Chapter 11 1 Chapter 11 Information Technology Auditing









































- Slides: 63

Chapter 11 -1

Chapter 11 Information Technology Auditing Introduction The Audit Function The IT Auditor’s Toolkit Auditing the Computerized AIS Information Technology Auditing Today Chapter 11 -2

Introduction Audits of accounting systems ensure that controls are functioning properly confirm that additional controls are not needed The nature of auditing includes the distinction between internal and external auditing the relationship between an IT audit and a financial audit Chapter 11 -3

Introduction the tools an IT auditor uses discussion of information technology governance, fraud in auditing, the impact of Sarbanes-Oxley on IT audits, and third-party and systems reliability assurance services Chapter 11 -4

The Audit Function The function of an audit is to examine and to assure. will differ according to the subject under examination. can be internal, or external, and concerns information systems also. Information technology auditing discusses internal auditing, External auditing, and IT auditing. Chapter 11 -5

The Audit Function Question An IT auditor a. must be an external auditor. b. must be an internal auditor. c. can be either an internal or external auditor. d. must be a certified public accountant. Chapter 11 -6

Internal Auditing An internal audit, which preserves its objectivity is carried out by company personnel reporting to top management and/or Ø the Audit Committee of the Board of Directors Ø is external to the corporate department or division being audited concerns employee adherence to Ø Chapter 11 -7 company policies and procedures, evaluation of internal controls

Internal Auditing is relatively broad in scope, including Ø auditing for fraud, Ø ensuring that employees are not copying software programs illegally can provide assurance to a company’s top management about Ø the efficiency of its organization and Ø effectiveness of its organization Chapter 11 -8

External Auditing The external audit is carried out by independent accountants has the attest function as its chief purpose confirming the accuracy of financial statements and Ø fairness of financial statements. Ø is conducted in the context of GAAP has expanded to check if financial statements are free of erroneous materials and Ø do not contain fraudulent misstatements Ø includes a variety of assurance services now Chapter 11 -9

Information Technology Auditing Information technology (IT) auditing involves evaluating the computer’s role in achieving audit objectives and Ø control objectives Ø means proving data and information are reliable, Ø confidential, Ø secure, and Ø available as needed Ø includes attest objectives like safeguarding of assets and data integrity, Ø operational effectiveness. Ø Chapter 11 -10

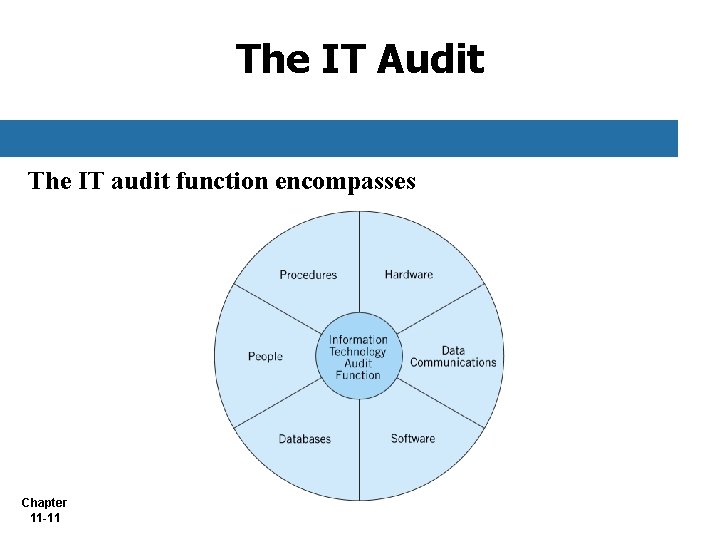
The IT Audit The IT audit function encompasses Chapter 11 -11

The Information Technology Audit Process Computer-assisted audit techniques (CAATs) are used when controls are weak for substantive testing of transactions and Ø account balances. Ø when controls are strong for compliance testing to ensure controls are in place and Ø working as prescribed. Ø Chapter 11 -12

The Information Technology Audit Process Chapter 11 -13

Careers in Information Systems Auditing The demand for IT auditors is growing increasing use of computer-based AISs systems becoming more technologically complex passing of the Sarbanes-Oxley bill IT auditing requires a variety of skills, combining accounting and information systems or computer science skills. Chapter 11 -14

Careers in Information Systems Auditing Information systems auditors may be internal or external can obtain professional certification as a Certified Information Systems Auditor (CISA) can also acquire certification as Certified Information Security Managers (CISM) Chapter 11 -15

Careers in Information Systems Auditing Auditors can achieve CISA certification Ø by completing an examination given by ISACA, Ø meeting specific experience requirements, Ø complying with a Code of Professional Ethics, Ø undergoing continuing professional education, and Ø complying with the Information Systems Auditing Standards Chapter 11 -16

Careers in Information Systems Auditing CISM certification, which Ø is also granted by ISACA Ø evaluates knowledge § § § Chapter 11 -17 in information security governance, information security program management, risk management, information security management, and response management.

