CERN European Organization for Nuclear Research GS Department




















































- Slides: 83

CERN – European Organization for Nuclear Research GS Department – Administrative Information Services Secure software development for the World Wide Web Derek Mathieson Group Leader Advanced Information Systems CERN – Geneva, Switzerland

Agenda l Impact of Security Flaws l Definitions l Types of Attack l Techniques / Solutions CERN GS-AIS

Why Secure Web Application? CERN GS-AIS

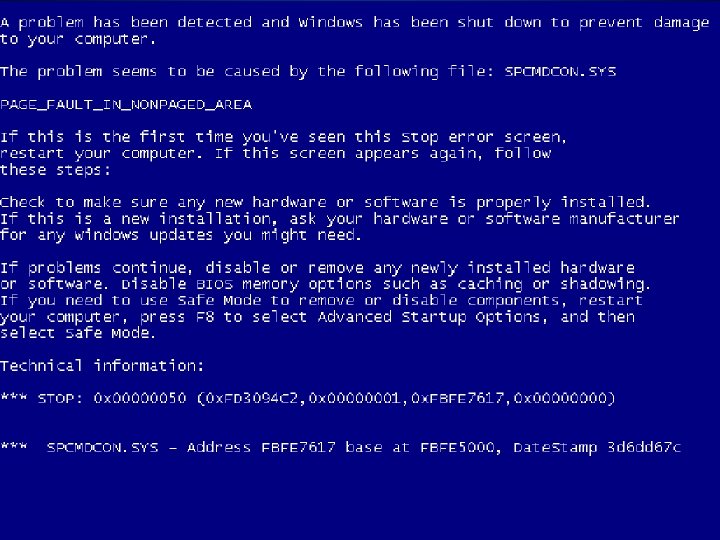
Impact of Security Flaws l Ping of death l Morris worm (1988) – ~6, 000 infected computers l Santy (2004) – ~40, 000 infected computers (in 24 hours) l Conficker (2008) – 17, 000 infected computers CERN GS-AIS

US Army l Computer CERN GS-AIS Virus Hits U. S. Drone Fleet

SONY Play. Station Network CERN GS-AIS

Sony. Pictures. com CERN GS-AIS

SONY Play. Station Network CERN GS-AIS

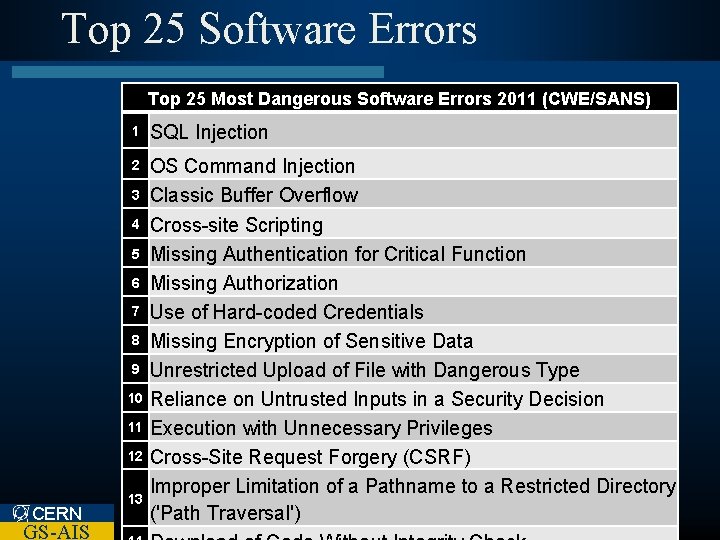
Top 25 Software Errors Top 25 Most Dangerous Software Errors 2011 (CWE/SANS) 1 SQL Injection 2 OS Command Injection Classic Buffer Overflow Cross-site Scripting Missing Authentication for Critical Function Missing Authorization Use of Hard-coded Credentials Missing Encryption of Sensitive Data Unrestricted Upload of File with Dangerous Type Reliance on Untrusted Inputs in a Security Decision Execution with Unnecessary Privileges Cross-Site Request Forgery (CSRF) Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') 3 4 5 6 7 8 9 10 11 12 CERN GS-AIS 13

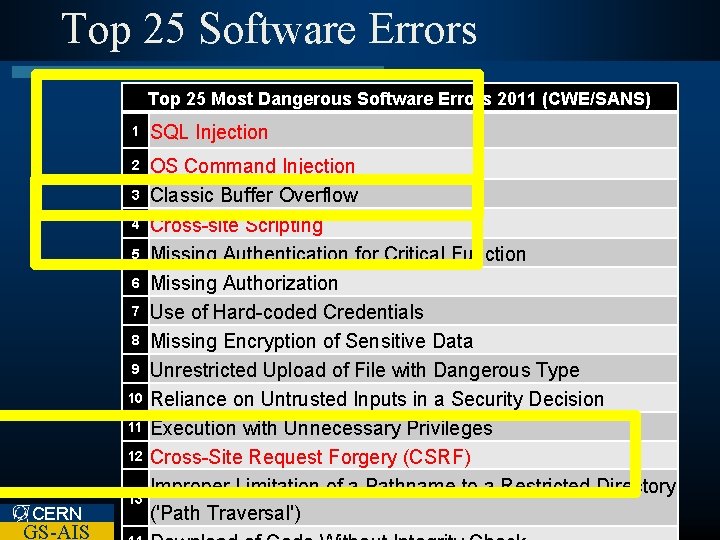
Top 25 Software Errors Top 25 Most Dangerous Software Errors 2011 (CWE/SANS) 1 SQL Injection 2 OS Command Injection Classic Buffer Overflow Cross-site Scripting Missing Authentication for Critical Function Missing Authorization Use of Hard-coded Credentials Missing Encryption of Sensitive Data Unrestricted Upload of File with Dangerous Type Reliance on Untrusted Inputs in a Security Decision Execution with Unnecessary Privileges Cross-Site Request Forgery (CSRF) Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') 3 4 5 6 7 8 9 10 11 12 CERN GS-AIS 13

Definitions l Identification l Authentication l Authorisation l Session CERN GS-AIS Management

Identification / Authentication l How Can You Prove Who You Are? – Biometric Passport – Photo ID – Fingerprint – Username / Password CERN GS-AIS

