Chap 2 Basic Switch Concepts and Configuration Learning

Chap 2 – Basic Switch Concepts and Configuration Learning Objectives • • Summarise the operation of Ethernet as defined for 100/1000 Mbps LANs in the IEEE 802. 3 standard. Explain the functions that enable a switch to forward Ethernet frames in a LAN. Configure a switch for operation in a network designed to support voice, video, and data transmissions. Configure basic security on a switch that will operate in a network designed to support voice, video, and data transmissions. 1 Chapter 2
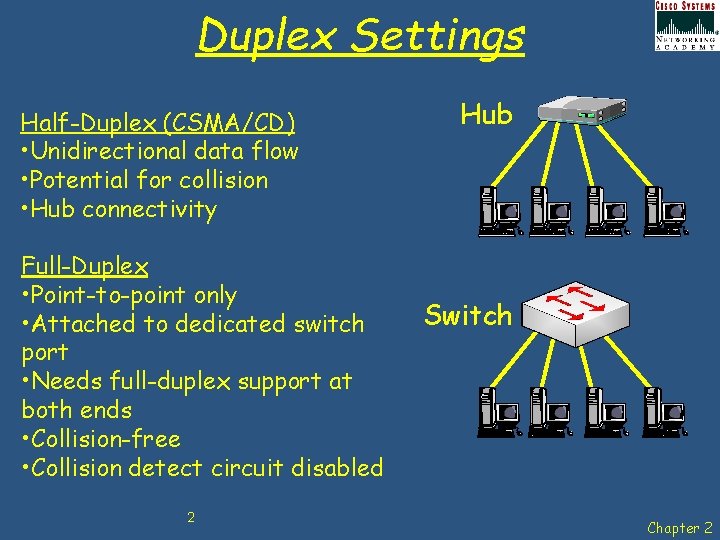
Duplex Settings Half-Duplex (CSMA/CD) • Unidirectional data flow • Potential for collision • Hub connectivity Full-Duplex • Point-to-point only • Attached to dedicated switch port • Needs full-duplex support at both ends • Collision-free • Collision detect circuit disabled 2 Hub Switch Chapter 2
Duplex Settings The Cisco Catalyst switches have three settings: • The auto option sets auto-negotiation of duplex mode. With auto-negotiation enabled, the two ports communicate to decide the best mode of operation. • The full option sets full-duplex mode. • The half option sets half-duplex mode. 3 Chapter 2
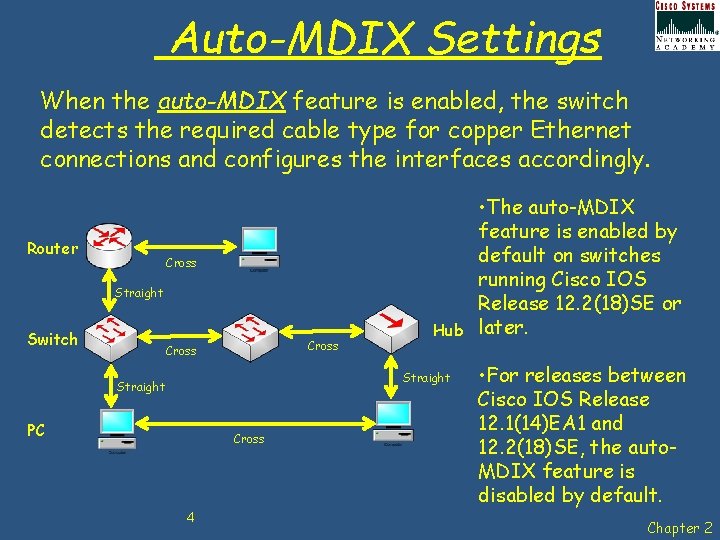
Auto-MDIX Settings When the auto-MDIX feature is enabled, the switch detects the required cable type for copper Ethernet connections and configures the interfaces accordingly. Router Cross Straight Switch Cross Hub Straight PC Cross 4 • The auto-MDIX feature is enabled by default on switches running Cisco IOS Release 12. 2(18)SE or later. • For releases between Cisco IOS Release 12. 1(14)EA 1 and 12. 2(18)SE, the auto. MDIX feature is disabled by default. Chapter 2
Switch MAC Tables - Summary • • Filter, forward and Flood network traffic using the physical address (MAC) of host computers Reads each frame as it passes through the network Places the source address in a MAC filter table and keeps track of port it was received on Examines the destination address and consults its table before processing the frame 5 Chapter 2
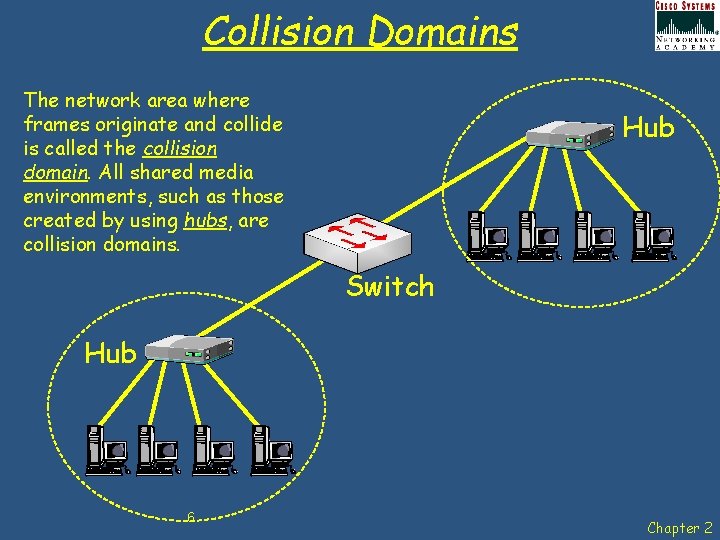
Collision Domains The network area where frames originate and collide is called the collision domain. All shared media environments, such as those created by using hubs, are collision domains. Hub Switch Hub 6 Chapter 2
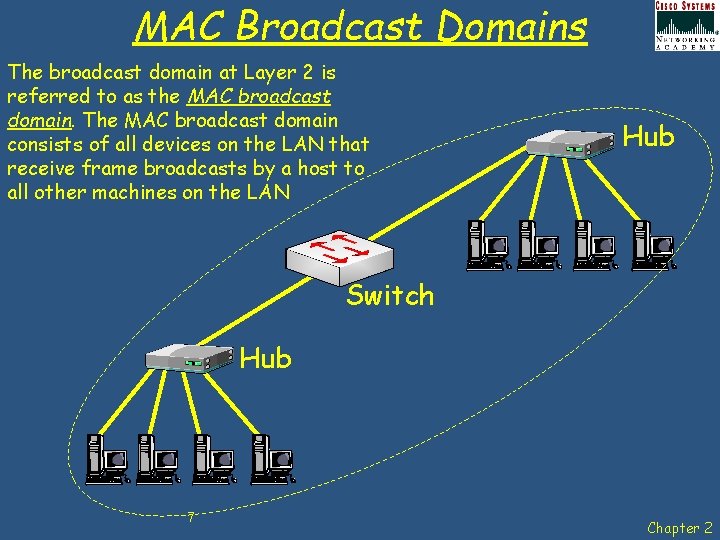
MAC Broadcast Domains The broadcast domain at Layer 2 is referred to as the MAC broadcast domain. The MAC broadcast domain consists of all devices on the LAN that receive frame broadcasts by a host to all other machines on the LAN Hub Switch Hub 7 Chapter 2
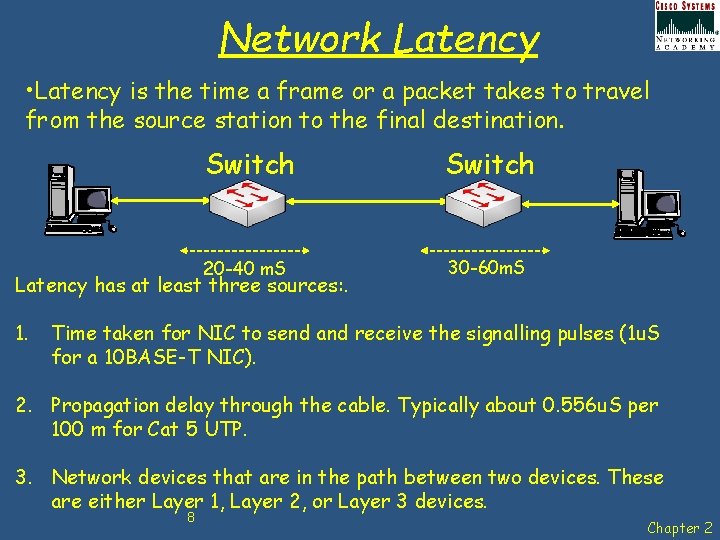
