Chapter 13 Wired LANs Ethernet 13 1 Copyright















- Slides: 40

Chapter 13 Wired LANs: Ethernet 13. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.

13— 11 IEEE STANDARDS In 1985, the Computer Society of the IEEE started a project, called Project 802, to set standards to enable intercommunication among equipment from a variety of manufacturers. Project 802 is a way of specifying functions of the physical layer and the data link layer of major LAN protocols. It is a way of specifying functions of the physical layer and the data link layer of major LAN protocols Topics discussed in this section: Data Link Layer Physical Layer 13. 2

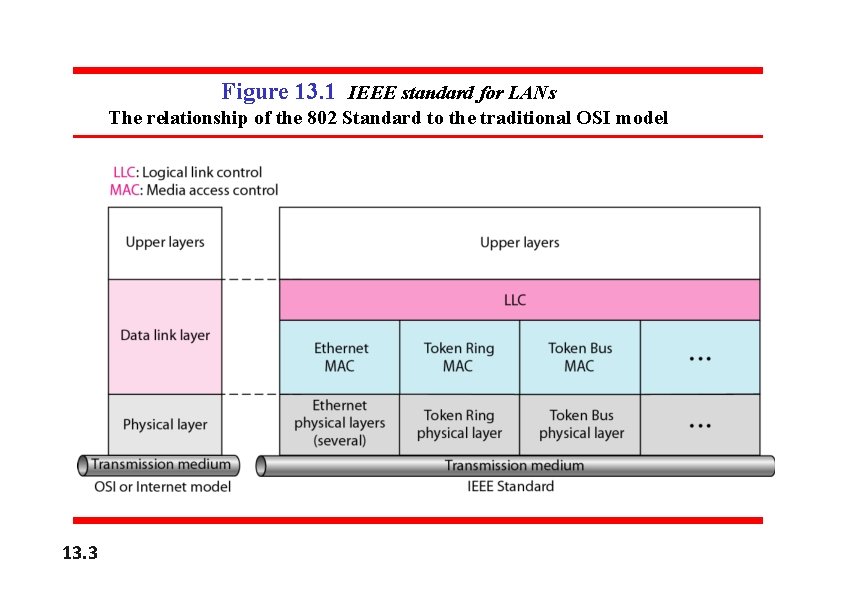
Figure 13. 1 IEEE standard for LANs The relationship of the 802 Standard to the traditional OSI model 13. 3

Data Link Layer The data link layer in the IEEE standard is divided into two sublayers: LLC and MAC. Data link control handles framing, flow control, and error control Logical Link Control (LLC) In IEEE Project 802, flow control, error control, and part of the framing duties are collected into one sublayer called the logical link control. Framing is handled in both the LLC sublayer and the MAC sublayer The LLC provides one single data link control protocol for all IEEE LANs. A single LLC protocol can provide interconnectivity between different LANs because it makes the MAC sublayer transparent.

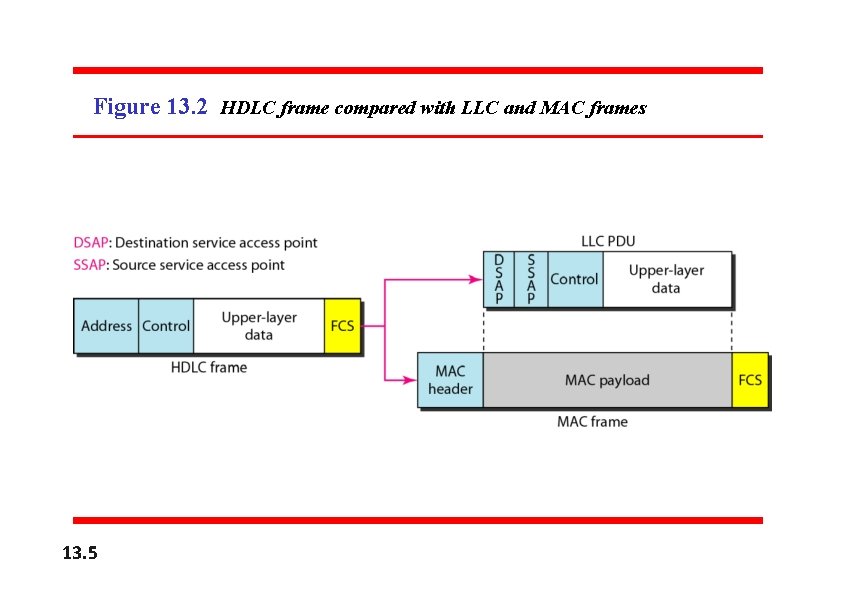
Figure 13. 2 HDLC frame compared with LLC and MAC frames 13. 5

Framing • LLC defines a protocol data unit (PDU) similar to that of HDLC. • The header contains a control field like the one in HDLC; this field is used for flow and error control. • The two other header fields define the upper-layer protocol at the source and destination that uses LLC. These fields are called the destination service access point (DSAP) and the source service access point (SSAP). • The other fields defined in a typical data link control protocol such as HDLC are moved to the MAC sublayer. • In other words, a frame defined in HDLC is divided into a PDU at the LLC sublayer and a frame at the MAC sublayer

Media Access Control (MAC) Multiple access methods includes random access, controlled access, and channelization. • IEEE Project 802 has created a sublayer called media access control that defines the specific access method for each LAN. • For example, it defines CSMA/CD as the media access method for Ethernet LANs and the token passing method for Token Ring and Token Bus LANs.

