Chapter 11 Privacy and Secrets Chapter Outline Privacy















- Slides: 17

Chapter 11 Privacy and Secrets

Chapter Outline Privacy and Regulation What to do about passwords Random Number generation Cryptography Secrets in Memory

What is Privacy?

What is Privacy? An expectation of non-dissemination of information without consent. What about information?

What is Privacy? An expectation of non-dissemination of information without consent. What about information? Confidential data about the program Data users think is private Data required by law to be kept as confidential

What is Privacy? An expectation of non-dissemination of information without consent. What about information? Confidential data about the program Data users think is private Data required by law to be kept as confidential Social Security Numbers Account numbers/credit card numbers, DL numbers Security codes, access codes, PINs, passwords, etc. Grades

Which laws? California's SB-1386 http: //info. sen. ca. gov/pub/01 -02/bill/sen/sb_13511400/sb_1386_bill_20020926_chaptered. html Children's Online Protection Act (COPPA) http: //www. ftc. gov/ogc/coppa 1. htm Federal Information Security Management Act (FISMA) http: //csrc. nist. gov/drivers/documents/FISMA-final. pdf Gramm-Leach-Bliley Act (GLBA) http: //www. ftc. gov/privacy/glbact/index. html Health Insurance Portability and Accountability Act (HIPAA) http: //www. hhs. gov/ocr/hipaa/ Payment Card Industry (PCI) Data Security Standard https: //www. pcisecuritystandards. org Safe Harbor Privacy Framework http: //www. export. gov/safeharbor/ Family Educational Rights and Privacy Act (FERPA): http: //www. ed. gov/policy/gen/guid/fpco/pdf/ferparegs. pdf

Where does private data enter? Directly Persisting from a DB or other data store Indirectly

How to handle Private data Label it as such, don't hide it. Be aware at all times of which variables carry private data and which don't. “Privacy violations” stem, for the most part, from misplaced trust. Minimize exposure of private data. Private data should be kept out of logs. Be aware of threads and re-entrant code.

Outbound Passwords Keep Passwords out of the source code. They are easy to find, even without the source code. Don't store Clear-text Passwords Store them, encrypted, in a configuration file. Store the encryption key in a different file. This can be repeated a few times.

Random Numbers Necesary for: Cryptography (key generation) Password generation Port randomization (for security) Unique session identifiers Etc. Need good entropy generators.

Some notes If there are N possible choices, there are log N bits of entropy Expect things to go wrong. Watch out for lack of independence Be conservative.

Cryptography Choose a good algorithm Watch what the standards organizations (ISO, NIST, etc) say. Researchers may publish attacks on certain codes: that does not invalidate the code. At the present time, recommended are: AES RSA SHA-2 (SHA-224, SHA-256, SHA-384, SHA-512)

Cryptography Don't roll your own Don't: Invent your own algorithm Create your own implementation Concoct your own key exchange protocol. Security through obscurity is a delusion.

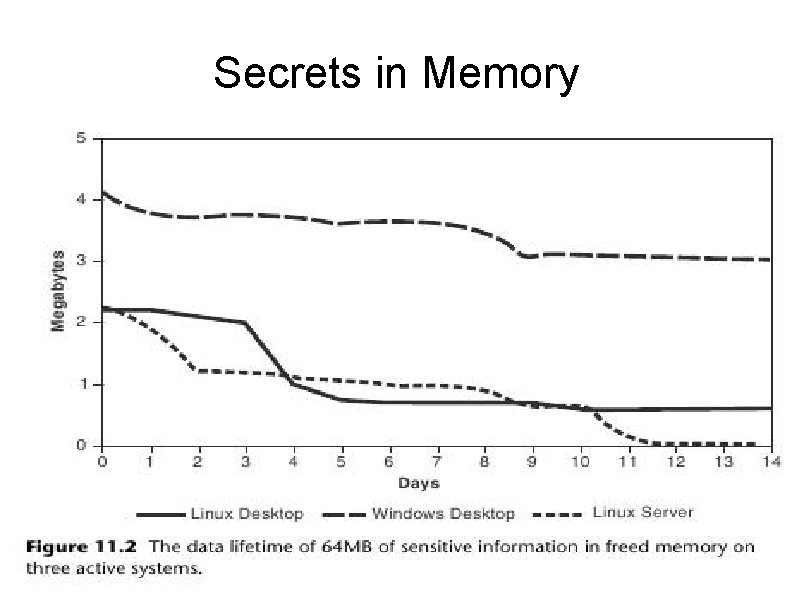
Secrets in Memory

How do attackers get secrets from memory? Remote exploits such as buffer overflow or format string attacks Physical attacks, such as stealing or discarded machines. Accidental leakage as in core dumps or page files.

How to control Information in Memory Minimize the time the secret is held in memory Lock the memory Share secrets sparingly Erase secrets securely Easier said than done: beware of optimizing compilers! Prevent unnecesary duplication.