Network Latency • Latency is the time a frame or a packet takes to travel from the source station to the final destination. Switch 20 -40 m. S 30 -60 m. S Latency has at least three sources: . 1. Time taken for NIC to send and receive the signalling pulses (1 u. S for a 10 BASE-T NIC). 2. Propagation delay through the cable. Typically about 0. 556 u. S per 100 m for Cat 5 UTP. 3. Network devices that are in the path between two devices. These are either Layer 1, Layer 2, or Layer 3 devices. 8 Chapter 2
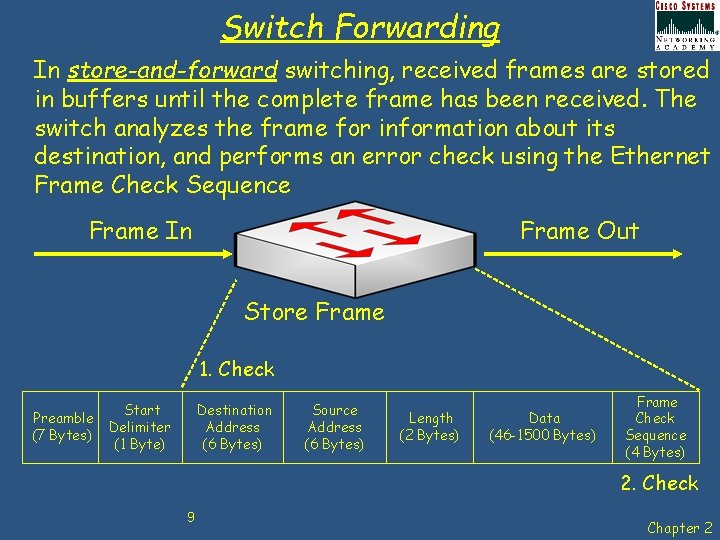
Switch Forwarding In store-and-forward switching, received frames are stored in buffers until the complete frame has been received. The switch analyzes the frame for information about its destination, and performs an error check using the Ethernet Frame Check Sequence Frame In Frame Out Store Frame 1. Check Preamble (7 Bytes) Start Delimiter (1 Byte) Destination Address (6 Bytes) Source Address (6 Bytes) Length (2 Bytes) Data (46 -1500 Bytes) Frame Check Sequence (4 Bytes) 2. Check 9 Chapter 2
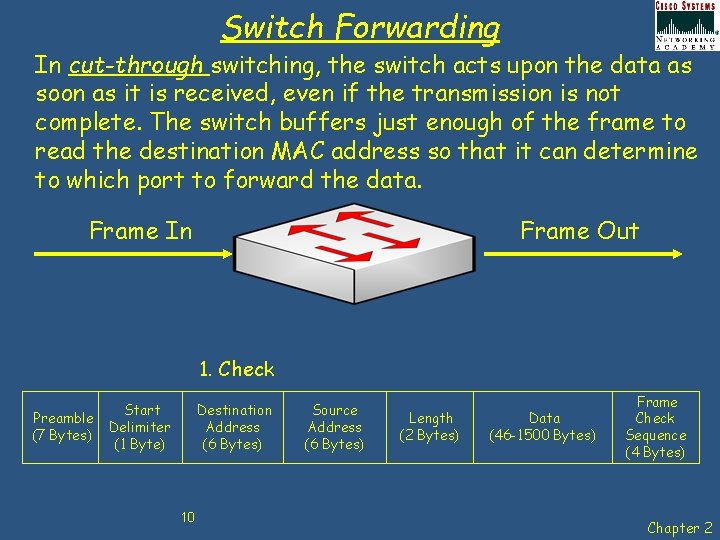
Switch Forwarding In cut-through switching, the switch acts upon the data as soon as it is received, even if the transmission is not complete. The switch buffers just enough of the frame to read the destination MAC address so that it can determine to which port to forward the data. Frame In Frame Out 1. Check Preamble (7 Bytes) Start Delimiter (1 Byte) Destination Address (6 Bytes) 10 Source Address (6 Bytes) Length (2 Bytes) Data (46 -1500 Bytes) Frame Check Sequence (4 Bytes) Chapter 2
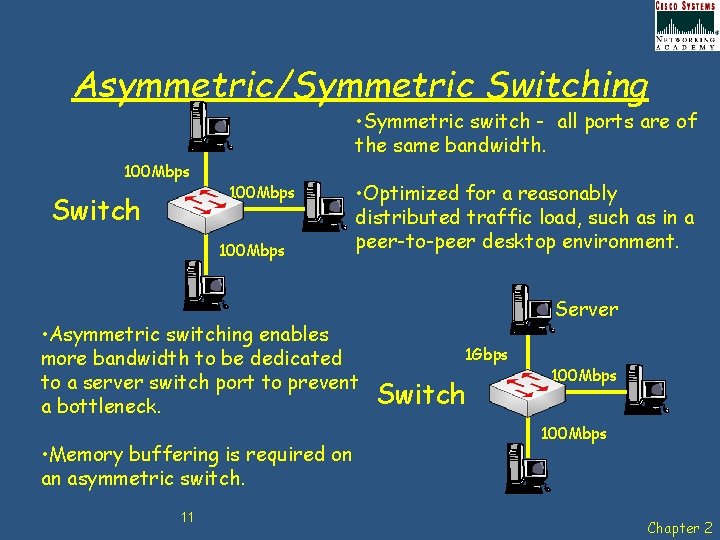
Asymmetric/Symmetric Switching • Symmetric switch - all ports are of the same bandwidth. 100 Mbps Switch 100 Mbps • Optimized for a reasonably distributed traffic load, such as in a peer-to-peer desktop environment. • Asymmetric switching enables more bandwidth to be dedicated to a server switch port to prevent a bottleneck. • Memory buffering is required on an asymmetric switch. 11 Server 1 Gbps Switch 100 Mbps Chapter 2
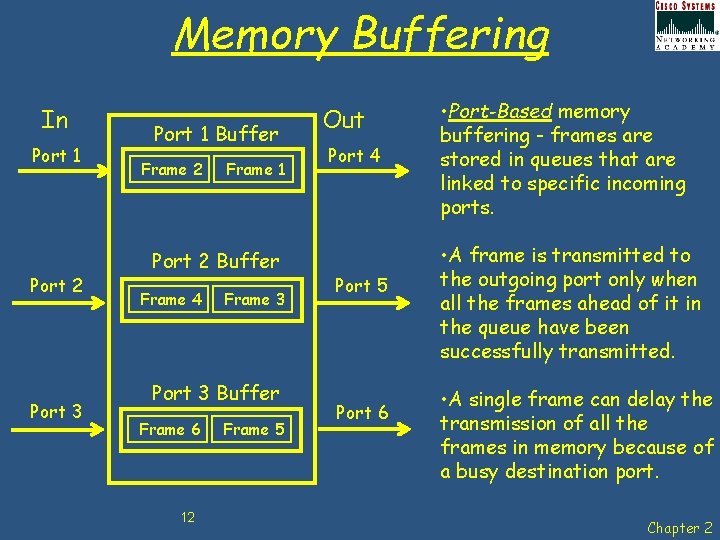
Memory Buffering In Port 1 Port 2 Port 3 Port 1 Buffer Frame 2 Frame 1 Port 2 Buffer Frame 4 Frame 3 Port 3 Buffer Frame 6 12 Frame 5 Out Port 4 Port 5 Port 6 • Port-Based memory buffering - frames are stored in queues that are linked to specific incoming ports. • A frame is transmitted to the outgoing port only when all the frames ahead of it in the queue have been successfully transmitted. • A single frame can delay the transmission of all the frames in memory because of a busy destination port. Chapter 2
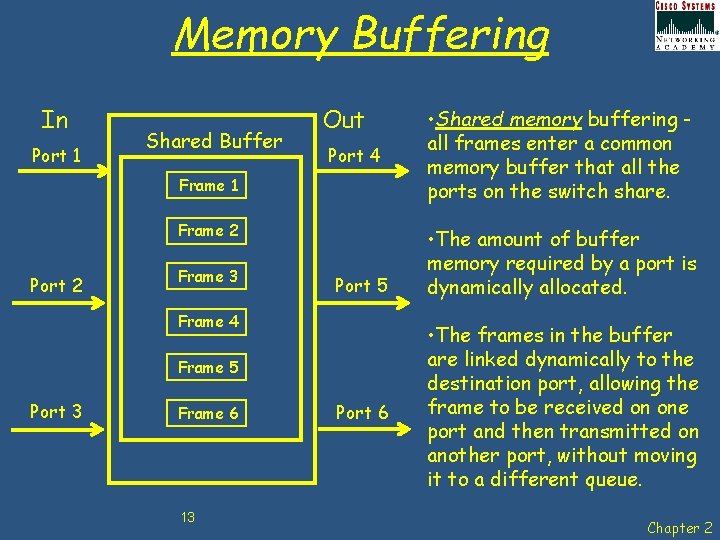
Memory Buffering In Port 1 Shared Buffer Out Port 4 Frame 1 Frame 2 Port 2 Frame 3 Port 5 Frame 4 Frame 5 Port 3 Frame 6 13 Port 6 • Shared memory buffering all frames enter a common memory buffer that all the ports on the switch share. • The amount of buffer memory required by a port is dynamically allocated. • The frames in the buffer are linked dynamically to the destination port, allowing the frame to be received on one port and then transmitted on another port, without moving it to a different queue. Chapter 2
