Chapter 14 Windows Operating Systems Understanding Operating Systems





















- Slides: 70

Chapter 14 Windows Operating Systems Understanding Operating Systems, Fourth Edition

Objectives You will be able to describe: • The importance of MS-DOS in early Windows releases • The design goals for Windows operating systems • The role of the Memory Manager, especially the Virtual Memory Manager • The use of the Device, Processor, and Network Managers in recent versions of Windows • The role of the NT file system in file management Understanding Operating Systems, Fourth Edition 2

Objectives (continued) You will be able to describe: • The challenges for Windows system security today • How the current Windows user interface functions Understanding Operating Systems, Fourth Edition 3

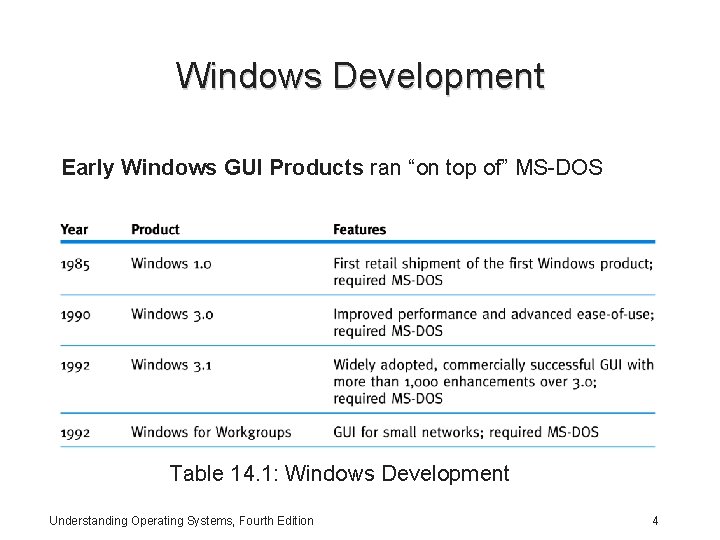
Windows Development Early Windows GUI Products ran “on top of” MS-DOS Table 14. 1: Windows Development Understanding Operating Systems, Fourth Edition 4

Windows Development (continued) • Windows for Workgroups: – First Windows product to accommodate the needs of network users – Could easily share directories, disks, and printers among several interconnected machines – Allowed personal intercommunication through e-mail and chat programs – Intended for small or mid-sized groups of PCs for small businesses or small departments of larger organizations Understanding Operating Systems, Fourth Edition 5

Operating Systems for Single Users • Disadvantages of running Windows on top of MS-DOS: – – Little built-in security Couldn’t perform multitasking Had no interprocess communication capability Written to work closely with the microcomputer’s hardware • Making it difficult to move OS to other platforms • Microsoft developed and released a succession of Windows OSs (not mere GUIs) to appeal to home and office users Understanding Operating Systems, Fourth Edition 6

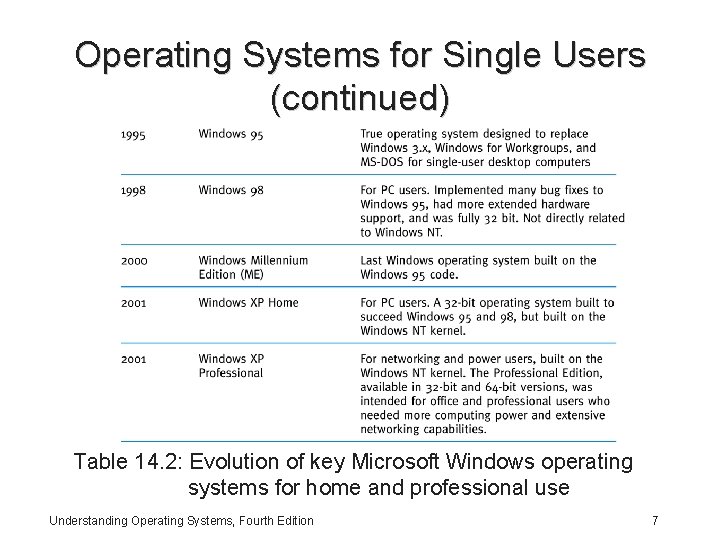
Operating Systems for Single Users (continued) Table 14. 2: Evolution of key Microsoft Windows operating systems for home and professional use Understanding Operating Systems, Fourth Edition 7

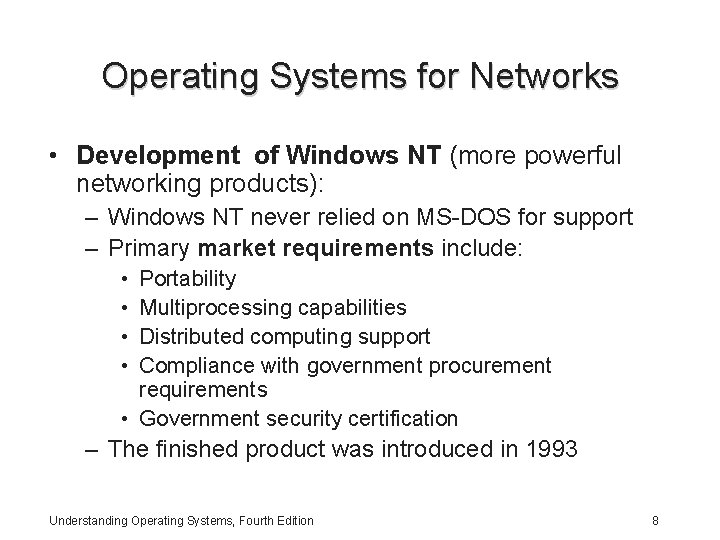
Operating Systems for Networks • Development of Windows NT (more powerful networking products): – Windows NT never relied on MS-DOS for support – Primary market requirements include: • • Portability Multiprocessing capabilities Distributed computing support Compliance with government procurement requirements • Government security certification – The finished product was introduced in 1993 Understanding Operating Systems, Fourth Edition 8