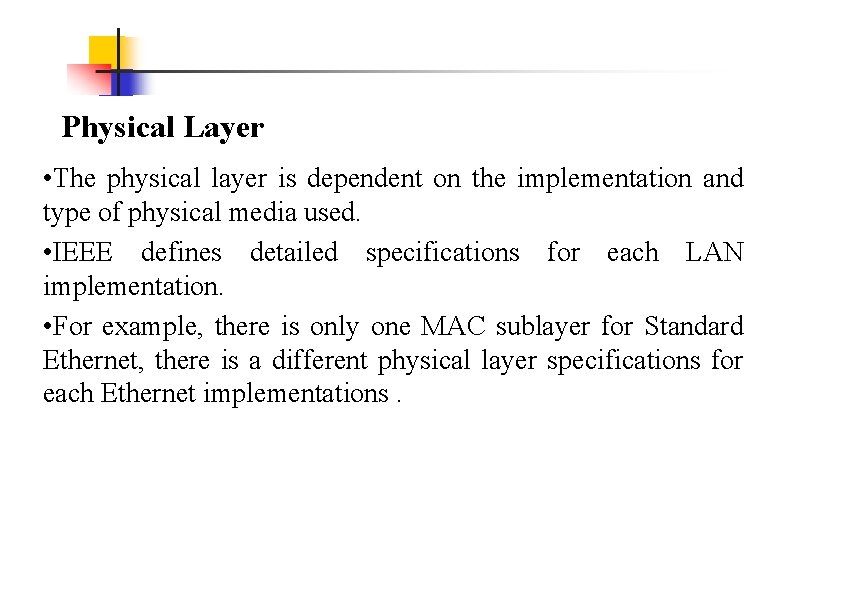
Physical Layer • The physical layer is dependent on the implementation and type of physical media used. • IEEE defines detailed specifications for each LAN implementation. • For example, there is only one MAC sublayer for Standard Ethernet, there is a different physical layer specifications for each Ethernet implementations.

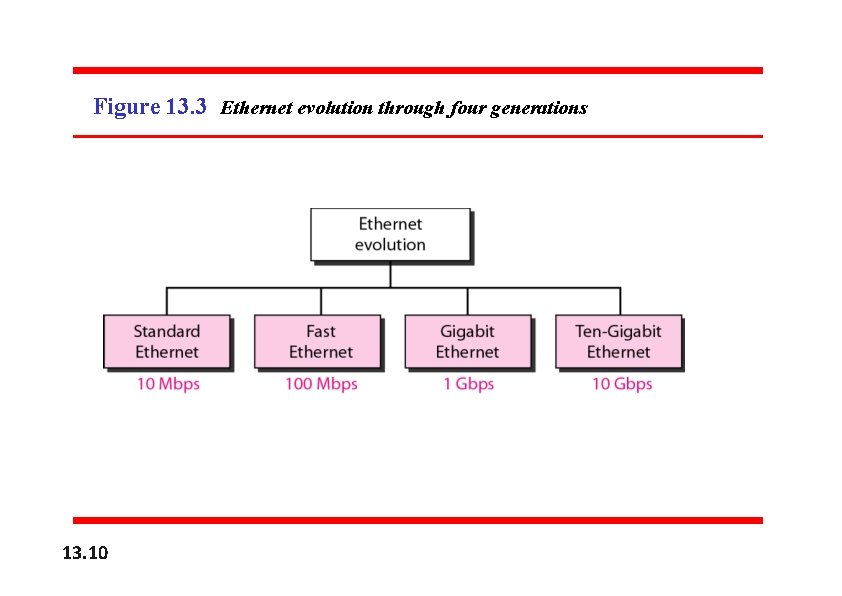
13 -2 STANDARD ETHERNET The original Ethernet was created in 1976 at Xerox’s The original Ethernet Center was created in 1976 Since at Xerox’s Alto Palo Alto Research (PARC). then, Palo it has Research Centerfour (PARC). Since then, it has gonediscuss throughthe four gone through generations. We briefly generations. We traditional) briefly discuss the Standard traditional) Standard (or Ethernet in this(orsection. Ethernet in this section. Topics discussed in this section: MAC Sublayer Physical Layer 13. 9

Figure 13. 3 Ethernet evolution through four generations 13. 10

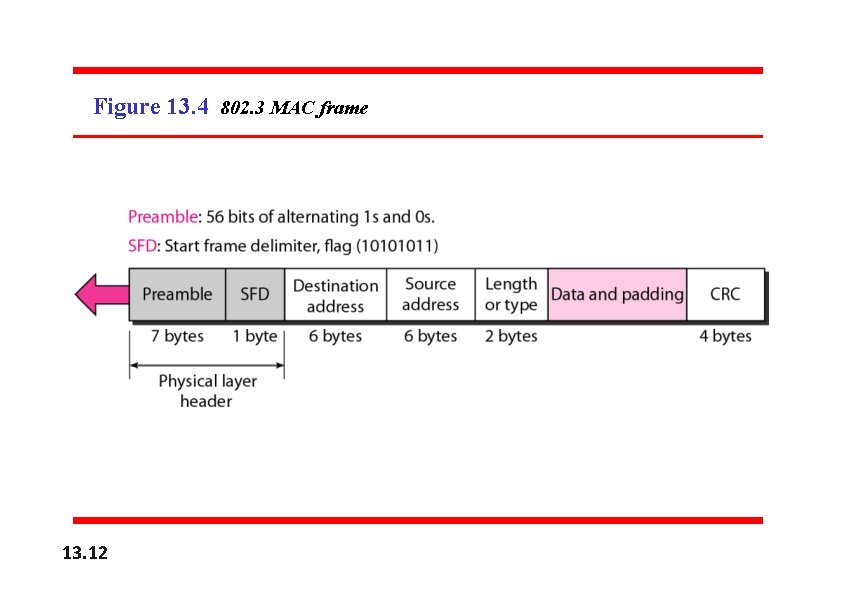
MAC Sublayer • In Standard Ethernet, the MAC sublayer governs the operation of the access method. • It also frames data received from the upper layer and passes them to the physical layer. Frame format • The Ethernet frame contains seven fields: preamble, SFD, DA, SA, length or type of protocol data unit (PDU), upper-layer data, and the CRC. • Ethernet does not provide any mechanism for acknowledging received frames, what is known as an unreliable medium.