Layer 2 & 3 Switching • • • Instead of using only the Layer 2 MAC address information forwarding decisions, a Layer 3 switch can also use IP address information. In addition to associating MAC addresses ports, a Layer 3 switch can also learn which IP addresses are associated with its interfaces. This allows the Layer 3 switch to direct traffic throughout the network based on IP address information. Layer 3 switches are also capable of performing Layer 3 routing functions, reducing the need for dedicated routers on a LAN. Because Layer 3 switches have specialized switching hardware, they can typically route data as quickly as they can switch. 14 Chapter 2
Layer 2 & 3 Switching • Routers perform additional Layer 3 services that Layer 3 switches are not capable of performing. Routers are also capable of performing packet forwarding tasks not found on Layer 3 switches. • Dedicated routers are more flexible in their support of WAN interface cards (WIC), making them the preferred, and sometimes only, choice for connecting to a WAN. 15 Chapter 2
Cisco Switch Boot Sequence 1. Switch loads the boot loader software from NVRAM 2. Boot Loader performs: • • Low-level CPU initialisation Performs POST for CPU subsystem Initialise flash file system on system board Loads default IOS into RAM and boots the switch 3. Operating system runs the config. txt file, stored in flash memory. 16 Chapter 2
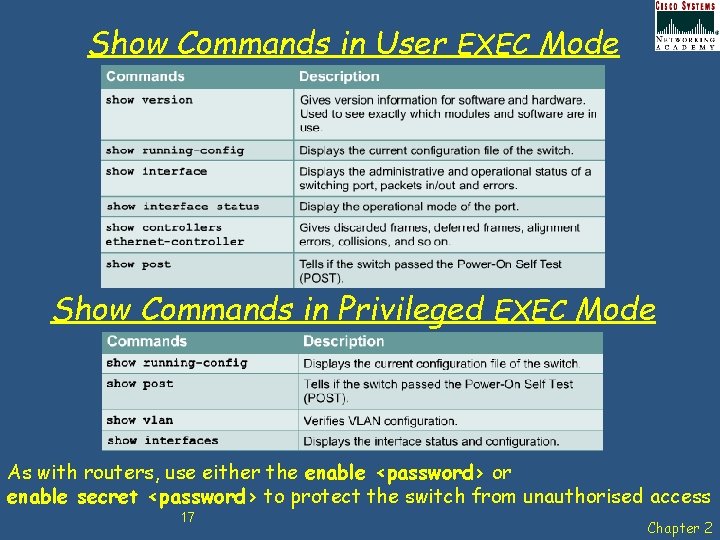
Show Commands in User EXEC Mode Show Commands in Privileged EXEC Mode As with routers, use either the enable <password> or enable secret <password> to protect the switch from unauthorised access 17 Chapter 2

Examining Help in the Switch CLI Command syntax help: If unfamiliar with which commands are available in the current context within the Cisco IOS CLI enter the ? command. Word help: Enter the first few character in a command sequence followed by ? . Do not include a space before the question mark. 18 Chapter 2
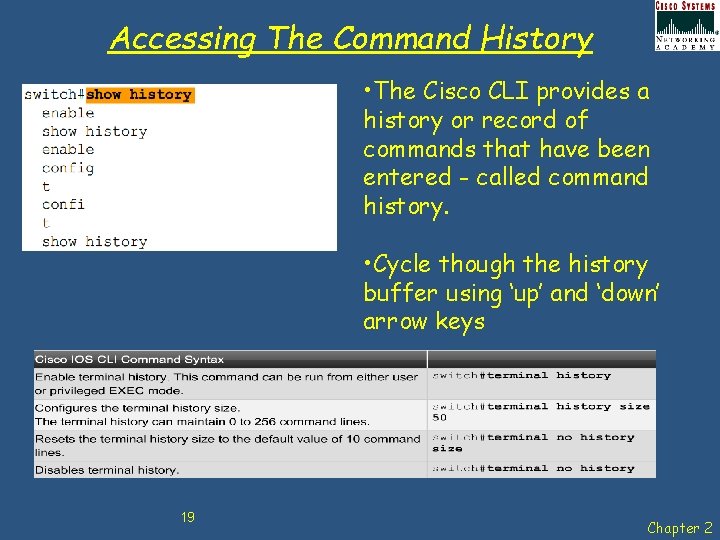
Accessing The Command History • The Cisco CLI provides a history or record of commands that have been entered - called command history. • Cycle though the history buffer using ‘up’ and ‘down’ arrow keys 19 Chapter 2
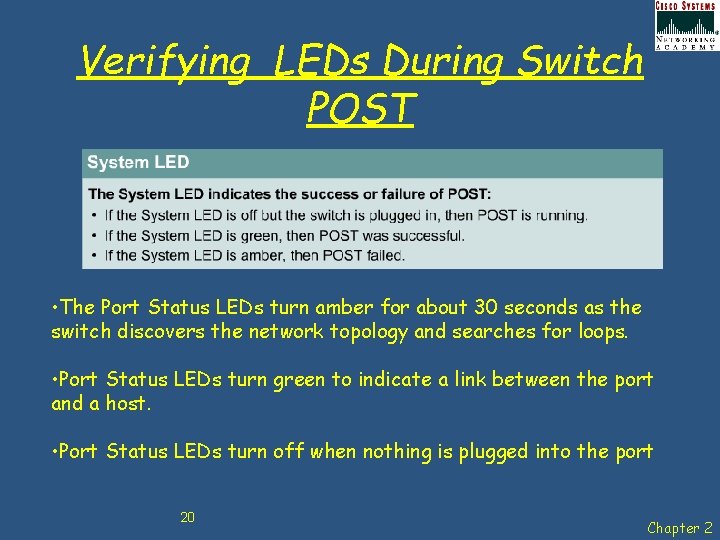
Verifying LEDs During Switch POST • The Port Status LEDs turn amber for about 30 seconds as the switch discovers the network topology and searches for loops. • Port Status LEDs turn green to indicate a link between the port and a host. • Port Status LEDs turn off when nothing is plugged into the port 20 Chapter 2
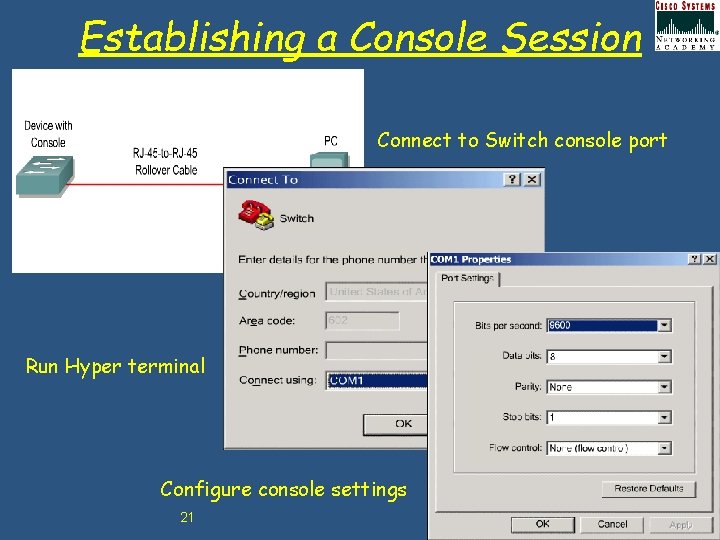
Establishing a Console Session Connect to Switch console port Run Hyper terminal Configure console settings 21 Chapter 2
