Chapter 12 File and Secondary Storage Management Chapter

















- Slides: 53

Chapter 12 File and Secondary Storage Management

Chapter 12 File and Secondary Storage Management Chapter Outline File-Management Systems Directory Content and Structure Storage Allocation File Manipulation Access Controls Focus – Windows NTFS File Migration, Backup, and Recovery Focus – RAID Storage Consolidation

Chapter Goals • Describe the components and functions of a file management system • Compare the logical and physical organization of files and directories • Explain how secondary storage locations are allocated to files and describe the data structures used to record those allocations • Describe file manipulation operations, including open, close, read, delete, and undelete operations • List access controls that can be applied to files and directories • Describe security, backup, recovery, and fault tolerance methods and procedures • Compare and contrast storage area networks and network-attached storage

Chapter 12 Topics

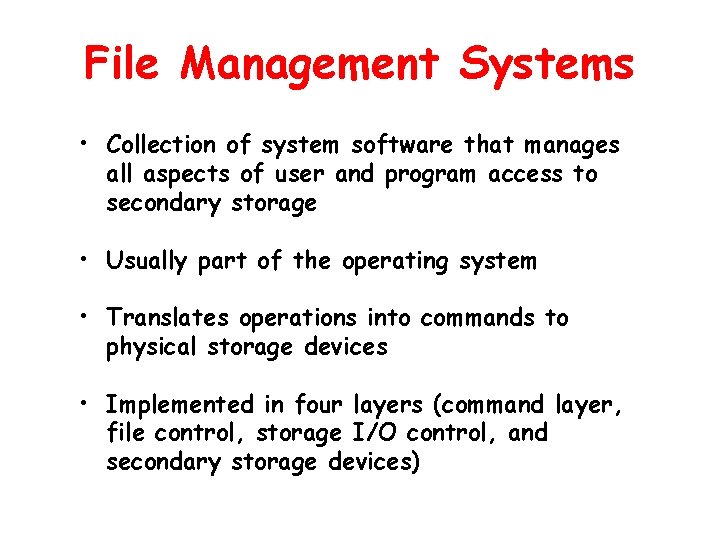
File Management Systems • Collection of system software that manages all aspects of user and program access to secondary storage • Usually part of the operating system • Translates operations into commands to physical storage devices • Implemented in four layers (command layer, file control, storage I/O control, and secondary storage devices)

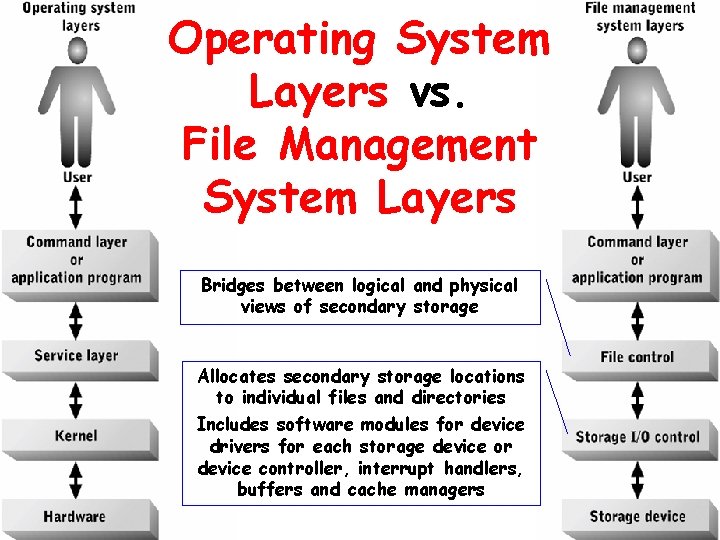
Operating System Layers vs. File Management System Layers Bridges between logical and physical views of secondary storage Allocates secondary storage locations to individual files and directories Includes software modules for device drivers for each storage device or device controller, interrupt handlers, buffers and cache managers

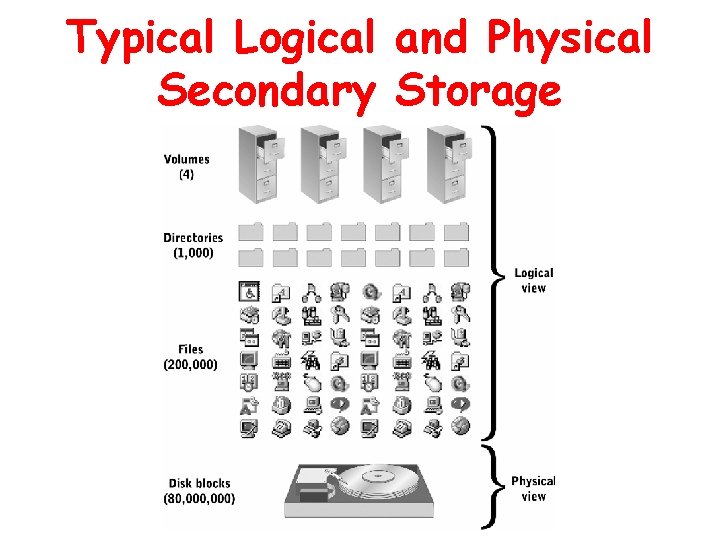
Logical and Physical Storage Views • Logical view – Collection of files organized within directories and storage volumes • Physical view – Collection of physical storage locations organized as a linear address space