Figure 13. 4 802. 3 MAC frame 13. 12

q. Preamble. The first field of the 802. 3 frame contains 7 bytes (56 bits) of alternating 0 s and 1 s that alerts the receiving system to the coming frame and enables it to synchronize its input timing. The pattern provides only an alert and a timing pulse. The 56 -bit pattern allows the stations to miss some bits at the beginning of the frame. The preamble is actually added at the physical layer and is not (formally) part of the frame. q Start frame delimiter (SFD). The second field (1 byte: 10101011) signals the beginning of the frame. The SFD warns the station or stations that this is the last chance for synchronization. The last 2 bits is 11 and alerts the receiver that the next field is the destination address. ❏ Destination address (DA). The DA field is 6 bytes and contains the physical address of the destination station or stations to receive the packet. We will discuss addressing shortly. ❏ Source address (SA). The SA field is also 6 bytes and contains the physical address of the sender of the packet. We will discuss addressing shortly. ❏ Length or type. This field is defined as a type field or length field. The original Ethernet used this field as the type field to define the upper-layer protocol using the MAC frame. The IEEE standard used it as the length field to define the number of bytes in the data field. Both uses are common today. ❏ Data. This field carries data encapsulated from the upper-layer protocols. It is a minimum of 46 and a maximum of 1500 bytes, as we will see later. ❏ CRC. The last field contains error detection information, in this case a CRC-32

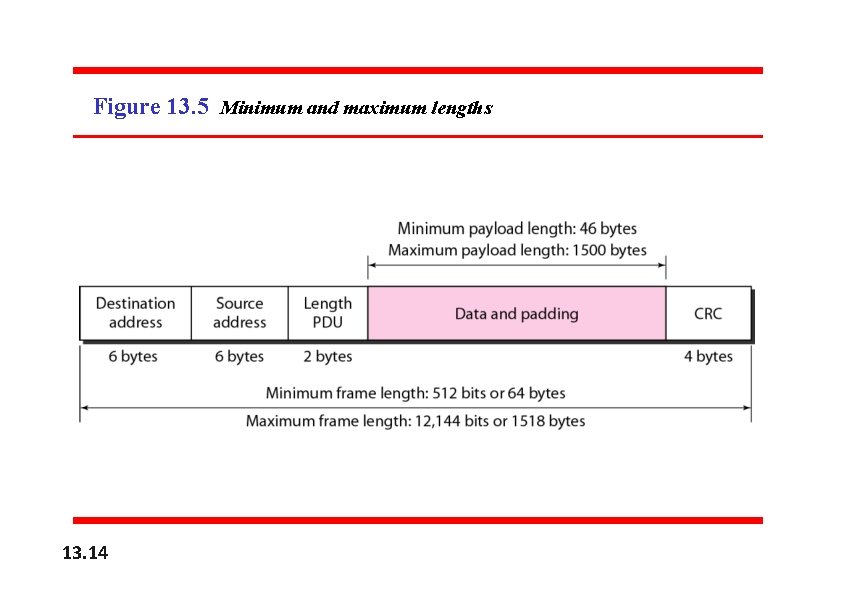
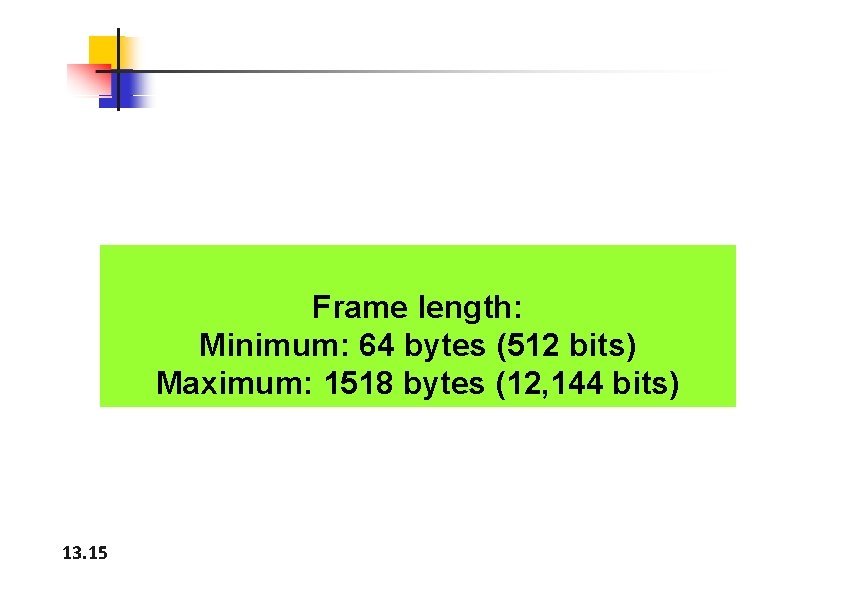
Figure 13. 5 Minimum and maximum lengths 13. 14

Frame length: Minimum: 64 bytes (512 bits) Maximum: 1518 bytes (12, 144 bits) 13. 15

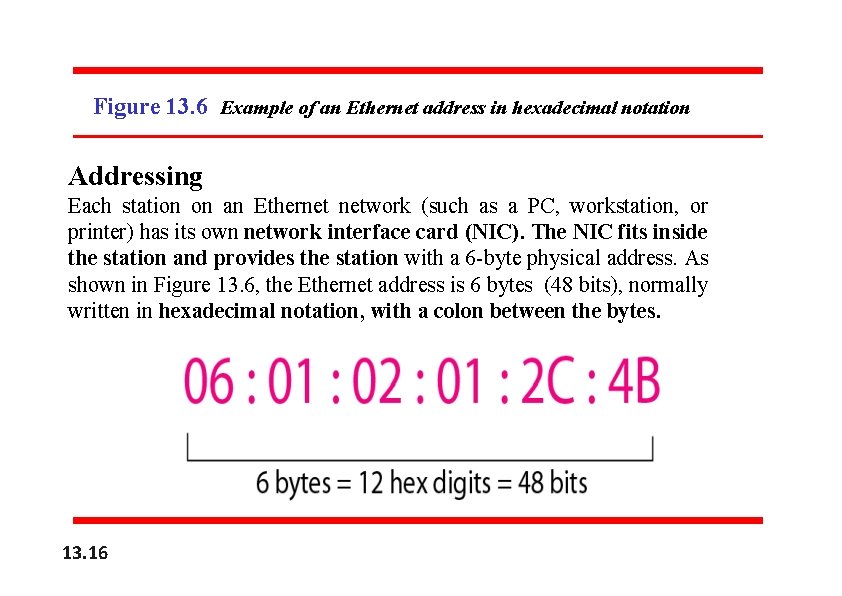
Figure 13. 6 Example of an Ethernet address in hexadecimal notation Addressing Each station on an Ethernet network (such as a PC, workstation, or printer) has its own network interface card (NIC). The NIC fits inside the station and provides the station with a 6 -byte physical address. As shown in Figure 13. 6, the Ethernet address is 6 bytes (48 bits), normally written in hexadecimal notation, with a colon between the bytes. 13. 16

