Chapter 10 Cipher Techniques Some Problems Types of

Chapter 10: Cipher Techniques Some Problems Types of Ciphers Networks Examples Slide #10 -1

1 to 10 in Chinese Characters Slide #10 -2

Now, can you recognize? 六八五 三十九 二四八 Slide #10 -3

Problems What can go wrong if you naively use ciphers Is the set of possible messages small? Do the messages exhibit regularities that remain after encipherment? Can an active wiretapper rearrange or change parts of the message? Slide #10 -4
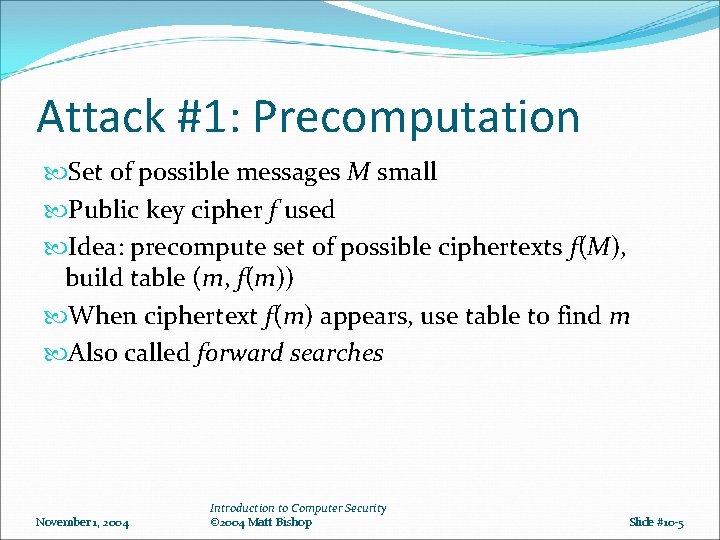
Attack #1: Precomputation Set of possible messages M small Public key cipher f used Idea: precompute set of possible ciphertexts f(M), build table (m, f(m)) When ciphertext f(m) appears, use table to find m Also called forward searches November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #10 -5

Example Cathy knows Alice will send Bob one of two messages: enciphered BUY, or enciphered SELL Using public key e. Bob, Cathy precomputes m 1 = { BUY } e. Bob, m 2 = { SELL } e. Bob Cathy sees Alice send Bob m 2 Cathy knows Alice sent SELL November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #10 -6

