Ch 12 Automatic Identification and Data Capture Sections










- Slides: 28

Ch 12 Automatic Identification and Data Capture Sections: 1. Overview of Automatic Identification Methods 2. Bar Code Technology 3. Radio Frequency Identification 4. Other AIDC Technologies © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 1/28

Automatic Identification and Data Capture § A family of technologies that provide direct entry of data into a computer or other microprocessor controlled system without using a keyboard Reasons for using AIDC: 1. Data accuracy 2. Timeliness 3. Labor reduction © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 2/28

Alternative to AIDC: Manual Methods of Data Collection and Entry Problems with manual collection and data entry: 1. Human errors § When data are collected and entered manually 2. Time factor § Time delay between occurrence of activities and events and entry of associated data § Manual methods are inherently time consuming 3. Labor cost § Cost of full-time attention of human worker © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 3/28

AIDC Applications § Retail sales and inventory control § Material handling § Shipping and receiving, sortation, order picking, mail and parcel handling § Factory operations § Order processing, WIP tracking, machine utilization, worker attendance § Other § Patient identification in hospitals, check processing in banks, security system © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 4/28

Components of AIDC Nearly all AIDC technologies consist of three principal components, which are the sequential steps in AIDC: 1. Data encoding - alphanumeric characters are translated to machine-readable form 2. Machine reading or scanning - scanner reads the encoded data and converts it to alternative form, usually an electrical signal 3. Data decoding - electrical signal is transformed into digital data and finally back into original alphanumeric characters © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 5/28

AIDC Technologies 1. Optical § Bar codes (linear and 2 -D), optical character recognition, machine vision 2. Electromagnetic § Radio frequency identification (RFID) 3. Magnetic § Data are encoded magnetically, similar to magnetic tape (e. g. , plastic credit cards, bank checks), and magnetic ink character recognition © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 6/28

AIDC Technologies 4. Smart card § Small plastic cards imbedded with microchips (integrated circuits) 5. Touch techniques § Touch screens 6. Biometric § Voice recognition, fingerprint analysis, retinal eye scans © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 7/28

Measures of AIDC Reading Accuracy 1. First read rate (FRR) § Probability of a successful (correct) reading by the scanner in its initial attempt 2. Substitution error rate (SER) § Probability of scanner incorrectly reading the encoded character as some other character § In a given set of encoded data containing n characters, the expected number of errors = SER * n © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 8/28

Bar Code Technology § Bar codes are of two basic types: 1. Linear § Encoded data are read using a linear sweep of the scanner 2. Two-dimensional § Encoded data must be read in both directions © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 9/28

Linear (One-Dimensional) Bar Codes Two forms of linear bar codes: 1. Width-modulated § Symbol consists of bars and spaces of varying width § Most widely used (e. g. , Universal Product Code) 2. Height-modulated § Symbol consists of bars and spaces of varying height § Used only by U. S. Postal Service for ZIP code identification © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 10/28

Two Forms of Bar Codes (a) (b) (a) Width-modulated bar code, exemplified here by the Universal Product Code (UPC), and (b) height-modulated bar code, exemplified by Postnet, used by the U. S. Postal Service © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 11/28

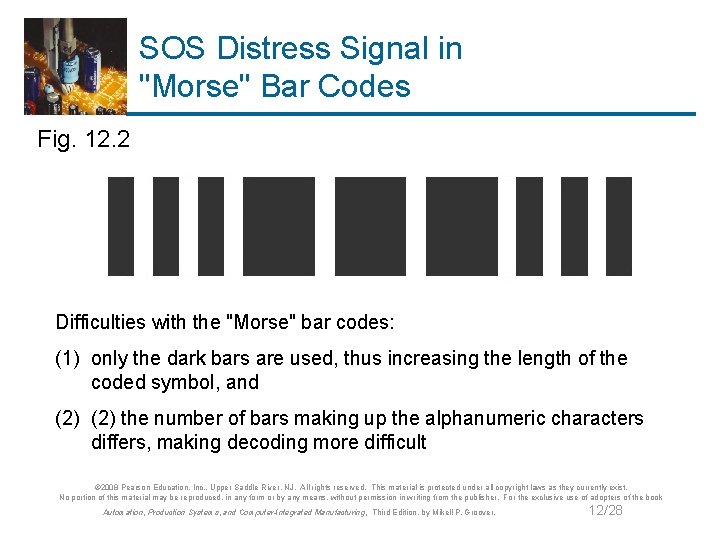
SOS Distress Signal in "Morse" Bar Codes Fig. 12. 2 Difficulties with the "Morse" bar codes: (1) only the dark bars are used, thus increasing the length of the coded symbol, and (2) the number of bars making up the alphanumeric characters differs, making decoding more difficult © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 12/28