Typical Logical and Physical Secondary Storage

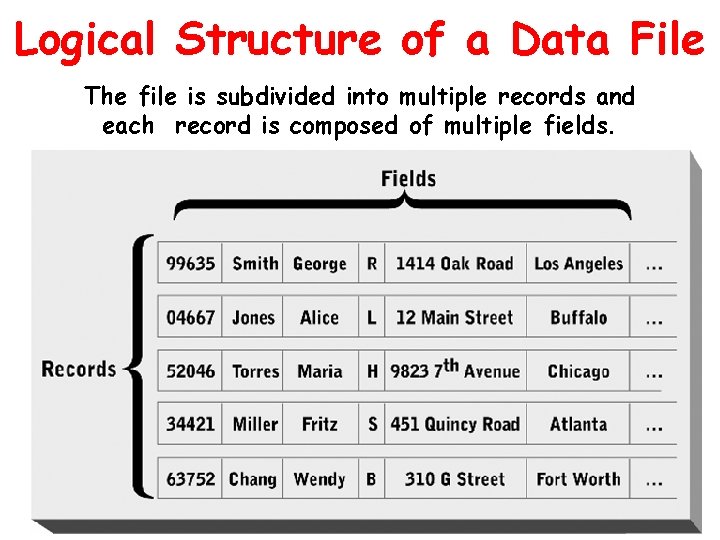
Logical Structure of a Data File The file is subdivided into multiple records and each record is composed of multiple fields.

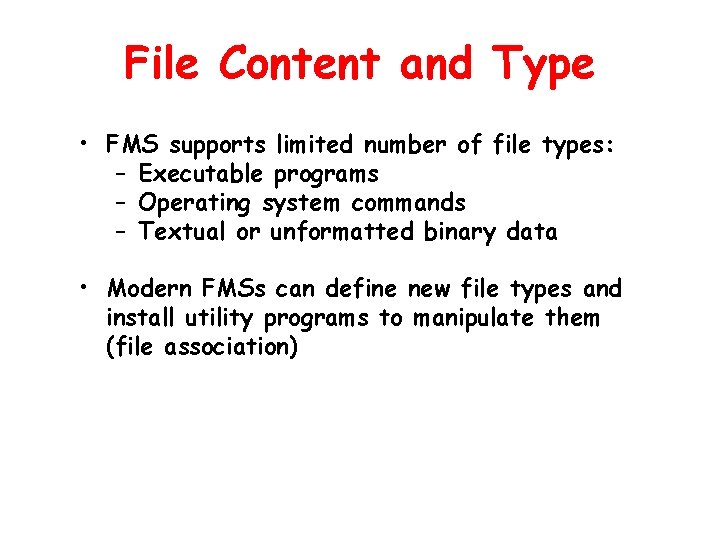
File Content and Type • FMS supports limited number of file types: – Executable programs – Operating system commands – Textual or unformatted binary data • Modern FMSs can define new file types and install utility programs to manipulate them (file association)

File Types • Normally declared when a file is created and: – Stored within a directory, or – Declared through a filename convention • Determine: – Physical organization of data items and data structures within secondary storage – Operations that may be performed upon the file – Filename restrictions

Registered File Types Windows XP

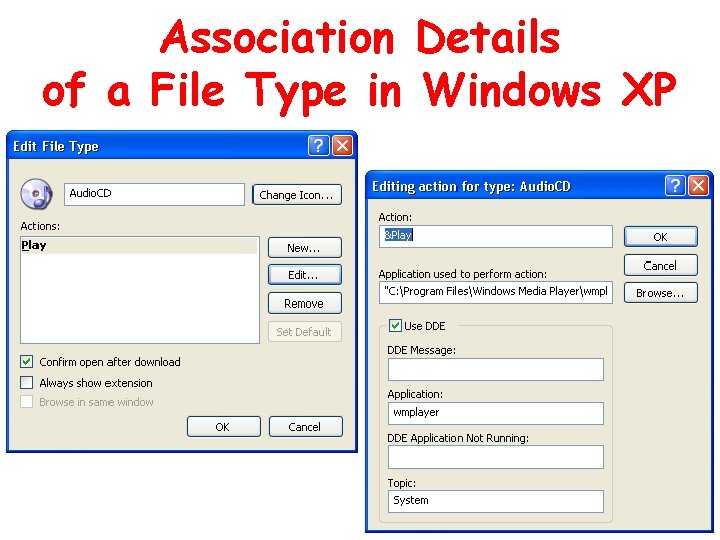
Association Details of a File Type in Windows XP

Directory Content and Structure A directory contains information about files and subdirectories • • name file type location size ownership access controls time stamps

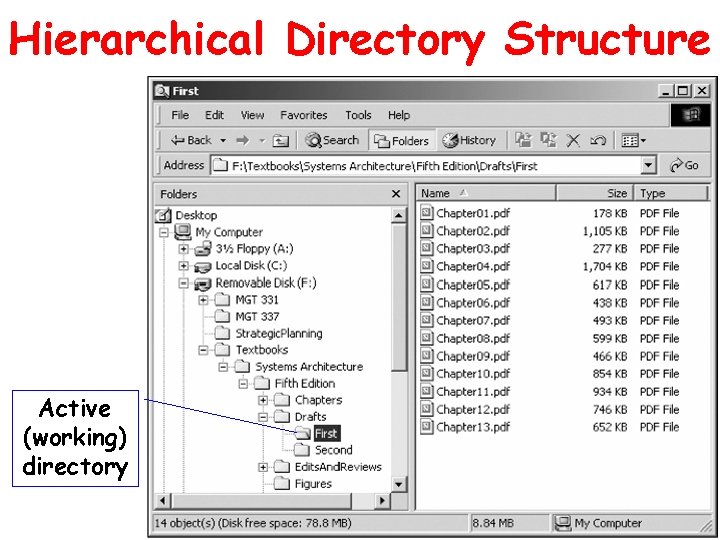
Hierarchical Directory Structure • Directories can contain other directories, creating a tree structure, but cannot be contained within more than one parent • Ways that names of access paths can be specified: – Complete path (fully qualified reference) – Relative path • Each storage device has a root directory

