Ch 2 Exploring Control Types and Methods Comp























































- Slides: 68

Ch 2: Exploring Control Types and Methods Comp. TIA Security+: Get Certified Get Ahead: SY 0 -401 Study Guide Darril Gibson

Jérôme Kerviel Rogue trader, lost € 4. 9 billion Largest fraud in banking history at that time Worked in the compliance department of a French bank Defeated security at his bank by concealing transactions with other transactions Arrested in Jan 2008, out and working at a computer consulting firm in April 2008 – Links Ch 7 a, 7 b

Understanding Control Types

Risk – The likelihood that a threat will exploit a vulnerability, resulting in a loss Risk Management – Using controls to reduce risk Controls – Also called countermeasures or safeguards

Types of Controls Technical – Uses technology to reduce vulnerabilities Management – Primarily administrative Operational – Ensure that day-to-day operations comply with security plan

Examples of Technical Controls Encryption Antivirus software Intrusion Detection Systems (IDSs) – Monitors a network or host for network-based threats Firewalls – Restrict network traffic with rules Least Privilege – Users have only enough permissions to do their job, but not more

Examples of Management Controls Risk Assessments – Quantitative risk assessment Uses cost and asset values to determine monetary risk – Qualitative analysis Categorizes and rates risks “High risk”, “Medium risk”, “Low risk”

Examples of Management Controls Vulnerability Assessments – Finds weaknesses, such as missing patches Penetration tests – Exploit vulnerabilities to demonstrate security flaws in a dramatic manner

Examples of Operational Controls Awareness and Training – Maintain password security – Clean desk policy – Understand phishing and malware Configuration Management – Record performance baselines – Change management Contingency Planning – Prepare for outages

Examples of Operational Controls Media Protection – Physical media like USB flash drives, hard drives, and backup tapes Physical and Environmental Protection – Cameras – Door locks – Heating and ventilation systems

NIST (National Institute of Standards and Technologies) Publishes Special Publications with security guidance (SP 800 Series) Unfortunately, NIST has been caught redhanded several times recommending insecure protocols to make the NSA's spying job easier Their credibility is still high in the USA, however

Controls Goals Preventative Controls – Prevent an incident from occurring Detective Controls – Detect when a vulnerability has been exploited – Cannot predict an incident – Cannot prevent an incident Corrective – Reverse the impact of an incident after it occurs

Controls Goals Deterrent Controls – Discourage an attacker from causing an incident Compensating Controls – Alternative controls used when a primary control is not feasible

Examples of Preventative Controls Hardening – Making systems more secure than default configurations – Removing and disabling unneeded services and protocols – Patches and updates – Enabling firewalls Security awareness and training

Examples of Preventative Controls Security Guards – Attacker is less likely to attempt social engineering and less likely to succeed Change Management – All changes most go through a change management process – Prevents ad-hoc configuration errors – Examples: promoting users to Administrator casually; installing a rogue Wi-Fi access point

Examples of Preventative Controls Account Disablement Policy – When an employee is terminated

Examples of Detective Controls Log monitoring – Firewall logs, server logs, etc. Trend analysis – Monitoring alerts from an Intrusion Detection System (IDS) can detect a trend of increased attacks on a specific system

Examples of Detective Controls Security Audit – Examines the security posture of an organization – Password audit – User permissions audit Video Surveillance – Records activity and detects what occurred – Visible cameras can also act as a preventative control, deterring attacks

Examples of Detective Controls Motion detection – Physical security

Comparing Detection and Prevention Controls Detective control – Can't predict or prevent an incident – Ex: video surveillance Preventive control – Stops an incident from occurring – Ex: guards

Corrective Controls Attempt to reverse the impact of an incident after it has occurred

Examples of Corrective Controls Active IDS – Detect attacks and modifies the environment to block them Backups and System Recovery – When data is lost, backups ensure that it can be recovered – System recovery restores damaged systems to operation

Deterrent Controls Attempt to discourage a threat – Discourage potential attackers from attacking – Discourage employees from violating security policies Examples – Cable locks on laptops Image from technologytell. com – Hardware locks on doors to server rooms, or server racks

Compensating Controls Alternative controls used instead of a primary control Example – Company wants to use smart cards for twofactor authentication – New employees, while waiting to get a smart card, are permitted to use a Time-based One. Time Password (TOTP) as a compensating control

Combining Control Types and Goals Types Goals – Technical – Managment – Operational – Preventive – Detective – Corrective – Deterrent – Compensating