Effectiveness of Information Systems Controls An external auditor’s objectives are to evaluate the risks Ø to the integrity of accounting data to make recommendations to managers Ø to improve these controls. Ø Chapter 11 -18

Risk Assessment A risk-based audit approach involves Determining the threats facing the AIS Ø errors and irregularities Identifying the control procedures Ø Chapter 11 -19 to prevent or detect the errors and irregularities

Risk Assessment Evaluating the control procedures within the AIS observing system operations, Ø inspecting documents, records, and reports, Ø checking samples of system inputs and outputs, and Ø tracing transactions through the system Ø Evaluating weaknesses identifying control deficiencies Ø determining compensating controls to make up for the deficiency Ø Chapter 11 -20

Information Systems Risk Assessment evaluates desirability of IT controls for an aspect of business risk. Ø disaster recovery or business continuity plan Ø Auditors and managers must answer each of the following questions: What assets or information does the company have that unauthorized individuals would want? Ø What is the value of these identified assets of information? Ø How can unauthorized individuals obtain valuable assets or information? Ø What are the chances of unauthorized individuals obtaining valuable assets or information? Ø Chapter 11 -21

Guidance in Reviewing and Evaluating IT Controls Two guides available to IT auditors Systems Auditability and Control (SAC) report identifies important information technologies and Ø specific risks related to these technologies Ø recommends controls to mitigate risks and Ø suggests audit procedures to validate these controls Ø Chapter 11 -22

Guidance in Reviewing and Evaluating IT Controls Control Objectives for Information and Related Technology (COBIT) provides guidance in assessing business risks, Ø controlling for business risks, and Ø evaluating the effectiveness of controls Ø Chapter 11 -23

Guidance in Reviewing and Evaluating IT Controls Question COBIT is a. a control framework developed by the Institute of Internal Auditors. b. a control framework developed specifically for organizations involved in e-business. c. an internal control model that covers both automated and manual systems. d. an internal control framework and model that encompasses an organization’s IT governance and information technologies. Chapter 11 -24

The Information Technology Auditor’s Toolkit IT auditors need to have the technical skills to understand the vulnerabilities in hardware and software Ø use of appropriate software to do their jobs Ø general-use software such as Ø word processing programs, § spreadsheet software, and § database management systems. § generalized audit software (GAS), and Ø automated workpaper software. Ø Chapter 11 -25

The Information Technology Auditor’s Toolkit people skills Ø to work as a team Ø to interact with clients and other auditors, Ø to interview many people constantly for evaluation Chapter 11 -26

Auditing with the Computer entails using computer-assisted audit techniques (CAATs) to help in auditing tasks and hence is effective and Ø saves time Ø is virtually mandatory since Ø data are stored on computer media and Ø manual access is impossible. Chapter 11 -27

General-Use Software Auditors use general-use software as productivity tools to improve their work such as spreadsheets and database management systems. Auditors use structured query language (SQL) to retrieve a client’s data and display these data for audit purposes. Chapter 11 -28

Generalized Audit Software Generalized audit software (GAS) packages enable auditors to review computer files without rewriting processing programs, are specifically tailored to auditor tasks have been developed in-house in large firms, or are available from various software suppliers Examples of GAS are Audit Command Language (ACL) Ø Interactive Data Extraction Ø Analysis (IDEA) Ø Chapter 11 -29

Generalized Audit Software Question Which of the following is not true with respect to generalized audit software (GAS)? a. They require auditors to rewrite processing programs frequently while reviewing computer files. b. They are specifically tailored to auditor tasks. c. They may be used for specific application areas, such as accounts receivable and inventory. d. They allow auditors to manipulate files to extract and compare data. Chapter 11 -30

Automated Workpaper Software Automated workpaper software is similar to general ledger software is much more flexible. Its features include: generated trial balances, adjusting entries, consolidations, and analytical procedures. Chapter 11 -31