May Not Be Obvious Digitized sound Seems like far too many possible plaintexts Initial calculations suggest 232 such plaintexts Analysis of redundancy in human speech reduced this to about 100, 000 (≈ 217) This is small enough to worry about precomputation attacks http: //www. freegreatdesign. com/vector/digital-sound-wave-vector-material-3054 Slide #10 -7
Movie - <The Reader> http: //www. filmofilia. com/the-reader-quad-poster-and-22 -minute-featurette-6927/ Slide #10 -8

Movie - <The Reader> Slide #10 -9
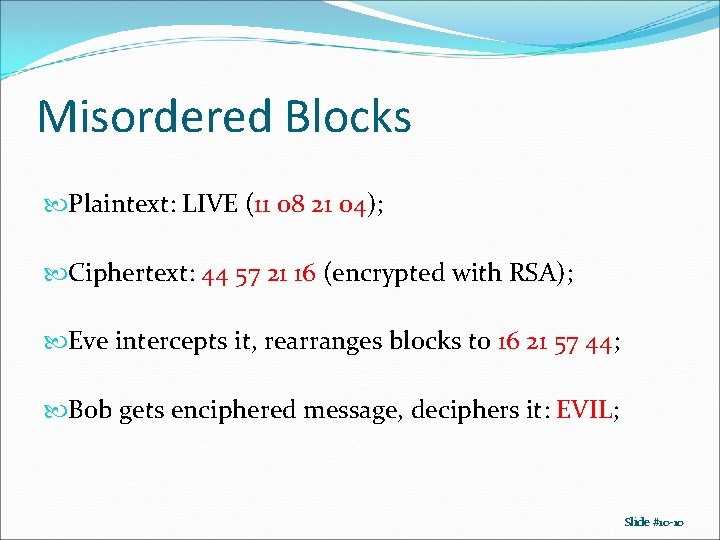
Misordered Blocks Plaintext: LIVE (11 08 21 04); Ciphertext: 44 57 21 16 (encrypted with RSA); Eve intercepts it, rearranges blocks to 16 21 57 44; Bob gets enciphered message, deciphers it: EVIL; Slide #10 -10

Statistical Regularities If plaintext repeats, ciphertext may too Example using DES: input (in hex): 3231 3433 3635 3837 corresponding output (in hex): ef 7 c 4 bb 2 b 4 ce 6 f 3 b Slide #10 -11
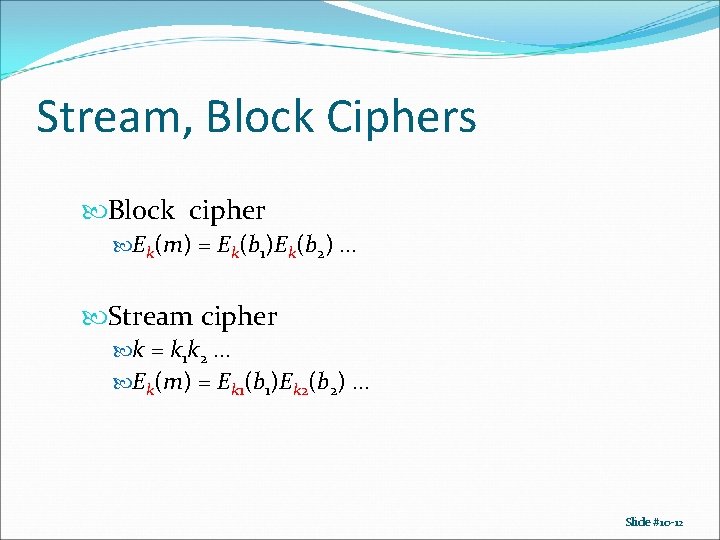
Stream, Block Ciphers Block cipher Ek(m) = Ek(b 1)Ek(b 2) … Stream cipher k = k 1 k 2 … Ek(m) = Ek 1(b 1)Ek 2(b 2) … Slide #10 -12
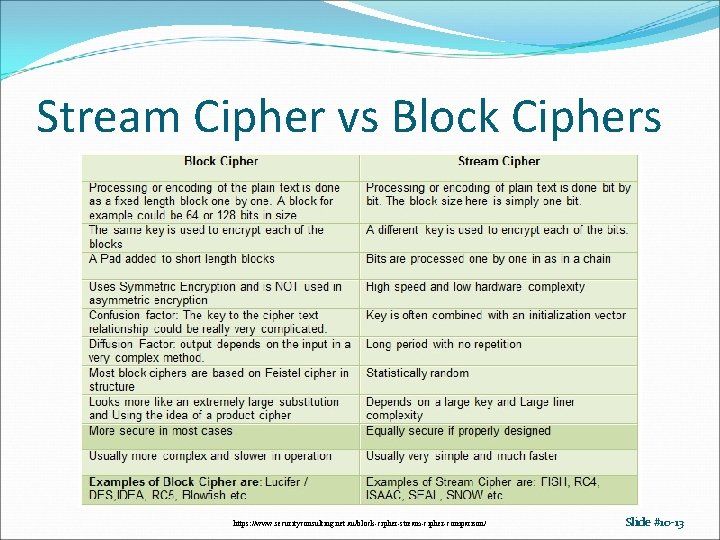
