Chapter 1 Introduction Components of computer security Threats














- Slides: 26

Chapter 1: Introduction • • Components of computer security Threats Policies and mechanisms The role of trust Assurance Operational Issues Human Issues Slide #1 -1

Basic Components • Confidentiality • Integrity • Availability Slide #1 -2

Confidentiality Keeping data and resources hidden • Need-to-know principle • Illicit access to information • Tools: cryptography – Encrypting data with a cryptographic key will assure privacy: only those with the decryption key can access the contents. • Resource hiding • Access control mechanisms support privacy Slide #1 -3

Integrity • Data integrity (integrity) – The data is authentic, e. g. , has not been tampered/corrupted • Origin integrity (authentication) – The source of the information is authentic • Integrity mechanisms fall intio two classes: – Prevention mechanisms (block unauthorized attempts) – Detection mechanisms (analyze system events and report integrity failures) Slide #1 -4

Availability Enable access to data and resources • Reliability • Denial of service attacks • Can be the most difficult to detect because the analyst must determine if an unusual access pattern is attributable to deliberate manipulation of resources or of the environment (reliability failure) Slide #1 -5

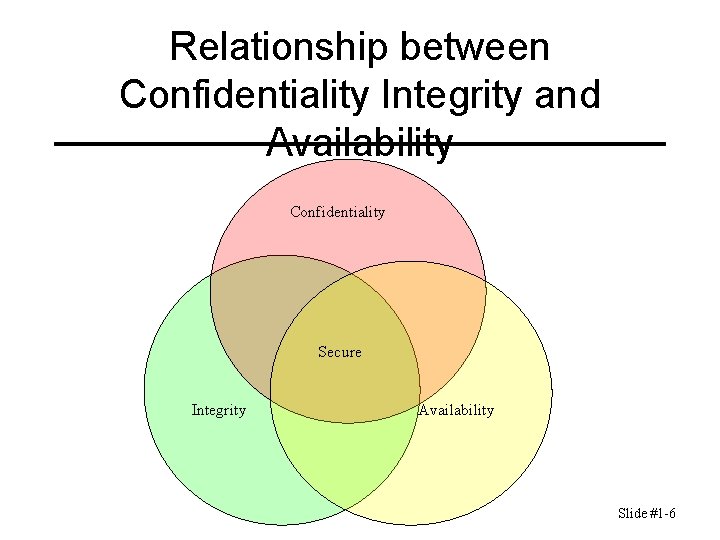
Relationship between Confidentiality Integrity and Availability Confidentiality Secure Integrity Availability Slide #1 -6

Other security requirements • Reliability – deals with accidental damage, • Safety – deals with the impact of system failure caused by the environment, • Dependability – reliance can be justifiably placed on the system • Survivability – deals with the recovery of the system after massive failure. • Accountability -- actions affecting security must be traceable to the responsible party. For this, – Audit information must be kept and protected, Slide # -7

Threats • A threat is a potential violation of security. • The violation need not occur for there to be a threat. • The fact that the violation might occur means that the actions that might cause it should be guarder against. • The three security services discussed earlier (confidentiality, integrity, availability) counter threats to the security of the system. Slide #1 -8

Classes of Threats • Disclosure – Snooping • Deception – Modification, spoofing, repudiation of origin, denial of receipt • Disruption – Modification • Usurpation – Modification, spoofing, delay, denial of service Slide #1 -9

Policies and Mechanisms • Policy says what is, and what is not, allowed – This defines “security” for the site/system/etc. – May be expressed in • natural language, which is usually imprecise but easy to understand • mathematics, which is usually precise but hard to understand • policy languages, which look like some form of programming language and try to balance precision with ease of understanding Slide #1 -10

Policies and Mechanisms • Mechanisms enforce policies – Mechanism = a method, tool or procedure – Mechanisms may be • technical, in which controls in the computer enforce the policy: for example, the requirement that a user supply a password to authenticate herself before using the computer • procedural, in which controls outside the system enforce the policy: for example, firing someone for bringing in a disk containing a game program obtained from an untrusted source Slide #1 -11

Policies and Mechanisms • Composition of policies – If policies conflict, discrepancies may create security vulnerabilities – The composition problem requires checking for inconsistencies among policies. – If, for example, one policy allows students and faculty access to all data, and the other allows only faculty access to all the data, then they must be resolved (e. g. , partition the data so that students and faculty can access some data, and only faculty access the other data). Slide #1 -12

Goals of Security • Prevention – Prevent attackers from violating security policy • Detection – Detect attackers’ violation of security policy • Recovery – Stop attack, assess and repair damage – Continue to function correctly even if attack succeeds Slide #1 -13

Trust and Assumptions • Trust underlies all aspects of security • Policies – Unambiguously partition system states – Correctly capture security requirements • Mechanisms – Assumed to enforce policy – Support mechanisms work correctly Slide #1 -14

