Channel Utilization Schemes 1 Introduction n Multiplexing schemes









- Slides: 25

Channel Utilization Schemes 1

Introduction n Multiplexing schemes n n TDMA FDMA Compression n Analog signal compression n n Voice compression Data compression n n Data compression Fax compression 2

1. Multiplexing n FDMA n n n Frequency bandwidth is divided into multiple subchannels. A sub-channel is given to users who need wireless communication, and they use it exclusively for the connection. A pair of channels are required, each for a direction. In AMPS system TDD (time division duplex) n n Special case of FDMA or TDMA One frequency is used for both direction n Called ping pong of flip flop 3

1. Multiplexing n TDM, STDM (statistical TDM) n n Time is divided into time slots. All frequency band is given to a user with n n Pre-decided rule (round-robin): TDM Irregularly with contention (demand) basis: STDM n n n It is known STDM method uses less frequency than TDM by 2~5 times. Used in GSM (Global System for Mobile transmission) Figure p. 93 4

1. Multiplexing n Multiple access with FDM and TDM: GSM n n p. 95 GSM operates at 900 MHz and 1800 MHz Each channel is composed of a downlink and an uplink frequency with 200 k. Hz per link. Each channel is divided by TDM into 8 slots for individual connections. 5

1. Multiplexing n Time slot: the smallest unit in TDM n n n Carrier: the smallest unit in FDM n n n 0. 577 ms 156. 25 bits = 148 bits + 8. 25 guard bits 200 k. Hz 890 -915 MHz for upward channel, and 935 -960 MHz for downward channel If f(C) is assigned for upward channel, f(C) + 45 MHz is assigned for downward channel Burst: the smallest unit of voice information n To locate a burst, time slot and carrier should be assigned 6

1. Multiplexing n Guard time (ramp time, tail) bits n To isolate one burst from another n n n From time to turn on or off the transmitter To compensate different distance to the base station Allowed power during a unit of burst p. 96 7

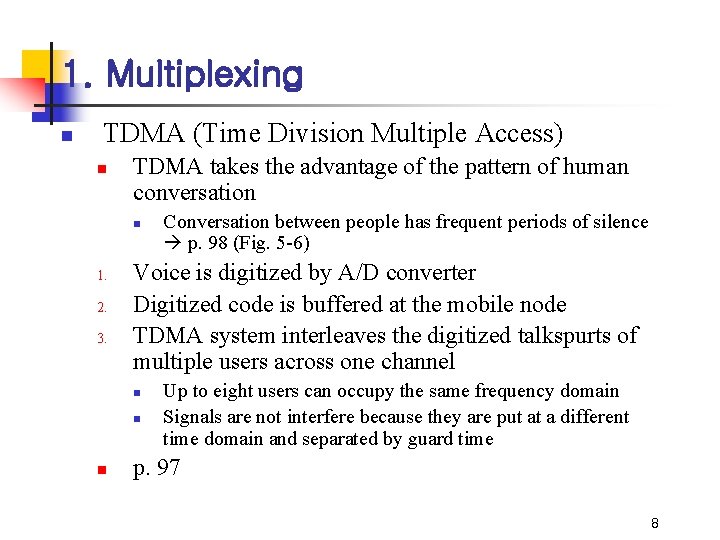
1. Multiplexing n TDMA (Time Division Multiple Access) n TDMA takes the advantage of the pattern of human conversation n 1. 2. 3. Voice is digitized by A/D converter Digitized code is buffered at the mobile node TDMA system interleaves the digitized talkspurts of multiple users across one channel n n n Conversation between people has frequent periods of silence p. 98 (Fig. 5 -6) Up to eight users can occupy the same frequency domain Signals are not interfere because they are put at a different time domain and separated by guard time p. 97 8