Comparing Physical Security Controls Perimeter – Fence around the whole campus – Security guards at gates Building – Guards and locked doors – Lighting and video cameras at entrances and exits

Comparing Physical Security Controls Secure work areas – For classified or restricted-access tasks Server and network rooks – Locking a wiring closer Hardware – Locking server cabinets – Cable locks for laptops

Door Access Systems Cipher locks – Image from mssparky. com Proximity Cards – image from beresfordco. com Biometrics

ID Badges Image from pimall. com

Tailgating Following a person through a secure door Also called piggybacking To prevent this, use mantraps, turnstiles, or security guards

Turnstile Image from sunshinetek. en. made-in-china. com

Man Trap Image from flaglerchat. com

Physical Access List and Logs Access List – Specifies who is allowed to enter – Enforced by guards Log – Records who went in and out – Video surveillance is most reliable

Video Surveillance (CCTV) Most reliable proof of a person's location and activity Only record in public areas Notify employees of the surveillance Do not record audio – It's often illegal without consent of all parties

Motion Detection And. . . Fence + Motion Detection – Detects attempts to climb the fence – Subject to false alarms from animals Lighting + Motion Detection – Motion detectors turn on bright lights – Must protect lights from intruders Alarms + Motion Detection – Motion detected after hours sets off alarm

Barricades Strong barricades – Appropriate for military bases – Look too forbidding for commercial businesses Bollards – Prevent vehicles from driving up to doors – Image from 1800 bollards. com

Signs Deterrent control, not preventive

Hardware Locks Cable locks for mobile computers Locking cabinets for servers Safe to secure small devices

Implementing Logical Access Controls

Least Privilege A technical control implemented with access controls Individuals and processes are granted only the rights and permissions they need – Don't let everyone log on as Administrator

Need to Know Users are only granted access to the data they need to know for their jobs Spectacular failure: Bradley Manning – Image from nydailynews. com

Group Policy Implemented on a Windows domain controller Security settings affect all computers and users in the domain Central point of administration

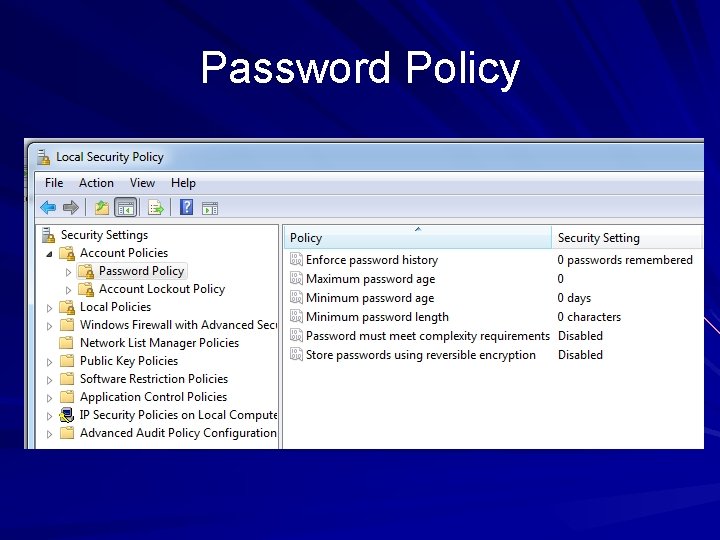
Password Policy

Application Passwords Service accounts – Used by automatic processes to fetch mail, update databases, etc. – Often use insecure or even default passwords that are rarely or never changed – Should be governed by a password policy

Account Management – Creating, Management, Disabling, or Terminating user accounts Centralized Account Management – One point of administration – Windows domain controller, using LDAP Decentralized – Accounts stored on each workstation locally – Windows workgroup

Disabling and Deleting Accounts Disable inactive accounts Terminated employees – Often old accounts are left active Leave of Absence – Disable account temporarily

Prohibiting Generic Accounts Disable Guest account Don't let administrators share "Administrator" or "root" account Otherwise logs don't identify who is using systems