Hierarchical Directory Structure Active (working) directory

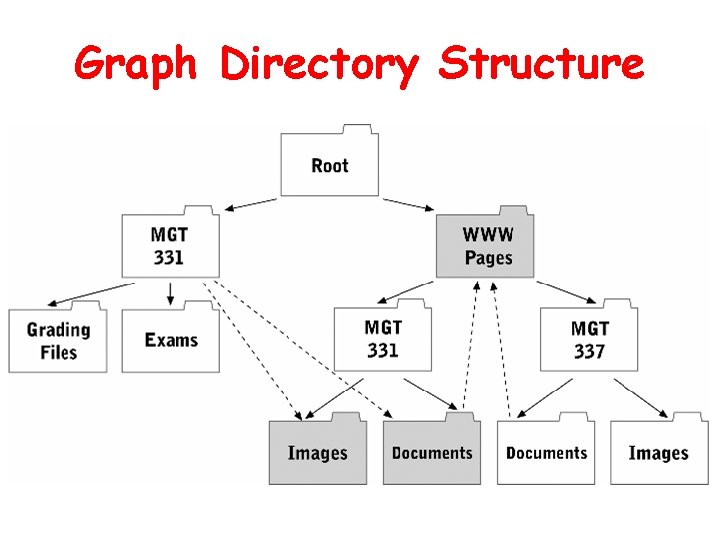
Graph Directory Structure • More flexible than hierarchical directory structure – Files and subdirectories can be contained within multiple directories – Directory links can form a cycle

Graph Directory Structure

Storage Allocation • Secondary storage devices – Large number of storage locations – Low frequency of allocation changes – Divided into allocation units

Allocation Units • Smallest number of secondary storage bytes that can be allocated to a file; cannot be smaller than unit of data transfer between storage device and controller (block) • Assigned/reclaimed by FMS as files and directories are created or expanded/shrink or are deleted • Size difficult to change once set

Allocation Unit Size • Tradeoffs – Efficient use of secondary storage space for files – Size of storage allocation data structures – Efficiency of storage allocation procedures • Smaller units – More efficient use of storage space • Larger units – Allow smaller storage allocation data structures

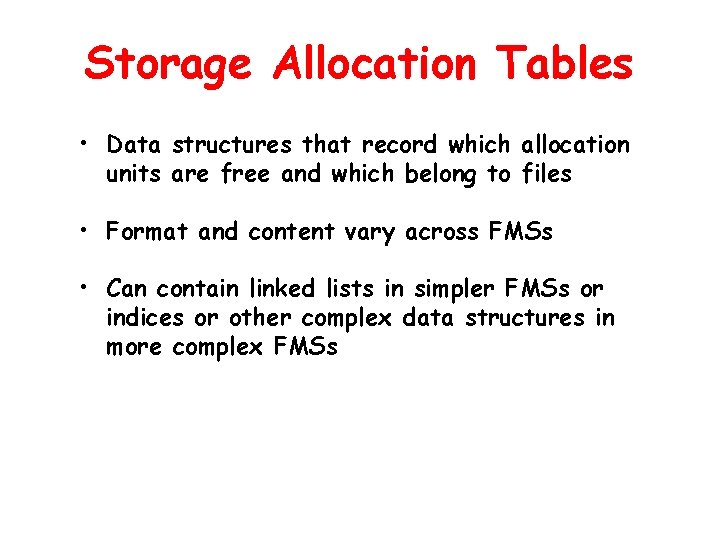
Storage Allocation Tables • Data structures that record which allocation units are free and which belong to files • Format and content vary across FMSs • Can contain linked lists in simpler FMSs or indices or other complex data structures in more complex FMSs

Storage Blocks Allocated to Three Files

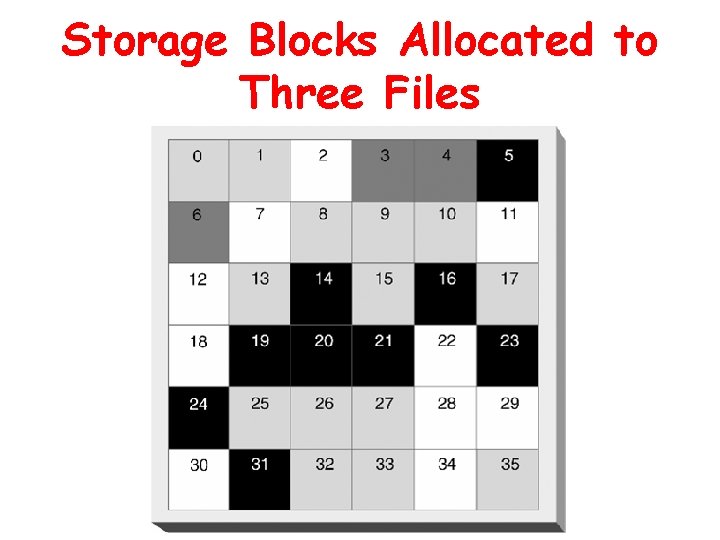
Directory Content for the Three Files Free allocation units are assigned to a hidden system file called Sys. Free