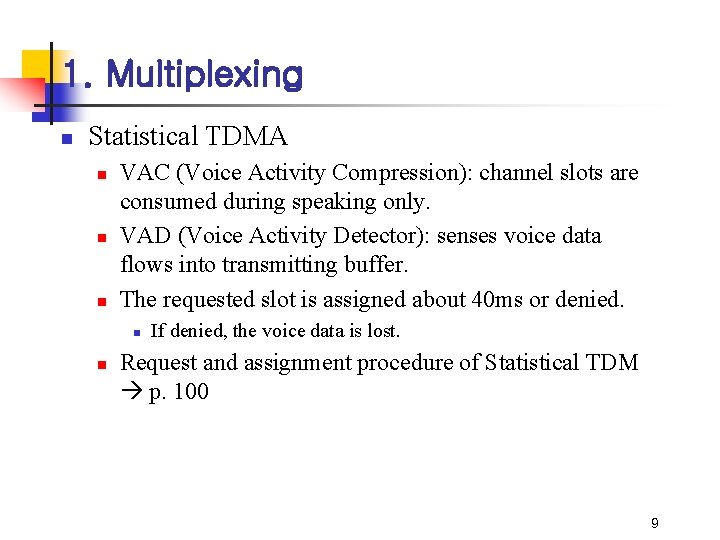
1. Multiplexing n Statistical TDMA n n n VAC (Voice Activity Compression): channel slots are consumed during speaking only. VAD (Voice Activity Detector): senses voice data flows into transmitting buffer. The requested slot is assigned about 40 ms or denied. n n If denied, the voice data is lost. Request and assignment procedure of Statistical TDM p. 100 9

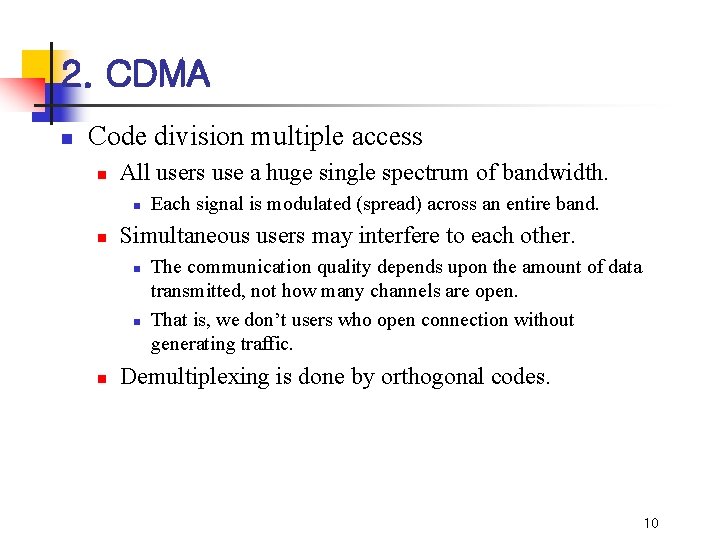
2. CDMA n Code division multiple access n All users use a huge single spectrum of bandwidth. n n Simultaneous users may interfere to each other. n n n Each signal is modulated (spread) across an entire band. The communication quality depends upon the amount of data transmitted, not how many channels are open. That is, we don’t users who open connection without generating traffic. Demultiplexing is done by orthogonal codes. 10

2. CDMA n CDMA and language analogy n Suppose there are 2 k persons in a bus. n n n Two of each comes from the same country. All others comes from all k different countries which uses all different languages. They talk to the other from the same country simultaneously. Even if the bus is very noisy, they can easily ignore others’ superfluous noise (voice), because they cannot understand the other language. If 2 k persons speak in a single language, they probably cannot hear the other’s voice. Similarly, CDMA receiver easily filters out the other’s talk as well as noise. 11

2. CDMA n Code division n 1 bit is coded into k-unit called chips. n n Bandwidth reduces by k. Data is coded with code sequence. 12