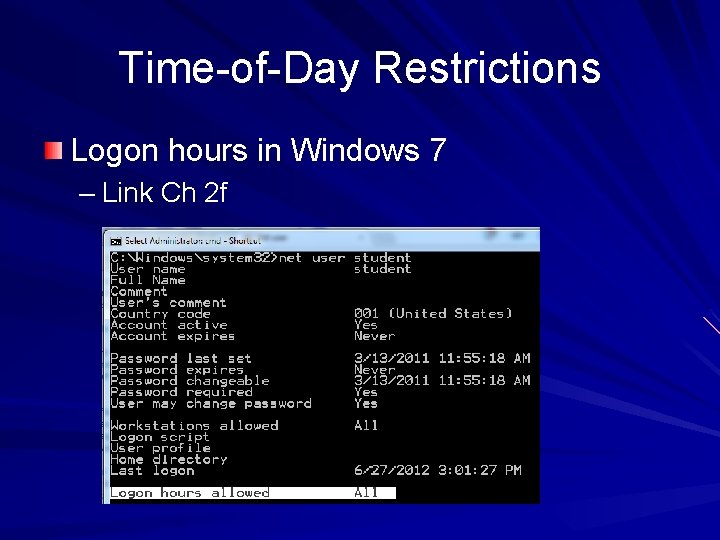
Time-of-Day Restrictions Logon hours in Windows 7 – Link Ch 2 f

Account Expiration and Access Review Account Expiration – Appropriate for temporary contract employees Account Access Review – Log and audit times of logon and logoff – Detect password-guessing attacks – Monitor remote access logins

Credential Management Also called "Password Managers" Stores passwords securely, protected by a master password Included in operating systems and browsers, or available for separate download

Comparing Access Control Models

RBAC, DAC, MAC Role-Based Access Control (RBAC) Rule-Based Access Control (RBAC) Discretionary Access Control (DAC) Mandatory Access Control (MAC)

Subjects and Objects Subjects – Users or groups that will access an object Object – A file, folder, share, printer, or other asset which subjects may want to access

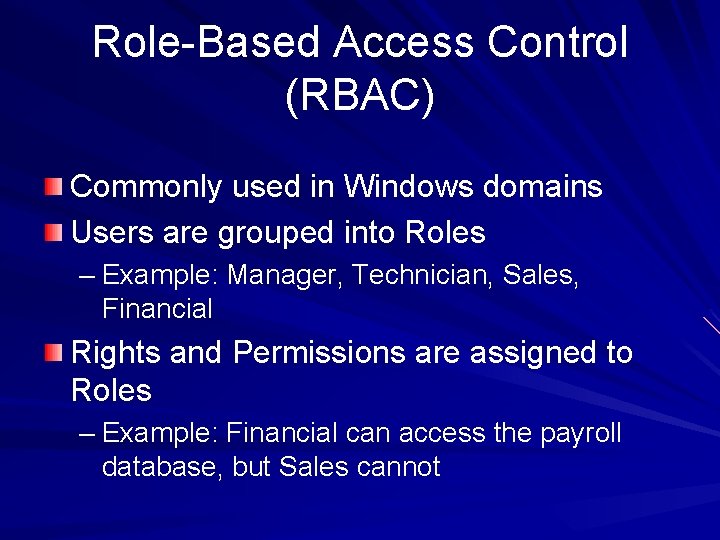
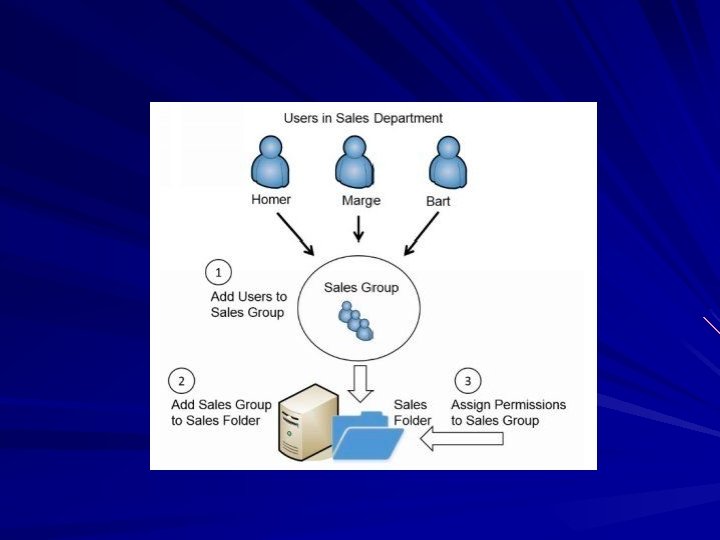
Role-Based Access Control (RBAC) Commonly used in Windows domains Users are grouped into Roles – Example: Manager, Technician, Sales, Financial Rights and Permissions are assigned to Roles – Example: Financial can access the payroll database, but Sales cannot