Definitions l Entity – A User, another computer system component l Identification – Providing credential such that a system can recognise the entity and distinguish it from other entities. l Authentication – The process of verifying the identity of an entity. CERN GS-AIS

Authentication Factors l Something an entity knows: – Password, PIN l Something an entity has: – ID Card, private key l Something an entity is: – Fingerprint, iris scan, … CERN GS-AIS

Authentication l Single / Multi-factor Authentication – Password only – Password + Fingerprint l Trade-off between – Convenience – Cost – Complexity – Security CERN GS-AIS

Identity Theft l Compromised Passwords – Self Service password reset l Lost ID Cards – Blocking List l Compromised Private Keys – CRL l What about Biometrics? – No easy solution CERN GS-AIS

Passwords l Server good practices – Never store them in ‘clear’ – Use encrypted communication protocols (SSL) – Log authentication failures – Use generic error messages: • User/password combination not recognised’ – Show user • Last login date • Previous failed login attempts CERN GS-AIS

Web Authentication Techniques l Basic Authentication l Digest Authentication l Form Authentication CERN GS-AIS

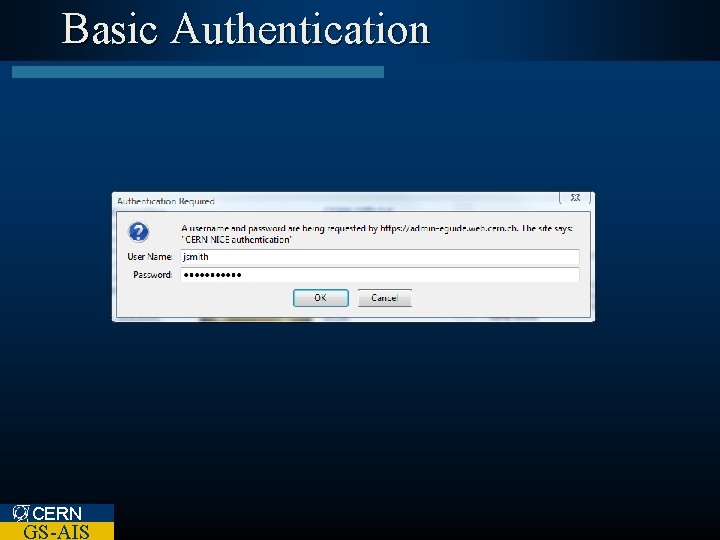
Basic Authentication CERN GS-AIS

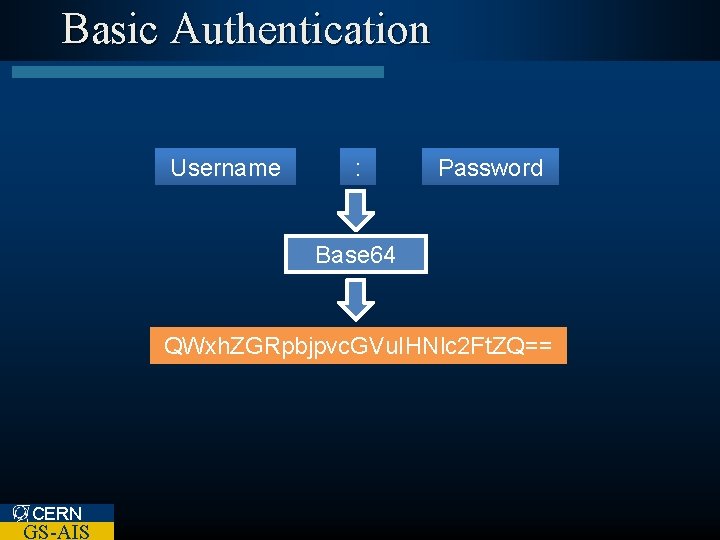
Basic Authentication Username : Password Base 64 QWxh. ZGRpbjpvc. GVu. IHNlc 2 Ft. ZQ== CERN GS-AIS

Basic Authentication l No encryption – Username / Password ‘encoded’ l Depends channel CERN GS-AIS on a secure communication

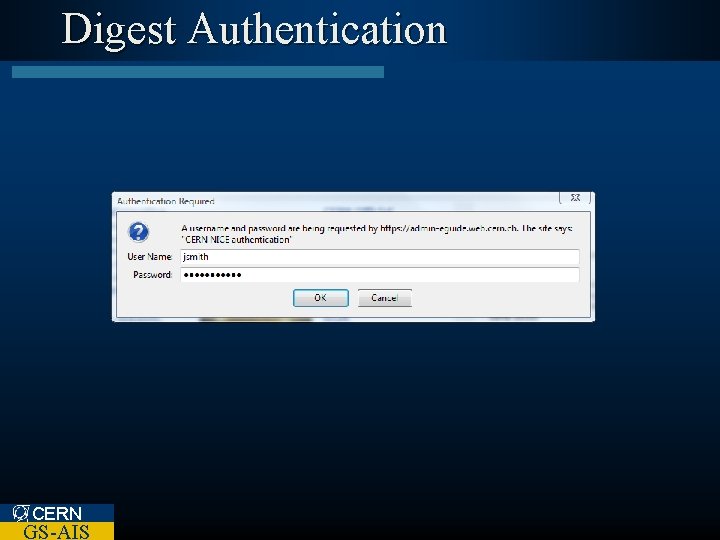
Digest Authentication CERN GS-AIS

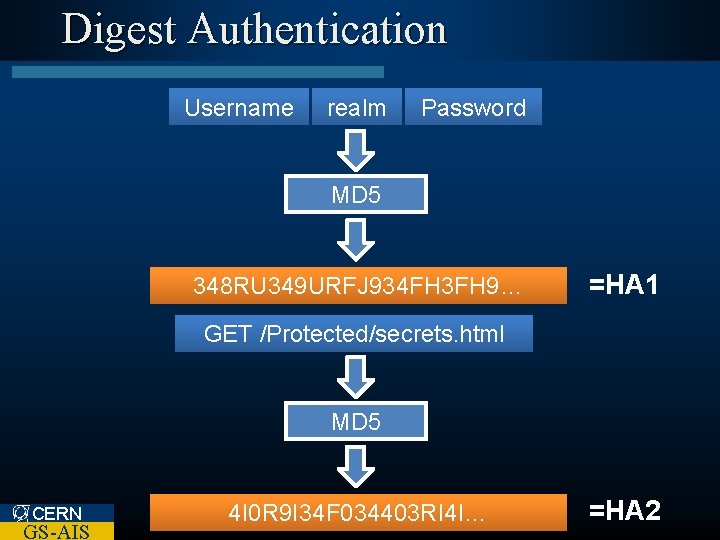
Digest Authentication Username realm Password MD 5 348 RU 349 URFJ 934 FH 3 FH 9… =HA 1 GETMethod /Protected/secrets. html URI MD 5 CERN GS-AIS 4 I 0 R 9 I 34 F 034403 RI 4 I… =HA 2