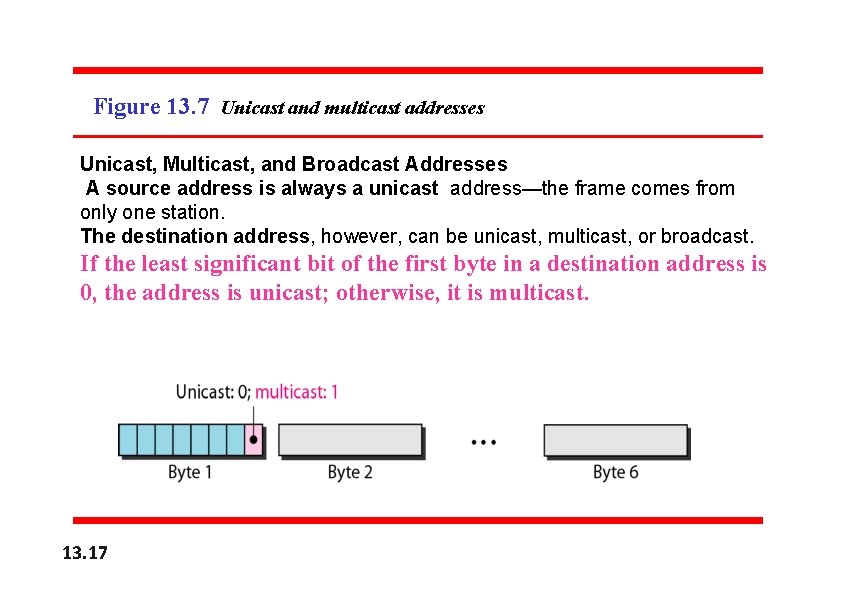
Figure 13. 7 Unicast and multicast addresses Unicast, Multicast, and Broadcast Addresses A source address is always a unicast address—the frame comes from only one station. The destination address, however, can be unicast, multicast, or broadcast. If the least significant bit of the first byte in a destination address is 0, the address is unicast; otherwise, it is multicast. 13. 17

v. A unicast destination address defines only one recipient; the relationship between the sender and the receiver is one-to-one. v. A multicast destination address defines a group of addresses; the relationship between the sender and the receivers is one-to-many. v. The broadcast address is a special case of the multicast address; the recipients are all the stations on the LAN. A broadcast destination address is forty-eight 1 s. The broadcast destination address is a special case of the multicast address in which all bits are 1 s. 13. 18

Example 13. 1 Define the type of the following destination addresses: a 4 A: 30: 10: 21: 10: 1 b 47: 20: 1 B: 2 E: 08: EE c. FF: FF: FF: FF Solution To find the type of the address, we need to look at the second hexadecimal digit from the left. If it is even, the address is unicast. If it is odd, the address is multicast. If all digits are F’s, the address is broadcast. Therefore, we have the following: a. This is a unicast address because A in binary is 1010. b. This is a multicast address because 7 in binary is 0111. c. This is a broadcast address because all digits are F’s. 13. 19

Example 13. 2 Show the address 47: 20: 1 B: 2 E: 08: EE is sent out on line. Solution The address is sent left-to-right, byte by byte; for each byte, it is sent right-to-left, bit by bit, as shown below: 13. 20

Figure 13. 8 Categories of Standard Ethernet 13. 21

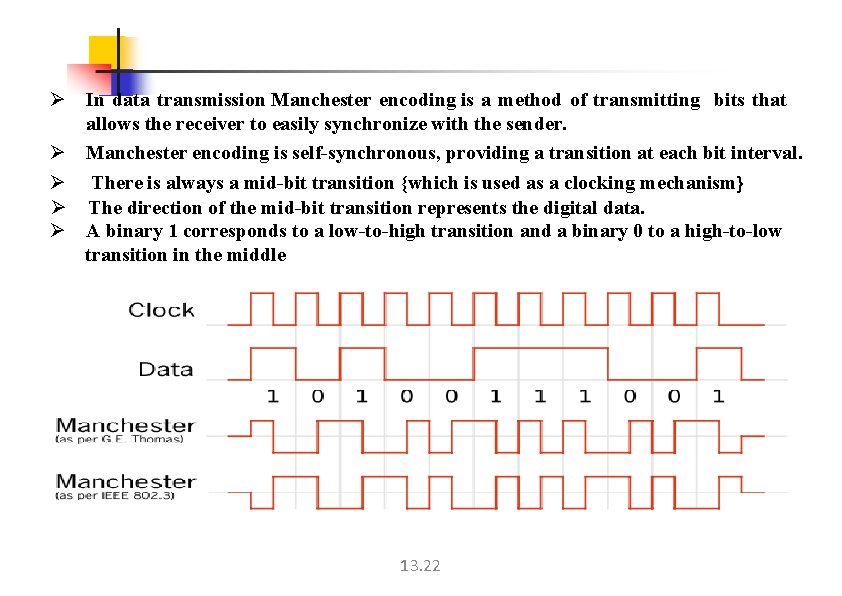
Ø In data transmission Manchester encoding is a method of transmitting bits that allows the receiver to easily synchronize with the sender. Ø Manchester encoding is self-synchronous, providing a transition at each bit interval. Ø There is always a mid-bit transition {which is used as a clocking mechanism} Ø The direction of the mid-bit transition represents the digital data. Ø A binary 1 corresponds to a low-to-high transition and a binary 0 to a high-to-low transition in the middle 13. 22