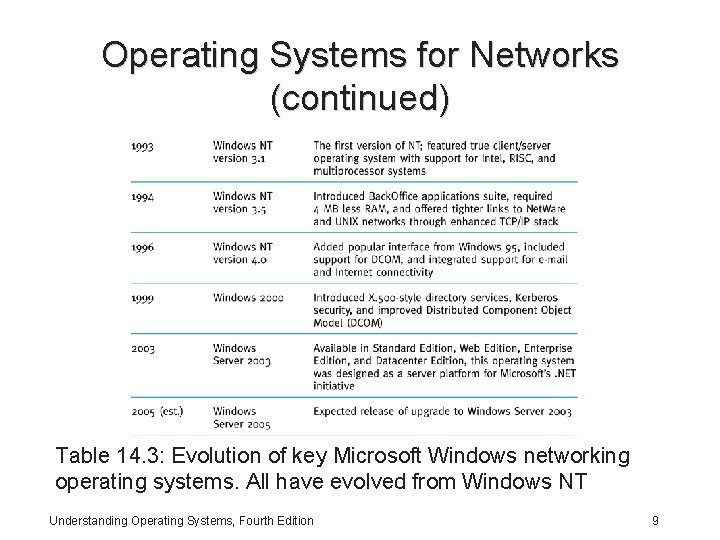
Operating Systems for Networks (continued) Table 14. 3: Evolution of key Microsoft Windows networking operating systems. All have evolved from Windows NT Understanding Operating Systems, Fourth Edition 9

Operating Systems for Networks (continued) • Microsoft offered Windows NT in several versions: – Windows NT Workstation for individuals needing a desktop operating system – Windows NT Server for small to medium-sized offices, Web servers, and off-site locations – Windows NT Server Enterprise Edition for larger and more complex networks Understanding Operating Systems, Fourth Edition 10

Operating Systems for Networks (continued) • In 1999, Windows NT name was changed to Windows 2000 and was available in four packages: – – Windows 2000 Professional Windows 2000 Server Windows 2000 Advanced Server Windows 2000 Datacenter Server • Designed for large data warehouses and other dataintensive business applications • Supported up to 64 GB of physical memory • Windows Server 2003 was also released with these same four packages plus a Web edition Understanding Operating Systems, Fourth Edition 11

Design Goals • To accommodate various needs of its users and to optimize resources, the Windows design team identified five design goals: – – – Extensibility Portability Reliability Compatibility Performance Understanding Operating Systems, Fourth Edition 12

Extensibility • Allows the system to be easily enhanced • To ensure the integrity of code, designers separated operating system functions into: – Privileged executive process (kernel mode) • Refers to a processor’s mode of operation in which all machine instructions are allowed • System memory is accessible – Nonprivileged processes “protected subsystems” (user mode): • Certain instructions are not allowed • System memory isn’t accessible Understanding Operating Systems, Fourth Edition 13

Extensibility (continued) • Windows designers also included four more features to ensure extensibility: – Modular structure so new components can be added to the executive process – Objects, a group of abstract data types manipulated by a special set of services • Allow system resources to be managed uniformly – Drivers for new file systems, devices, and networks that can be added to the system at any time – Remote procedure call • Allows an application to call remote services regardless of their location on the network Understanding Operating Systems, Fourth Edition 14

Portability • Ability to operate on different machines that are based on different processors or configurations with a minimum amount of recoding • To achieve this goal, Windows development followed certain guidelines: – Written in a standardized, high-level language available in all machines – System accommodated hardware to which it was expected to be ported – Minimized code that interacted directly with the hardware — to reduce incompatibility errors Understanding Operating Systems, Fourth Edition 15

Portability (continued) – Isolation of all hardware-dependent code into modules - that could be easily modified whenever the operating system was ported • Windows NT and successors have the following features: – Modular code – Much of Windows is written in C – Contains a hardware abstraction layer (HAL) • A dynamic-link library that provides isolation from hardware dependencies furnished by different vendors Understanding Operating Systems, Fourth Edition 16

Reliability • Refers to the robustness of a system and its ability to protect itself and its users from accidental or deliberate damage by user programs • Following features strengthen the system: – Structured exception handling – Modular design – NTFS File System (NT File System) which can recover from all types of errors – U. S. government-certifiable security architecture – Virtual memory strategy Understanding Operating Systems, Fourth Edition 17

Compatibility • Refers to an operating system’s ability to execute programs written for other operating systems or for earlier versions of the same system – Use of protected subsystems • Provides execution of applications that are different from its primary programming interface – Provides source-level compatibility with POSIX applications – Recent versions of Windows support already-existing file systems, e. g. , MS-DOS FAT, CDFS, and NTFS – Built-in verification of important hardware and software Understanding Operating Systems, Fourth Edition 18

