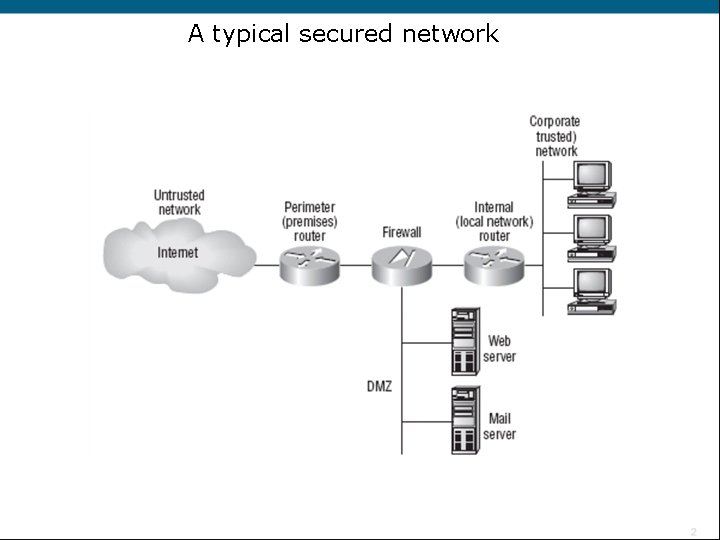
Chapter 10 Security A typical secured network Recognizing




- Slides: 16

Chapter 10 Security

A typical secured network

Recognizing Security Threats 1 - Application-layer attacks Ex: http: //www. companyname. com/scripts/. . %5 c. . /winnt/system 32/cmd. exe? /c+dir+c: 2 - Autorooters 3 - Backdoors 4 - Denial of service (Do. S) and distributed denial of service (DDo. S) attacks • TCP SYN flood (SYN, SYN-ACK, & ACK) • Ping of death • Tribe Flood Network (TFN) and Tribe Flood Network 2000 (TFN 2 K) • Stacheldraht 5 - IP spoofing 6 - Man-in-the-middle attacks (Using Sniffer) 7 - Network reconnaissance (port scans, DNS queries, and ping sweeps) 8 - Packet sniffers 9 - Password attacks (IP spoofing, packet sniffing, & Trojan horses) 10 - Brute force attack 11 - Port redirection attacks 12 - Trojan horse attacks and viruses 13 - Trust exploitation attacks

Mitigating Security Threats 1 - Cisco’s IOS Firewall • Stateful IOS Firewall inspection engine using Context-Based Access Control (CBAC) • Intrusion detection • Firewall voice traversal • ICMP inspection • Authentication proxy (RADIUS or TACACS+) Router(config)#enable use-tacacs Router(config)#tacacs-server ? host Specify a TACACS server key Set TACACS+ encryption key timeout Time to wait for a TACACS server to reply Router(config)#enable last-resort • Destination URL policy management • Per-user firewalls • Cisco IOS router and firewall provisioning • Denial of service (Do. S) detection and prevention • Dynamic port mapping • Java applet blocking 2 - Basic and Advanced Traffic Filtering • Policy-based, multi-interface support • Network Address Translation (NAT) • Time-based access lists • Peer router authentication (RIPv 2, EIGRP, or OSPF)

Access Lists 1 - Standard access lists 2 - Extended access lists 3 - Advanced access lists a- Inbound access lists b- Outbound access lists Uses of Access lists • Traffic filtration • Telnet filtration General Tips • Deny addresses from your internal networks. • Deny any local host addresses (127. 0. 0. 0/8). • Deny any reserved private addresses. • Deny addresses in the IP multicast address range (224. 0. 0. 0/4).

Standard Access Lists Router(config)#access-list NO. Action Source Router(config)#access-list ? <1 -99> IP standard access list <100 -199> IP extended access list <1100 -1199> Extended 48 -bit MAC address access list <1300 -1999> IP standard access list (expanded range) <200 -299> Protocol type-code access list <2000 -2699> IP extended access list (expanded range) <700 -799> 48 -bit MAC address access list compiled Enable IP access-list compilation dynamic-extended Extend the dynamic ACL absolute timer rate-limit Simple rate-limit specific access list Router(config)#access-list 10 ? deny Specify packets to reject permit Specify packets to forward remark Access list entry comment Router(config)#access-list 10 deny ? Hostname or A. B. C. D any host Address to match Any source host A single host address Router(config-if)#ip access-group 10 out (or in)