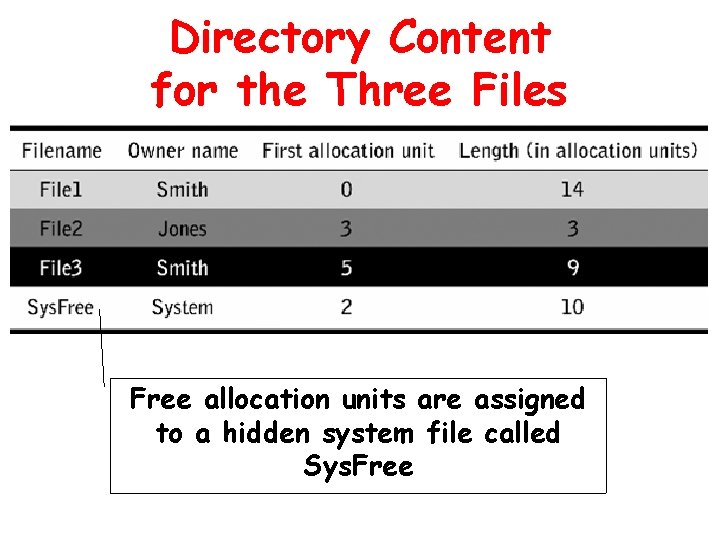
Storage Allocation Table for the Three Files All of a file allocation’s units are “chained” together in sequential order by a series of pointers.

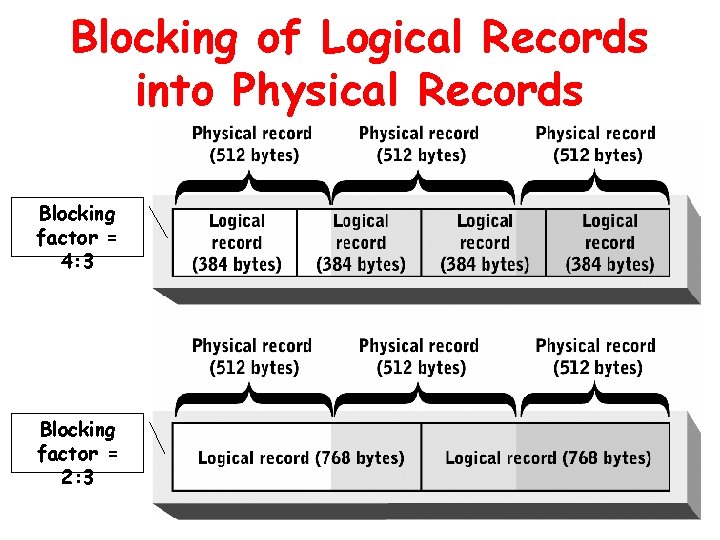
Blocking • Logical record grouping within physical records • Described by a numeric ratio of logical records to physical records (blocking factor)

Blocking of Logical Records into Physical Records Blocking factor = 4: 3 Blocking factor = 2: 3

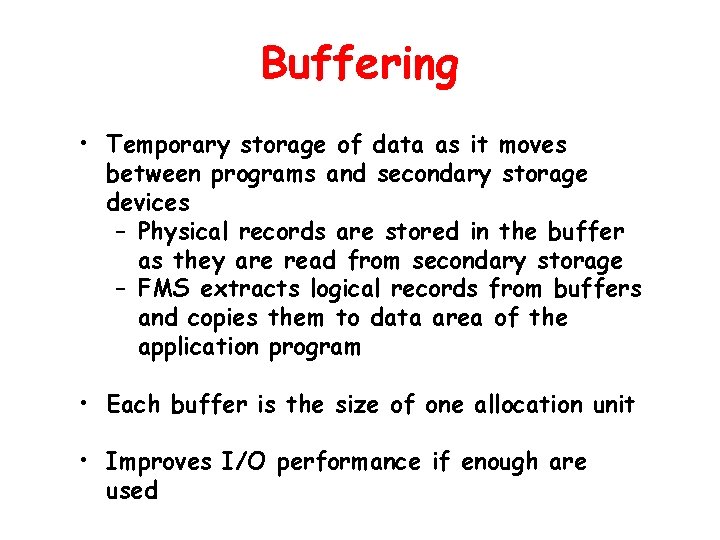
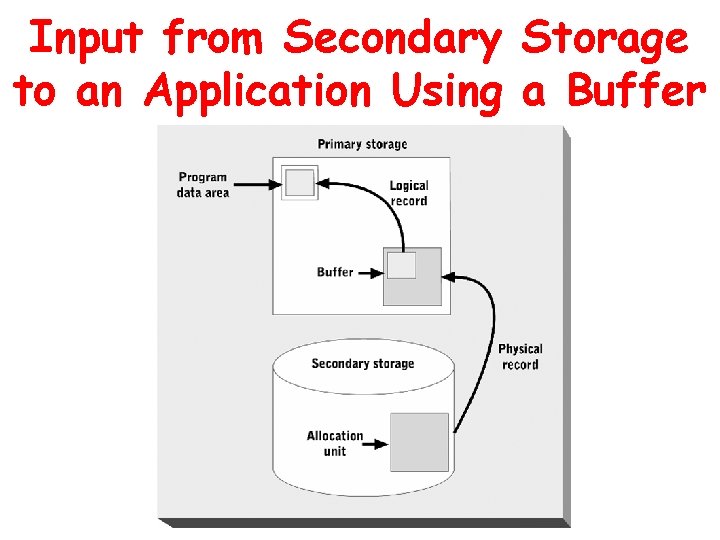
Buffering • Temporary storage of data as it moves between programs and secondary storage devices – Physical records are stored in the buffer as they are read from secondary storage – FMS extracts logical records from buffers and copies them to data area of the application program • Each buffer is the size of one allocation unit • Improves I/O performance if enough are used