Performance • Several features that help Windows achieve good performance levels include: – Testing and optimization of system calls, page faults, and other crucial processes – Incorporation of local procedure call (LPC) — to guarantee fast communication among the protected subsystems – Speed of frequently used system services is maximized – Critical elements of Windows’ networking software built into privileged portion of operating system Understanding Operating Systems, Fourth Edition 19

Memory Management • Every operating system uses its own view of physical memory and makes its application programs access memory in specified ways • When physical memory becomes full, the Virtual Memory Manager pages some of the memory contents to disk, freeing physical memory for other processes • Challenge for all Windows OSs: To run application programs written for Windows, MSDOS, or POSIX without programs crashing into each other’s memory Understanding Operating Systems, Fourth Edition 20

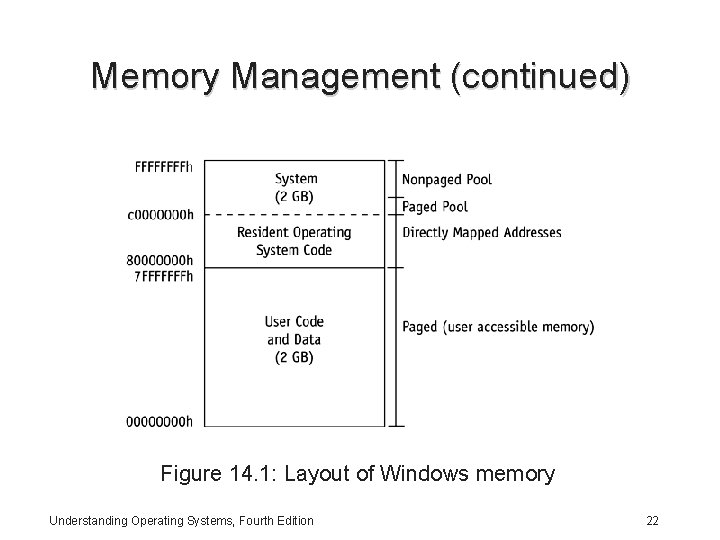
Memory Management (continued) Memory layout in recent versions of Windows: • Operating system resides in high virtual memory and the user’s code and data reside in low virtual memory • User process can’t read or write to system memory directly • All user-accessible memory can be paged to disk, as can the segment of system memory labeled paged pool • Segment of system memory labeled nonpaged pool is never paged to disk Understanding Operating Systems, Fourth Edition 21

Memory Management (continued) Figure 14. 1: Layout of Windows memory Understanding Operating Systems, Fourth Edition 22

User-Mode Features • VM Manager allows user-mode subsystems to share memory efficiently • Provides services that a process can use to manage its virtual memory in the following ways: – – – Allocate memory in two stages Read and/or write protection for virtual memory Lock virtual pages in physical memory Retrieve information about virtual pages Protect virtual pages Rewrite virtual pages to disk Understanding Operating Systems, Fourth Edition 23

Virtual Memory Implementation • Virtual Memory Manager relies on: – Address space management – Paging techniques • Address Space Management: – Upper half of the virtual address space is accessible only to kernel-mode processes – Code in the lower part of this section, kernel code and data, is never paged out of memory Understanding Operating Systems, Fourth Edition 24

Paging • Pager: Part of VM manager that transfers pages between page frames in memory and disk storage and is a complex combination of: – Software policies • Determine when to bring a page into memory and where to put it – Hardware mechanisms • Include the exact manner in which the VM Manager translates virtual addresses into physical addresses • Pager is not portable • Windows keeps this code small and well isolated Understanding Operating Systems, Fourth Edition 25

Paging (continued) • Paging policies dictate how and when paging is done and are composed of: – Fetch policy • Determines when the pager copies a page from disk to memory – Placement policy • Determines where the virtual page is loaded in memory – Replacement policy • Determines which virtual page must be removed from memory to make room for a new page Understanding Operating Systems, Fourth Edition 26

Processor Management • Windows is a preemptive-multitasking, multithreaded operating system • Process in Windows NT-derived OS requires at least one thread of execution. By default, a process contains one thread, which is composed of: – A unique identifier – Contents of a volatile set of registers indicating processor’s state – Two stacks used during the thread’s execution – Private storage area used by subsystems and dynamic-link libraries Understanding Operating Systems, Fourth Edition 27

Processor Management (continued) Threads: • Thread components are called the thread’s context • Actual data forming this context varies from one processor to another • Kernel schedules threads for execution on a processor • The thread is what actually executes the code • The overhead incurred by a thread is minimal Understanding Operating Systems, Fourth Edition 28