Rule-Based Access Control (RBAC) Rules define what is allowed – Examples: firewall rules, Parental Controls, Time-of-Day restrictions

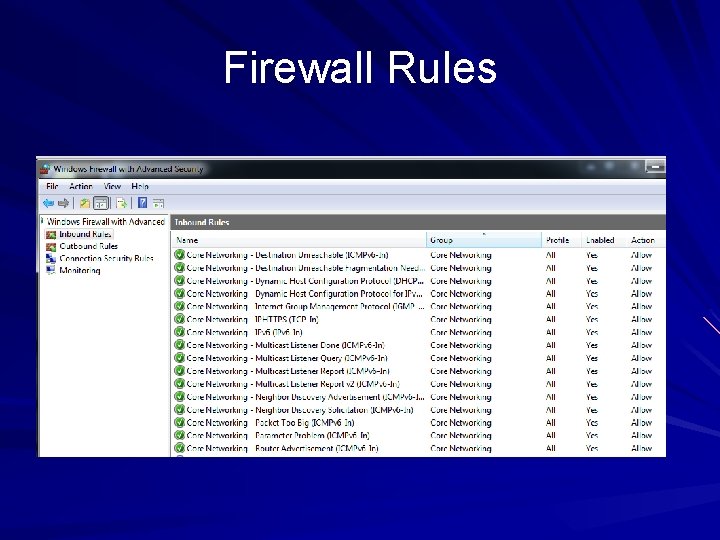
Firewall Rules

Cisco ACLs Link Ch 2 g

Discretionary Access Control (DAC) Each object has an owner The owner assigns access rights at their discretion Used by Windows computers that are not in a corporate domain

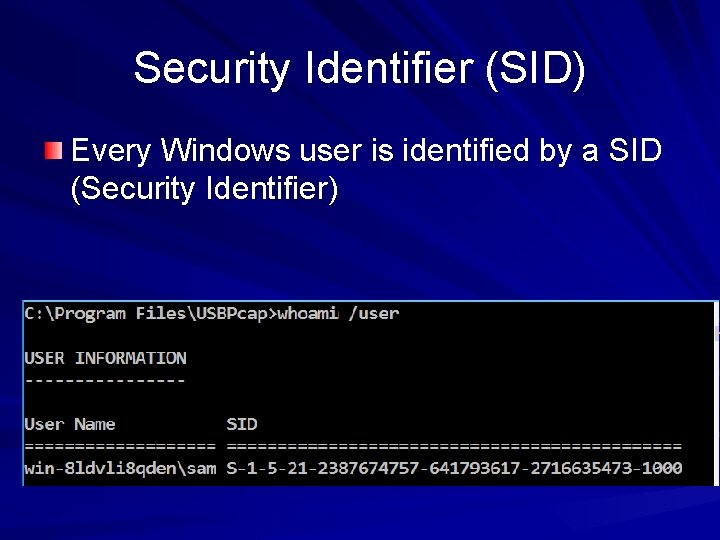
Security Identifier (SID) Every Windows user is identified by a SID (Security Identifier)

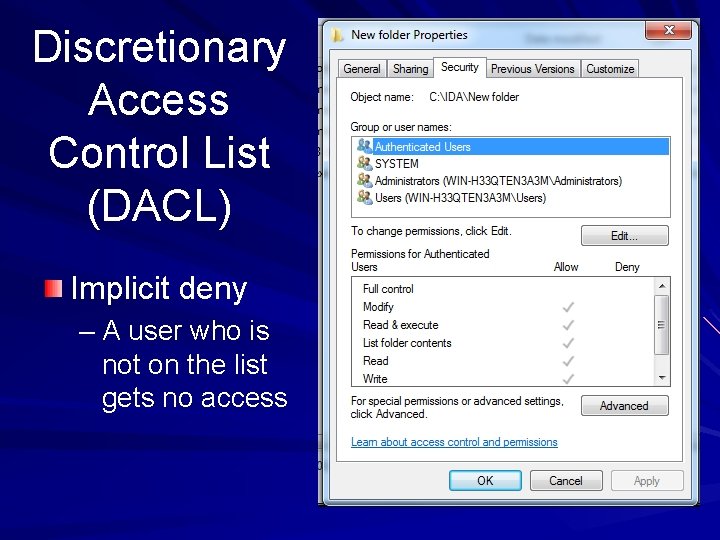
Discretionary Access Control List (DACL) Implicit deny – A user who is not on the list gets no access


