Chapter 11 Information Security Management Agenda Security Threats





























- Slides: 31

Chapter 11 Information Security Management

Agenda • Security Threats – Sources – Problems • Security Program – – – Senior Management’s Security Role Technical Safeguard Data Safeguard Human Safeguard Disaster Preparedness Incident Response

Sources of Security Threats • Human error and mistakes – – Employees and non-employees Accidental problems Poorly written application programs Poorly designed procedures • Malicious human activity – – Employees, former employees, hackers, and outside criminals Intentionally destroy data or other systems components Steal for financial gain Terrorism • Natural events and disasters – Acts of nature – Loss of capability, service, and recovery

Problems of Security Threats • • • Unauthorized data disclosure Incorrect data modification Faulty service Denial of service Loss of infrastructure

Unauthorized Data Disclosure • Pretexting: someone pretending to be someone else • Phishing: someone pretending a legitimate company and obtaining confidential data by email • Spoofing: IP spoofing and Email spoofing • Sniffing: intercepting computer communication • Drive-by sniffers: intercepting unprotected wireless network

Incorrect Data Modification • Human error – employees follow procedures incorrectly – procedures have been incorrectly designed • Hacking

Faulty Service • Incorrect system operation – Human procedure mistake • Usurpation – Unauthorized program in a computer system

Denial of Service • Human error • Malicious hacker • Natural disasters

Loss of Infrastructure • Human accidents • Theft and terrorist events • Natural disasters

Security Program • Senior management involvement – Security policy – Cost and benefit analysis • Safeguards of various kinds – Technical protection: hardware and software – Data protection: data – Human protection: people and procedure • Incident response – Program response to security incident

Security Elements • By National Institute of Standards and Technology (NIST) • Support the mission of the organization • An integral element of sound management • Cost effective • Explicit security responsibilities and accountability • Comprehensive and integrated approach • Periodically reassessing • Constrained by social factor

Senior Management Role • Security policy – General policy: goals and assets – Issue-specific policy: computer and email usage – System-specific policy: specific information systems • Risk management and assessment – – – Assets and vulnerability Threats Likelihood of an adverse occurrence Consequences Safeguard and cost Probable loss

Technical Safeguard • • • Identification and authentication Encryption Digital signature Firewall Malware protection Design secure application

Identification and Authentication • Identification – User name • Authentication – Pass word (what you know) – Smart card (what you have) – Biometric authentication: fingerprints, facial features, retinal scans (what you are) – Single sign-on for multiple systems (Kerberos) – Wireless: WPA (Wi-Fi Protected Access) and WPA 2

Encryption • Symmetric encryption: one key • Asymmetric encryption: public key and private key • Secure Socket Layer (SSL) and Transport Layer Security (TLS): only client verify true Web site • Digital signature – Hashing – Message digest (check digits) – Digital certificate and certificate authorities

Firewall • Definition – A computing device to prevent unauthorized network access • Device – A special-purpose computer – A program on a general-purpose computer or on a router • Type – – Perimeter firewall Internal firewall Packet-filtering firewall Access control list (ACL)

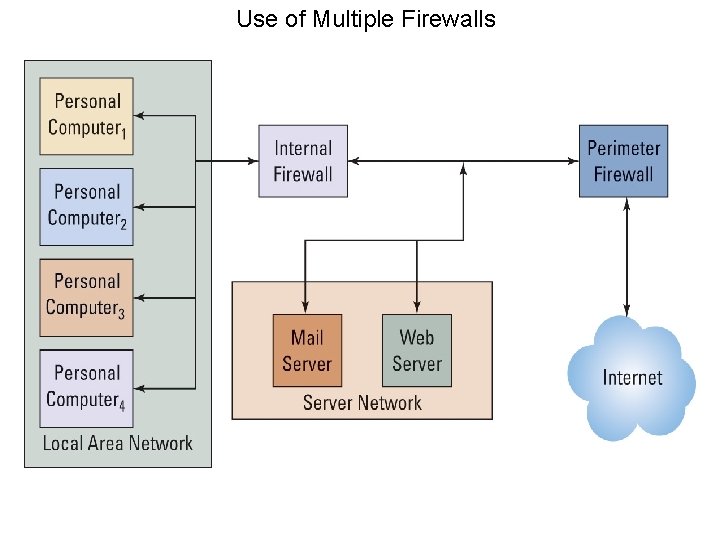
Use of Multiple Firewalls

Malware • Malware: viruses, worms, Trojan horses, spyware, and adware • Spyware: programs installed without the user’s knowledge for spying • Adware: installed without the user’s permission for observing user behavior and popping up ads

Spyware and Adware Symptoms • • Slow system start up Sluggish system performance Many pop-up ads Browser homepage changes, taskbar, and other interfaces • Unusual hard disk activity

Malware Safeguard • • Install antivirus and antispyware programs Scan computer frequently Update malware definitions Open email attachments only from known sources • Promptly install software updates from legitimate sources • Browse only in reputable Internet neighborhoods

Data Safeguard • • • Specifying user rights and responsibilities User account and password Store sensitive data in encrypted form Regular backup and practice recovery Backup copy at remote location Reside in locked, controlled-access facilities

Human Safeguard for Employee • Position definition – Job tasks and responsibilities – Least possible privilege – Documenting security sensitivity for each position • Hiring and Screening – Interviews, references, and background investigations • Dissemination and enforcement – Security policies, procedures, and responsibilities awareness – Training – Security responsibility, accountability, and compliance • Termination – Termination policies and procedures – Remove accounts and passwords – Recover keys for encrypted data

Human Safeguard for Non Employee • Temporary personnel, vendors, partner personnel, and the public • Require vendors and partners to perform appropriate screening and security training • Harden (extraordinary measures to reduce a system’s vulnerability) the Web site or other facility against attack

Account Administration • User accounts – Creation of new user accounts, modification of existing account permissions, and removal of unneeded accounts • Password – Change password – Use proper password • Help-desk policies and procedures for user’s forgetting password

Systems Procedures • Users and operations personnel • Procedures for normal, backup, and recovery operations

Systems Monitoring • Log analysis • Security testing • Investigating and learning from security incident • In-house IT personal and outside security consultants • Updating security: new technology and requirement

Disaster Preparedness • • Locate infrastructure in safe location Identify mission-critical systems Identify resources needed to run those systems Prepare remote backup facility – Hot sites: providing remote processing centers run by commercial disaster-recovery services – Cold site: providing office space, but customers themselves provide and install the equipment needed to continue operations • Train and rehearse

Incident Response • Have a plan • Critical personnel and off-hours contact information • Centralized reporting • Prepare specific response for speed • Practice

Discussion • Ethic guide (343 a-b) – Address the proper ethic issues of a online retailer related to its customer’s information. • Problem solving (351 a-b) – Address the security issues of hiring a white hat hacker. • Security guide (357 a-b) – Address the meta security issues of any organization. • Reflection guide (361 a-b) – Address the future of IT and IS five years latter.

Case Study • Case 11 -1 Antiphishing Tactics (365 -366): 2 only

Points to Remember • Security Threats – Sources – Problems • Security Program – – – Senior Management’s Security Role Technical Safeguard Data Safeguard Human Safeguard Disaster Preparedness Incident Response