Central Monitoring Solution VMS January 2020 Edition 2020



- Slides: 37

Central Monitoring Solution - VMS January 2020 Edition 2020. All Rights Reserved, page 1 Eye To Eye Security

Contents System Structure Product Overview Main Features Case Study References Eye To Eye Security 2020. All Rights Reserved, page 2

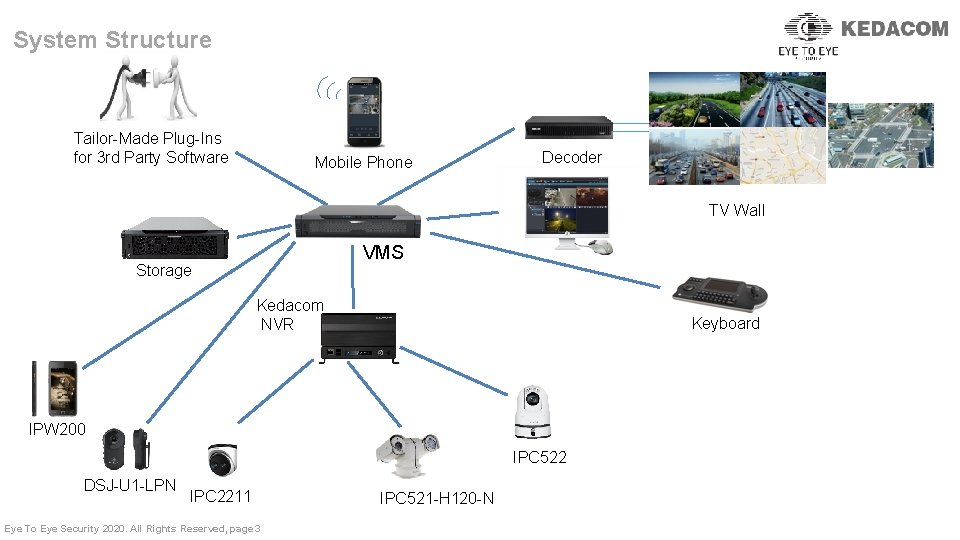
System Structure Tailor-Made Plug-Ins for 3 rd Party Software Mobile Phone Decoder TV Wall VMS Storage Kedacom NVR Keyboard IPW 200 IPC 522 DSJ-U 1 -LPN IPC 2211 Eye To Eye Security 2020. All Rights Reserved, page 3 IPC 521 -H 120 -N

Contents System Structure Product Overview Main Features Case Study References Eye To Eye Security 2020. All Rights Reserved, page 4

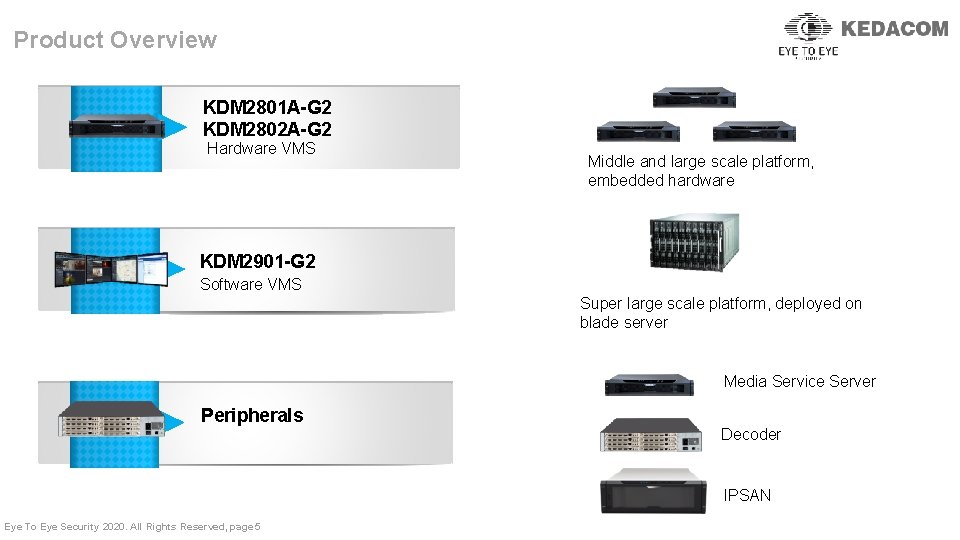
Product Overview KDM 2801 A-G 2 KDM 2802 A-G 2 Hardware VMS Middle and large scale platform, embedded hardware KDM 2901 -G 2 Software VMS Super large scale platform, deployed on blade server Media Service Server Peripherals Decoder IPSAN Eye To Eye Security 2020. All Rights Reserved, page 5