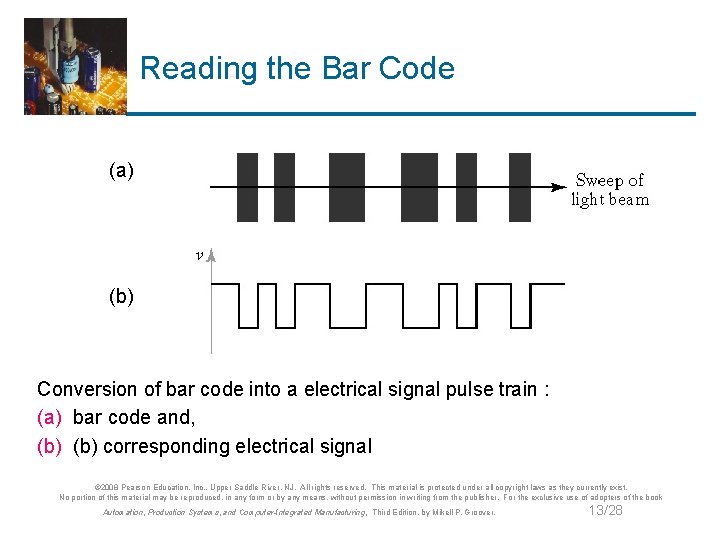
Reading the Bar Code (a) (b) Conversion of bar code into a electrical signal pulse train : (a) bar code and, (b) corresponding electrical signal © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 13/28

Code 39 A typical grouping of characters to form a bar code in Code 39. © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 14/28

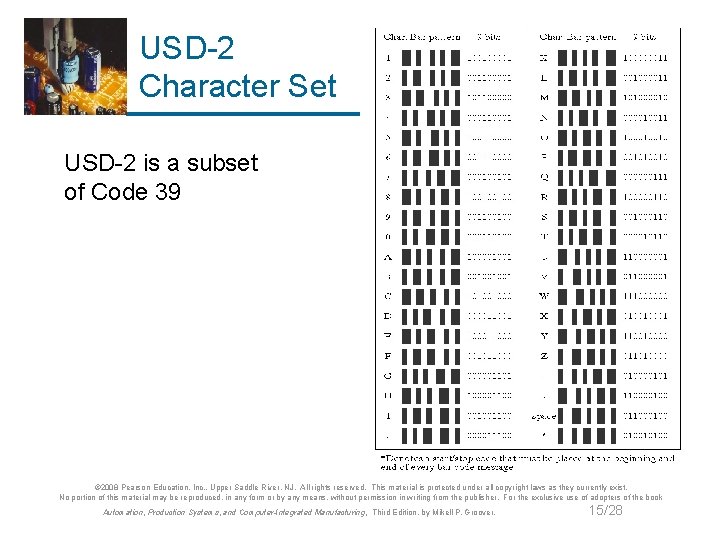
USD-2 Character Set USD-2 is a subset of Code 39 © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 15/28

Linear Bar Code Readers Usually classified as: 1. Contact § Hand-held wands or light pens operated by moving the tip quickly past the bar code 2. Noncontact § Readers focus a light beam on the bar code and a photodetector reads the reflected signal 1. Fixed beam - stationary readers used fixed beam 2. Moving beam - light beam (lasers) traverse an angular sweep to search for the bar code © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 16/28

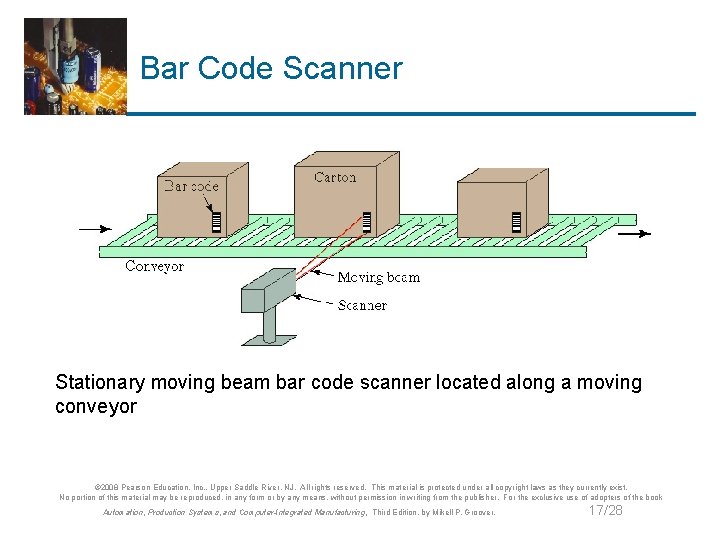
Bar Code Scanner Stationary moving beam bar code scanner located along a moving conveyor © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 17/28