Set IP Address and Default Gateway • • • To allow the switch to be accessible by Telnet and other TCP/IP applications, IP addresses and a default gateway should be set. By default, VLAN 1 is the management VLAN (more later). Security risk, better to assign a random VLAN as the management VLAN In a switch-based network, all internetworking devices should be in the management VLAN. This will allow a single management workstation to access, configure, and manage all the internetworking devices. The default gateway is only for management purposes, not for user Ethernet frames (and packets) – allows telnet from this switch into a device on another network. 22 Chapter 2
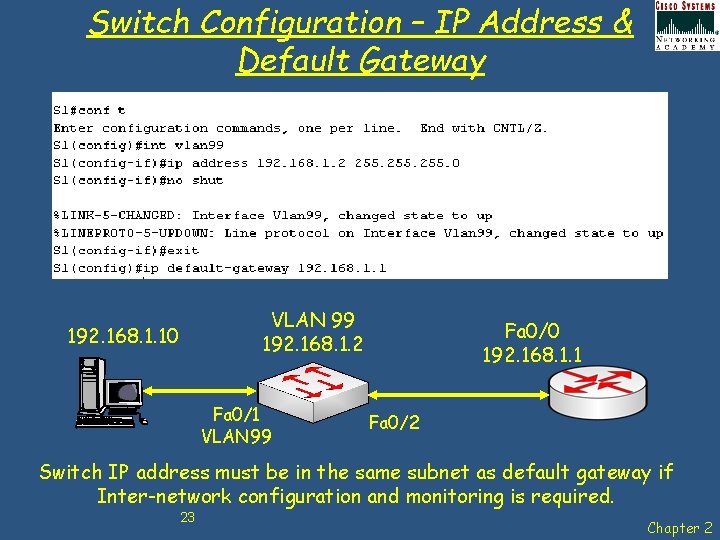
Switch Configuration – IP Address & Default Gateway VLAN 99 192. 168. 1. 2 192. 168. 1. 10 Fa 0/1 VLAN 99 Fa 0/0 192. 168. 1. 1 Fa 0/2 Switch IP address must be in the same subnet as default gateway if Inter-network configuration and monitoring is required. 23 Chapter 2
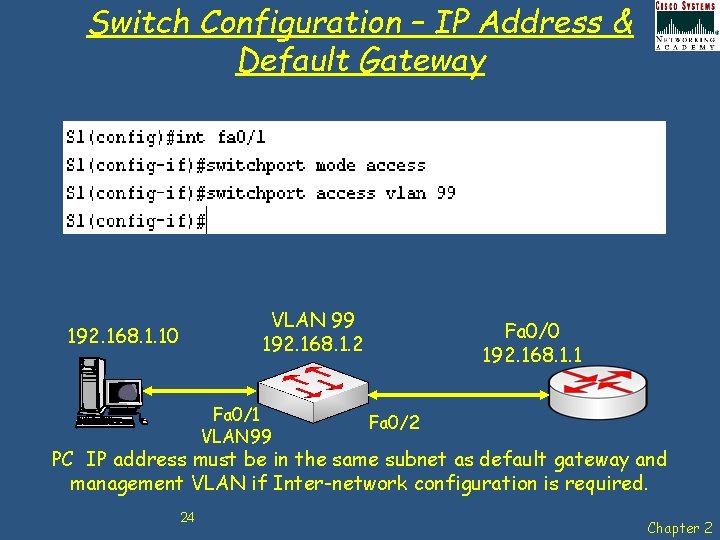
Switch Configuration – IP Address & Default Gateway VLAN 99 192. 168. 1. 2 192. 168. 1. 10 Fa 0/1 VLAN 99 Fa 0/0 192. 168. 1. 1 Fa 0/2 PC IP address must be in the same subnet as default gateway and management VLAN if Inter-network configuration is required. 24 Chapter 2
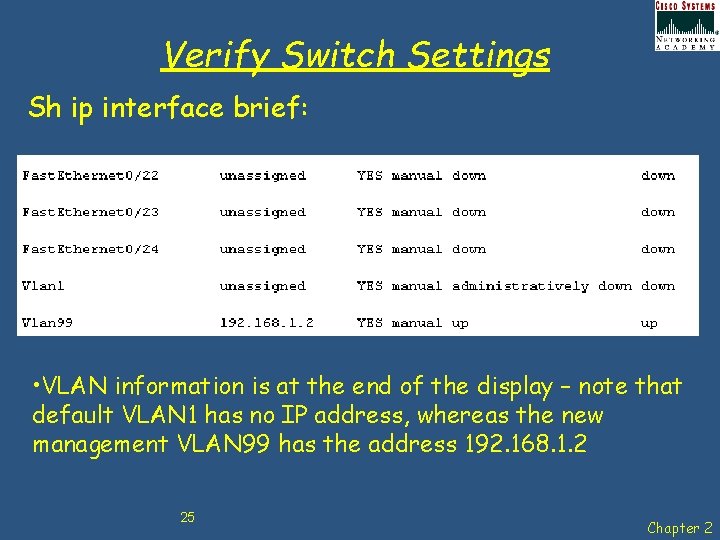
Verify Switch Settings Sh ip interface brief: • VLAN information is at the end of the display – note that default VLAN 1 has no IP address, whereas the new management VLAN 99 has the address 192. 168. 1. 2 25 Chapter 2
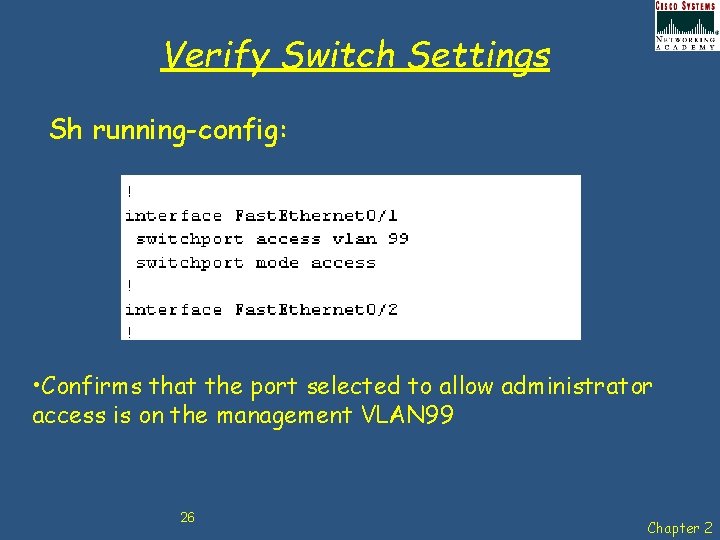
Verify Switch Settings Sh running-config: • Confirms that the port selected to allow administrator access is on the management VLAN 99 26 Chapter 2
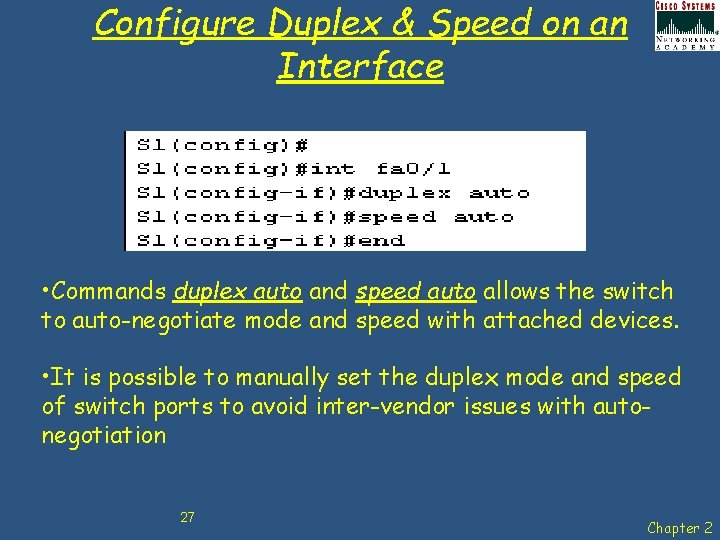
Configure Duplex & Speed on an Interface • Commands duplex auto and speed auto allows the switch to auto-negotiate mode and speed with attached devices. • It is possible to manually set the duplex mode and speed of switch ports to avoid inter-vendor issues with autonegotiation 27 Chapter 2
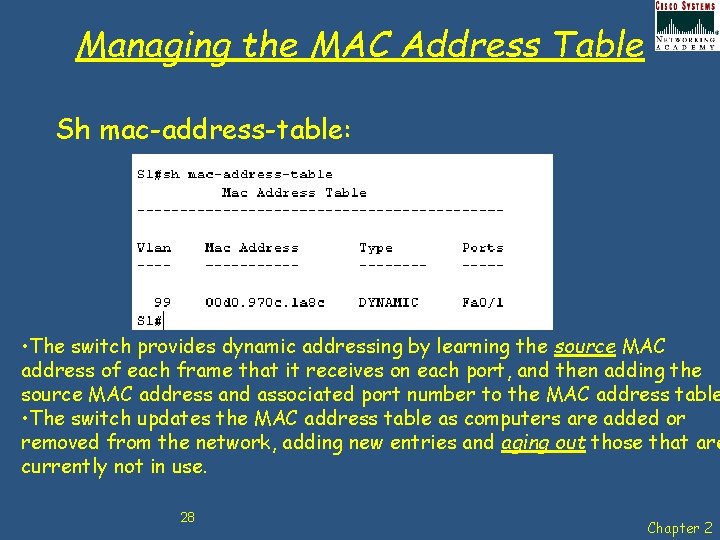
Managing the MAC Address Table Sh mac-address-table: • The switch provides dynamic addressing by learning the source MAC address of each frame that it receives on each port, and then adding the source MAC address and associated port number to the MAC address table • The switch updates the MAC address table as computers are added or removed from the network, adding new entries and aging out those that are currently not in use. 28 Chapter 2
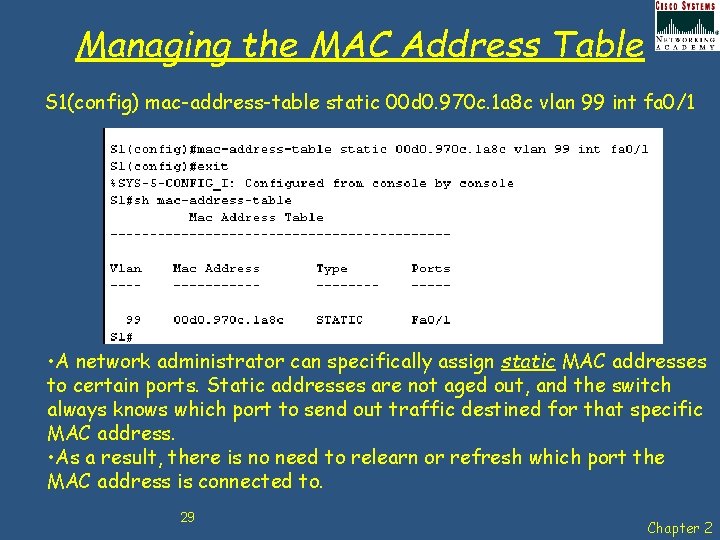
Managing the MAC Address Table S 1(config) mac-address-table static 00 d 0. 970 c. 1 a 8 c vlan 99 int fa 0/1 • A network administrator can specifically assign static MAC addresses to certain ports. Static addresses are not aged out, and the switch always knows which port to send out traffic destined for that specific MAC address. • As a result, there is no need to relearn or refresh which port the MAC address is connected to. 29 Chapter 2