Contents System Structure Product Overview Main Features Case Study References Eye To Eye Security 2020. All Rights Reserved, page 6

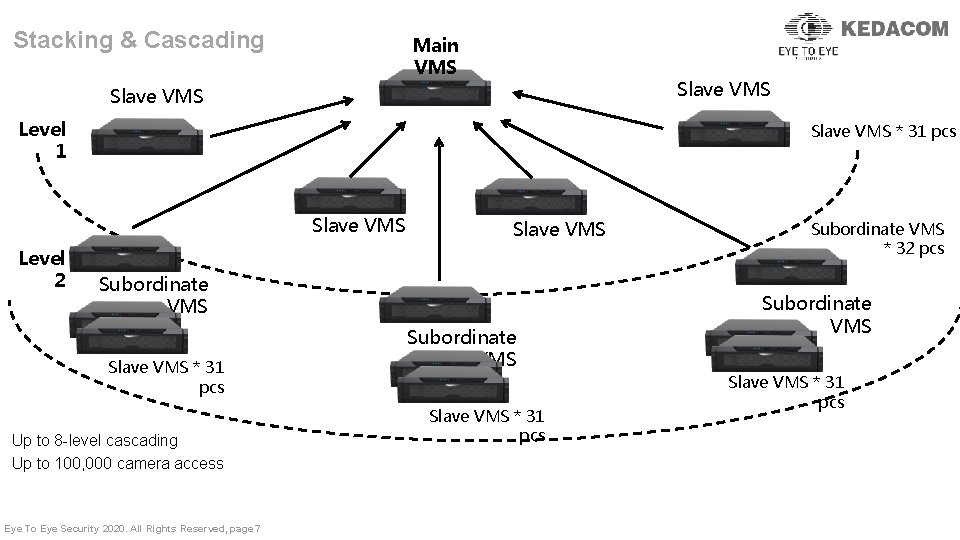
Stacking & Cascading Main VMS Slave VMS Level 1 Slave VMS * 31 pcs Slave VMS Level 2 Slave VMS Subordinate VMS Slave VMS * 31 pcs Up to 8 -level cascading Up to 100, 000 camera access Eye To Eye Security 2020. All Rights Reserved, page 7 Subordinate VMS Slave VMS * 31 pcs Subordinate VMS * 32 pcs Subordinate VMS Slave VMS * 31 pcs

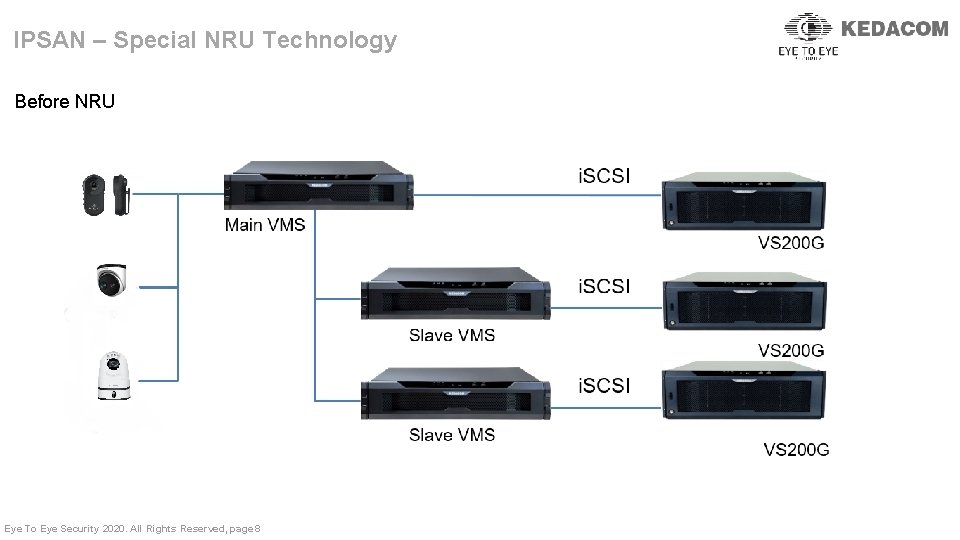
IPSAN – Special NRU Technology Before NRU Eye To Eye Security 2020. All Rights Reserved, page 8