Digest Authentication HA 1 nonce HA 2 MD 5 R 3984 UR 34 R 43 RU… CERN GS-AIS =response

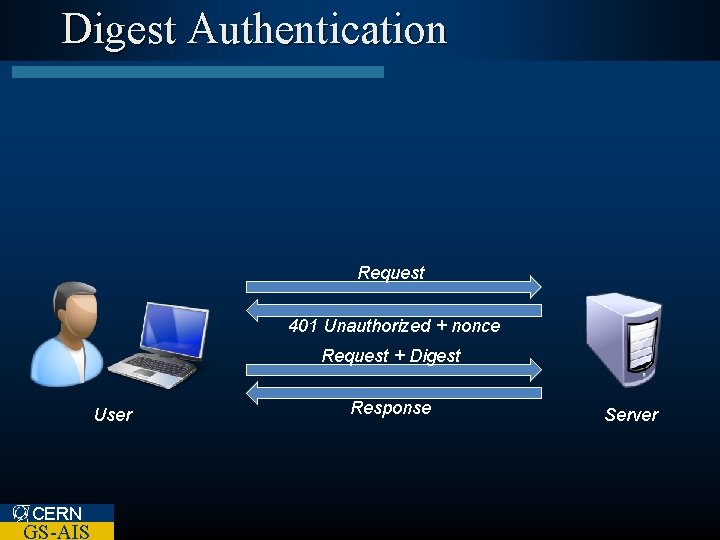
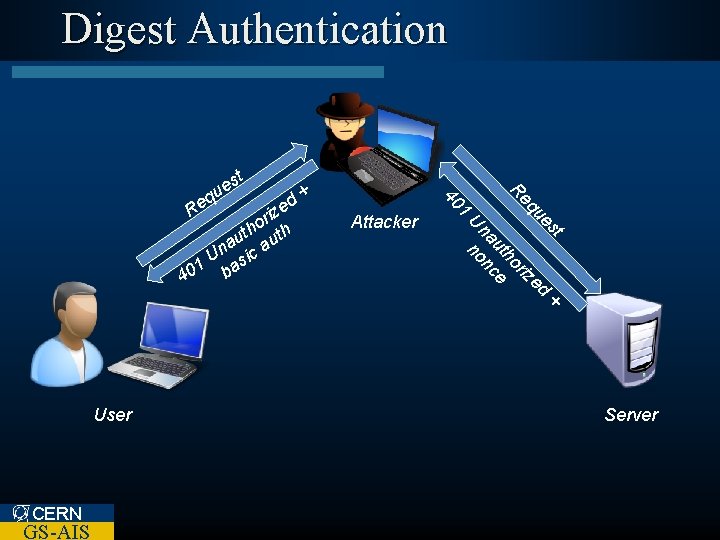
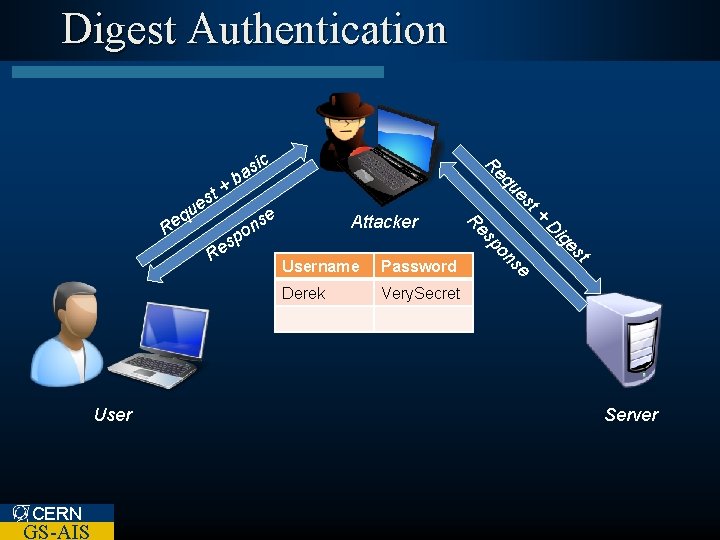
Digest Authentication l Advantages – Communication is more secure • Some doubts over irreversibility of MD 5 – Server nonce can avoid replay attacks l Disadvantages – Server password file is contains usable credentials in plaintext – Vulnerable to a man-in-the-middle (Mit. M) attack CERN GS-AIS

Digest Authentication Request 401 Unauthorized + nonce Request + Digest User CERN GS-AIS Response Server

Digest Authentication t GS-AIS st + ue ed eq riz R ho ut ce na on n CERN U User Attacker 1 + d ize r o h h t au aut n U sic 1 a 40 b q Re 40 s ue Server

Digest Authentication eq t es ig Very. Secret D Derek e Password ns Username + s Re st ue Attacker po GS-AIS e ns o p es CERN u R User + R q Re t es ic s ba Server

Form Authentication CERN GS-AIS

Form Authentication l Advantages – Simple to develop – Richer User Interface – Can use multifactor authentication l Disadvantages – Depends on a secure communication channel (usually) CERN GS-AIS

Other Authentication Methods l Single Sign-on – Open. ID, Shibboleth, … l Integrated Windows Authentication l Token-based – One Time Passwords (OTP) • Secure. ID, Yubi. Key – Public key authentication (SSL client certificates). CERN GS-AIS

Authorisation CERN GS-AIS

Authorisation l An Authorisation system should: – Allow access to resources to users/systems that are permitted to access them. – Prevent access to those that are not permitted. CERN GS-AIS

Authorisation l System requirements: – Who (entity) – What (resource) – Which operation (read / update / delete / …) – Access Policy CERN GS-AIS