Verify Switch Settings – Show Commands With some minor differences, Cisco switch show commands follow the same syntax and display similar information to those used on Cisco routers 30 Chapter 2
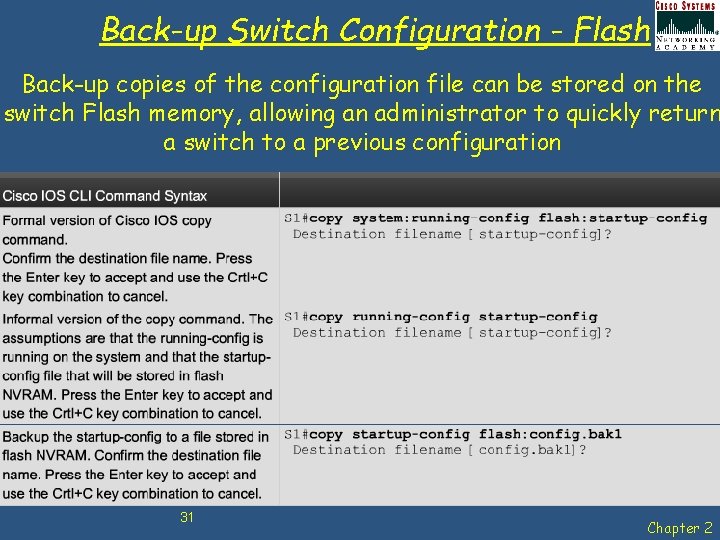
Back-up Switch Configuration - Flash Back-up copies of the configuration file can be stored on the switch Flash memory, allowing an administrator to quickly return a switch to a previous configuration 31 Chapter 2
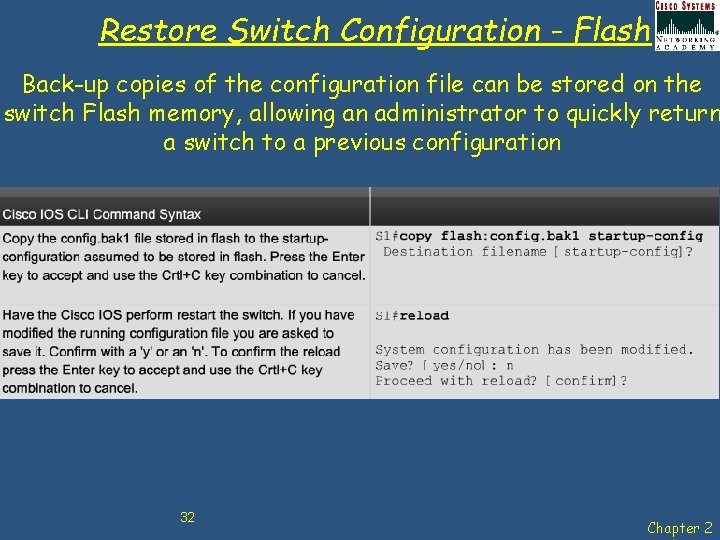
Restore Switch Configuration - Flash Back-up copies of the configuration file can be stored on the switch Flash memory, allowing an administrator to quickly return a switch to a previous configuration 32 Chapter 2
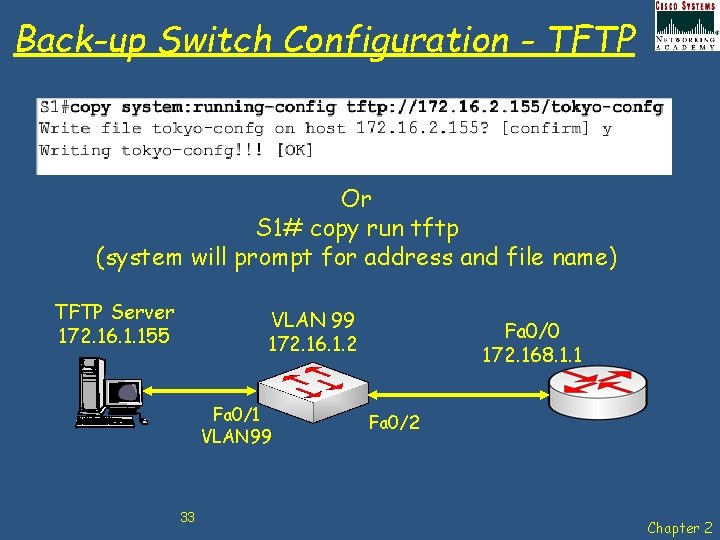
Back-up Switch Configuration - TFTP Or S 1# copy run tftp (system will prompt for address and file name) TFTP Server 172. 16. 1. 155 VLAN 99 172. 16. 1. 2 Fa 0/1 VLAN 99 33 Fa 0/0 172. 168. 1. 1 Fa 0/2 Chapter 2
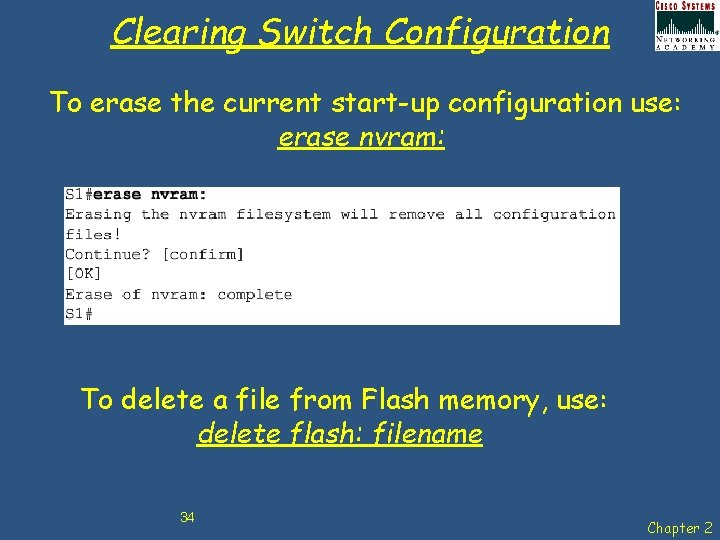
Clearing Switch Configuration To erase the current start-up configuration use: erase nvram: To delete a file from Flash memory, use: delete flash: filename 34 Chapter 2
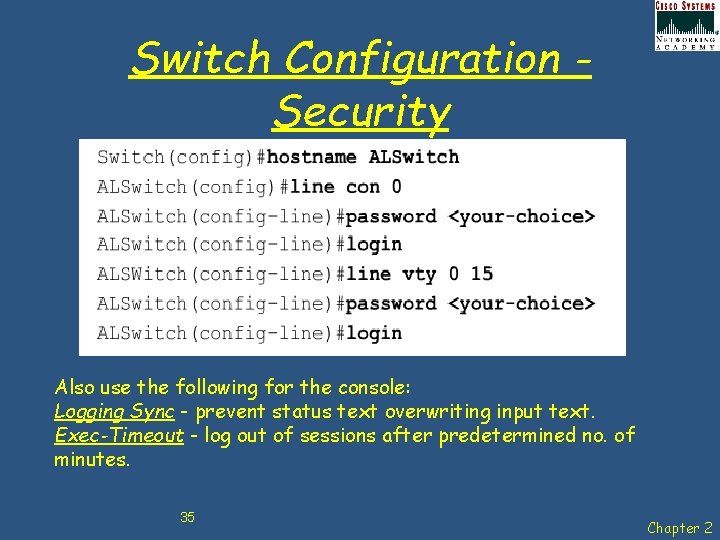
Switch Configuration Security Also use the following for the console: Logging Sync - prevent status text overwriting input text. Exec-Timeout - log out of sessions after predetermined no. of minutes. 35 Chapter 2
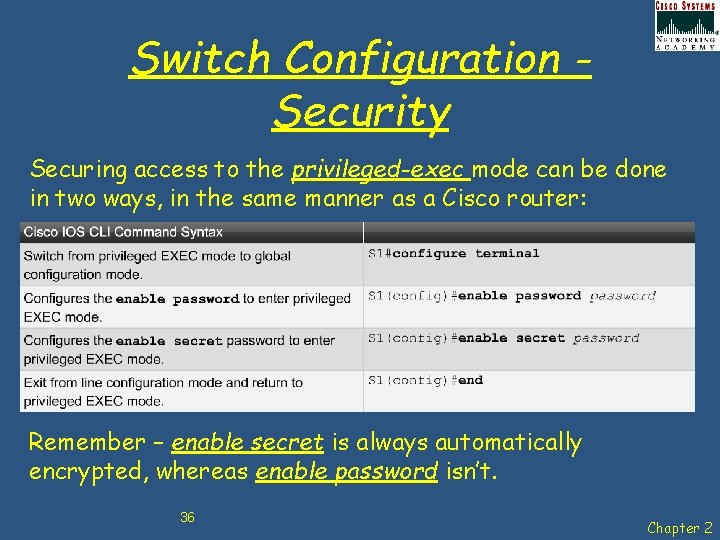
Switch Configuration Security Securing access to the privileged-exec mode can be done in two ways, in the same manner as a Cisco router: Remember – enable secret is always automatically encrypted, whereas enable password isn’t. 36 Chapter 2
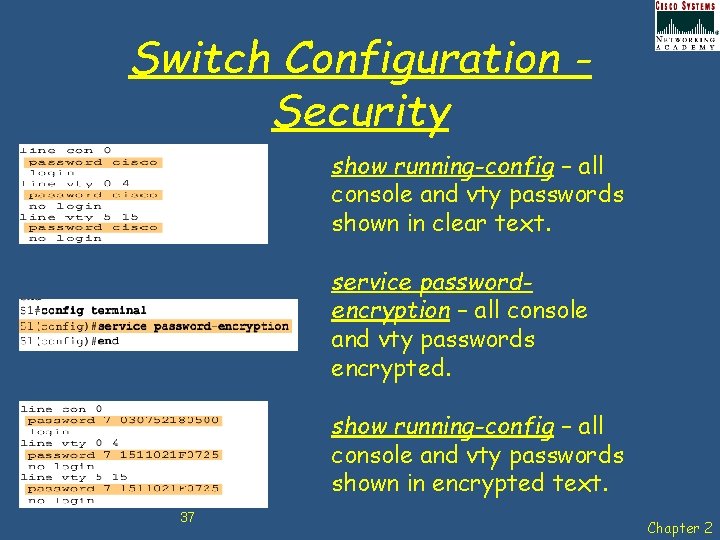
Switch Configuration Security show running-config – all console and vty passwords shown in clear text. service passwordencryption – all console and vty passwords encrypted. show running-config – all console and vty passwords shown in encrypted text. 37 Chapter 2
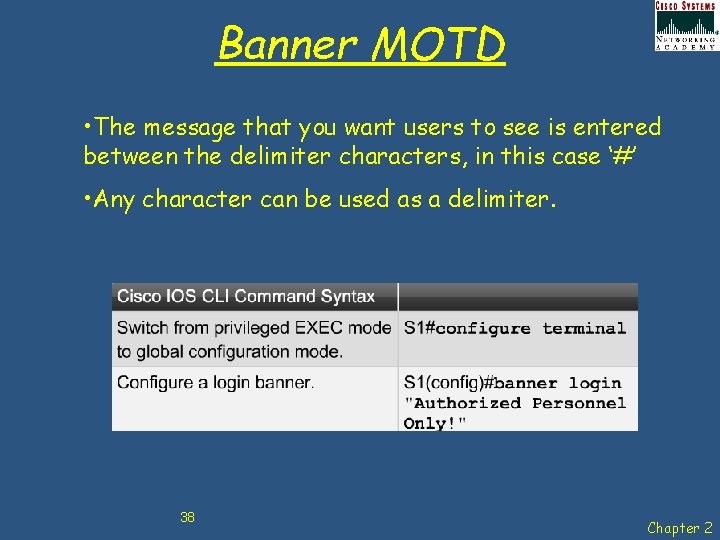
Banner MOTD • The message that you want users to see is entered between the delimiter characters, in this case ‘#’ • Any character can be used as a delimiter. 38 Chapter 2

Telnet & SSH gives the same type of access as Telnet, but guarantees security, as communication between SSH client and SSH server is encrypted. Cisco recommends implementation of SSHv 2 when possible, because it uses a more enhanced security encryption algorithm than SSHv 1. Configure switch with domain-name, encryption key, SSH version & enable SSH on vty lines. • To re-enable the Telnet protocol on a Cisco 2960 switch, 39 Chapter 2