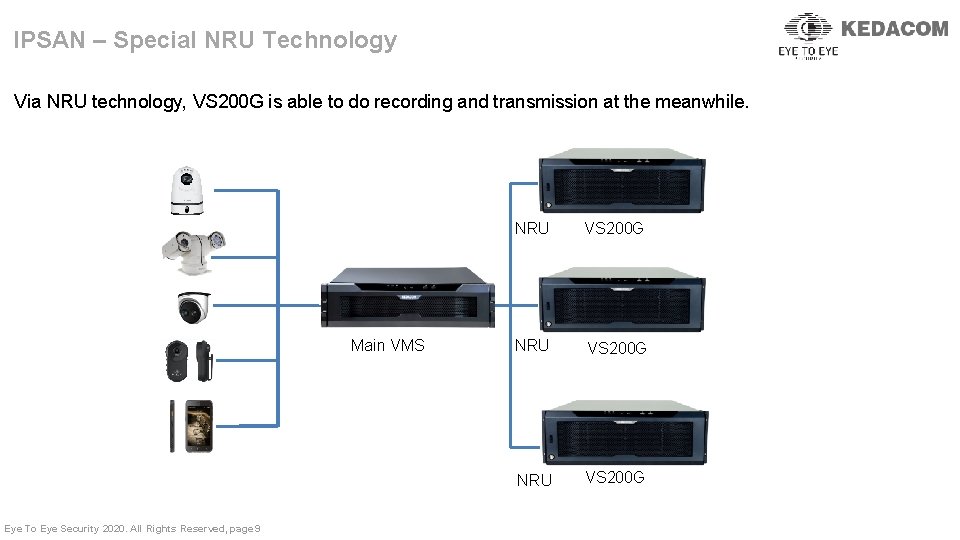
IPSAN – Special NRU Technology Via NRU technology, VS 200 G is able to do recording and transmission at the meanwhile. Main VMS Eye To Eye Security 2020. All Rights Reserved, page 9 NRU VS 200 G

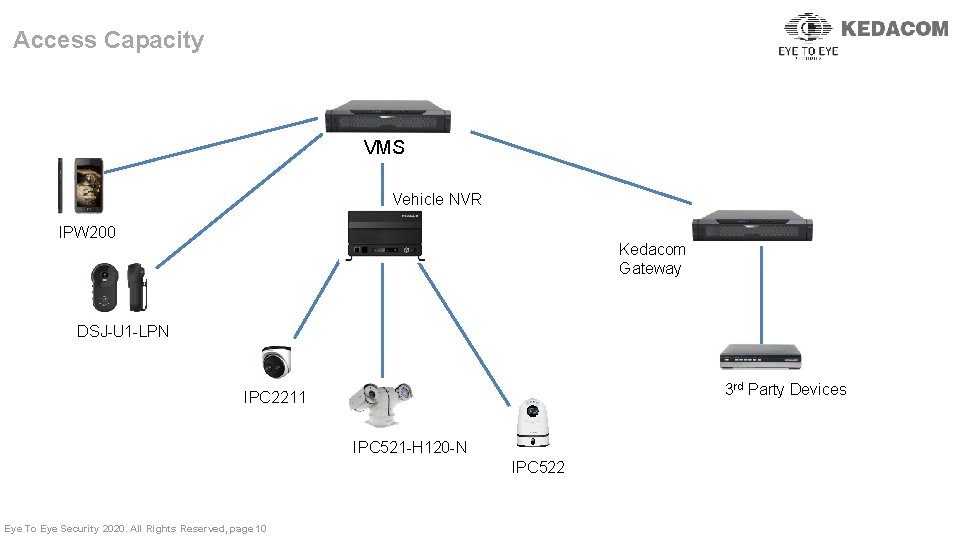
Access Capacity VMS Vehicle NVR IPW 200 Kedacom Gateway DSJ-U 1 -LPN 3 rd Party Devices IPC 2211 IPC 521 -H 120 -N IPC 522 Eye To Eye Security 2020. All Rights Reserved, page 10

VMS Management Client Tree Structure | Status Monitoring | Batching Operation | Precise searching | Virtual TV Wall | E-Map Eye To Eye Security 2020. All Rights Reserved, page 11

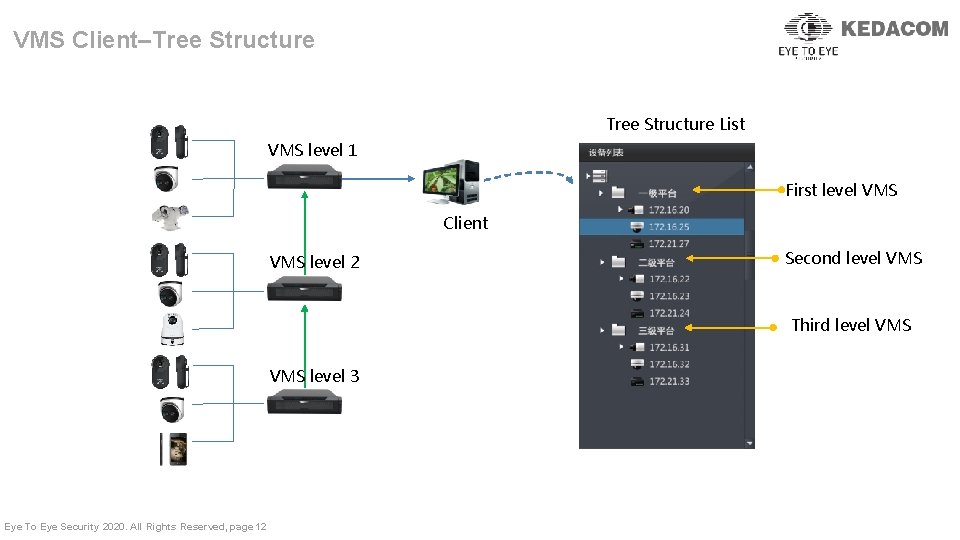
VMS Client–Tree Structure List VMS level 1 First level VMS Client VMS level 2 Second level VMS Third level VMS level 3 Eye To Eye Security 2020. All Rights Reserved, page 12