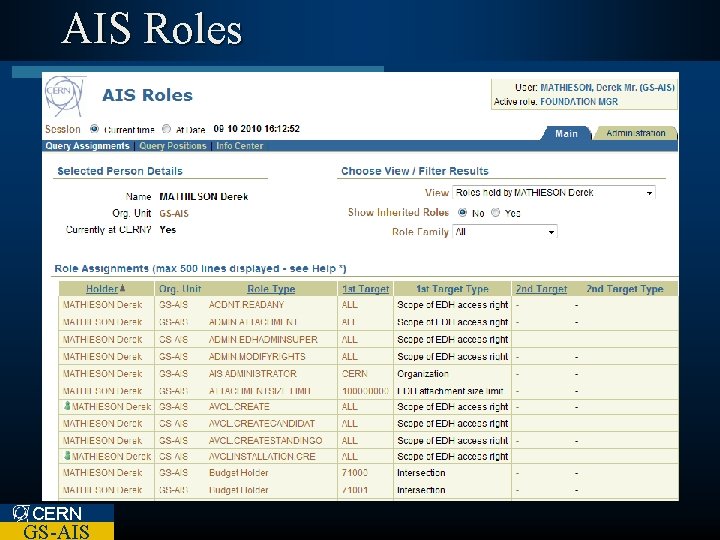
Role Based Access Control l Roles are identified – e. g. administrator, group leader, developer. l Rights are assigned to roles – group leader can access homepage l Roles are assigned to entities – Derek is a group leader CERN GS-AIS

AIS Roles CERN GS-AIS

Role Based Access Control l Less complex than individual assignment of access rights l Roles can link to organization roles – Automatic maintenance – Less administration CERN GS-AIS

Authorisation: Good Practices l Check every access l Centralise rights management l Principal of Least Privilege CERN GS-AIS

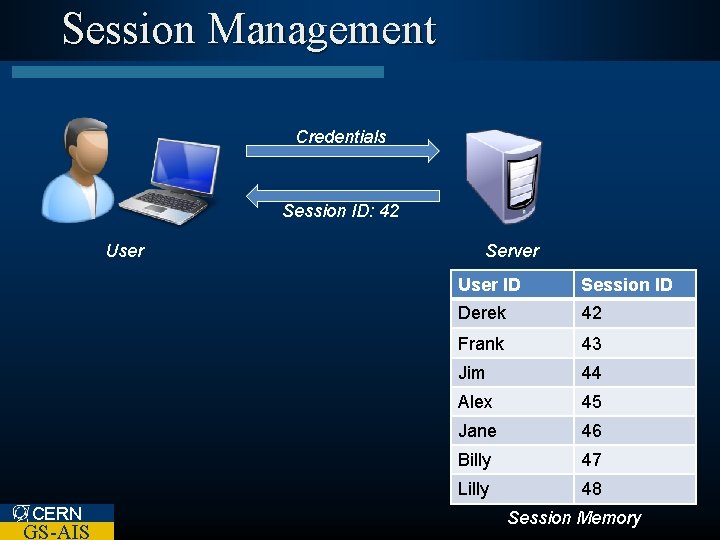
Session Management CERN GS-AIS

Session Management l Why do we need it? – HTTP is state-less CERN GS-AIS

Session Management Credentials Session ID: 42 User CERN GS-AIS Server User ID Session ID Derek 42 Frank 43 Jim 44 Alex 45 Jane 46 Billy 47 Lilly 48 Session Memory

Session Management l Good Practices – Keep Session ID secret! • Use encrypted communications. – Make them unpredictable • Based on a random sequence • Never re-used – Time limited l Use CERN GS-AIS a standard framework

Types of Attack CERN GS-AIS

Types of Attack l Session – Session Fixation / Session ID Forgery – Cross-Site Scripting – Cross-Site Request Forgery l Injection – SQL Injection – Command Injection l Google CERN GS-AIS Hacks

Session ID Forgery l URL Manipulation l POST parameter Manipulation CERN GS-AIS

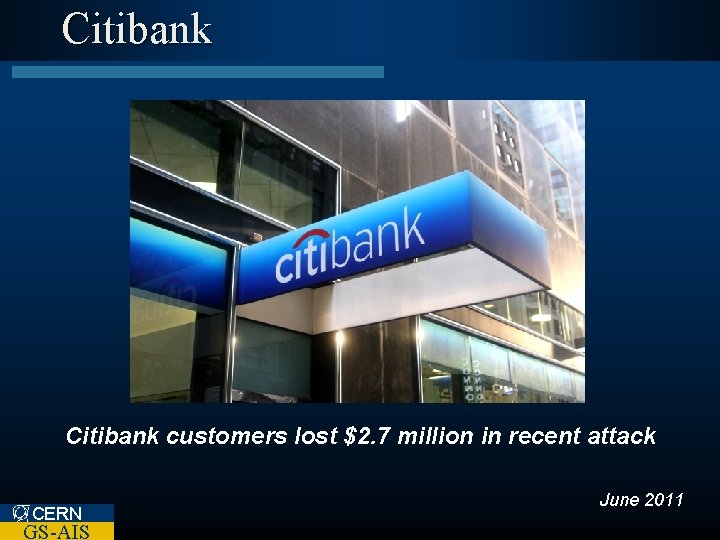
Citibank customers lost $2. 7 million in recent attack CERN GS-AIS June 2011

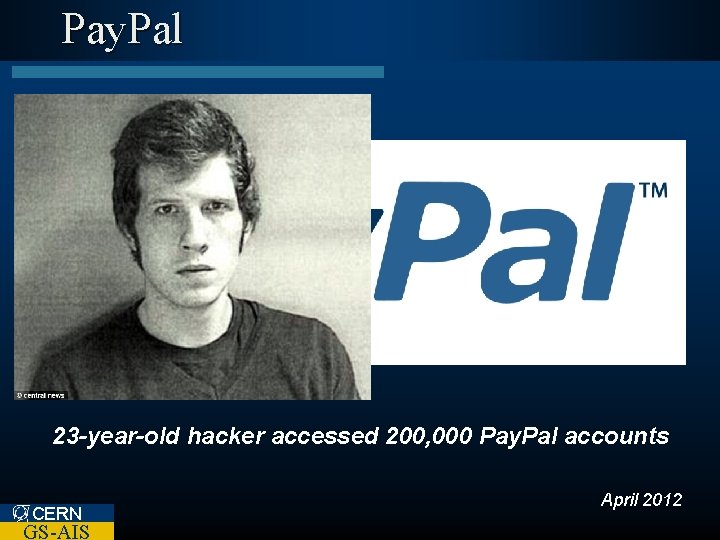
Pay. Pal 23 -year-old hacker accessed 200, 000 Pay. Pal accounts CERN GS-AIS April 2012