Input from Secondary Storage to an Application Using a Buffer

File Manipulation • Exact set of service layer functions varies among FMSs, but typically includes create, copy, move, delete, read, and write • Application programs interact directly with FMS through OS service layer • Users interact indirectly with FMS through command layer

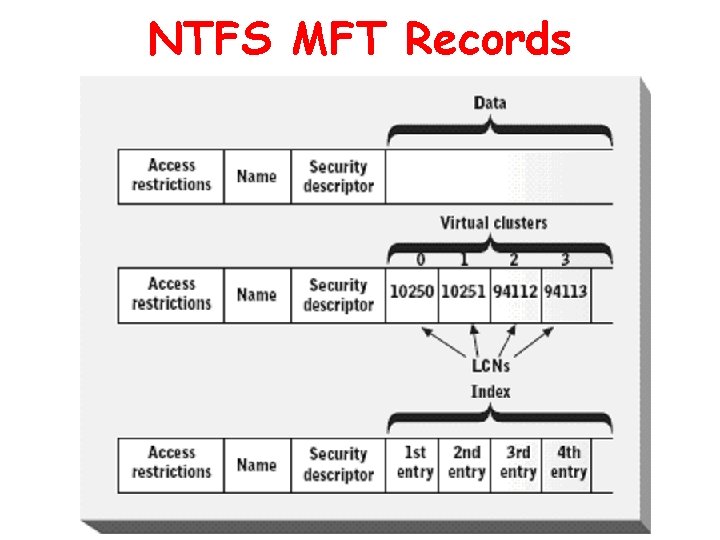
NTFS MFT Records

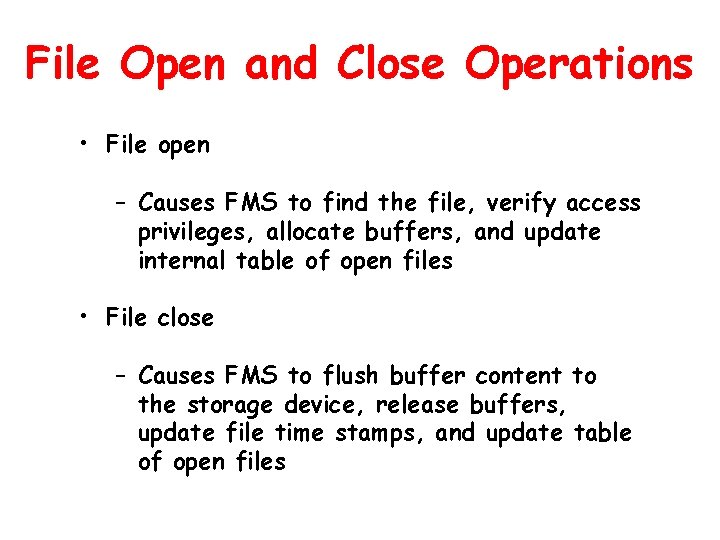
File Open and Close Operations • File open – Causes FMS to find the file, verify access privileges, allocate buffers, and update internal table of open files • File close – Causes FMS to flush buffer content to the storage device, release buffers, update file time stamps, and update table of open files

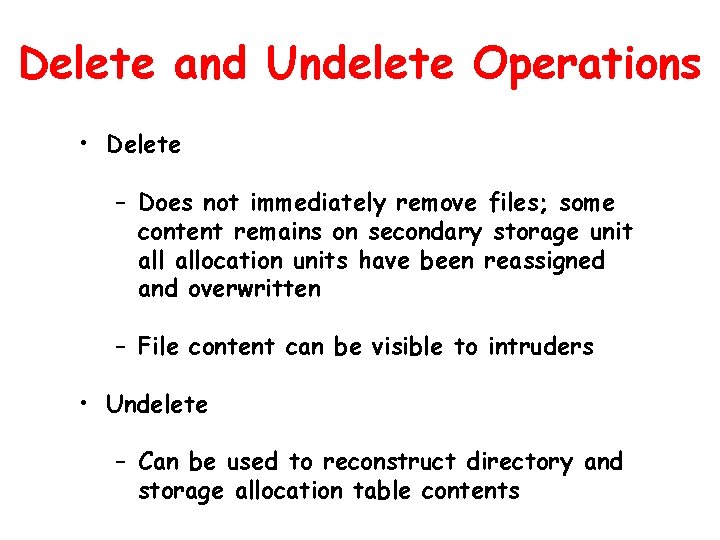
Delete and Undelete Operations • Delete – Does not immediately remove files; some content remains on secondary storage unit allocation units have been reassigned and overwritten – File content can be visible to intruders • Undelete – Can be used to reconstruct directory and storage allocation table contents

Access Controls • Granted by file owners and system administrators for reading, writing, and executing files • Provide security at the expense of additional FMS overhead

File Migration, Backup, and Recovery • Provided by most FMSs to protect files against damage or loss

File Migration (Version Control) • Automatic storage and backup of old file versions • Balances storage cost of each file version with anticipated user demand for that version

