Chapter 1 Databases and Database Users Copyright 2011

Chapter 1 Databases and Database Users Copyright © 2011 Pearson Education, Inc. Publishing as Pearson Addison-Wesley
Chapter 1 Outline Types of Databases and Database Applications Basic Definitions Typical DBMS Functionality Example of a Database (UNIVERSITY) Main Characteristics of the Database Approach Types of Database Users Advantages of Using the Database Approach Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Types of Database Applications Traditional Applications: More Recent Applications: Numeric and Textual Databases in Business Applications Multimedia Databases (images, videos, voice, etc. ) Geographic Information Systems (GIS) Data Warehouses Real-time and Active Databases Many other applications Initial part of book focuses on traditional applications A number of recent applications are described later in the book (for example, Chapters 26, 27, 28, 29) Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Basic Definitions Database: A collection of related data. Data: Known facts that can be recorded and have an implicit meaning. Mini-world: Some part of the real world about which data is stored in a database. For example, student registration, grades and transcripts at a university. Database Management System (DBMS): A software package/system to facilitate the creation and maintenance of a computerized database. Database System: The DBMS software together with the data itself. Sometimes, the application programs and interfaces are also included. Copyright © 2011 Ramez Elmasri and Shamkant Navathe
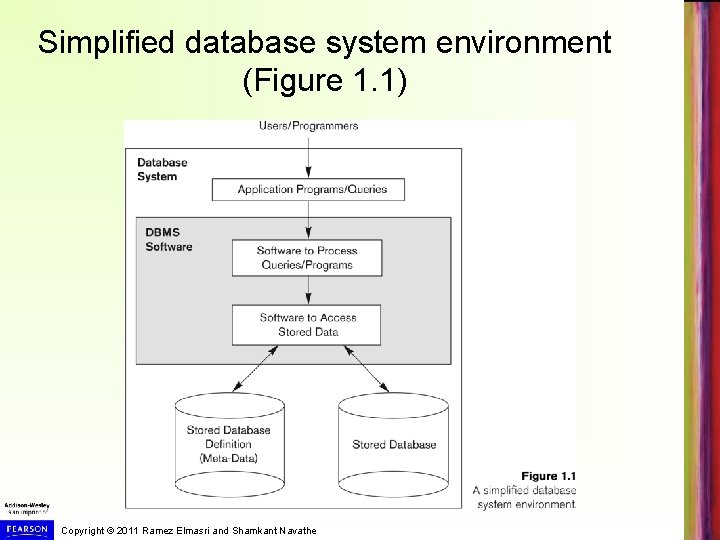
Simplified database system environment (Figure 1. 1) Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Typical DBMS Functionality Define a particular database in terms of its data types, structures, and constraints Construct or Load the initial database contents on a secondary storage medium (typically hard disk) Manipulating the database: Retrieval: Querying, generating reports Modification: Insertions, deletions and updates to its content Accessing/changing the database through Web applications Processing and Sharing by a set of concurrent users and application programs – yet, keeping all data valid and consistent Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Typical DBMS Functionality (cont. ) Other features: Protection or Security measures to prevent unauthorized access “Active” processing to take internal actions on data Presentation and Visualization of data Maintaining the database and associated programs over the lifetime of the database application Called database, software, and system life-cycle maintenance Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Example of a Database UNIVERSITY Application Mini-world for the example: Part of a UNIVERSITY environment. Some mini-world entities: STUDENTs COURSEs SECTIONs (of COURSEs) (academic) DEPARTMENTs INSTRUCTORs Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Example of a Database UNIVERSITY Application (cont. ) Some mini-world relationships: SECTIONs are of specific COURSEs STUDENTs take SECTIONs COURSEs have prerequisite COURSEs INSTRUCTORs teach SECTIONs COURSEs are offered by DEPARTMENTs STUDENTs major in DEPARTMENTs Note: The above entities and relationships are typically expressed in a conceptual data model, such as the ENTITY-RELATIONSHIP data model (see Chapters 7, 8) Copyright © 2011 Ramez Elmasri and Shamkant Navathe

Example of a Database UNIVERSITY Application (cont. ) The next two slides (Figure 1. 2 from textbook) show what a simple UNIVERSITY database may look like Copyright © 2011 Ramez Elmasri and Shamkant Navathe