Cross-Site Scripting XSS CERN GS-AIS

Cross-Site Scripting l The most common publicly-reported security vulnerability – Up to 68% of websites could be vulnerable CERN GS-AIS

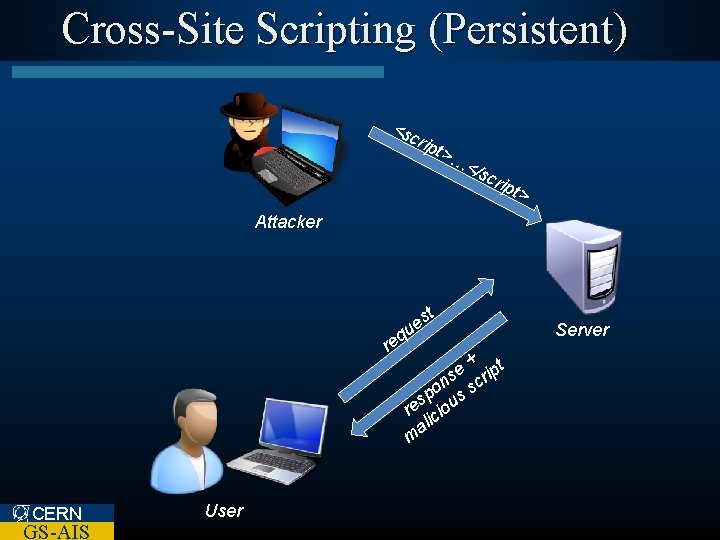
Cross-Site Scripting (Persistent) <s crip t>… </s crip t> Attacker q re st e u + t e s crip n po us s s re cio ali m CERN GS-AIS User Server

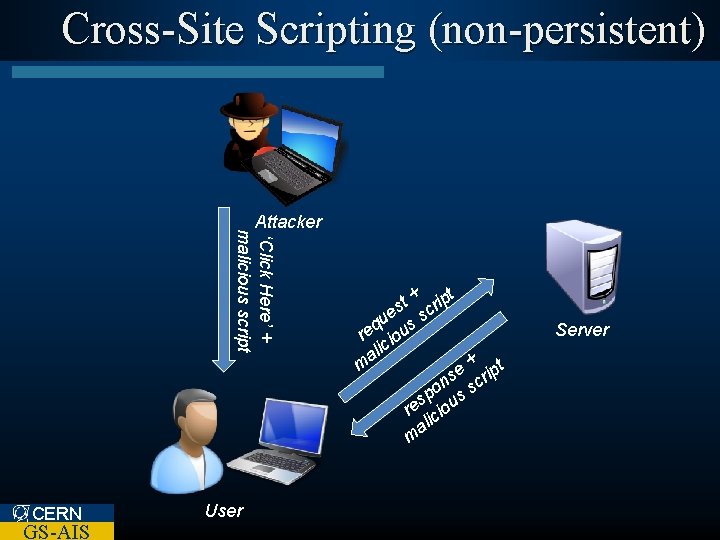
Cross-Site Scripting (non-persistent) ‘Click Here’ + malicious script Attacker CERN GS-AIS User + ipt t s cr e u ss q re iou c ali + t m e s crip n po us s s re cio ali m Server

Cross-Site Scripting: Impact l Site CERN GS-AIS defacement

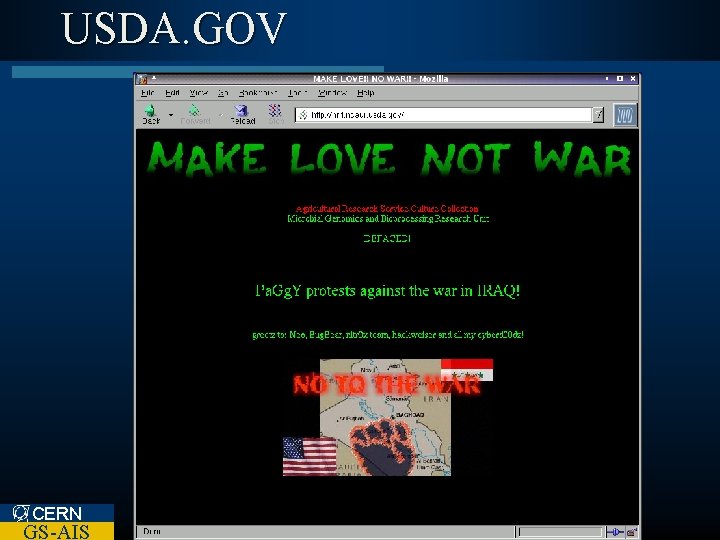
USDA. GOV CERN GS-AIS

EU President CERN GS-AIS

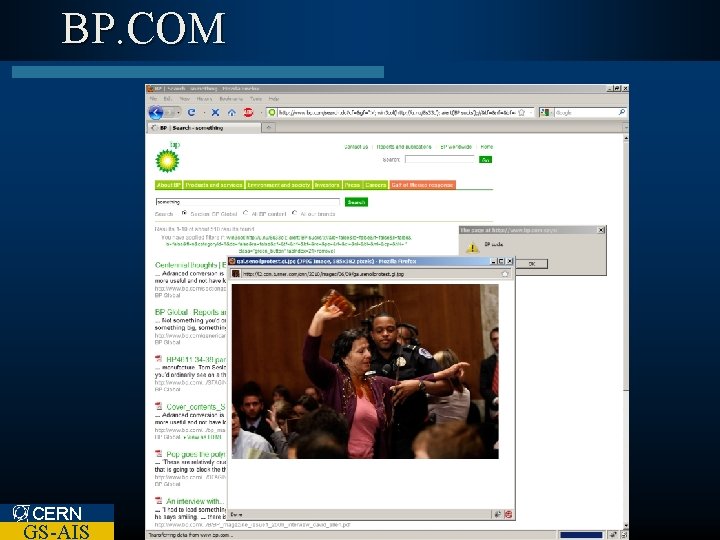
BP. COM CERN GS-AIS

Cross-Site Scripting: Impact l Site defacement l Identity Theft l Malware distribution l… CERN GS-AIS