Common Security Attacks – MAC Address Flooding • MAC address tables are limited in size. MAC flooding makes use of this limitation to bombard the switch with fake source MAC addresses until the switch MAC address table is full. • The switch then enters into what is known as a fail-open mode, and starts acting as a hub, broadcasting frames to all the machines on the network. • As a result, the attacker can see all of the frames sent from a victim host to another host without a MAC address table entry. 40 Chapter 2
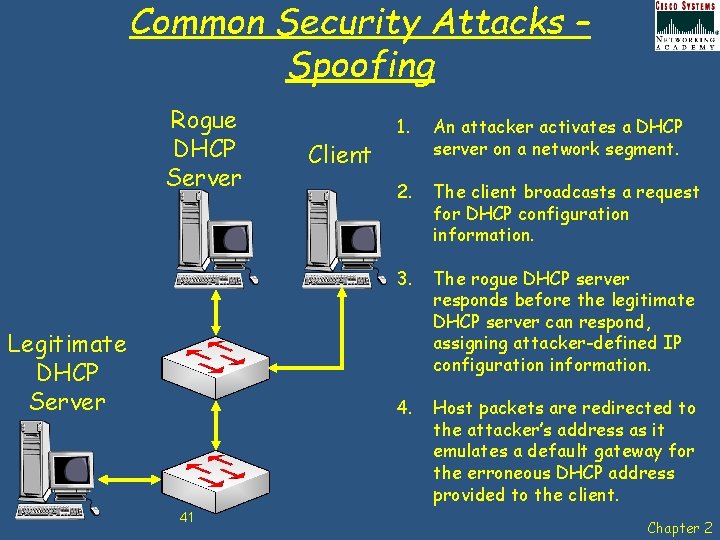
Common Security Attacks – Spoofing Rogue DHCP Server Legitimate DHCP Server 41 Client 1. An attacker activates a DHCP server on a network segment. 2. The client broadcasts a request for DHCP configuration information. 3. The rogue DHCP server responds before the legitimate DHCP server can respond, assigning attacker-defined IP configuration information. 4. Host packets are redirected to the attacker’s address as it emulates a default gateway for the erroneous DHCP address provided to the client. Chapter 2
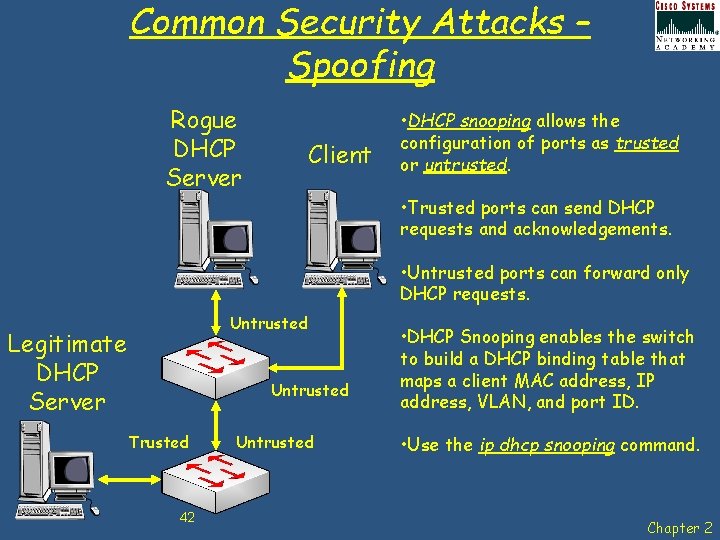
Common Security Attacks – Spoofing Rogue DHCP Server Client • DHCP snooping allows the configuration of ports as trusted or untrusted. • Trusted ports can send DHCP requests and acknowledgements. • Untrusted ports can forward only DHCP requests. Untrusted Legitimate DHCP Server Untrusted Trusted 42 Untrusted • DHCP Snooping enables the switch to build a DHCP binding table that maps a client MAC address, IP address, VLAN, and port ID. • Use the ip dhcp snooping command. Chapter 2

Common Security Attacks – Cisco Discovery Protocol • CDP contains information about the device, such as the IP address, software version, platform, capabilities, and the native VLAN. • When this information is available to an attacker, they can use it to find exploits to attack a network, typically in the form of a Denial of Service (Do. S) attack. • To address this vulnerability, it is recommended that CDP is disabled on devices that do not need to use it. 43 Chapter 2

Common Security Attacks – Cisco Discovery Protocol Types of Telnet attacks: 1. Brute force password attacks 2. Do. S attacks Protection against brute force attack: 1. Use strong passwords 2. Change passwords frequently 3. Limit Telnet access to essential personnel Protection against Do. S: 1. Update to latest version of CISCO IOS 44 Chapter 2

Common Security Attacks – Network Security Audits help to: 1. Reveal what sorts of information an attacker can gather by monitoring network traffic. 2. Discover incorrectly configured switch ports 3. Determine the age out period of MAC address tables. Network Penetration Testing helps to: 1. Identify weaknesses within the configuration of networking devices. 2. Launch attacks to test a network. 45 Chapter 2
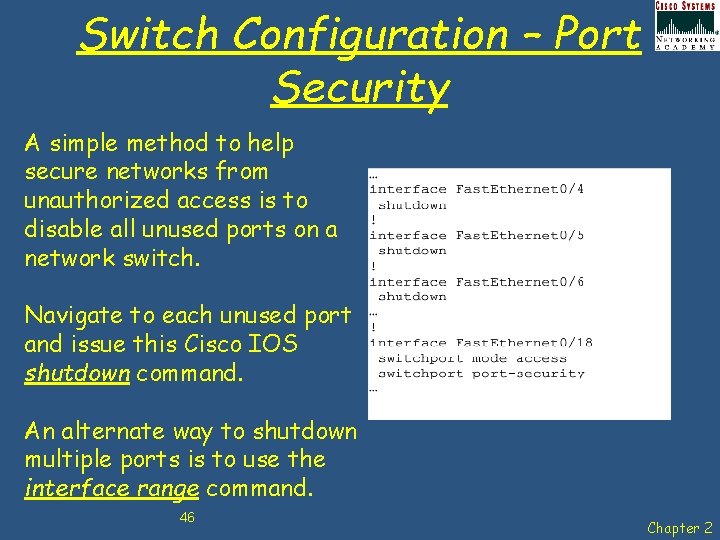