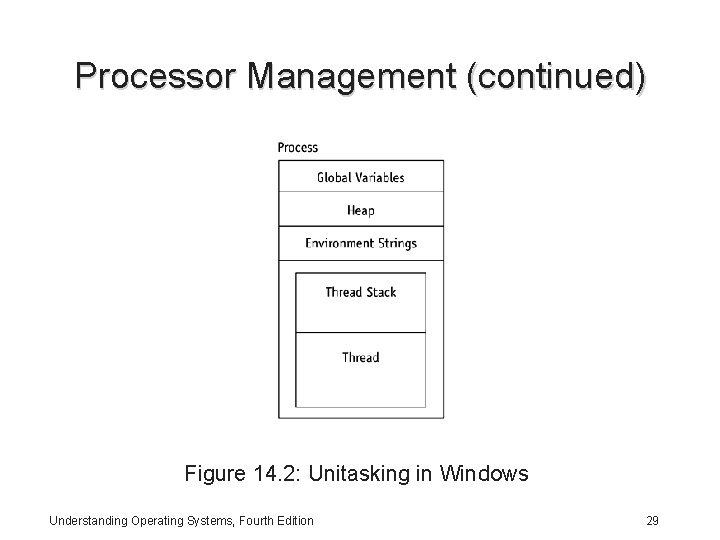
Processor Management (continued) Figure 14. 2: Unitasking in Windows Understanding Operating Systems, Fourth Edition 29

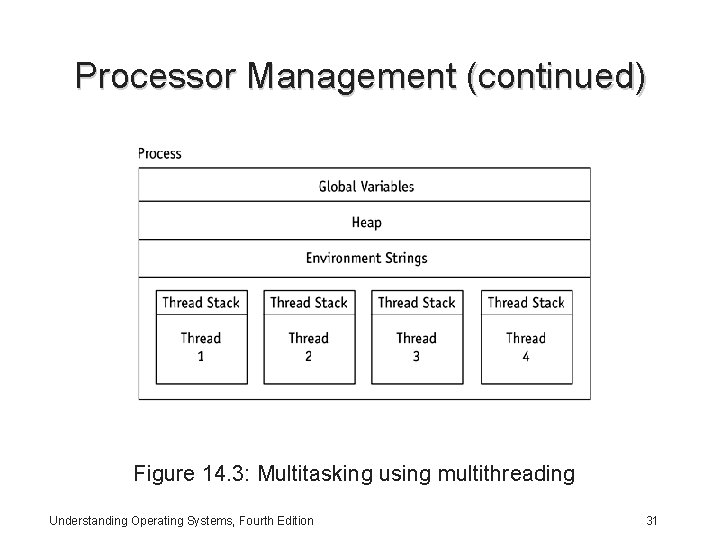
Processor Management (continued) Multithreading: • For systems with multiple processors, a process can have as many threads as there are CPUs available • All threads belonging to one process share its global variables, heap, and environment strings • Versions of Windows since NT include some synchronization mechanisms to avoid problems with multiple threads Understanding Operating Systems, Fourth Edition 30

Processor Management (continued) Figure 14. 3: Multitasking using multithreading Understanding Operating Systems, Fourth Edition 31

Device Management • The I/O system in Windows NT and its networking descendents was designed to provide following: – Multiple installable file systems including FAT, CDFS, and NTFS – Services to make device-driver development as easy as possible yet workable on multiprocessor systems – Ability for system administrators to add drivers to the system or remove them from the system dynamically – Fast I/O processing while allowing drivers to be written in high-level language – Mapped file I/O capabilities for image activation, file caching, and application use Understanding Operating Systems, Fourth Edition 32

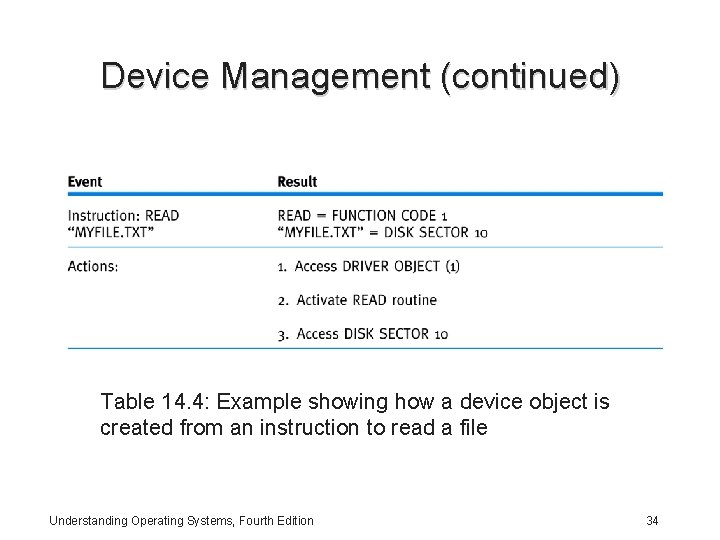
Device Management (continued) • The I/O system is packet driven i. e. , every I/O request is represented by an I/O request packet (IRP) – An IRP is a data structure that controls how the I/O operation is processed at each step • I/O Manager – Creates an IRP that represents each I/O operation – Passes the IRP to the appropriate driver – Disposes of the packet when the operation is complete Understanding Operating Systems, Fourth Edition 33

Device Management (continued) Table 14. 4: Example showing how a device object is created from an instruction to read a file Understanding Operating Systems, Fourth Edition 34

Device Management (continued) • Tasks of I/O Manager: – – Supplies code, common to different drivers Manages buffers for I/O requests Provides time-out support for drivers Records which installable file systems are loaded into the operating system – Provides flexible I/O facilities • Allow subsystems such as POSIX to implement their respective I/O application programming interfaces – Allows device drivers and file systems to be loaded dynamically based on the needs of the user Understanding Operating Systems, Fourth Edition 35