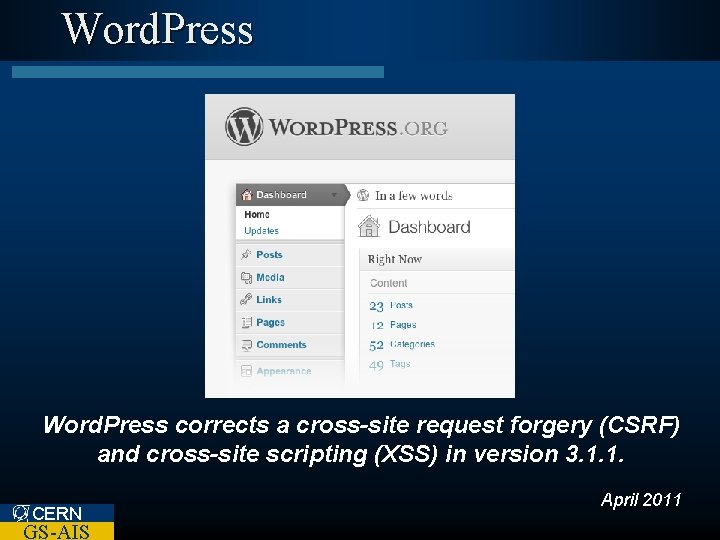
Word. Press corrects a cross-site request forgery (CSRF) and cross-site scripting (XSS) in version 3. 1. 1. CERN GS-AIS April 2011

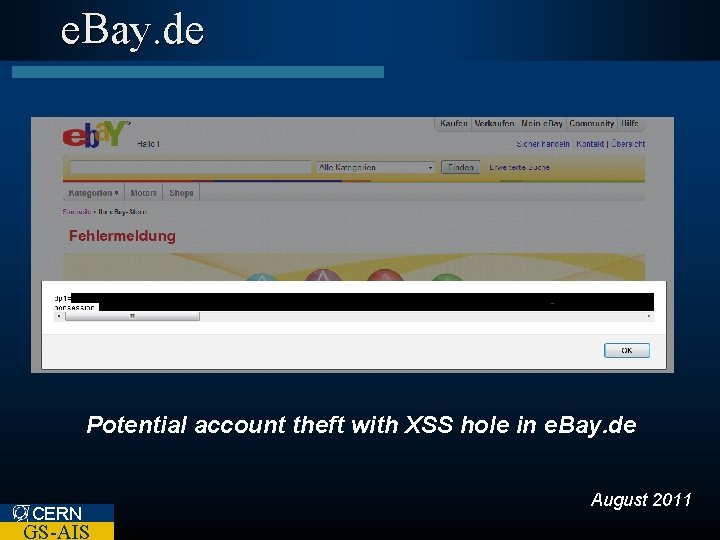
e. Bay. de Potential account theft with XSS hole in e. Bay. de CERN GS-AIS August 2011

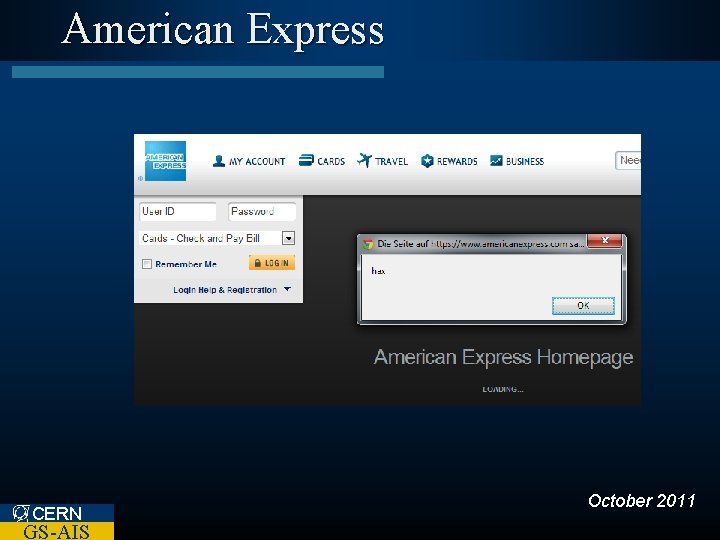
American Express CERN GS-AIS October 2011

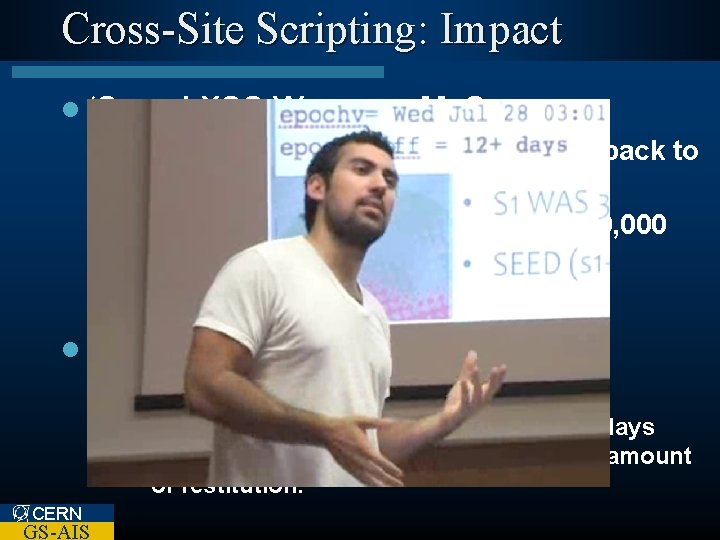
Cross-Site Scripting: Impact l ‘Samy’ XSS Worm on My. Space – Automatically made ‘friend request’ back to author. – Within 20 hours of release over 1, 000 users were affected. l Author: Samy Kamkar – Arrested and on felony charge. • Sentenced to three years probation, 90 days community service and an undisclosed amount of restitution. CERN GS-AIS