Switch Configuration – Port Security A simple method to help secure networks from unauthorized access is to disable all unused ports on a network switch. Navigate to each unused port and issue this Cisco IOS shutdown command. An alternate way to shutdown multiple ports is to use the interface range command. 46 Chapter 2
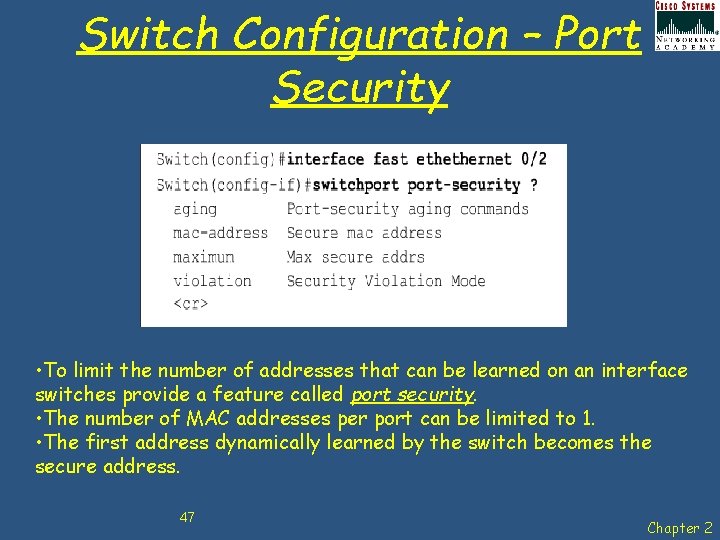
Switch Configuration – Port Security • To limit the number of addresses that can be learned on an interface switches provide a feature called port security. • The number of MAC addresses per port can be limited to 1. • The first address dynamically learned by the switch becomes the secure address. 47 Chapter 2
Switch Configuration – Port Security • • • Static secure MAC addresses: MAC addresses are manually configured by using the switchport-security mac-address interface configuration command. MAC addresses configured in this way are stored in the address table and are added to the running configuration on the switch. Dynamic secure MAC addresses: MAC addresses are dynamically learned and stored only in the address table. MAC addresses configured in this way are removed when the switch restarts. Sticky secure MAC addresses: You can configure a port to dynamically learn MAC addresses and then save these MAC addresses to the running configuration. 48 Chapter 2

• switchport mode access Sets the interface mode as access; an interface in the default mode (dynamic desirable) cannot be configured as a secure port. • switchport-security Enables port security on the interface • switchport-security maximum 6 Sets the maximum number of secure MAC addresses for the interface. The range is 1 to 132; the default is 1. • switchport-security aging time 5 Learned addresses are not aged out by default but can be with this command. Value from 1 to 1024 in minutes. • switchport-security mac-address 0000. 000 b Enter a static secure MAC address for the interface, repeating the command as many times as necessary. You can use this command to enter the maximum number of secure MAC addresses. If you configure fewer secure MAC addresses than the maximum, the remaining MAC addresses are dynamically learned. • switchport-security mac-address sticky Enable dynamic learning of MAC address on the interface. • switchport-security violation shutdown Set the violation mode, the action to be taken when a security violation is detected. 49 Chapter 2

Port Security: Violation Switch(config-if)#switchport-security violation {protect | restrict | shutdown} By default, if the maximum number of connections is achieved and a new MAC address attempts to access the port, the switch must take one of the following actions: • Protect: Frames from the non-allowed address are dropped, but there is no log of the violation. The protect argument is platform or version dependent. • • Restrict: Frames from the non-allowed address are dropped, a log message is created and Simple Network Management Protocol (SNMP) trap sent. Shut down: If any frames are seen from a non-allowed address, the interface is errdisabled, a log entry is made, SNMP trap sent and manual intervention (no shutdown) or errdisable recovery must be used to make the interface usable. Port LED is switched off. 50 Chapter 2