Device Management (continued) • Windows provides a device-independent model for I/O services – This model takes advantage of a concept called a “multilayered device driver” • Each device driver is made up of a standard set of routines including the following: – Initialization routine, dispatch routine, start I/O routine, completion routine, unload routine, error logging routine Understanding Operating Systems, Fourth Edition 36

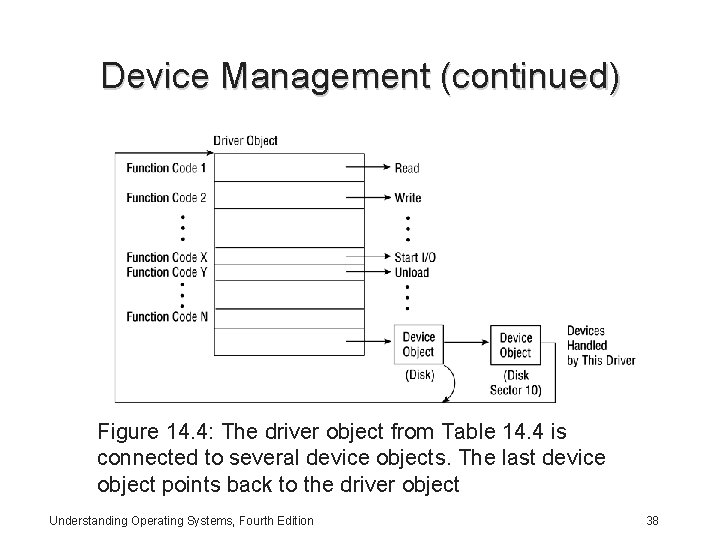
Device Management (continued) • I/O Manager must determine from the file object’s name which driver should be called to process the request of accessing a file. It uses: – Driver object: • Represents an individual driver in the system • I/O Manager creates it when a driver is loaded into the system • A driver object may have multiple device objects connected to it – Device object: • Represents a physical, logical, or virtual device on the system and describes its characteristics Understanding Operating Systems, Fourth Edition 37

Device Management (continued) Figure 14. 4: The driver object from Table 14. 4 is connected to several device objects. The last device object points back to the driver object Understanding Operating Systems, Fourth Edition 38

Device Management (continued) • The list of device objects represents the physical, logical, and virtual devices that are controlled by the driver • Advantages to representing devices and drivers with different objects: – Provides portability: Frees the I/O manager from having to know details about individual drivers • It just follows a pointer to locate a driver – Allows new drivers to be easily loaded – Easier to assign drivers to control additional or different devices if system configuration changes Understanding Operating Systems, Fourth Edition 39

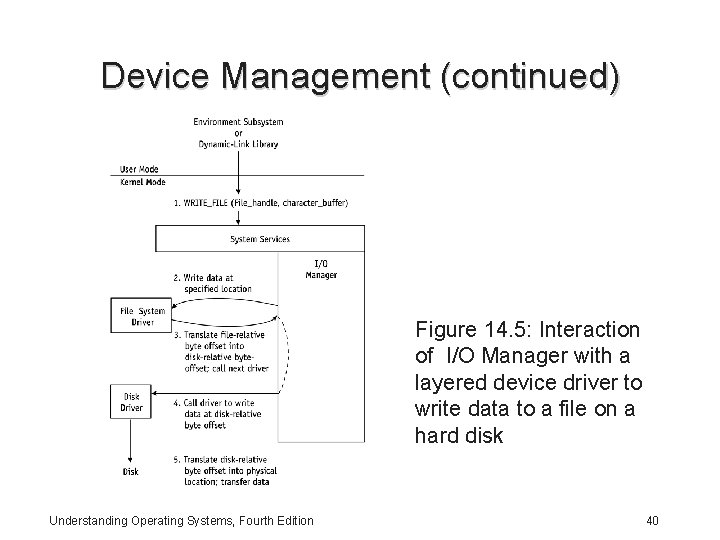
Device Management (continued) Figure 14. 5: Interaction of I/O Manager with a layered device driver to write data to a file on a hard disk Understanding Operating Systems, Fourth Edition 40

Device Management (continued) • The I/O Manager knows nothing about the file system • Overhead involved when the I/O Manager passes requests for information back and forth – Uses single-layer device driver approach for simple devices, e. g. , serial and parallel printer ports – Uses multilayered approach for more complicated devices, e. g. , hard drives • Almost all low-level I/O operations are asynchronous Understanding Operating Systems, Fourth Edition 41

File Management • Current versions of Windows are designed to be independent of the file system on which they operate • Windows supports multiple file systems for hard disks including: – MS-DOS’s FAT file system – 32 -bit FAT file system – NTFS • NTFS extends the capabilities of the FAT and FAT 32 file systems Understanding Operating Systems, Fourth Edition 42

File Management (continued) • NTFS extends the capabilities of the FAT and FAT 32 file systems by adding: – File system recovery – Ability to handle large storage media, on the order of approximately 17 billion gigabytes in size – Security features, including execute-only files – Unicode filenames – Support for the POSIX operating system environment – Features for future extensibility Understanding Operating Systems, Fourth Edition 43