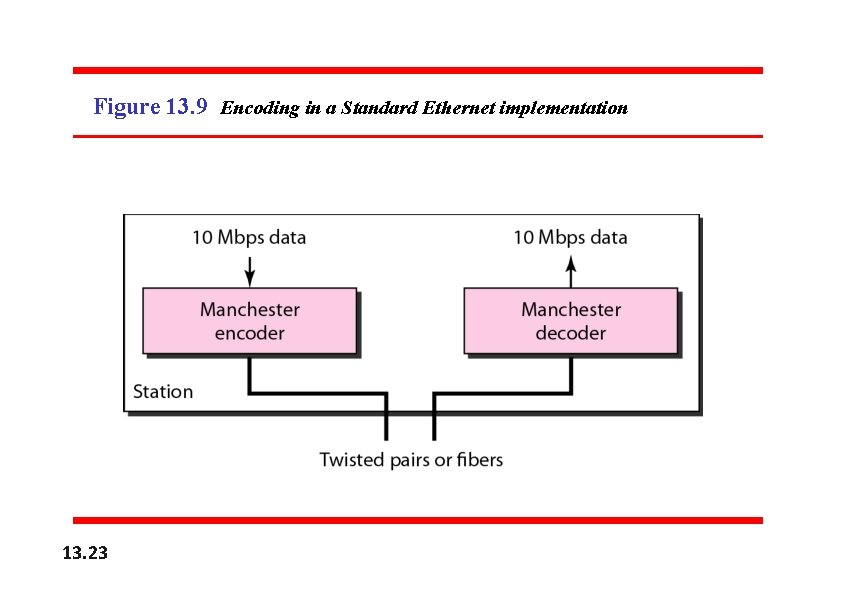
Figure 13. 9 Encoding in a Standard Ethernet implementation 13. 23

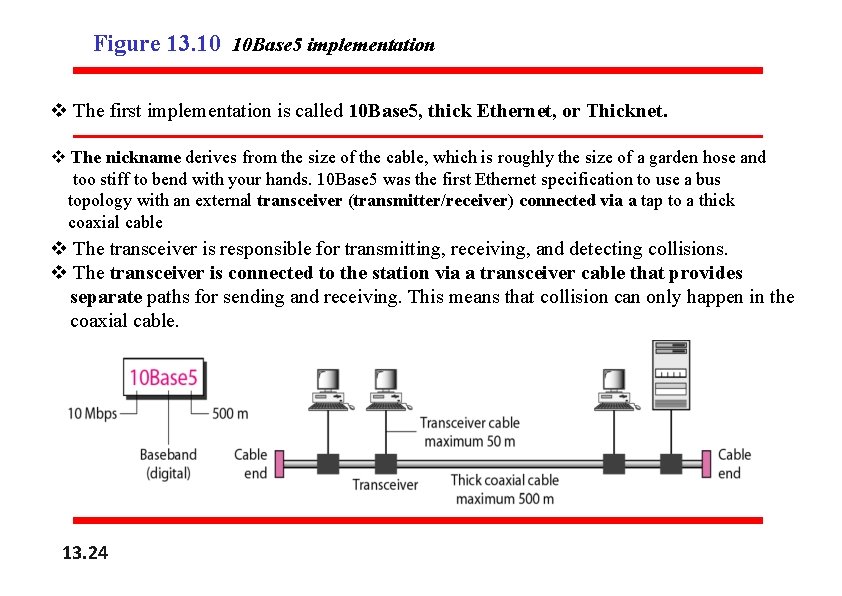
Figure 13. 10 10 Base 5 implementation v The first implementation is called 10 Base 5, thick Ethernet, or Thicknet. v The nickname derives from the size of the cable, which is roughly the size of a garden hose and too stiff to bend with your hands. 10 Base 5 was the first Ethernet specification to use a bus topology with an external transceiver (transmitter/receiver) connected via a tap to a thick coaxial cable v The transceiver is responsible for transmitting, receiving, and detecting collisions. v The transceiver is connected to the station via a transceiver cable that provides separate paths for sending and receiving. This means that collision can only happen in the coaxial cable. 13. 24

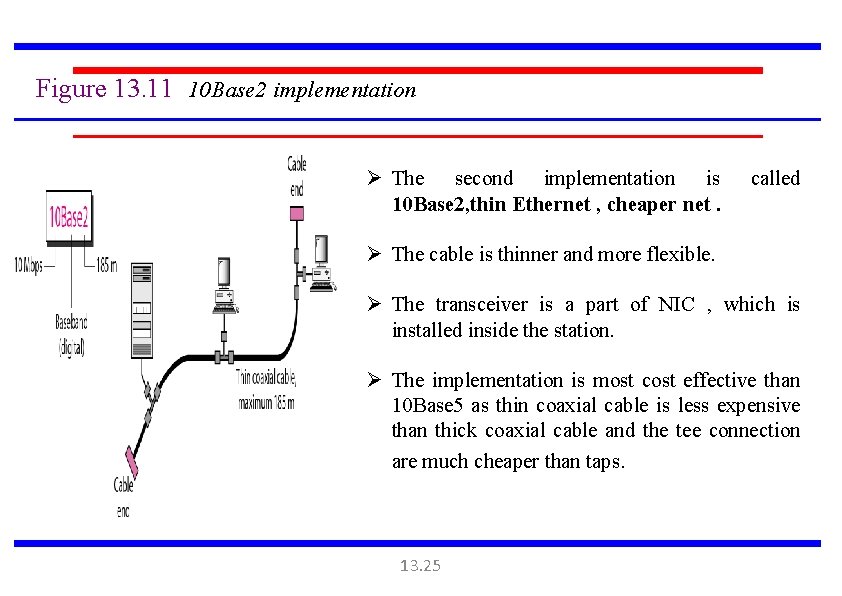
Figure 13. 11 10 Base 2 implementation Ø The second implementation is 10 Base 2, thin Ethernet , cheaper net. called Ø The cable is thinner and more flexible. Ø The transceiver is a part of NIC , which is installed inside the station. Ø The implementation is most cost effective than 10 Base 5 as thin coaxial cable is less expensive than thick coaxial cable and the tee connection are much cheaper than taps. 13. 25