Stream Cipher vs Block Ciphers https: //www. securityconsulting. net. au/block-cipher-stream-cipher-comparison/ Slide #10 -13
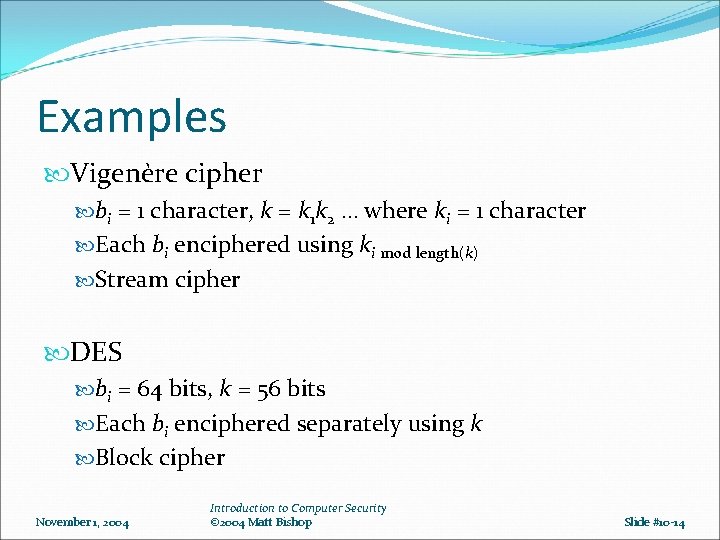
Examples Vigenère cipher bi = 1 character, k = k 1 k 2 … where ki = 1 character Each bi enciphered using ki mod length(k) Stream cipher DES bi = 64 bits, k = 56 bits Each bi enciphered separately using k Block cipher November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #10 -14
Stream Ciphers But how to generate a good key? Slide #10 -15
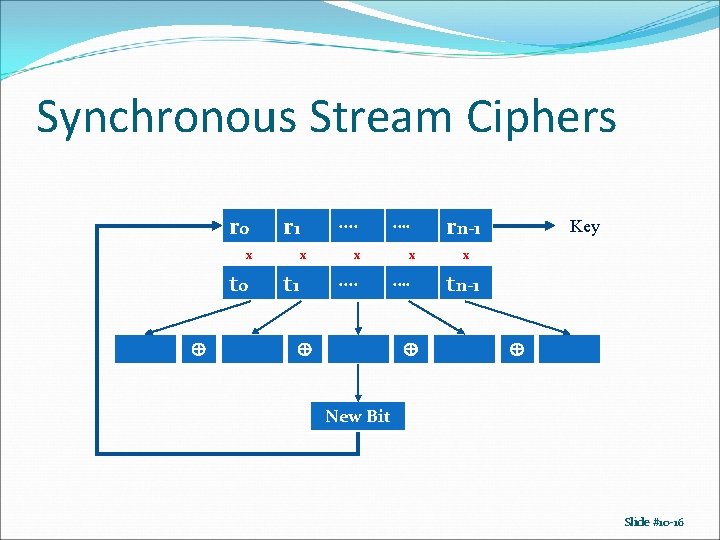
Synchronous Stream Ciphers r 0 r 1 x t 0 x t 1 . . x . . …. x …. rn-1 Key x tn-1 New Bit Slide #10 -16
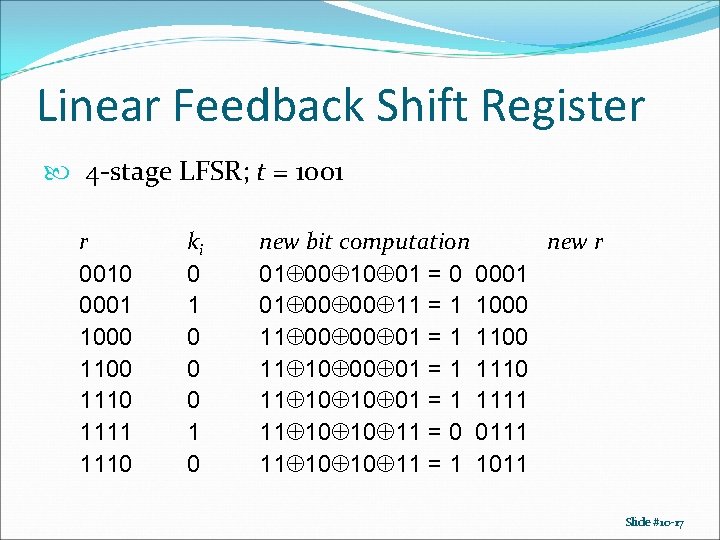
Linear Feedback Shift Register 4 -stage LFSR; t = 1001 r 0010 0001 1000 1110 1111 1110 ki 0 1 0 0 0 1 0 new bit computation new r 01 00 10 01 = 0 0001 01 00 00 11 = 1 1000 11 00 00 01 = 1 1100 11 10 00 01 = 1 1110 11 10 10 01 = 1 1111 11 10 10 11 = 0 0111 11 10 10 11 = 1 1011 Slide #10 -17
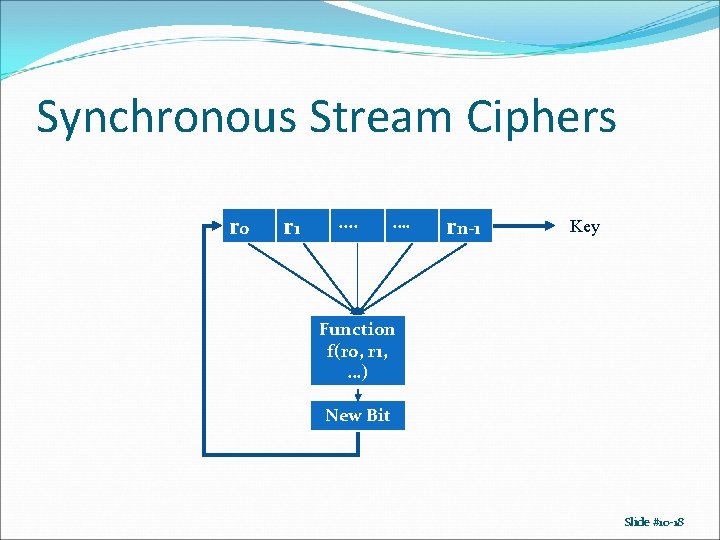
Synchronous Stream Ciphers r 0 r 1 . . …. rn-1 Key Function f(r 0, r 1, …) New Bit Slide #10 -18