Wildcard Masking Router(config)#access-list 10 deny 172. 16. 10. 0. 0. 255 Router(config)#access-list 10 deny 172. 16. 0 0. 0. 3. 255 Controlling VTY (Telnet) Access Router(config)#access-list 50 permit 172. 16. 10. 3 Router(config)#line vty 0 4 Router(config-line)#access-class 50 in

Extended Access Lists Router(config)#access-list NO. Action Protocol Source Destination Condition Port no. Ex: Router(config)#access-list 110 permit tcp any host 172. 16. 30. 2 eq 80 Router(config)#access-list 110 deny tcp any host 172. 16. 30. 2 gt 1023 Router(config)#int s 0 Router(config-if)#ip access-group 110 out

Access Lists Example

Advanced Access Lists 1 - Named ACLs 2 - Switch Port ACLs 3 - Time based ACLs 1 - Named ACLs Router(config)#ip access-list ? extended Extended Acc logging Control access list logging standard Standard Access List Router(config)#ip access-list standard Block. Sales Router(config-std-nacl)#deny 172. 16. 40. 0. 0. 255 Router(config-std-nacl)#permit any Router(config-std-nacl)#exit

2 - Switch Port ACLs Conditions 1 - Inbound only. 2 - Named only. Switch(config)#mac access-list extended Name of list Switch(config-ext-macl)#Action Source Destination Ex: Switch(config)#mac access-list extended Block_MAC_Sales Switch(config-extended-macl)#deny any host 000 d. 29 bd. 4 b 85 Switch(config-extended-macl)#permit any Switch(config-ext-macl)#int f 0/6 Switch(config-if)#mac access-group Block_MAC_Sales in

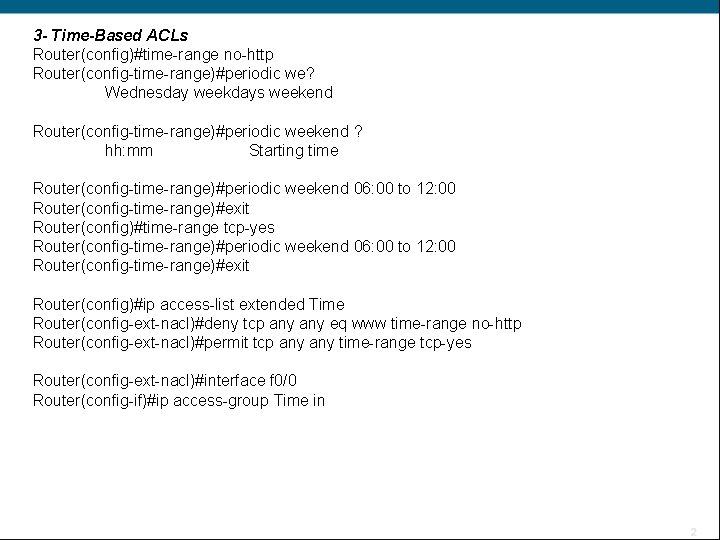
3 - Time-Based ACLs Router(config)#time-range no-http Router(config-time-range)#periodic we? Wednesday weekdays weekend Router(config-time-range)#periodic weekend ? hh: mm Starting time Router(config-time-range)#periodic weekend 06: 00 to 12: 00 Router(config-time-range)#exit Router(config)#time-range tcp-yes Router(config-time-range)#periodic weekend 06: 00 to 12: 00 Router(config-time-range)#exit Router(config)#ip access-list extended Time Router(config-ext-nacl)#deny tcp any eq www time-range no-http Router(config-ext-nacl)#permit tcp any time-range tcp-yes Router(config-ext-nacl)#interface f 0/0 Router(config-if)#ip access-group Time in

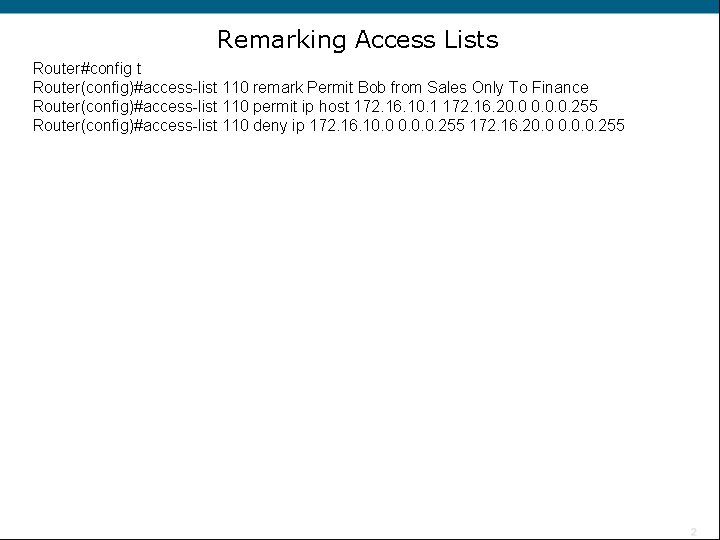
Remarking Access Lists Router#config t Router(config)#access-list 110 remark Permit Bob from Sales Only To Finance Router(config)#access-list 110 permit ip host 172. 16. 10. 1 172. 16. 20. 0. 0. 255 Router(config)#access-list 110 deny ip 172. 16. 10. 0. 0. 255 172. 16. 20. 0. 0. 255