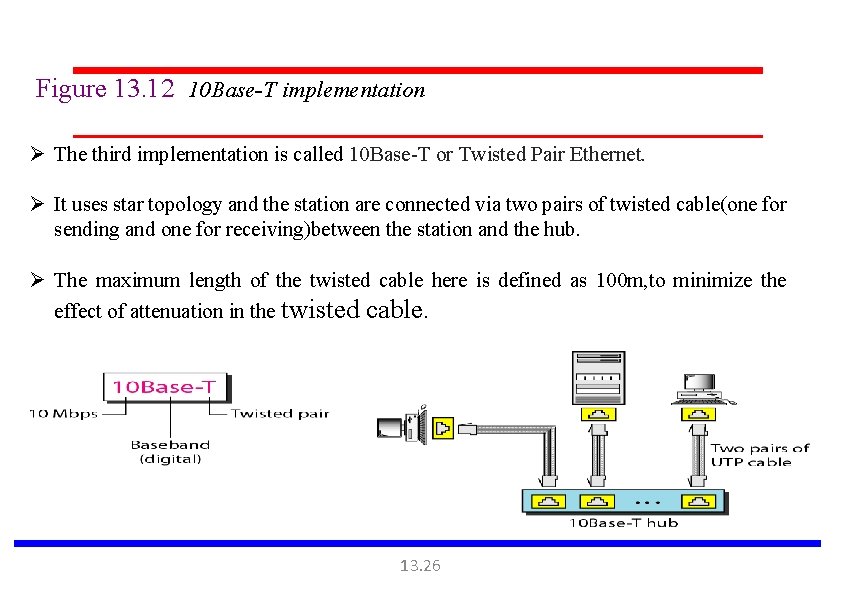
Figure 13. 12 10 Base-T implementation Ø The third implementation is called 10 Base-T or Twisted Pair Ethernet. Ø It uses star topology and the station are connected via two pairs of twisted cable(one for sending and one for receiving)between the station and the hub. Ø The maximum length of the twisted cable here is defined as 100 m, to minimize the effect of attenuation in the twisted cable. 13. 26

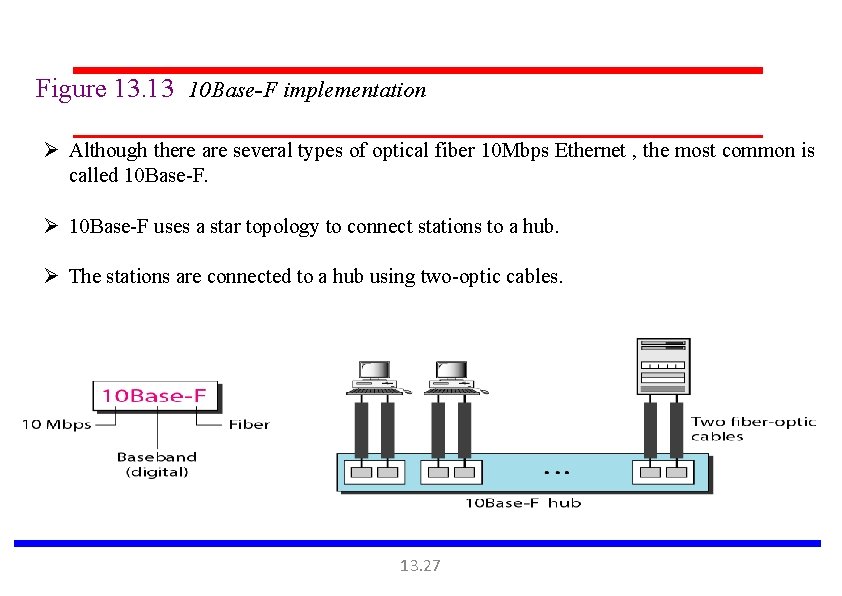
Figure 13. 13 10 Base-F implementation Ø Although there are several types of optical fiber 10 Mbps Ethernet , the most common is called 10 Base-F. Ø 10 Base-F uses a star topology to connect stations to a hub. Ø The stations are connected to a hub using two-optic cables. 13. 27

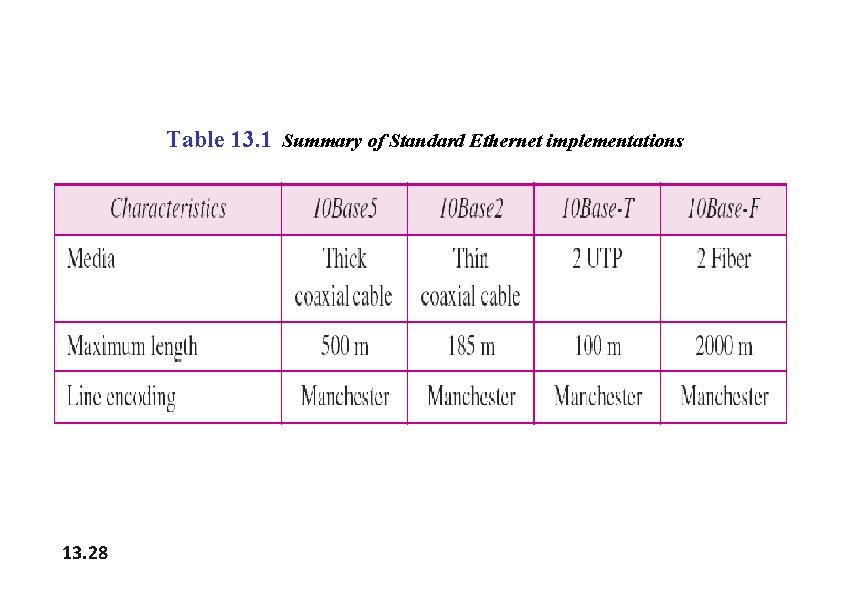
Table 13. 1 Summary of Standard Ethernet implementations 13. 28

13 --33 CHANGES IN THE STANDARD The 10 -Mbps Standard Ethernet has gone through several changes before moving to the higher data rates. These changes actually opened the road to the evolution of the Ethernet to become compatible with other high-data-rate LANs. Topics discussed in this section: Bridged Ethernet Switched Ethernet Full-Duplex Ethernet 13. 29