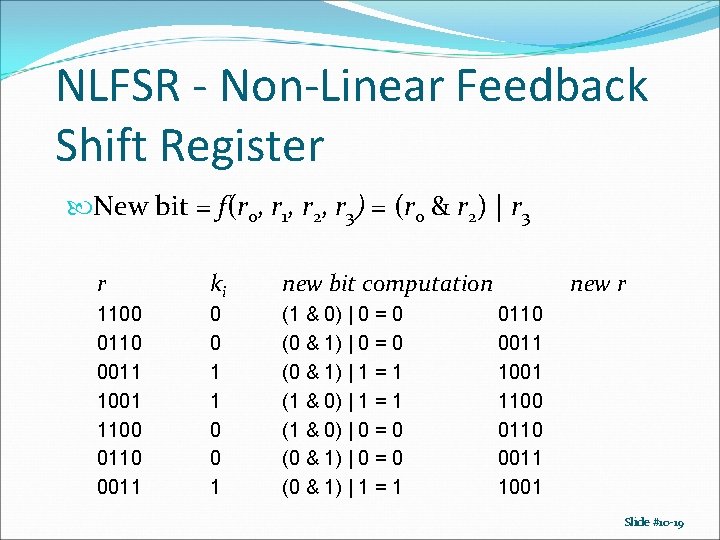
NLFSR - Non-Linear Feedback Shift Register New bit = f(r 0, r 1, r 2, r 3) = (r 0 & r 2) | r 3 r ki new bit computation 1100 0110 0011 1001 1100 0110 0011 0 0 1 (1 & 0) | 0 = 0 (0 & 1) | 1 = 1 new r 0110 0011 1001 1100 0110 0011 1001 Slide #10 -19

Self-Synchronous Stream Cipher Take key from message itself (autokey) Example: Vigenère, key drawn from plaintext key XTHEBOYHASTHEBA plaintext THEBOYHASTHEBAG ciphertext QALFPNFHSLALFCT Problem: Statistical regularities in plaintext show in key Once you get any part of the message, you can decipher more November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1020

Another Example Take key from ciphertext (autokey) Example: Vigenère, key drawn from ciphertext key XQXBCQOVVNGNRTT plaintext THEBOYHASTHEBAG ciphertext QXBCQOVVNGNRTTM Problem: Attacker gets key along with ciphertext, so deciphering is trivial November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #10 -21
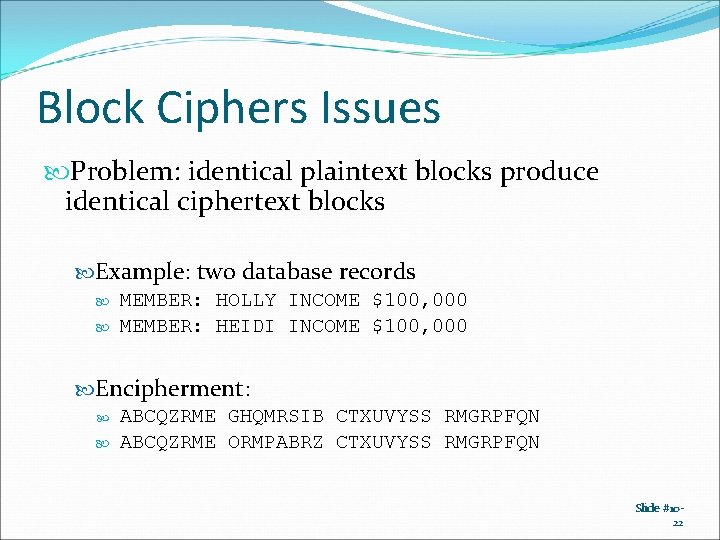