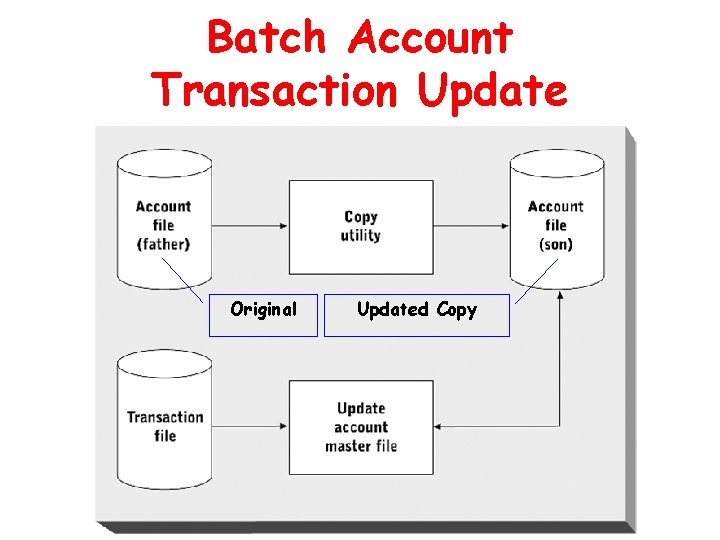
Batch Account Transaction Update Original Updated Copy

File Backup • Protects against data loss (file content, directory content, and storage allocation tables) • Store backup copies on a different storage device in a different physical location • Manual or automatic • Full or incremental

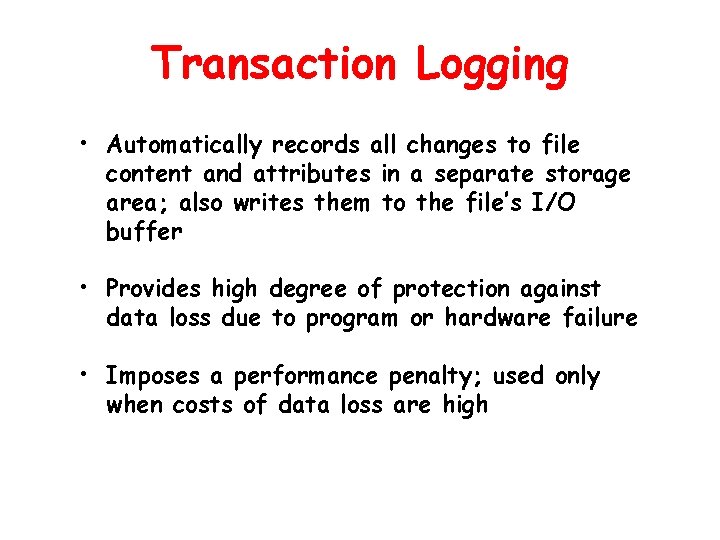
Transaction Logging • Automatically records all changes to file content and attributes in a separate storage area; also writes them to the file’s I/O buffer • Provides high degree of protection against data loss due to program or hardware failure • Imposes a performance penalty; used only when costs of data loss are high

File Recovery • Automated and manual components • Can search backup logs for copies of lost or damaged files • Can perform consistency checking and repair procedures for crashed system or physically damaged storage device

Fault Tolerance • Methods of securing file content against hardware failure – File backup – Recovery – Transaction logging – Mirroring – RAID • “Redundant Array of Inexpensive Disks”

Mirroring • All disk write operations are made concurrently to two different storage devices • Provides high degree of protection against data loss with no performance penalty if implemented in hardware • Disadvantages – Cost of redundant disk drives – Higher cost of disk controllers that implement mirroring

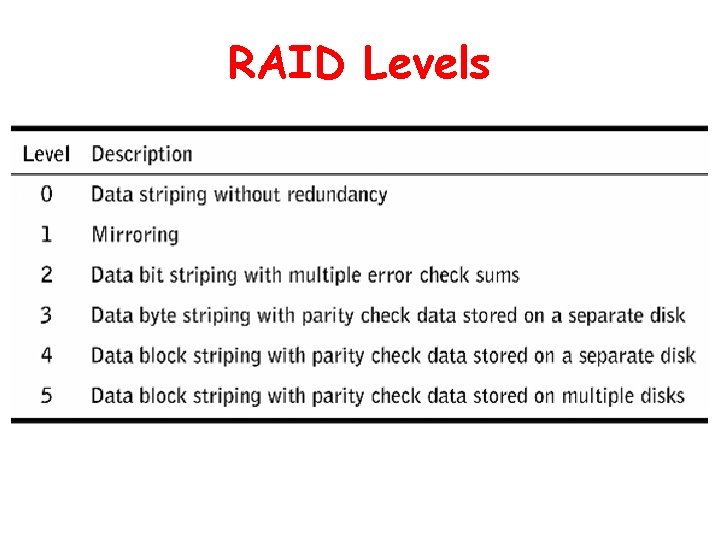
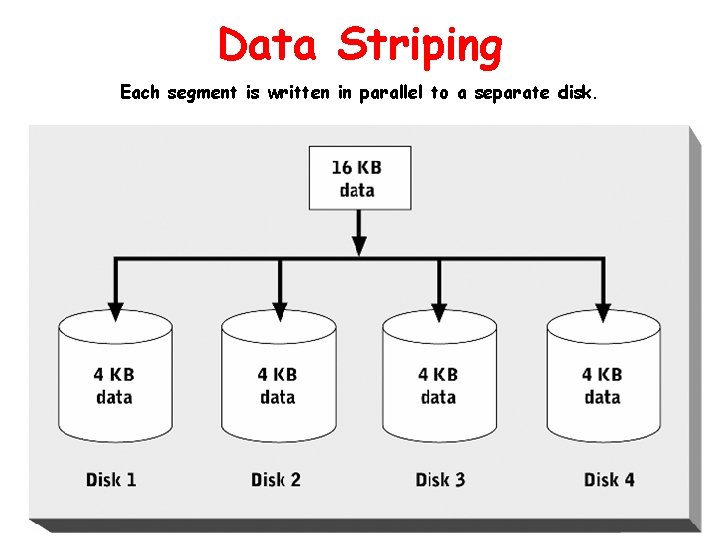
RAID • Disk storage technique that improves performance and fault tolerance • All levels except RAID 1 use data striping – Breaks a unit of data into smaller segments and stores them on multiple disks • Multiple levels can be layered to combine their best features (e. g. RAID 10) • Can be implemented in hardware or software

RAID Levels

Data Striping Each segment is written in parallel to a separate disk.