File Management (continued) • Primary file handling concept in current versions of Windows is the virtual file • Programs perform I/O on virtual files, manipulating them by using file handles – An executive file object that represents all sources and destinations of I/O • Processes call native file object services such as those to read from or write to a file • I/O Manager directs these virtual file requests to real files, file directories, physical devices Understanding Operating Systems, Fourth Edition 44

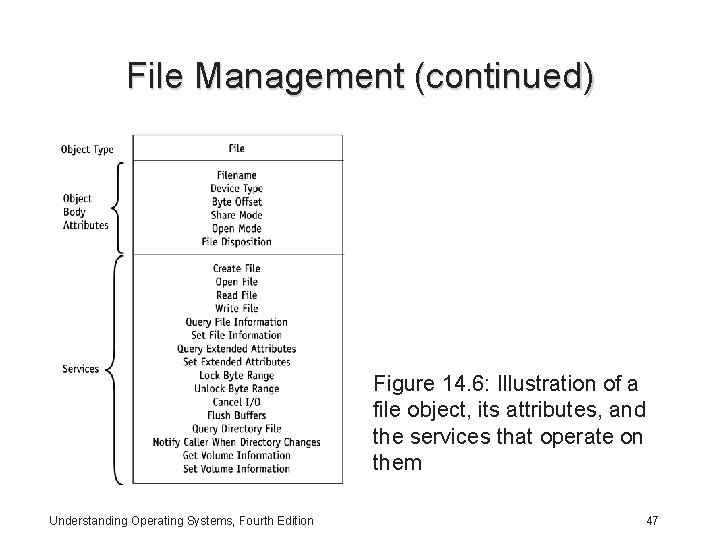
File Management (continued) • File objects: – – Have hierarchical names, Protected by object-based security Support synchronization Handled by object services • When opening a file, a process supplies the file’s name and the type of access required Understanding Operating Systems, Fourth Edition 45

File Management (continued) File objects: • Help bridge the gap – Between the characteristics of physical devices and directory structures, file system structures, and data formats • Provide a memory-based representation of shareable physical resources • Are created with a new set of handle-specific attributes each time a process opens a handle Understanding Operating Systems, Fourth Edition 46

File Management (continued) Figure 14. 6: Illustration of a file object, its attributes, and the services that operate on them Understanding Operating Systems, Fourth Edition 47

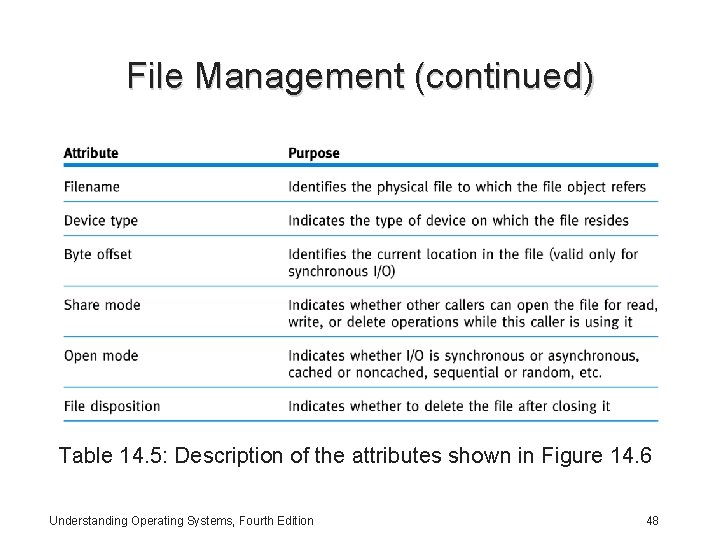
File Management (continued) Table 14. 5: Description of the attributes shown in Figure 14. 6 Understanding Operating Systems, Fourth Edition 48

File Management (continued) • Mapped file I/O is an important feature of the I/O system – Achieved through the cooperation of the I/O system and the VM Manager • Memory-mapped files exploit virtual memory capabilities • Cache manager uses mapped I/O to manage its memory-based cache • NTFS supports long filenames that can include spaces and special characters – Automatically shortens filenames when required Understanding Operating Systems, Fourth Edition 49

Network Management • Networking is an integral part of the Windows NTbased operating systems and provides services such as: – User accounts, resource security – Mechanisms used to implement communication between computers, such as with named pipes and mailslots • Named pipes provide a high-level interface for passing data between two processes regardless of their locations • Mailslots provide one-to-many and many-to-one communication mechanisms Understanding Operating Systems, Fourth Edition 50

MS-NET • Microsoft Networks(MS-NET) was released in 1984 and became the model for the NT Network Manager • Three MS-NET components: – Redirector – Server message block (SMB) protocol – Network server • MS-NET components were extensively refurbished and incorporated into Windows NT and later versions Understanding Operating Systems, Fourth Edition 51

MS-NET (continued) • Redirector: – Coded in the C programming language – Implemented as a loadable file system driver – Not dependent on the system’s hardware architecture – Function: To direct an I/O request from a user or application to the remote server that has the appropriate file or resource • A network can incorporate multiple redirectors Understanding Operating Systems, Fourth Edition 52

MS-NET (continued) SMB Protocol: • A high-level specification formatting messages to be sent across the network • Correlates to the application layer (layer 7) and the presentation layer (layer 6) of the OSI model • An API called Net. BIOS interface is used to pass I/O requests structured in the SMB format to a remote computer • Both SMB protocols and Net. BIOS API were adopted in several networking products before appearing in Windows Understanding Operating Systems, Fourth Edition 53