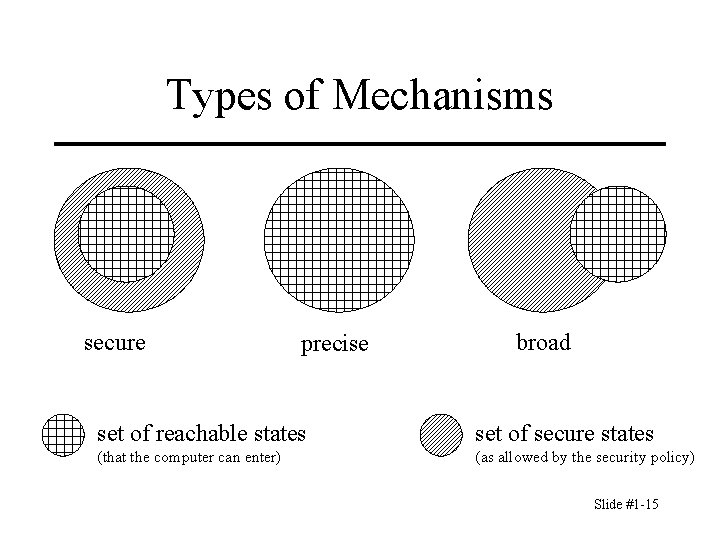
Types of Mechanisms secure precise broad set of reachable states set of secure states (that the computer can enter) (as allowed by the security policy) Slide #1 -15

Assurance • Specification – Requirements analysis – Statement of desired functionality • Design – How system will meet specification • Implementation – Programs/systems that carry out design Slide #1 -16

Assurance • Assurance is a measure of how well the system meets its requirements – informally, how much you can trust the system to do what it is supposed to do. It does not say what the system is to do; rather, it only covers how well the system does it. Slide #1 -17

Assurance • Specifications arise from requirements analysis, in which the goals of the system are determined. – The specification says what the system must do to meet those requirements. – It is a statement of functionality, not assurance, and can be very formal (mathematical) or informal (natural language). – The specification can be high-level or low-level (for example, describing what the system as a whole is to do vs. what specific modules of code are to do). Slide #1 -18

Assurance • The design architects the system to satisfy, or meet, the specifications – Typically, the design is layered by breaking the system into abstractions, and then refining the abstractions as you work your way down to the hardware. – An analyst also must show the design matches the specification. – The implementation is the actual coding of the modules and software components. These must be correct (perform as specified) and their aggregation must satisfy the design. Slide #1 -19

Operational Issues • Cost-Benefit Analysis – Is it cheaper to prevent or recover? • Risk Analysis – Should we protect something? – How much should we protect this thing? • Laws and Customs – Are desired security measures illegal? – Will people do them? Slide #1 -20

Human Issues • Organizational Problems – Power and responsibility • those responsible have the power to enforce it • For example, – system administrators are responsible for security, but only security officers can make the rules. • People problems – Outsiders and insiders • It is speculated that insiders account for 80 -90% of all security problems – Social engineering Slide #1 -21

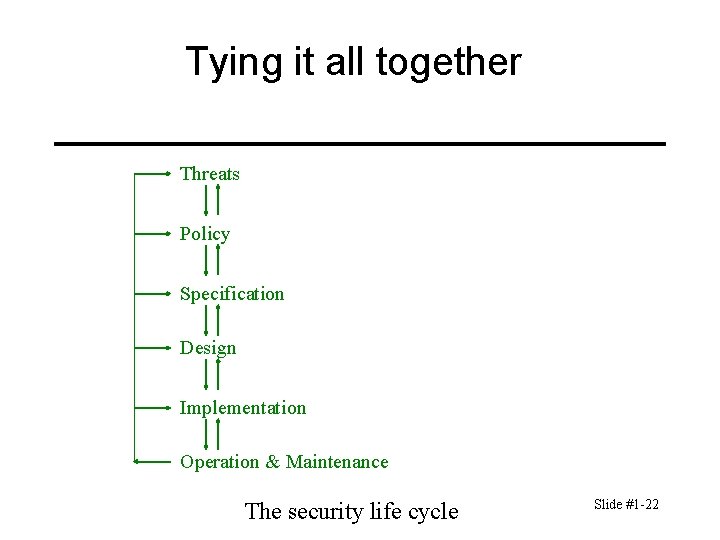
Tying it all together Threats Policy Specification Design Implementation Operation & Maintenance The security life cycle Slide #1 -22

Key Points • Policy defines security, and mechanisms enforce security – Confidentiality – Integrity – Availability • Trust and knowing assumptions • Importance of assurance • The human factor Slide #1 -23

Key Points How to achieve Computer Security: 1. Security principles/concepts: explore general principles/concepts that can be used as a guide to design secure information processing systems. 2. Security mechanisms: explore some of the security mechanisms that can be used to secure information processing systems. 3. Physical/Organizational security: consider Slide #1 -24 physical & organizational security measures

References Even at this general level there is disagreement on the precise definitions of some of the required security aspects. References: • Orange book – US Dept of Defense, Trusted Computer System Evaluation Criteria. • ITSEC – European Trusted Computer System Product Criteria. • CTCPEC – Canadian Trusted Computer System Slide #1 -25 Product Criteria

Fundamental Dilemma: Functionality or Assurance • Security mechanisms need additional computation • Security policies interfere with working patterns, and can be very inconvenient • Managing security requires additional effort and costs. • Ideally there should be a tradeoff • Risk analysis Slide #1 -26