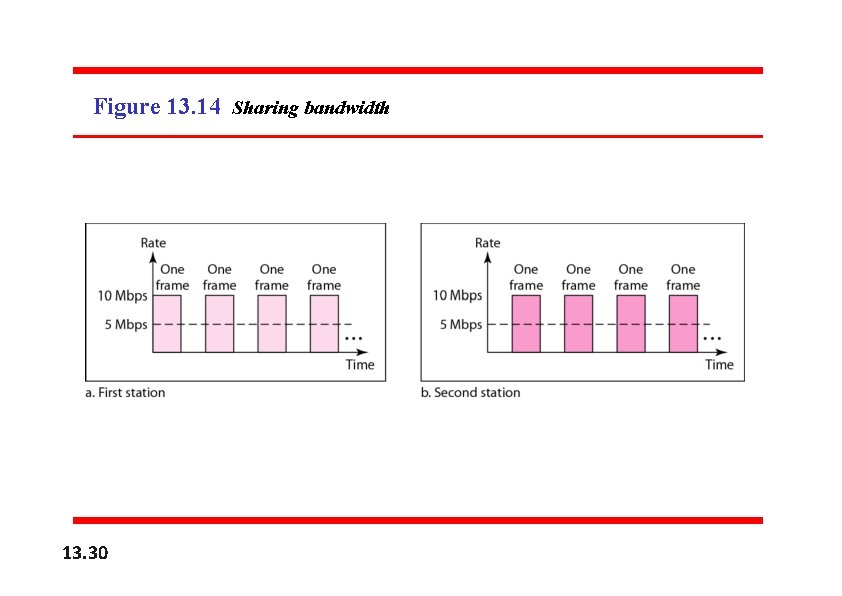
Figure 13. 14 Sharing bandwidth 13. 30

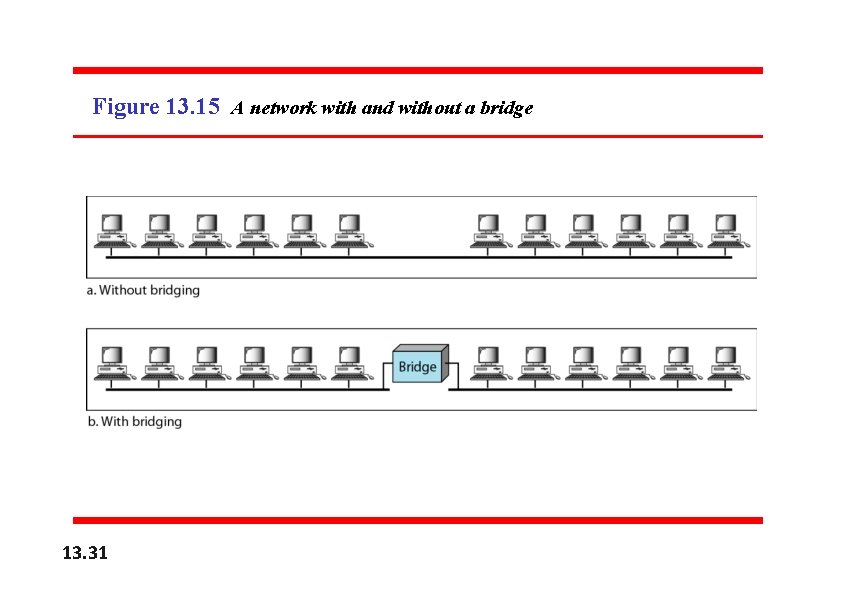
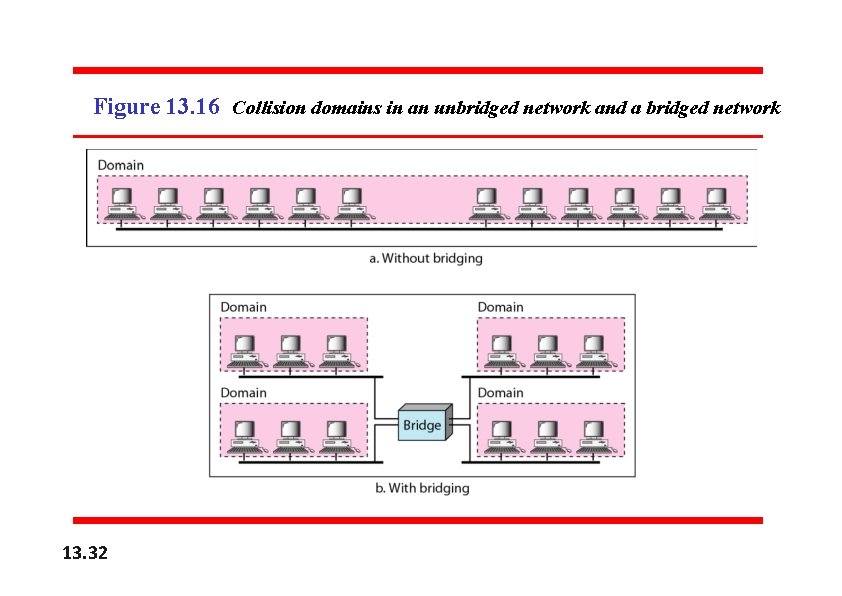
Figure 13. 15 A network with and without a bridge 13. 31

Figure 13. 16 Collision domains in an unbridged network and a bridged network 13. 32

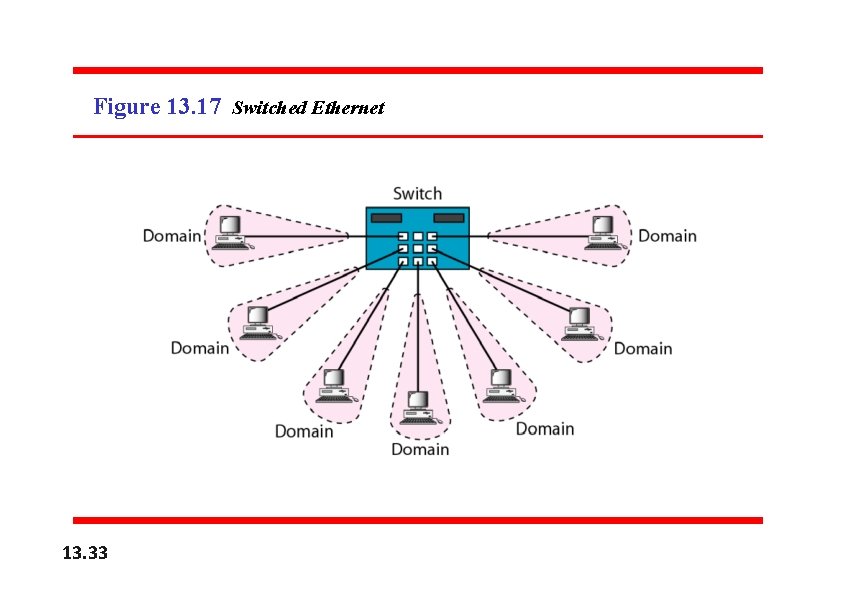
Figure 13. 17 Switched Ethernet 13. 33

Figure 13. 18 Full-duplex switched Ethernet 13. 34

13 -4 FAST ETHERNET Fast Ethernet was designed to compete with LAN protocols such as FDDI or Fiber Channel. IEEE created Fast Ethernet under the name 802. 3 u. Fast Ethernet is backward-compatible with Standard Ethernet, but it can transmit data 10 times faster at a rate of 100 Mbps. Topics discussed in this section: MAC Sublayer Physical Layer GOALS OF FAST ETHERNET: Ø Upgrade the data rate to 100 Mbps. Ø Make it compatible with standard Ethernet. Ø Keep the same 48 bit-address. Ø Keep the same frame format. Ø Keep the same minimum and maximum 13. 35 frame lengths.