MS-NET (continued) Windows Server operating systems: • Written in C for complete compatibility with existing MS-NET and LAN manager SMB protocols • Implemented as loadable file system drivers • Have no dependency on the hardware architecture on which the operating system is running Understanding Operating Systems, Fourth Edition 54

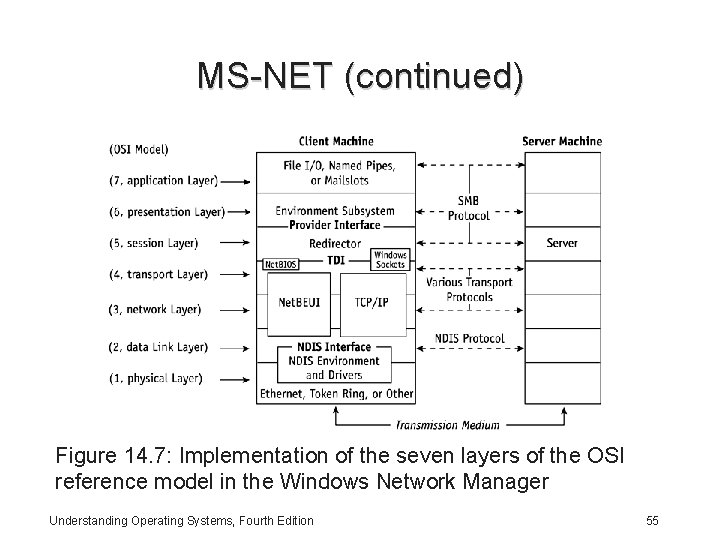
MS-NET (continued) Figure 14. 7: Implementation of the seven layers of the OSI reference model in the Windows Network Manager Understanding Operating Systems, Fourth Edition 55

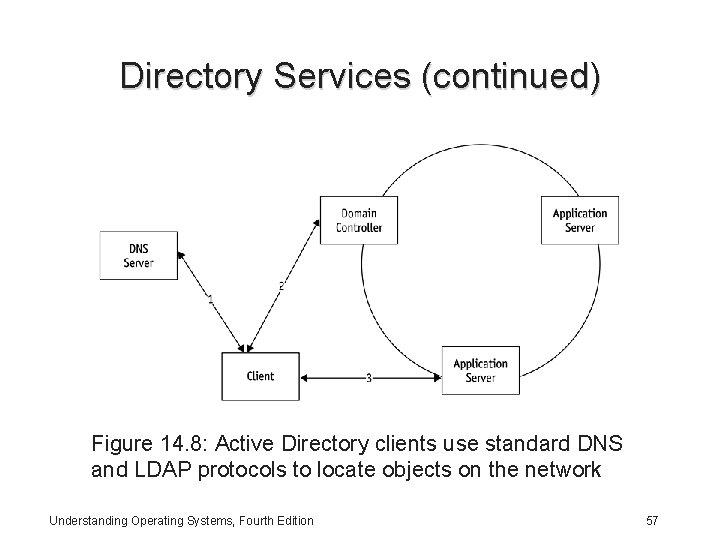
Directory Services • Active Directory: Database that stores all types of information so it can be a general-purpose directory service for a heterogeneous network – Built entirely around DNS and LDAP – Groups machines into administrative units called domains • Each domain gets a DNS domain name (e. g. , pitt. edu) • Each domain must have at least one domain controller • A domain can have more than one domain controller – Active Directory clients use standard DNS and LDAP protocols to locate objects on the network Understanding Operating Systems, Fourth Edition 56

Directory Services (continued) Figure 14. 8: Active Directory clients use standard DNS and LDAP protocols to locate objects on the network Understanding Operating Systems, Fourth Edition 57

Security Management • Windows network operating systems provide an object-based security model – A security object can represent any resource in the system: a file, device, process, program, or user – Allows administrators to give precise security access to specific objects in the system while allowing them to monitor and record how objects are used • Biggest concern in Windows OS: Need for aggressive patch management – To combat many viruses and worms that target these systems Understanding Operating Systems, Fourth Edition 58

Security Basics • U. S. Department of Defense has identified and categorized OS features into seven levels of security • To comply with the Class C 2 level of security, Windows 2000 and above include the following features: – – A secure logon facility Discretionary access control Auditing ability Memory protection Understanding Operating Systems, Fourth Edition 59

Security Basics (continued) • Windows strives to prevent access by unauthorized users by supporting a multilayered security system – Password management is the first layer of security – In NTFS, users encounter a second layer of security that deals directly with file access security – Windows makes distinctions between owners and groups – Users can decide what type of operations a person is allowed to perform on a file – Gives the user auditing capabilities that automatically keep track of who uses files and how Understanding Operating Systems, Fourth Edition 60