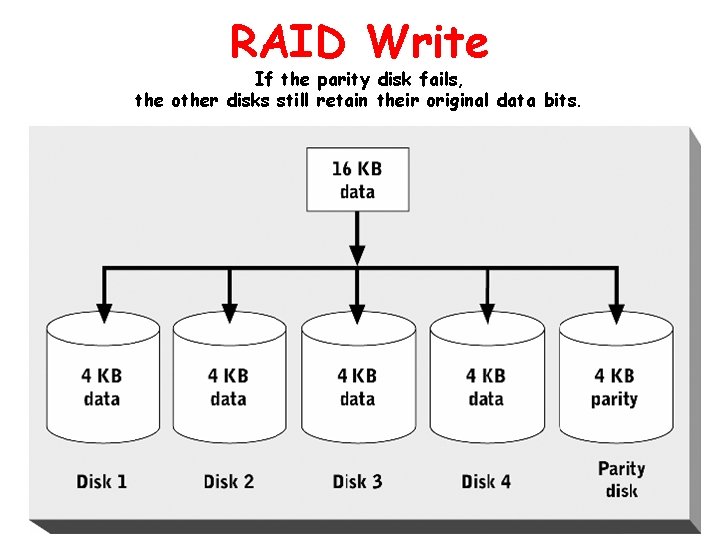
RAID Write If the parity disk fails, the other disks still retain their original data bits.

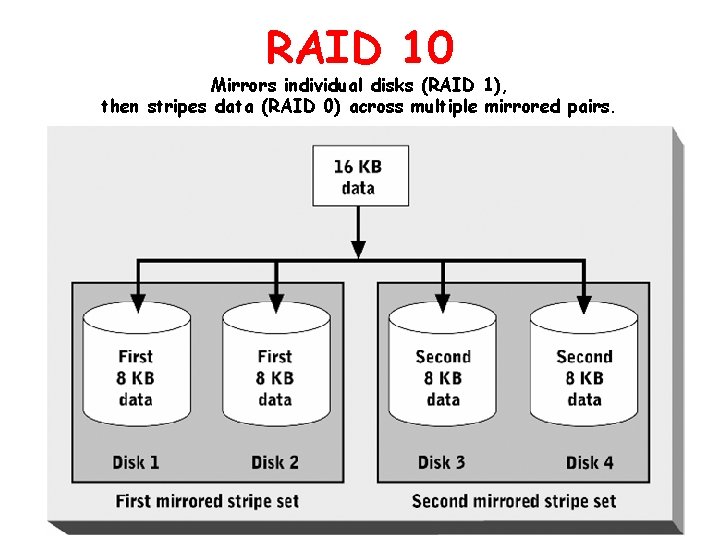
RAID 10 Mirrors individual disks (RAID 1), then stripes data (RAID 0) across multiple mirrored pairs.

Storage Consolidation • Overcomes inefficiencies of direct-attached storage (DAS) in multiple-server environments • Common approaches – Storage area network (SAN) – Network-attached storage (NAS)