Block Ciphers Issues Problem: identical plaintext blocks produce identical ciphertext blocks Example: two database records MEMBER: HOLLY INCOME $100, 000 MEMBER: HEIDI INCOME $100, 000 Encipherment: ABCQZRME GHQMRSIB CTXUVYSS RMGRPFQN ABCQZRME ORMPABRZ CTXUVYSS RMGRPFQN Slide #1022
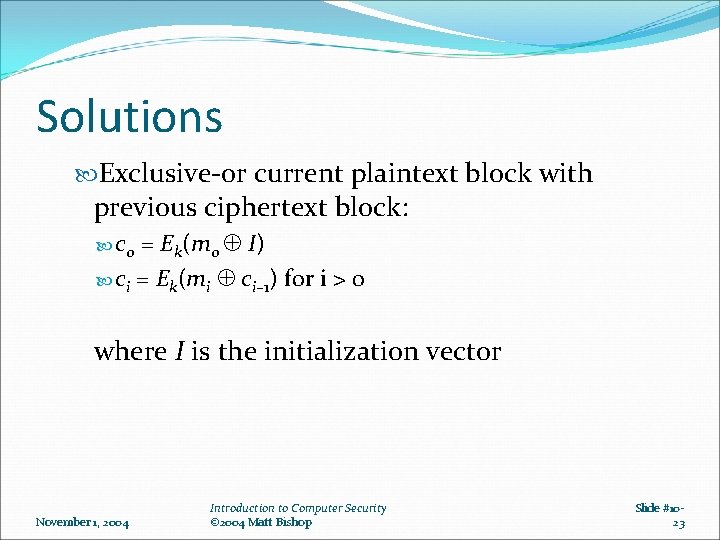
Solutions Exclusive-or current plaintext block with previous ciphertext block: = Ek(m 0 I) ci = Ek(mi ci– 1) for i > 0 c 0 where I is the initialization vector November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1023
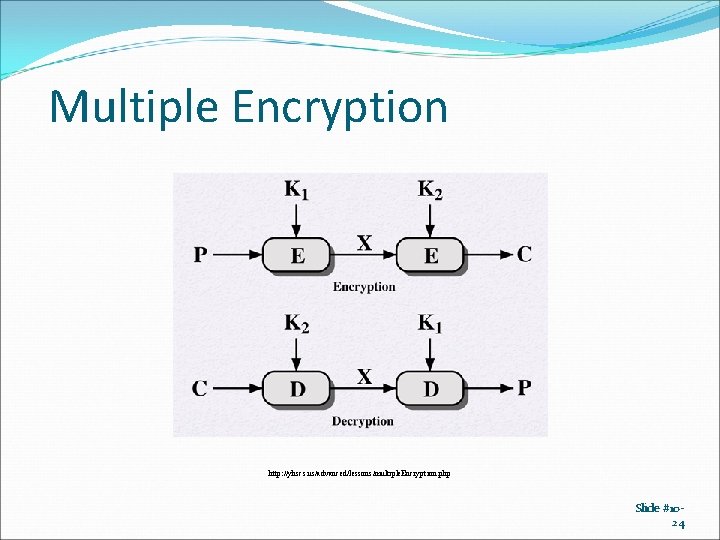
Multiple Encryption http: //yhscs. us/advanced/lessons/multiple. Encryption. php Slide #1024
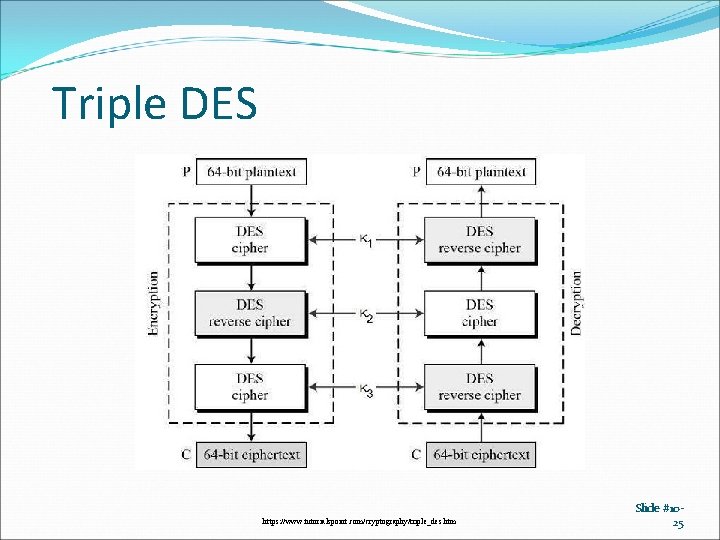
Triple DES https: //www. tutorialspoint. com/cryptography/triple_des. htm Slide #1025
Triple Caesar Cipher? Slide #1026
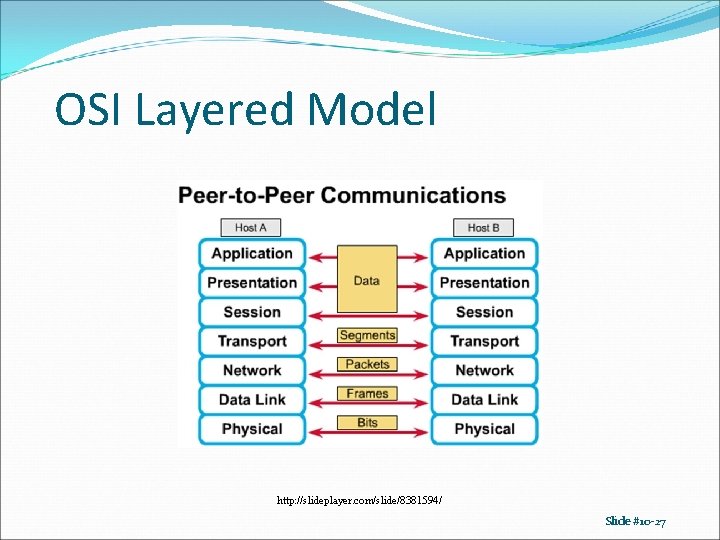
OSI Layered Model http: //slideplayer. com/slide/8381594/ Slide #10 -27
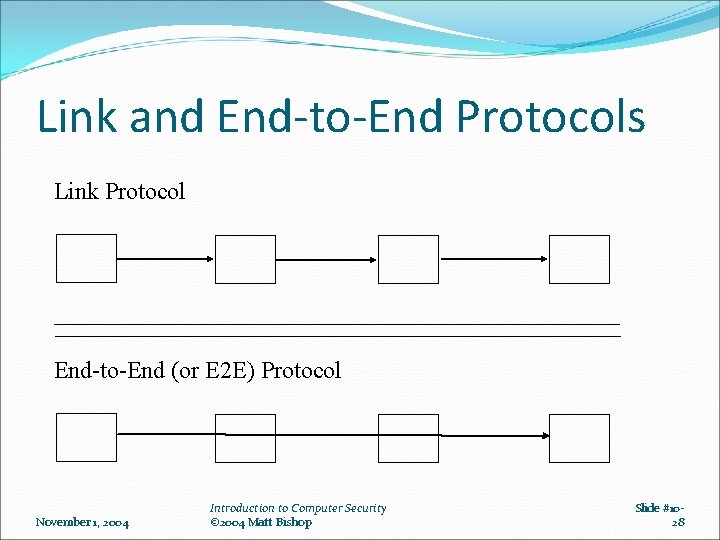
Link and End-to-End Protocols Link Protocol End-to-End (or E 2 E) Protocol November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1028