People skills The most important skills auditors need are people skills. Auditors will find that many of the audit steps are nontechnical need to work in a team, have to interact with clients and other auditors, require strong interpersonal relationships. will need to interview the CIO Chapter 11 -32

People skills Many of the controls that an IT auditor needs to evaluate have more to do with human behavior than technology one of the best protections viruses and worms is regularly updated antivirus software but it is even more important to see if the security administrator is checking for virus updates and patches on a regular basis. Chapter 11 -33

Auditing the Computerized AIS Testing Computer Programs Validating Computer Programs Review of Systems Software Validating Users and Access Privileges Continuous Auditing Chapter 11 -34

Objectives of an Information Systems Audit In an IT audit, auditors should meet the following objectives Checking security provisions, which protect computer equipment, programs, communications, and data from unauthorized access, modification, destruction. or Program development and acquisition are performed in accordance with management’s authorization. Ø Program modifications have authorization and approval from management. Ø Chapter 11 -35

Objectives of an Information Systems Audit Ø Processing of transactions, files, reports, and other computer records is accurate and complete. Ø Source data that are inaccurate or improperly authorized are identified and handled according to prescribed managerial policies. Ø Computer data files are accurate, complete, and confidential. Chapter 11 -36

Auditing Computerized AISAuditing Around the Computer Auditing around the computer assumes that accurate output verifies proper processing operations pays little or no attention to the control procedures within the IT environment is generally not an effective approach to auditing a computerized environment. Chapter 11 -37

Auditing Computerized AISAuditing Through the Computer Five techniques used to audit a computerized AIS are: use of test data, integrated test facility, and parallel simulation to test programs, use of audit techniques to validate computer programs, use of logs and specialized control software to review systems software, use of documentation and CAATs to validate user accounts and access privileges, and use of embedded audit modules to achieve continuous auditing. Chapter 11 -38

Testing Computer Programs - Test Data The auditor’s responsibility is to develop test data Ø that tests the range of exception situations arrange the data in preparation for computerized processing complete the audit test by Ø comparing the results with a predetermined set of answers investigate further if the results do not agree Test data can check if program edit test controls are in place and working can be developed using software programs called test data generators Chapter 11 -39

Testing Computer Programs Integrated Test Facility An integrated test facility (ITF) establishes a fictitious entity such as a department, branch, customer, or employee, enters transactions for that entity, and observes how these transactions are processed. is effective in evaluating integrated online systems and complex programming logic, and aims to audit an AIS in an operational setting. Chapter 11 -40

Testing Computer Programs Integrated Test Facility The auditor’s role is to examine the results of transaction processing find out how well the AIS does the tasks required of it Ø Chapter 11 -41 by introducing artificial transactions into the data processing stream of the AIS.

Testing Computer Programs Parallel Simulation In Parallel Simulation, the auditor uses live input data, rather than test data, in a program, which is written or controlled by the auditor Ø simulates all or some of the operations of the real program that is actually in use. Ø needs to understand the client system, should possess sufficient technical knowledge, and should know how to predict the results. Chapter 11 -42

Testing Computer Programs Parallel Simulation Parallel simulation eliminates the need to prepare a set of test data, can be very time-consuming and thus cost-prohibitive usually involves replicating only certain critical functions of a program. Chapter 11 -43

Validating Computer Programs Auditors must validate any program presented to them Ø to thwart a clever programmer’s dishonest program Procedures that assist in program validation are tests of program change control procedures to protect against unauthorized program changes Ø begins with an inspection of the documentation Ø includes program authorization forms to be filled Ø ensures accountability and adequate supervisory controls Ø Chapter 11 -44

Validating Computer Programs program comparison guards against unauthorized program tampering Ø performs certain control total tests of program authenticity Ø using a test of length § using a comparison program § Chapter 11 -45

Validating Computer Programs Question Which of the following is an audit technique for auditing computerized AISs? a. Parallel simulation b. Use of specialized control software c. Continuous auditing d. All of the above are techniques used to audit computerized AISs. Chapter 11 -46

Review of Systems Software Systems software includes operating system software, utility programs, program library software, and access control software. Chapter 11 -47

Review of Systems Software Auditors should review systems software documentation. Systems software can generate incident reports, which list events that are Ø unusual or interrupt operations security violations (such as unauthorized access attempts), § hardware failures, and § software failures § Chapter 11 -48