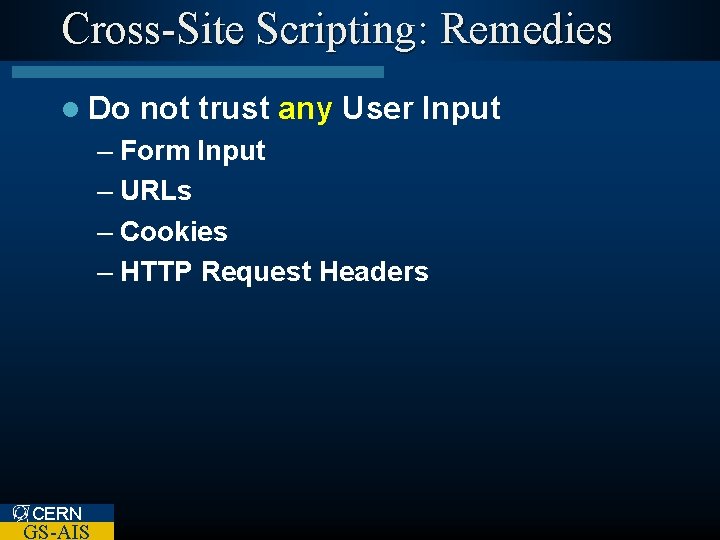
Cross-Site Scripting: Remedies l Do not trust any User Input – Form Input – URLs – Cookies – HTTP Request Headers CERN GS-AIS

Cross-Site Scripting: Remedies l Remove / replace HTML entities – ‘White List’ or ‘Black List’ Filter l Use Non-HTML Lightweight mark-up – Wiki – bb-code – Textile l Use a Site Scanning Tool – We use Acunetix CERN GS-AIS

Exploit Test Site http: //bit. ly/K 8 Zy 6 K CERN GS-AIS

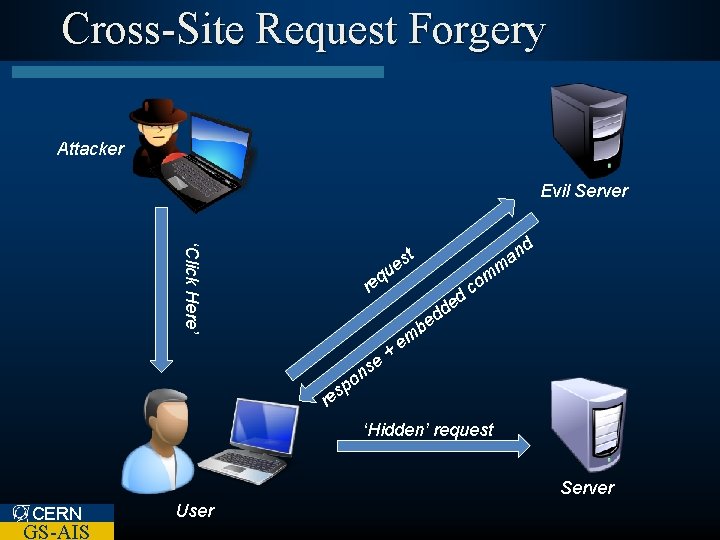
Cross-Site Request Forgery CSRF / XSRF CERN GS-AIS

Cross-Site Request Forgery Attacker Evil Server ‘Click Here’ d t es m u eq r d d be o sp se + an ed om c em n re ‘Hidden’ request Server CERN GS-AIS User

Cross-Site Request Forgery Embedded Image <img src="http: //bank. example/withdraw? account=bob&amount=1000000&for=mallory"> Hidden Form <body onload="document. secretform. submit()"> <form name="secretform" method="POST" action="http: bank. example/account"> <input type="hidden" name="action" value= "transfer"> … </form> </body> CERN GS-AIS

CSRF: Remedies l For End Users: Very Little! – Log out before visiting other sites – Don’t use ‘remember me’ features – Don’t visit ‘untrustworthy’ sites CERN GS-AIS

CSRF: Remedies l For Website Authors – Include a hidden ‘nonce’ token in forms – Ignore GET parameters when processing a POST – Include Authentication Cookies in POST body (via Java. Script) CERN GS-AIS

Injection Exploits SQL Injection CERN GS-AIS

SQL Injection l SQL Injection is user input allowed to pass through to the database directly CERN GS-AIS

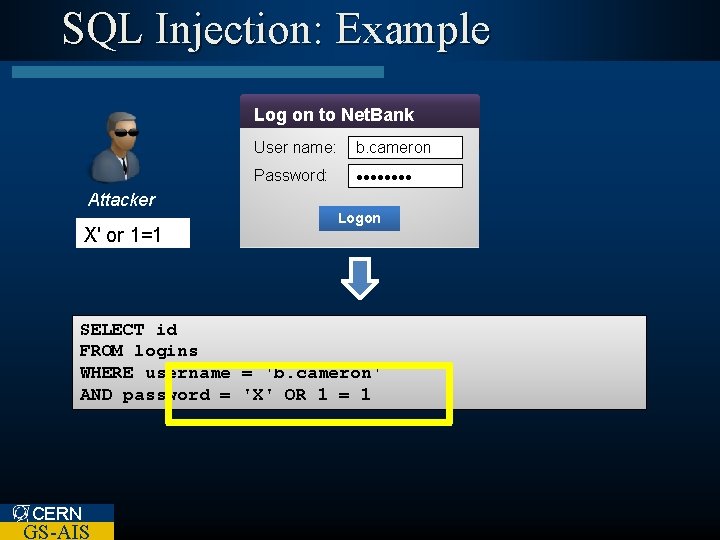
SQL Injection: Example Log on to Net. Bank User name: b. cameron Password: • • • • Attacker X' or 1=1 Logon SELECT id FROM logins WHERE username = 'b. cameron' '$username' AND password = 'X' '$password' 'Secret. Word' OR 1 = 1 CERN GS-AIS

SQL Injection: Remedies l Do not trust any User Input – Form Input – URLs – Cookies – HTTP Request Headers l Use CERN GS-AIS a Site Scanning Tool

SQL Injection: Remedies l Prepared Statements SELECT id FROM logins WHERE username = ? AND password = ? – Advantages • Precompiled Query: Faster (usually) • Database engine does the bind – Disadvantages • (a little) More Complex CERN GS-AIS

Other Exploits CERN GS-AIS

Command Injection l Variation of SQL Injection – Injects malicious OS command exec ("ls. ; " +cat /home/myfiles") $user. Path) /etc/passwd") CERN GS-AIS