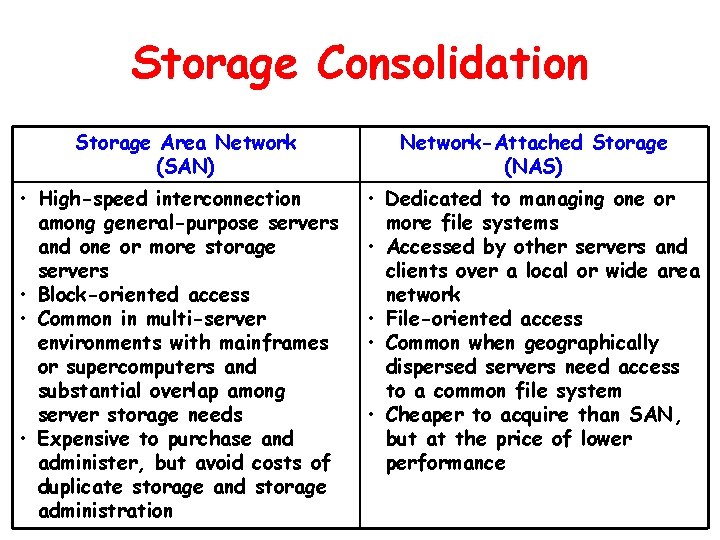
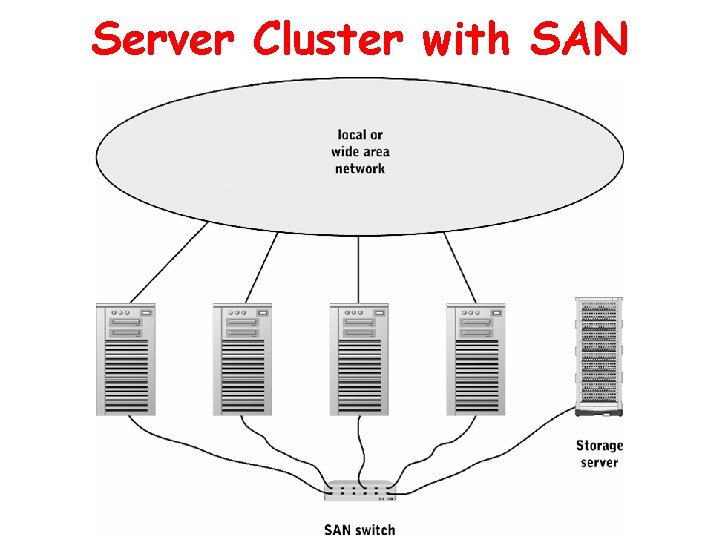
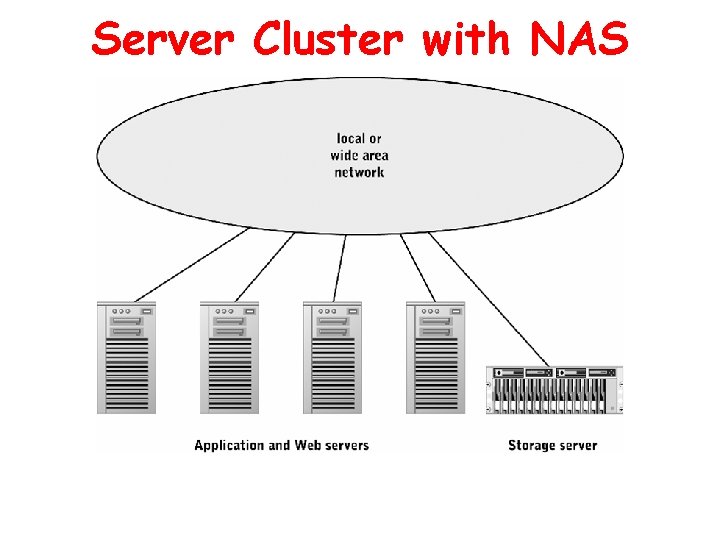
Storage Consolidation Storage Area Network (SAN) • High-speed interconnection among general-purpose servers and one or more storage servers • Block-oriented access • Common in multi-server environments with mainframes or supercomputers and substantial overlap among server storage needs • Expensive to purchase and administer, but avoid costs of duplicate storage and storage administration Network-Attached Storage (NAS) • Dedicated to managing one or more file systems • Accessed by other servers and clients over a local or wide area network • File-oriented access • Common when geographically dispersed servers need access to a common file system • Cheaper to acquire than SAN, but at the price of lower performance

Server Cluster with SAN

Server Cluster with NAS

Summary File management systems Directory content and structure Storage allocation File manipulation Access controls File migration, backup, and recovery Storage consolidation

Chapter Goals • Describe the components and functions of a file management system • Compare the logical and physical organization of files and directories • Explain how secondary storage locations are allocated to files and describe the data structures used to record those allocations • Describe file manipulation operations, including open, close, read, delete, and undelete operations • List access controls that can be applied to files and directories • Describe security, backup, recovery, and fault tolerance methods and procedures • Compare and contrast storage area networks and network-attached storage
 Secondary storage vs primary storage
Secondary storage vs primary storage Storage devices of computer
Storage devices of computer Uses rigid metallic platters
Uses rigid metallic platters File-file yang dibuat oleh user pada jenis file di linux
File-file yang dibuat oleh user pada jenis file di linux Secondary storage management
Secondary storage management Difference between logical file and physical file
Difference between logical file and physical file Object based and unified storage
Object based and unified storage A storage structure consisting of information about a file
A storage structure consisting of information about a file File ///storage/emulated/0/android/register.text
File ///storage/emulated/0/android/register.text Fungsi sistem file
Fungsi sistem file Distributed file system definition
Distributed file system definition What does a markup tag tells the web browser
What does a markup tag tells the web browser In a file-oriented information system, a transaction file
In a file-oriented information system, a transaction file Secondary storage device
Secondary storage device Magnetic tape secondary storage
Magnetic tape secondary storage Contoh secondary storage
Contoh secondary storage Introduction to storage
Introduction to storage Drum printer definition
Drum printer definition Mass storage structure
Mass storage structure Brief history of computer hardware
Brief history of computer hardware Storage area network
Storage area network Magnetic disk
Magnetic disk Kerja komputer dan peralatan teknologi informasi
Kerja komputer dan peralatan teknologi informasi Shadow paging
Shadow paging Emc information storage and management
Emc information storage and management Module 4 operating systems and file management
Module 4 operating systems and file management Define offal
Define offal Food safety and storage chapter 19
Food safety and storage chapter 19 Storage resource management software
Storage resource management software Dynamic disk vs basic disk performance
Dynamic disk vs basic disk performance Storage resource management
Storage resource management Ibm storage management
Ibm storage management Source language issues in compiler design
Source language issues in compiler design Storage resource management tools
Storage resource management tools Enterprise storage resource management
Enterprise storage resource management Storage infrastructure management activities
Storage infrastructure management activities Storage management in programming languages
Storage management in programming languages Management files for
Management files for Components of operating system
Components of operating system E office implementation
E office implementation Ansys project file management
Ansys project file management Objective file management
Objective file management Android manifest persistent
Android manifest persistent Cs1001 c
Cs1001 c Electronic file management
Electronic file management 3 importance of file management
3 importance of file management Objectives of file management system
Objectives of file management system Getw and putw in c
Getw and putw in c Top management middle management first line management
Top management middle management first line management Top management middle management first line management
Top management middle management first line management Top management middle management first line management
Top management middle management first line management Php file
Php file Enter.php?chapter=
Enter.php?chapter= File.php?n=
File.php?n=