Data Classification detemines how much protection the data requires – The access control model (RBAC, DAC, or MAC) helps determine how the data is protected US Gov't uses these classifications – Top Secret – Confidential – Unclassified

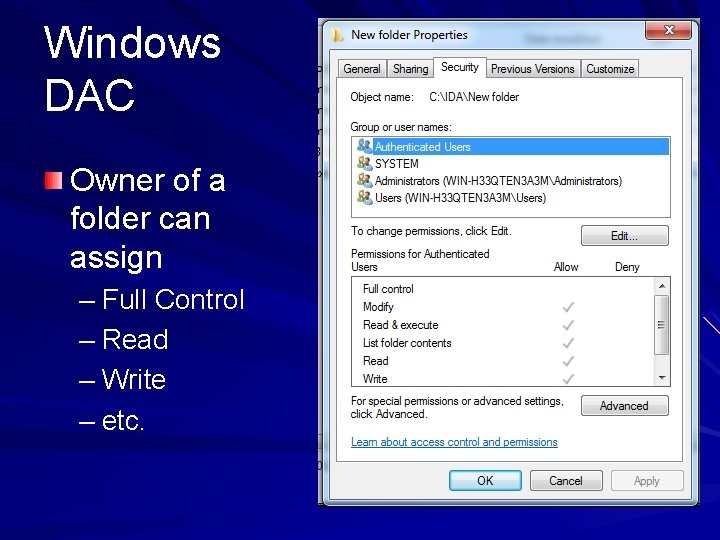
Windows DAC Owner of a folder can assign – Full Control – Read – Write – etc.

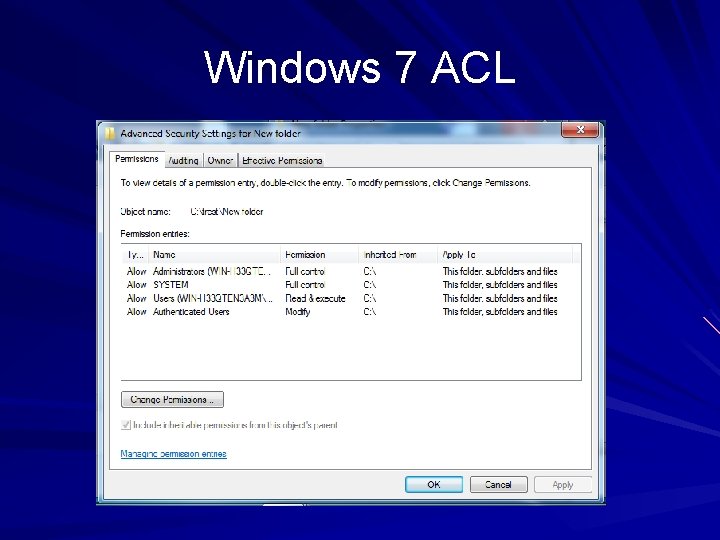
Windows 7 ACL

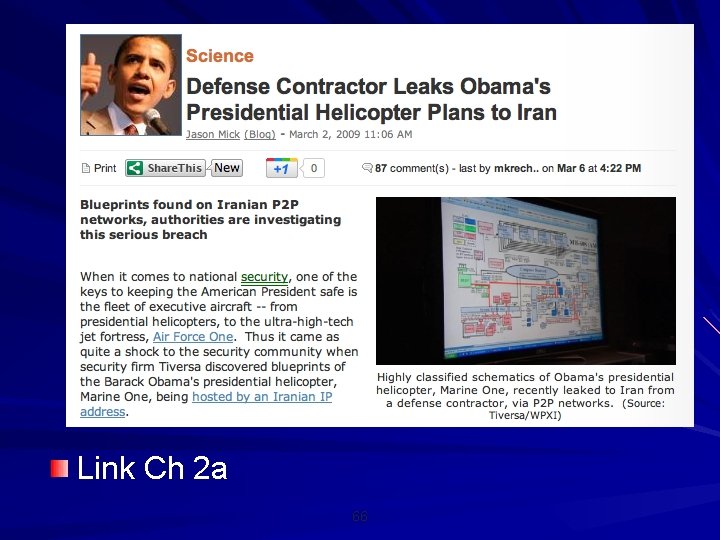
Link Ch 2 a 66

Mandatory Access Control (MAC) Most restrictive, used by military Subjects and objects are classified by a higher authority – Top Secret – Confidential – Unclassified

Mandatory Access Control (MAC) Top Secret data must stay on "Top Secret" devices, and only seen by personnel cleared for "Top Secret" access