Encryption Link encryption Each host enciphers message so host at “next hop” can read it Message can be read at intermediate hosts End-to-end encryption Host enciphers message so host at other end of communication can read it Message cannot be read at intermediate hosts November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1029
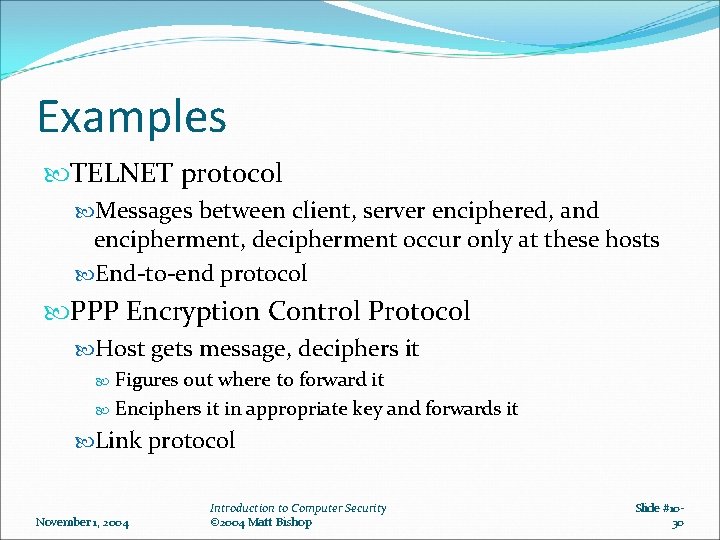
Examples TELNET protocol Messages between client, server enciphered, and encipherment, decipherment occur only at these hosts End-to-end protocol PPP Encryption Control Protocol Host gets message, deciphers it Figures out where to forward it Enciphers it in appropriate key and forwards it Link protocol November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1030
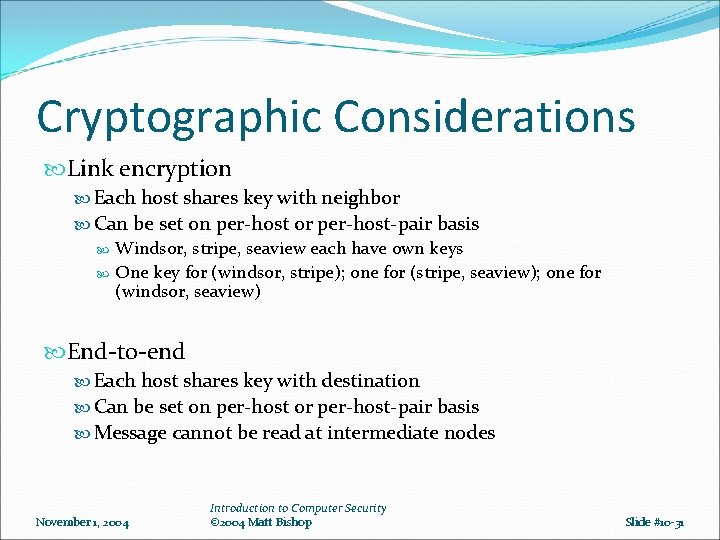
Cryptographic Considerations Link encryption Each host shares key with neighbor Can be set on per-host or per-host-pair basis Windsor, stripe, seaview each have own keys One key for (windsor, stripe); one for (stripe, seaview); one for (windsor, seaview) End-to-end Each host shares key with destination Can be set on per-host or per-host-pair basis Message cannot be read at intermediate nodes November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #10 -31
