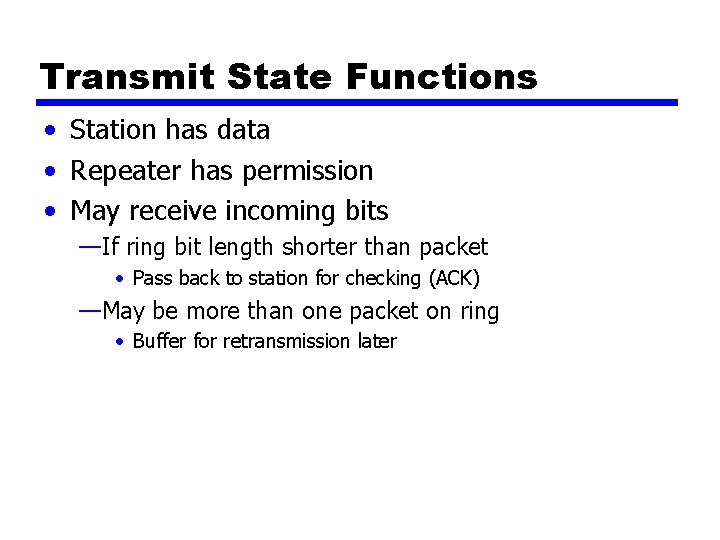
Transmit State Functions • Station has data • Repeater has permission • May receive incoming bits —If ring bit length shorter than packet • Pass back to station for checking (ACK) —May be more than one packet on ring • Buffer for retransmission later

Bypass State • Signals propagate past repeater with no delay (other than propagation delay) • Partial solution to reliability problem (see later) • Improved performance

Ring Repeater States

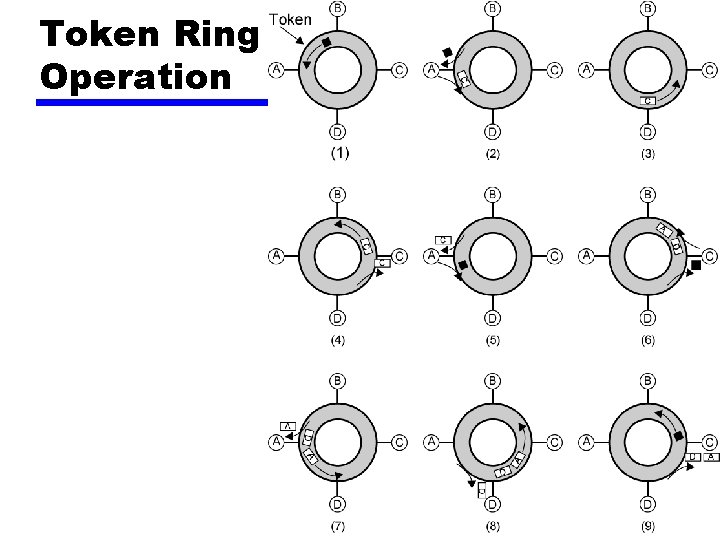
802. 5 MAC Protocol • • • Small frame (token) circulates when idle Station waits for token Changes one bit in token to make it SOF for data frame Append rest of data frame Frame makes round trip and is absorbed by transmitting station • Station then inserts new token when transmission has finished and leading edge of returning frame arrives • Under light loads, some inefficiency • Under heavy loads, round robin

Token Ring Operation

Dedicated Token Ring • • • Central hub Acts as switch Full duplex point to point link Concentrator acts as frame level repeater No token passing