Figure 13. 19 Fast Ethernet topology 13. 36

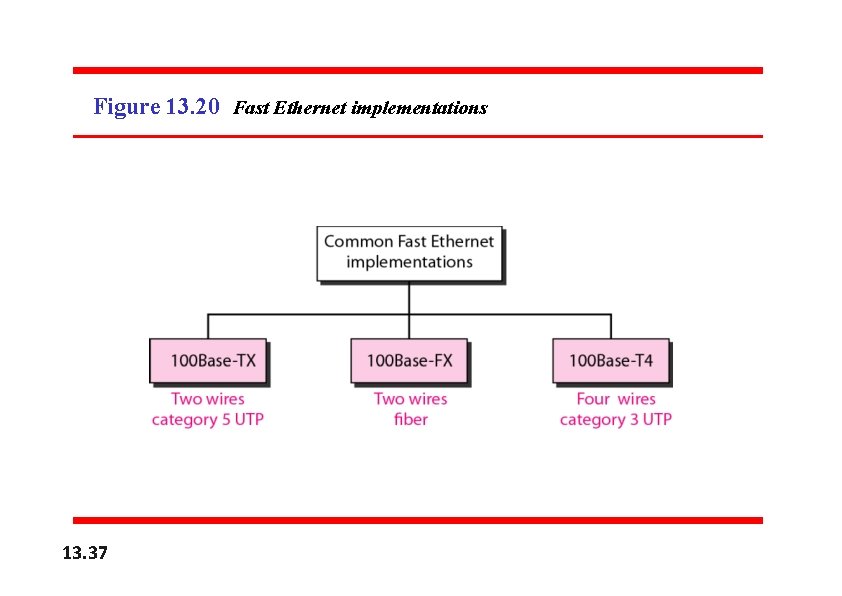
Figure 13. 20 Fast Ethernet implementations 13. 37

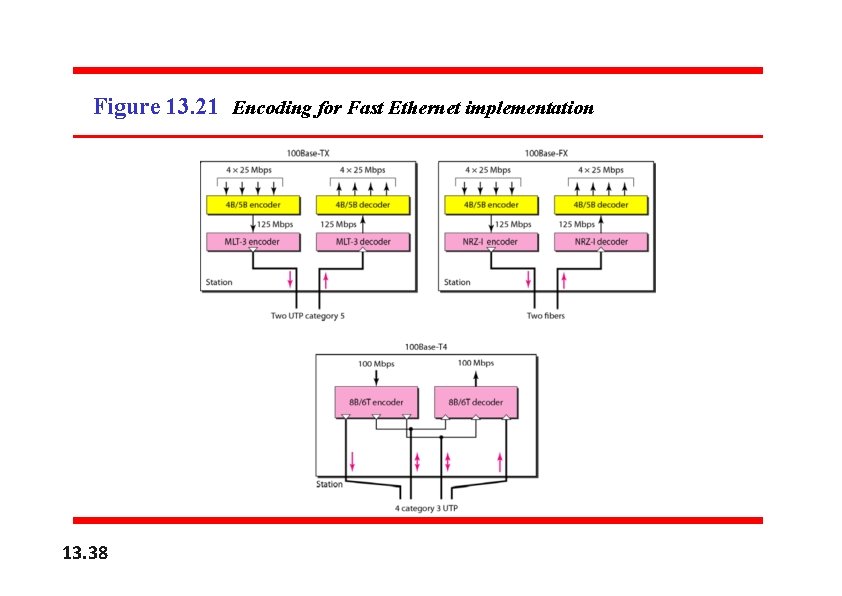
Figure 13. 21 Encoding for Fast Ethernet implementation 13. 38

100 Base-TX ü 100 Base-TX uses two pairs of twisted-pair cable (either category 5 UTP or STP) ü For this implementation, the MLT-3 scheme was selected since it has good . bandwidth performance, since MLT-3 is not a self-synchronous line coding scheme, 4 B/5 B block coding is used to provide bit synchronization by preventing the occurrence of a long sequence of 0 s and 1 s. ü This creates a data rate of 125 Mbps, which is fed into MLT-3 for encoding. 100 Base-FX ü 100 Base-FX uses two pairs of fiber-optic cables. ü Optical fiber can easily handle high bandwidth requirements by using simple encoding schemes. ü The designers of 100 Base-FX selected the NRZ-I encoding scheme for this implementation. ü NRZ-I has a bit synchronization problem for long sequences of 0 s (or 1 s, based on the encoding. To overcome this problem, the designers used 4 B/5 B block encoding ü The block encoding increases the bit rate from 100 to 125 Mbps, which can easily be handled by fiber-optic cable.

100 Base-TX ü A 100 Base-TX network can provide a data rate of 100 Mbps, but it requires the use of category 5 UTP or STP cable. ü A new standard, called 100 Base-T 4, was designed to use category 3 or higher UTP ü The implementation uses four pairs of UTP for transmitting 100 Mbps. ü Encoding/decoding in 100 Base-T 4 is more complicated. As this implementation uses category 3 UTP, each twisted-pair cannot easily handle more than 25 Mbaud. ü In this design, one pair switches between sending and receiving. Three pairs of UTP category 3, however, can handle only 75 Mbaud (25 Mbaud) each. ü An encoding scheme is used which converts 100 Mbps to a 75 Mbaud signal (8 B/6 T) ü In 8 B/6 T, eight data elements are encoded as six signal elements. This means that 100 Mbps uses only (6/8) × 100 Mbps, or 75 Mbaud. Table 13. 2 Summary of Fast Ethernet implementations 13. 40