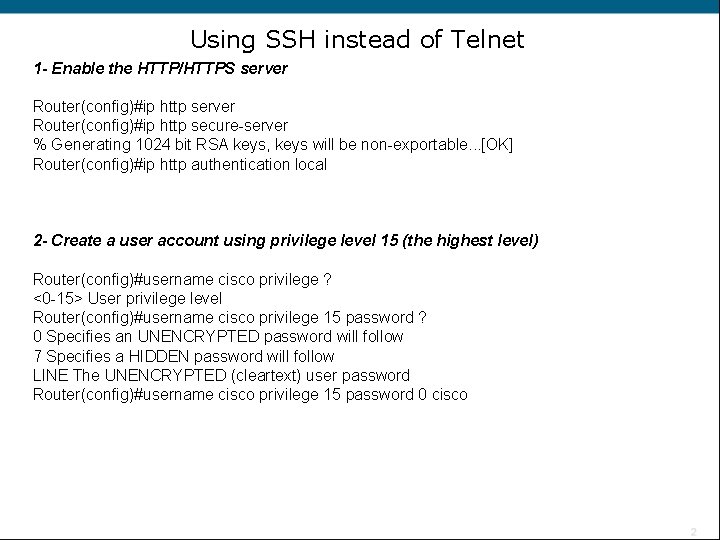
Using SSH instead of Telnet 1 - Enable the HTTP/HTTPS server Router(config)#ip http secure-server % Generating 1024 bit RSA keys, keys will be non-exportable. . . [OK] Router(config)#ip http authentication local 2 - Create a user account using privilege level 15 (the highest level) Router(config)#username cisco privilege ? <0 -15> User privilege level Router(config)#username cisco privilege 15 password ? 0 Specifies an UNENCRYPTED password will follow 7 Specifies a HIDDEN password will follow LINE The UNENCRYPTED (cleartext) user password Router(config)#username cisco privilege 15 password 0 cisco

3 - Configure the console, SSH, and Telnet to provide local login authentication at privilege level access Router(config)#line console 0 Router(config-line)#login local Router(config-line)#exit Router(config)#line vty 0 ? <1 -1180> Last Line number <cr> Router(config)#line vty 0 1180 Router(config-line)#privilege level 15 Router(config-line)#login local Router(config-line)#transport input telnet ssh Router(config-line)#^Z Router#clock set 00: 00 21 mar 2009

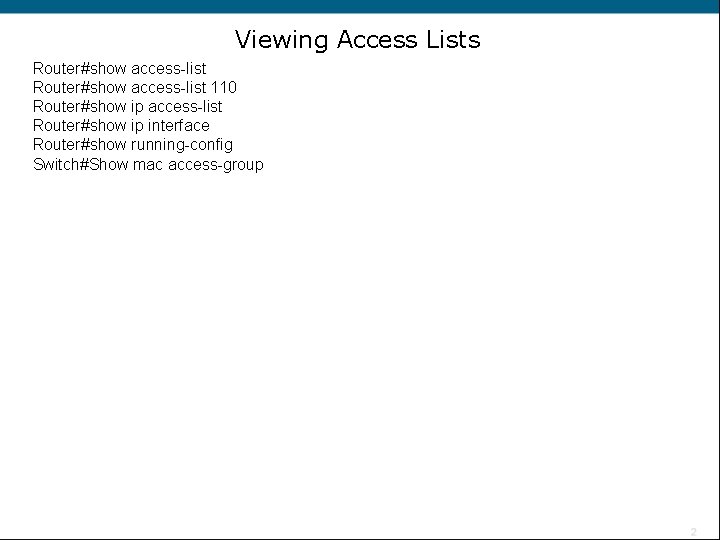
Viewing Access Lists Router#show access-list 110 Router#show ip access-list Router#show ip interface Router#show running-config Switch#Show mac access-group