Bar-Coded Route Sheet Bar-coded production order and route sheet © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 18/28

Two-Dimensional Bar Codes § § First 2 -D bar code introduced in 1987 Two basic types of 2 -D bar code symbols 1. Stacked bar codes § Consists of multiple rows of conventional bar codes stacked on top of each other 2. Matrix symbologies § Consists of 2 -D patterns of data cells that are usually square and are colored dark or white § Advantage over stacked bar codes is capability to contain more data © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 19/28

2 -D Stacked Bar Code (PDF 417) Fig 12. 8 © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 20/28

2 -D Matrix Bar Code (Data Matrix) Fig. 12. 9 © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 21/28

Radio Frequency Identification RFID uses an identification tag containing electronically coded data that is attached to the subject item. § The tag consists of a memory microchip and an antenna, usually encased in a plastic container § The tag is a transponder - a device capable of emitting a signal of its own when it receives a signal from an external source § The tag communicates the encoded data by RF as the item passes a reader and is activated by a lowlevel RF magnetic field transmitted by the reader. © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 22/28

Radio Frequency Identification § RFID represents the biggest challenge to the predominance of bar codes § Wal-Mart, Target, Metro AG (Germany) and U. S. Do. D have mandated their suppliers use RFID on incoming materials § According to a study of Wal-Mart, "RFID stores are 63 percent more effective in replenishing out-of-stock items than traditional stores" © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 23/28

Types of RFID Tags 1. Passive tags § Have no internal power source § They derive their electrical power from the external signal transmitted by the reader § Smaller, less expensive, longer lasting 2. Active tags § Have their own battery power packs § Possess a larger memory capacity and longer communication range § Higher cost and used for higher value items © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 24/28

Industrial Applications of RFID § § § Inventory management Supply chain management Tracking systems Warehouse control Location identification Work-in-progress © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 25/28

RFID Advantages and Disadvantages § Advantages § Identification does not depend on physical contact or direct line of sight § Much more data can be contained in the identification tag than with most AIDC technologies § Data in read/write tags can be altered for historical usage purposes or to reuse the tag § Disadvantages § More expensive than most other AIDC technologies © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 26/28

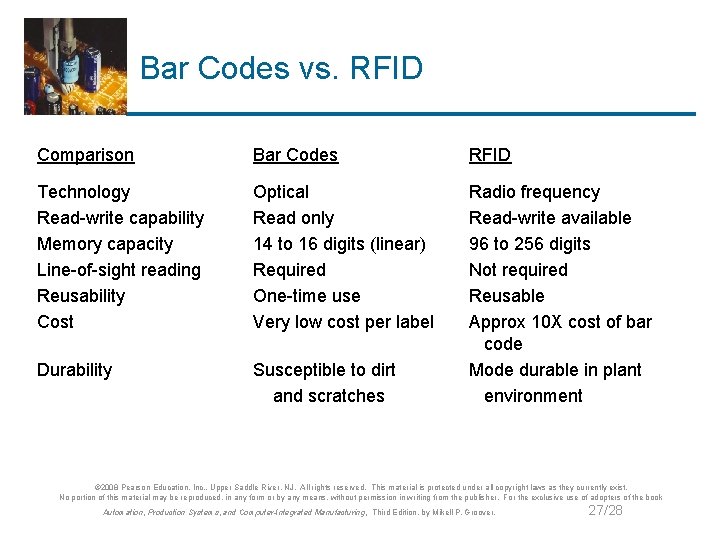
Bar Codes vs. RFID Comparison Bar Codes RFID Technology Read-write capability Memory capacity Line-of-sight reading Reusability Cost Optical Read only 14 to 16 digits (linear) Required One-time use Very low cost per label Durability Susceptible to dirt and scratches Radio frequency Read-write available 96 to 256 digits Not required Reusable Approx 10 X cost of bar code Mode durable in plant environment © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 27/28

Other AIDC Technologies § Magnetic stripes § Used for credit cards and money access cards § More expensive than bar codes § Must contact scanner to obtain a reading § Optical character recognition (OCR) § Can be read by humans and machine readers § Low first read rate § Machine vision § Principal application is inspection § Used with 2 -D optical symbols © 2008 Pearson Education, Inc. , Upper Saddle River, NJ. All rights reserved. This material is protected under all copyright laws as they currently exist. No portion of this material may be reproduced, in any form or by any means, without permission in writing from the publisher. For the exclusive use of adopters of the book Automation, Production Systems, and Computer-Integrated Manufacturing, Third Edition, by Mikell P. Groover. 28/28