Continued next page… Copyright © 2011 Ramez Elmasri and Shamkant Navathe
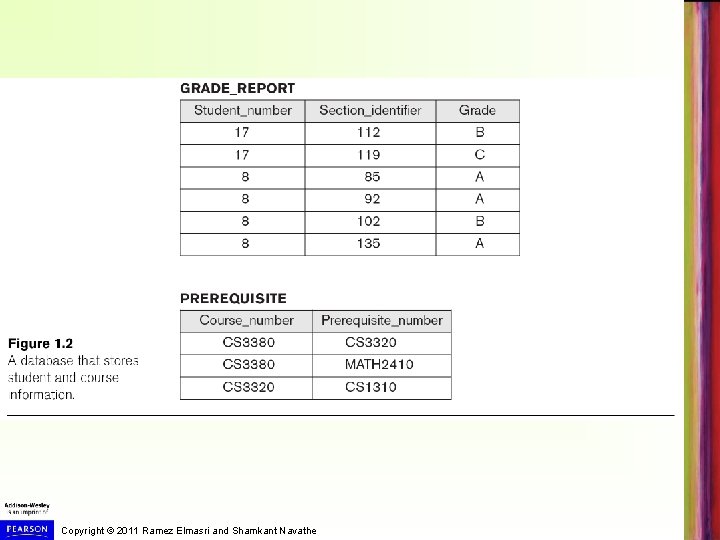
Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Main Characteristics of the Database Approach Self-describing nature of a database system: A DBMS catalog stores the description of a particular database (e. g. data structures, types, and constraints) The description is called meta-data (see next slide). This allows the DBMS software to work with different database applications (university, bank, airlines, etc. ) Insulation between programs and data: Called program-data independence. Allows changing data structures and data storage organization without having to change the DBMS access programs. Copyright © 2011 Ramez Elmasri and Shamkant Navathe
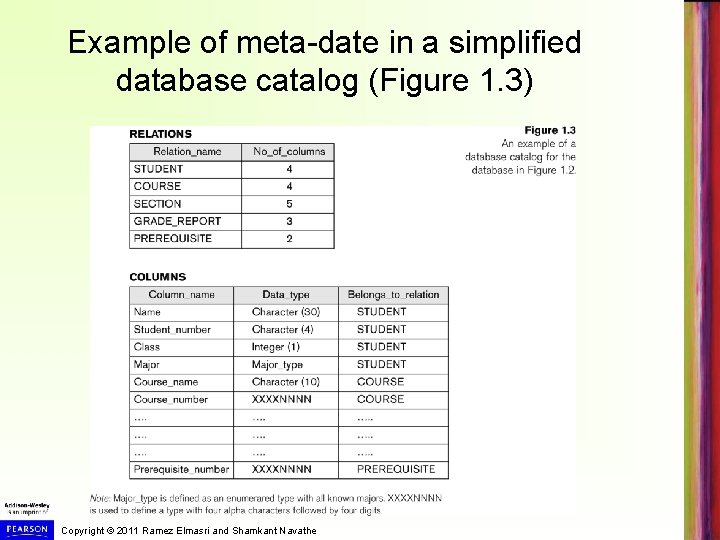
Example of meta-date in a simplified database catalog (Figure 1. 3) Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Main Characteristics of the Database Approach (cont. ) Insulation between programs and data (cont. ): Accomplished through data abstraction A data model is used to hide storage details and present the users with a conceptual view of the database. Programs refer to the data model constructs rather than data storage details Support of multiple views of the data: Each user may see a different view of the database, which describes only the data of interest to that user. Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Main Characteristics of the Database Approach (cont. ) Sharing of data and multi-user transaction processing: Allowing a set of user transactions to access and update the database concurrently (at the same time). Concurrency control within the DBMS guarantees that each transaction is correctly executed or aborted Recovery subsystem ensures each completed transaction has its effect permanently recorded in the database OLTP (Online Transaction Processing) is a major part of database applications (allows hundreds of concurrent transactions to execute per second) Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Types of Database Users may be divided into Those who actually use and control the database content, and those who design, develop and maintain database applications (called “Actors on the Scene”), and Those who design and develop the DBMS software and related tools, and the computer systems operators (called “Workers Behind the Scene”). Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Database Users: End-users Actors on the scene End-users: Use the database for queries, reports, and updating the database content. Can be categorized into: Casual end-users: access database occasionally when needed Naïve (or Parametric) end-users: largest section of end-user population. Use previously implemented and tested programs (called “canned transactions”) to access/update the database. Examples are bank-tellers or hotel reservation clerks or sales clerks. Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Database Users: End-users (cont) Sophisticated end-users: These include business analysts, scientists, engineers, others thoroughly familiar with the system capabilities. Many use tools in the form of software packages that work closely with the stored database. Stand-alone end-users: Mostly maintain personal databases using ready-touse packaged applications. An example is a tax program user that creates its own internal database. Another example is a user that maintains an address book Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Database Users: DB Administrators (DBAs) and Designers Actors on the scene (continued) Database administrators: Responsible for authorizing/controlling access to the database; coordinating and monitoring its use; acquiring software and hardware resources; and monitoring efficiency of operations. Database Designers: Responsible for defining database structure, constraints, and transactions; communicate with users to understand their needs. Copyright © 2011 Ramez Elmasri and Shamkant Navathe
Advantages of Using the Database Approach Controlling redundancy in data storage and in development and maintenance efforts. Restricting unauthorized access to data. Providing persistent storage for program Objects Sharing of data among multiple users. In Object-oriented DBMSs – see Chapter 11 Providing Storage Structures (e. g. indexes) for efficient Query Processing Copyright © 2011 Ramez Elmasri and Shamkant Navathe

Advantages of Using the Database Approach (cont. ) Providing backup and recovery services. Providing multiple interfaces to different classes of users. Representing complex relationships among data. Enforcing integrity constraints on the database. Drawing inferences and actions from the stored data using deductive and active rules Allowing multiple “views” of the same data (see next slide, Figure 1. 5 from textbook) Copyright © 2011 Ramez Elmasri and Shamkant Navathe

Copyright © 2011 Ramez Elmasri and Shamkant Navathe
- Slides: 23