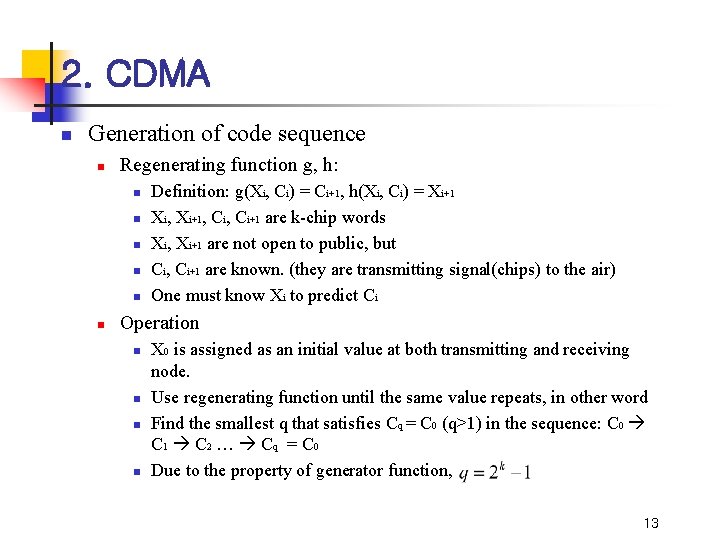
2. CDMA n Generation of code sequence n Regenerating function g, h: n n n Definition: g(Xi, Ci) = Ci+1, h(Xi, Ci) = Xi+1 Xi, Xi+1, Ci+1 are k-chip words Xi, Xi+1 are not open to public, but Ci, Ci+1 are known. (they are transmitting signal(chips) to the air) One must know Xi to predict Ci Operation n n X 0 is assigned as an initial value at both transmitting and receiving node. Use regenerating function until the same value repeats, in other word Find the smallest q that satisfies Cq = C 0 (q>1) in the sequence: C 0 C 1 C 2 … Cq = C 0 Due to the property of generator function, 13

2. CDMA n Good security in CDMA system n n Party A tries to send data to party B Everybody has the same generator function g(), but Only party A and B knows the code, and They are synchronously generate the code sequence. n n Only party A and B knows the code sequence. All others have different code sequence. n n Anybody except party A and B cannot correctly decode the transmitted data. Hacking of code sequence without knowing code C 0. n To produce correct sequence, hackers have to know the state variable X or, they have to execute the next. 1. 2. 3. n Record the total unit-cycle = (chips) Record the current k-bit( chips ) sequence. (call this S) Find out where S is located in the whole sequence Step 1 and 3 is practically impossible k is very large in real system 14

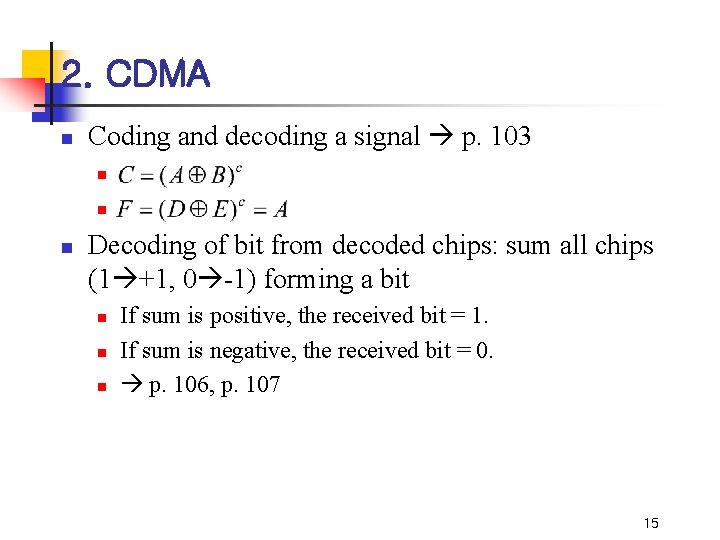
2. CDMA n Coding and decoding a signal p. 103 n n n Decoding of bit from decoded chips: sum all chips (1 +1, 0 -1) forming a bit n n n If sum is positive, the received bit = 1. If sum is negative, the received bit = 0. p. 106, p. 107 15

2. CDMA n Chip-wise operator: XOR n Definition n n Properties n n n Proof of (F=A) n 16

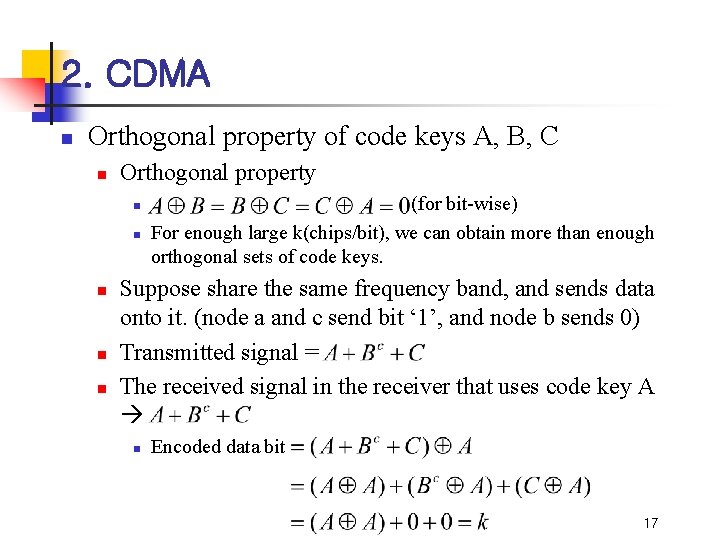
2. CDMA n Orthogonal property of code keys A, B, C n Orthogonal property n n n (for bit-wise) For enough large k(chips/bit), we can obtain more than enough orthogonal sets of code keys. Suppose share the same frequency band, and sends data onto it. (node a and c send bit ‘ 1’, and node b sends 0) Transmitted signal = The received signal in the receiver that uses code key A n Encoded data bit 17