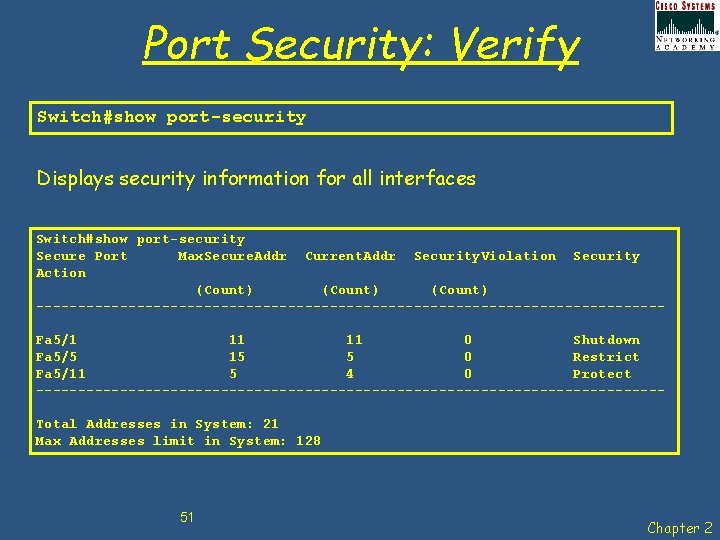
Port Security: Verify Switch#show port-security Displays security information for all interfaces Switch#show port-security Secure Port Max. Secure. Addr Current. Addr Security. Violation Security Action (Count) -------------------------------------Fa 5/1 11 11 0 Shutdown Fa 5/5 15 5 0 Restrict Fa 5/11 5 4 0 Protect -------------------------------------Total Addresses in System: 21 Max Addresses limit in System: 128 51 Chapter 2
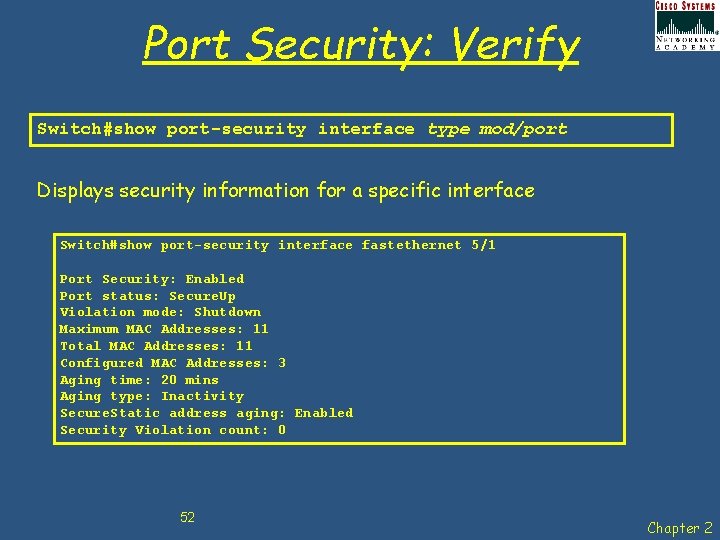
Port Security: Verify Switch#show port-security interface type mod/port Displays security information for a specific interface Switch#show port-security interface fastethernet 5/1 Port Security: Enabled Port status: Secure. Up Violation mode: Shutdown Maximum MAC Addresses: 11 Total MAC Addresses: 11 Configured MAC Addresses: 3 Aging time: 20 mins Aging type: Inactivity Secure. Static address aging: Enabled Security Violation count: 0 52 Chapter 2
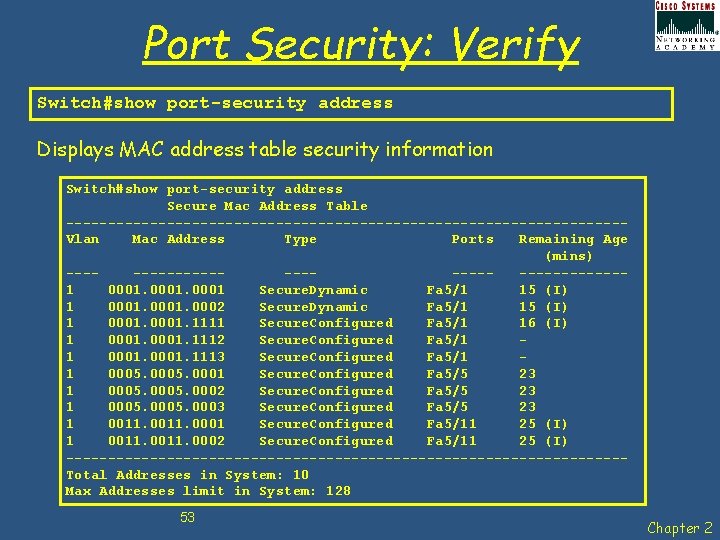
Port Security: Verify Switch#show port-security address Displays MAC address table security information Switch#show port-security address Secure Mac Address Table ---------------------------------Vlan Mac Address Type Ports Remaining Age (mins) ----------------1 0001 Secure. Dynamic Fa 5/1 15 (I) 1 0001. 0002 Secure. Dynamic Fa 5/1 15 (I) 1 0001. 1111 Secure. Configured Fa 5/1 16 (I) 1 0001. 1112 Secure. Configured Fa 5/1 1 0001. 1113 Secure. Configured Fa 5/1 1 0005. 0001 Secure. Configured Fa 5/5 23 1 0005. 0002 Secure. Configured Fa 5/5 23 1 0005. 0003 Secure. Configured Fa 5/5 23 1 0011. 0001 Secure. Configured Fa 5/11 25 (I) 1 0011. 0002 Secure. Configured Fa 5/11 25 (I) ---------------------------------Total Addresses in System: 10 Max Addresses limit in System: 128 53 Chapter 2

Chap 2 – Basic Switch Concepts and Configuration Learning Objectives • • Summarise the operation of Ethernet as defined for 100/1000 Mbps LANs in the IEEE 802. 3 standard. Explain the functions that enable a switch to forward Ethernet frames in a LAN. Configure a switch for operation in a network designed to support voice, video, and data transmissions. Configure basic security on a switch that will operate in a network designed to support voice, video, and data transmissions. 54 Chapter 2

Any Questions? 55 Chapter 2
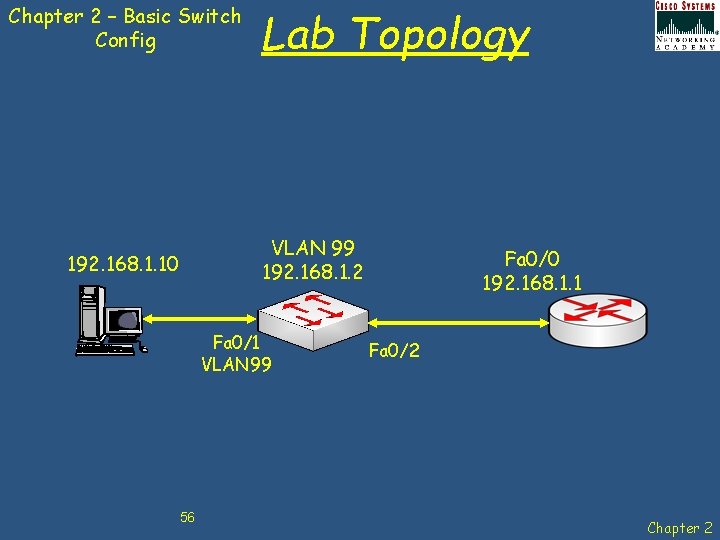
Chapter 2 – Basic Switch Config Lab Topology VLAN 99 192. 168. 1. 2 192. 168. 1. 10 Fa 0/1 VLAN 99 56 Fa 0/0 192. 168. 1. 1 Fa 0/2 Chapter 2
- Slides: 56