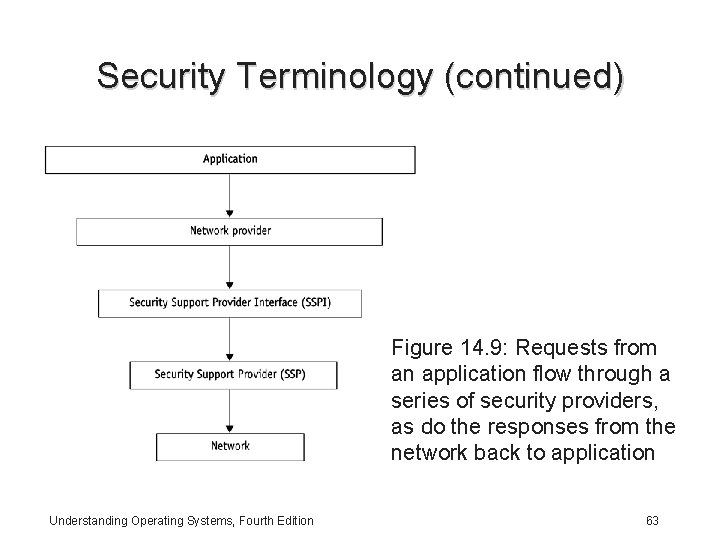
Security Terminology • Built-in security for recent Windows network OS is a necessary element for managers of Web servers and networks – Requires an authentication mechanism that allows a client to prove its identity to a server – Client needs to supply authorization information • Server uses it to determine which specific access rights have been given to client – Needs to provide data integrity using a variety of methods • Windows provide this with Kerberos security Understanding Operating Systems, Fourth Edition 61

Security Terminology (continued) Kerberos Security: • Provides authentication, data integrity, data privacy, and mutual authentication • Each domain has its own Kerberos server • Microsoft has implemented the standard Kerberos protocol • Microsoft has separated the users of distributed security services from their providers – Allows support for many options without creating unusable complexity Understanding Operating Systems, Fourth Edition 62

Security Terminology (continued) Figure 14. 9: Requests from an application flow through a series of security providers, as do the responses from the network back to application Understanding Operating Systems, Fourth Edition 63

User Interface • Desktop contains the icons for the tools and applications one can use to get work done – Users can use mouse, light pen, or stylus to move around the desktop • To start an application, users double-click an application icon or select it from the Start menu • To quit an application, they can select Exit from the File menu or click the “x” in the top-right corner of the window Understanding Operating Systems, Fourth Edition 64

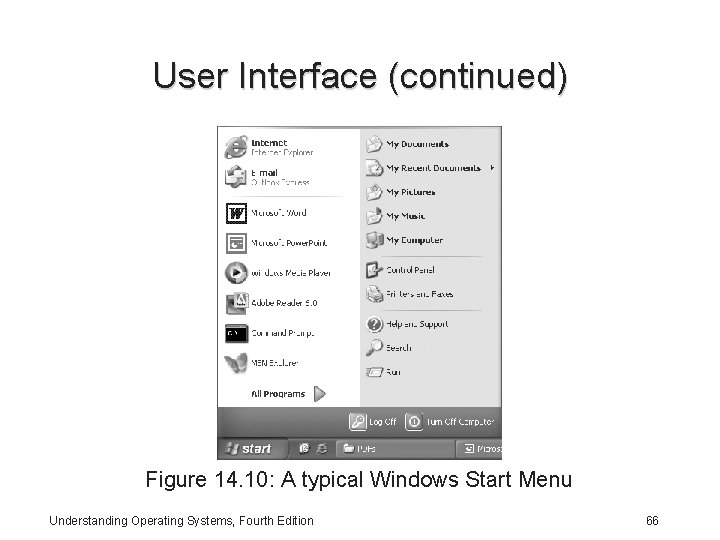
User Interface (continued) • Start Menu divides functions into logical groups and from here users access common functions including the following: – All Programs – My Documents, My Pictures, My Music, My Computer – Control Panel, Help and Support – Search, Run, Log Off, Turn Off Computer Understanding Operating Systems, Fourth Edition 65

User Interface (continued) Figure 14. 10: A typical Windows Start Menu Understanding Operating Systems, Fourth Edition 66

User Interface (continued) • The Windows Task Manager: – Opened by pressing and holding the Ctrl, Alt, and Delete keys – Allows user to view running applications and processes, and set the priorities of each – Allows user to view information about performance, networking, and other users logged into system • Windows Explorer: Contains directory and file display tools and a file-finding tool – Features a series of pull-down menus: File, Edit, View, Favorites, Tools, Help, etc. Understanding Operating Systems, Fourth Edition 67

User Interface (continued) • My Network Places: helps users identify and access network resources such as folders, printers, and connections to other nodes • Command interface that resembles MS-DOS is available from most Windows desktops • Keyboard shortcuts: e. g. , Ctrl+C for copy • Built-in input methods and fonts for many languages. – e. g. , Administrator can select one or several languages during installation • Windows also offers an on-screen keyboard Understanding Operating Systems, Fourth Edition 68

Summary • Current Windows operating systems incorporate ease-of-use with the technical power to operate a network across several existing platforms • Windows systems are designed to evolve modularly and consistently over time • Portability feature eases the difficulty of migrating OS to new hardware platforms • Security controls in Windows have helped OS gain inroads with organizations requiring consistent protection for their data and applications Understanding Operating Systems, Fourth Edition 69

Summary (continued) • Windows’ authentication models support new user interfaces from bank teller machines to fingerprint or retinal scanners • Allow the implementation of different security architectures, further extending the reach of Windows into the market • Require aggressive patch management to combat viruses and worms Understanding Operating Systems, Fourth Edition 70