Google Hacking Database l http: //www. exploit-db. com/google-dorks/ CERN GS-AIS

Summary l Do not trust any User Input – Form Input – URLs – Cookies – HTTP Request Headers l Use CERN GS-AIS a Site Scanning Tool

Thank You CERN GS-AIS

Questions l My website is not well known – No bad people will find it… l http: //www. exploit-db. com CERN GS-AIS

Questions l Hacking websites is difficult. – You need to be an expert programmer. l Metasploit l Be. EF CERN GS-AIS

http: //www. 1337 day. com/ CERN GS-AIS

http: //www. exploit-db. com/ CERN GS-AIS

Thank You CERN GS-AIS
 Lesson 15 nuclear quest nuclear reactions
Lesson 15 nuclear quest nuclear reactions Fisión nuclear vs fision nuclear
Fisión nuclear vs fision nuclear Cern beams department
Cern beams department Mar capeans
Mar capeans Cern openlab
Cern openlab Intel vp weekly compute projectian
Intel vp weekly compute projectian Cern it department
Cern it department European landowners organization
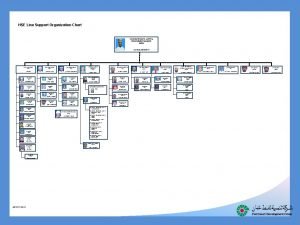
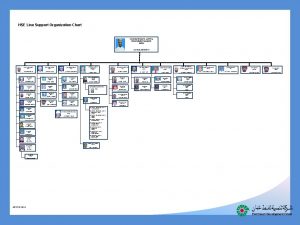
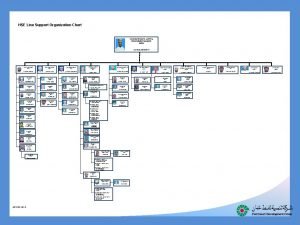
European landowners organization Hse department organization chart
Hse department organization chart Organization chart hse department
Organization chart hse department Hse org chart
Hse org chart Organization chart of banquet department
Organization chart of banquet department Hse advisor adalah
Hse advisor adalah Hse department organization chart
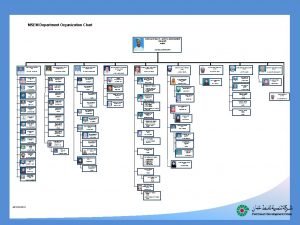
Hse department organization chart Mse org chart
Mse org chart Harib9
Harib9 Hse department organization chart
Hse department organization chart Safety department organization chart
Safety department organization chart Process organization in computer organization
Process organization in computer organization Point by point organization
Point by point organization European strategy forum on research infrastructures
European strategy forum on research infrastructures European commission community research
European commission community research Fspos vägledning för kontinuitetshantering
Fspos vägledning för kontinuitetshantering Novell typiska drag
Novell typiska drag Tack för att ni lyssnade bild
Tack för att ni lyssnade bild Vad står k.r.å.k.a.n för
Vad står k.r.å.k.a.n för Varför kallas perioden 1918-1939 för mellankrigstiden?
Varför kallas perioden 1918-1939 för mellankrigstiden? En lathund för arbete med kontinuitetshantering
En lathund för arbete med kontinuitetshantering Kassaregister ideell förening
Kassaregister ideell förening Personlig tidbok för yrkesförare
Personlig tidbok för yrkesförare A gastrica
A gastrica Densitet vatten
Densitet vatten Datorkunskap för nybörjare
Datorkunskap för nybörjare Stig kerman
Stig kerman Hur skriver man en tes
Hur skriver man en tes Magnetsjukhus
Magnetsjukhus Nyckelkompetenser för livslångt lärande
Nyckelkompetenser för livslångt lärande Påbyggnader för flakfordon
Påbyggnader för flakfordon Tryck formel
Tryck formel Svenskt ramverk för digital samverkan
Svenskt ramverk för digital samverkan Kyssande vind analys
Kyssande vind analys Presentera för publik crossboss
Presentera för publik crossboss Vad är ett minoritetsspråk
Vad är ett minoritetsspråk Bat mitza
Bat mitza Treserva lathund
Treserva lathund Mjälthilus
Mjälthilus Claes martinsson
Claes martinsson Centrum för kunskap och säkerhet
Centrum för kunskap och säkerhet Byggprocessen steg för steg
Byggprocessen steg för steg Bra mat för unga idrottare
Bra mat för unga idrottare Verktyg för automatisering av utbetalningar
Verktyg för automatisering av utbetalningar Rutin för avvikelsehantering
Rutin för avvikelsehantering Smärtskolan kunskap för livet
Smärtskolan kunskap för livet Ministerstyre för och nackdelar
Ministerstyre för och nackdelar Tack för att ni har lyssnat
Tack för att ni har lyssnat Vad är referatmarkeringar
Vad är referatmarkeringar Redogör för vad psykologi är
Redogör för vad psykologi är Stål för stötfångarsystem
Stål för stötfångarsystem Atmosfr
Atmosfr Borra hål för knoppar
Borra hål för knoppar Vilken grundregel finns det för tronföljden i sverige?
Vilken grundregel finns det för tronföljden i sverige? Fr formel
Fr formel Tack för att ni har lyssnat
Tack för att ni har lyssnat Rita perspektiv
Rita perspektiv Verksamhetsanalys exempel
Verksamhetsanalys exempel Tobinskatten för och nackdelar
Tobinskatten för och nackdelar Toppslätskivling dos
Toppslätskivling dos Modell för handledningsprocess
Modell för handledningsprocess Egg för emanuel
Egg för emanuel Elektronik för barn
Elektronik för barn Fredsgudinna
Fredsgudinna Strategi för svensk viltförvaltning
Strategi för svensk viltförvaltning Kung dog 1611
Kung dog 1611 Ellika andolf
Ellika andolf Sju för caesar
Sju för caesar Tack för att ni lyssnade
Tack för att ni lyssnade Uppställning multiplikation
Uppställning multiplikation Olika rim dikter
Olika rim dikter Inköpsprocessen steg för steg
Inköpsprocessen steg för steg Rbk mätning
Rbk mätning Ledarskapsteorier
Ledarskapsteorier Cellorov
Cellorov Myndigheten för delaktighet
Myndigheten för delaktighet Trög för kemist
Trög för kemist