Validating Users and Access Privileges The IT auditor needs to verify that the software parameters are set appropriately must make sure that IT staff are using them appropriately needs to make sure that all users are valid and Ø each has access privileges appropriate to their job Ø There a variety of auditor software tools, CAATs, which can settings and databases and § make the work more efficient § Chapter 11 -49

Continuous Approach Continuous auditing can be achieved by embedded audit modules or audit hooks Ø application subroutines capture data for audit purposes exception reporting Ø mechanisms reject certain transactions that fall outside predefined specifications Ø Chapter 11 -50 prespecified criteria in a special log called SCARF

Continuous Approach transaction tagging Ø tags with a special identifier for certain transactions snapshot technique Ø examination of the way transactions are processed continuous and intermittent simulation Ø Chapter 11 -51 embedding of an audit module in a DBMS

Information Technology Auditing Today Information technology auditing today involves Information Technology Governance Auditing for Fraud—Statement on Auditing Standards No. 99 The Sarbanes-Oxley Act of 2002 Third-Party Reliability Assurances Information Systems Reliability Assurances Chapter 11 -52

Information Technology Governance Information Technology governance is the process of using IT resources efficiently, Ø responsibly, and Ø strategically. Ø The IT Governance Institute, is affiliated to ISACA was created in 1998 Chapter 11 -53

Information Technology Governance The objectives of IT governance are twofold: to fulfill the organizational mission and to compete effectively to ensure that the IT resources are managed effectively and Ø that management controls IT related risks. Ø Chapter 11 -54

Auditing for Fraud—Statement on Auditing Standards No. 99 Earlier financial statement audits required auditors to attest to the fairness of financial statements not to detect fraudulent activities. Financial statement audits now require auditors to attest to the fairness of financial statements detect fraudulent activities assist a fraud investigator in many ways where an audit trail needs to be reconstructed Ø when computerized records must be retrieved Ø Chapter 11 -55

Auditing for Fraud—Statement on Auditing Standards No. 99 Question With respect to changes in IT auditing today, which of the following is not true? a. IT governance, which ties IT to organizational strategy, is increasingly important. b. Section 404 of the Sarbanes-Oxley Act of 2002 created an increase in demand for both IT auditors and internal auditors. c. IT auditors are concerned only with supporting financial auditors and should not investigate fraud cases. d. Third-party assurance seals may provide some comfort to e-business customers regarding the security of online transactions. Chapter 11 -56

The Sarbanes-Oxley Act of 2002 In 2002, Congress passed the Sarbanes-Oxley Act, which limits the services that auditors can provide to their clients, prohibits public accounting firms from offering nonaudit services to clients at the same time they are conducting audits. The SOX has basically four groups of compliance requirements. These are audit committee/corporate governance requirements, issues regarding certification, disclosure, and internal controls, rules about financial statement reporting, and Chapter 11 -57 regulations governing executive reporting and conduct.

The Sarbanes-Oxley Act of 2002 The two most important provisions of SOX for auditors are Section 302 – requiring CFOs and CEOs to certify that their company’s financial statements are accurate and complete Section 404 – requiring both the CEO and CFO to attest to their organization’s internal controls over financial reporting Chapter 11 -58

Information Systems Reliability Assurance Auditing electronic commerce is a specialized field because of the skill level involved, of the many safeguards, inherent in non-e-commerce systems, which do not exist here, of the lack of hard-copy documents for verification, and of an electronic transaction, which does not guarantee validity or authenticity Auditors need to attest this type of format to provide the traditional assurance by an audit report or Ø digital signature Ø Chapter 11 -59

Third-Party Assurance Internet systems and web sites are a source of risk for many companies, need specialized audits of these systems, have created a market for third-party assurance services, which Ø Chapter 11 -60 is limited to data privacy.

Third-Party Assurance The AICPA introduced Trust Services an assurance service. The principles of Trust Services are security, availability, processing integrity, online privacy, and confidentiality. Chapter 11 -61

Copyright 2005 John Wiley & Sons, Inc. All rights reserved. Reproduction or translation of this work beyond that permitted in Section 117 of the 1976 United States Copyright Act without the express written permission of the copyright owner is unlawful. Request for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. The purchaser may make backup copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages, caused by the use of these programs or from the use of the information contained herein. Chapter 11 -62

Chapter 11 -63