Traffic Analysis Link encryption Can protect headers of packets Possible to hide source and destination Note: may be able to deduce this from traffic flows End-to-end encryption Cannot hide packet headers Intermediate nodes need to route packet Attacker can read source, destination November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1032
Privacy-Enhanced Electronic Mail (PEM) Applications layer protocol http: //www. intelligentedu. com/computer_security_for_everyone/10 -email-security. html Slide #1033
Goals of PEM Confidentiality 1. • Only sender and recipient(s) can read message Origin authentication 2. • Identify the sender precisely Data integrity 3. • Any changes in message are easy to detect Non-repudiation of origin 4. • November 1, 2004 Whenever possible … Introduction to Computer Security © 2004 Matt Bishop Slide #1034
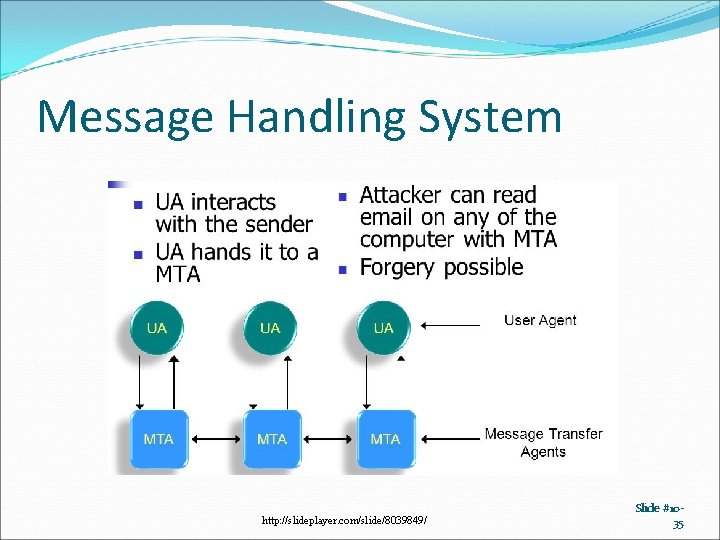
Message Handling System http: //slideplayer. com/slide/8039849/ Slide #1035

Design Principles Do not change related existing protocols Cannot alter SMTP Do not change existing software Need compatibility with existing software Make use of PEM optional Available if desired, but email