2. CDMA n Similarly for transmission of general data, only data encrypted with code key A is decrypted using the code key A. n n The received data can easily ignore other’s communication But actually the more users sends data, the more interference increases noise n There is upper bound in the number of simultaneous transmission. 18

2. CDMA n Direct sequence and frequency hopping n n Direct sequencing: (general method) all users share a huge frequency band. Frequency hopping: a transmitter changes its carrier frequency often. (currently not used) n Sender and receiver have a common rule how to choose the frequency in the unit of chips. n n Users may conflict a chip due to sharing of a frequency band. p. 108 19

2. CDMA n Comparison of AMPS(FDMA), TDMA, and CDMA n n n Complexity: FDMA < TDMA < CDMA Frequency efficiency (bit rate/allocated frequency): FDMA < TDMA < CDMA p. 109 table 1. 2. 3. 4. 5. 6. 7. 8. Total frequency band allocated to the mobile service Frequency reuse Frequency band allocated to a single channel Number of simultaneous RF channels = term 1 / term 3 Number of RF channels per a cell (base station) = term 4 / term 2 Usable channels per cell Call per radio frequency Voice channel per cell = term 6 x term 7 20

3. Compression n Compression technique n Shrink the size of digital data using statistical behavior by n Analog data: n n n Discrete data: n n Analyze the analog data and represent it numerically Choose major terms Reduce the repeated terms or characters Compression scheme depends upon the type of service n e. g. a good compression scheme in voice does not guarantee its performance in image compression. 21

3. Compression n Voice compression technique n Vocoder: encoding scheme applied only to voice signal n n n Currently most advanced technique can dive about 2 k bps data rate and Used as voice response system (off-line calculation) Channel vocoder n n n Waveform is processed into parameters that measure vocal characteristics. Parameters represent the energy of voice signal from sub-band pass filter. Encoding n n n An original signal is analyzed and find out the closest parameters. Calculated parameter set and send this set instead of analog voice signal. Decoding n From received parameter set, build (synthesize) voice signal 22

3. Compression n LPC (Linear Prediction Coding) n n n Generally voice pattern lasts to pronounce a vowel or a consonant, and then jumps to the next one. Even in the transient period, it shows a habitual way of change. With the input data collected so far, predict how the signal will change next. Vector quantization p. 111 n n The pattern of a speech signal is defined in 20~50 ms durations (called speech segments or parcels) The segments are stored in a register in 6 PCM word blocks. Blocks are compared against a table of values (a codebook). The entry that is closest to the actual value is used as the transmitted value. 23

3. Compression n Data compression technique n Use variable-length characters instead of ASCII (fixed length). n n Frequently used characters (vowels, spaces) are given short length. Bit mapping: a bit(or a word) is used to indicate compression will be done in following characters. n Run length encoding (Kermit): n n n Repeated characters are represented by three bytes 1 st byte: the next two bytes is not normal characters but run length encoding. 2 nd byte: number of repetition 3 rd byte: repeated characters Relative encoding n For data that represents analog stream (symbol, graph) n n n Data is sampled at fixed in intervals. If the curve is smooth, two consecutive data is of similar value. If the curve shows sharp fluctuation, it may not be effective. (it may lengthen data) 24

3. Compression n Fax compression n Fax operation: n Data scanning n n Encoding: shrink the output data size. Run length encoding scheme n n Image on the paper is scanned vertically and horizontally. Output: electrical image are made of 0 and 1 (if white and black). Images coded as w/b runs (00000 or 1111 0: 5 1: 4) Relative encoding scheme n n Only the changed part from previous line is coded. Effective if two adjacent lines are very alike. 25