still works without them Some recipients may use it, others not Enable communication without prearrangement Out-of-bands authentication, key exchange problematic November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1036
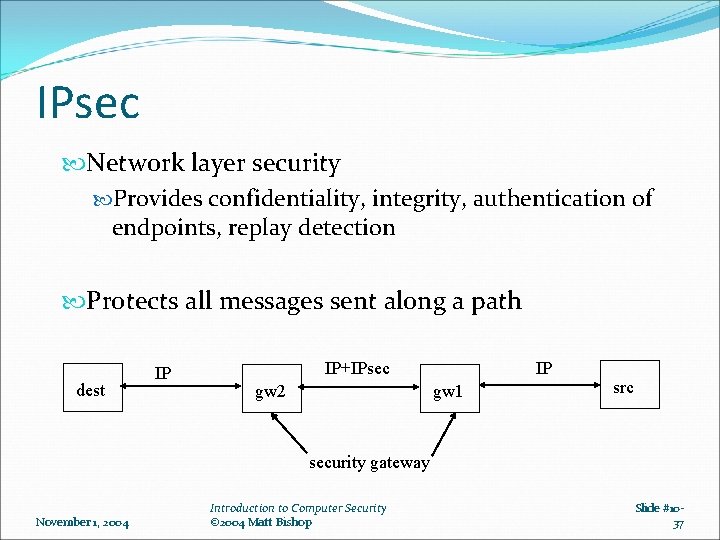
IPsec Network layer security Provides confidentiality, integrity, authentication of endpoints, replay detection Protects all messages sent along a path dest IP IP+IPsec gw 2 IP gw 1 src security gateway November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #1037
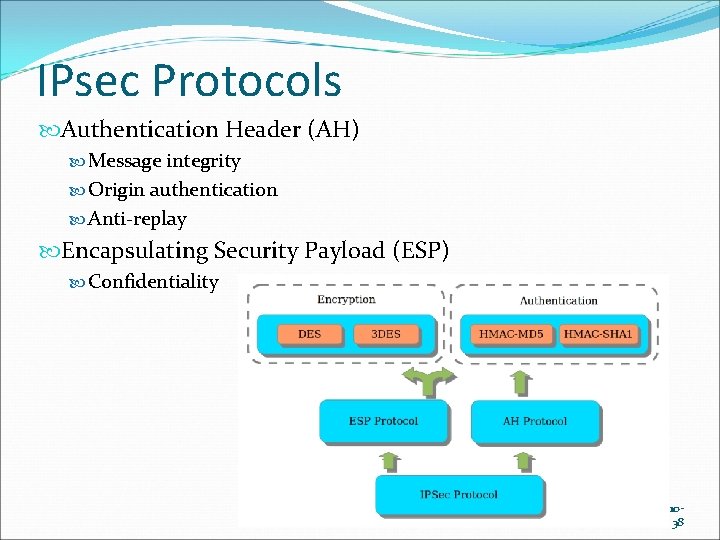
IPsec Protocols Authentication Header (AH) Message integrity Origin authentication Anti-replay Encapsulating Security Payload (ESP) Confidentiality Slide #1038

IPsec Transport Mode Encapsulate IP packet data area Use IP to send IPsec-wrapped data packet Note: IP header not protected http: //www. rfwireless-world. com/Terminology/IPsec. html Slide #10 -39

IPsec Tunnel Mode Encapsulate IP packet (IP header and IP data) Use IP to send IPsec-wrapped packet Note: IP header protected http: //www. rfwireless-world. com/Terminology/IPsec. html Slide #10 -40
- Slides: 40