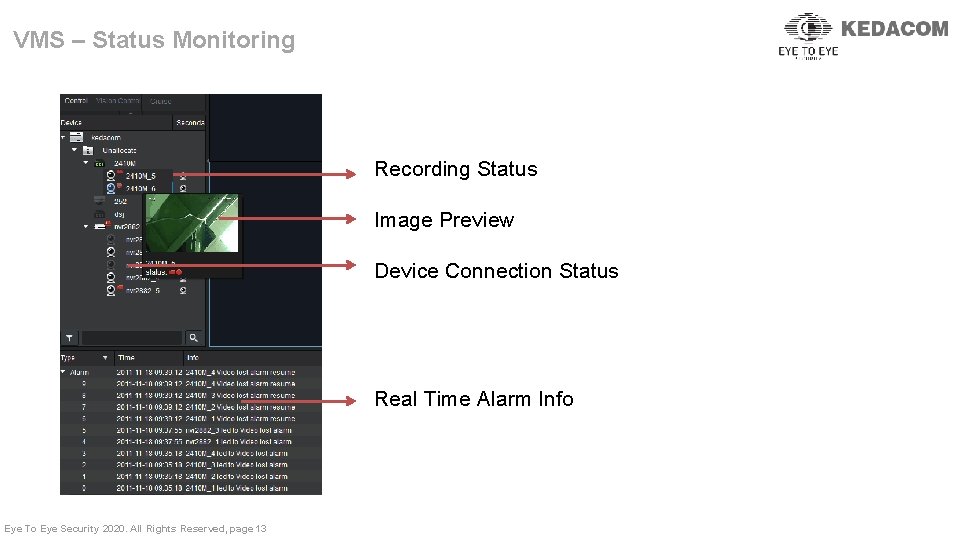
VMS – Status Monitoring Recording Status Image Preview Device Connection Status Real Time Alarm Info Eye To Eye Security 2020. All Rights Reserved, page 13

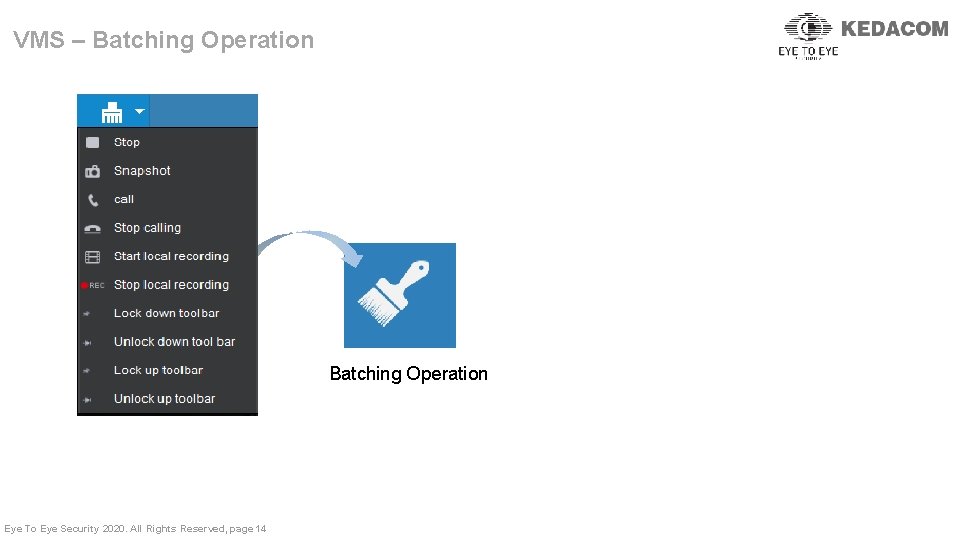
VMS – Batching Operation Eye To Eye Security 2020. All Rights Reserved, page 14

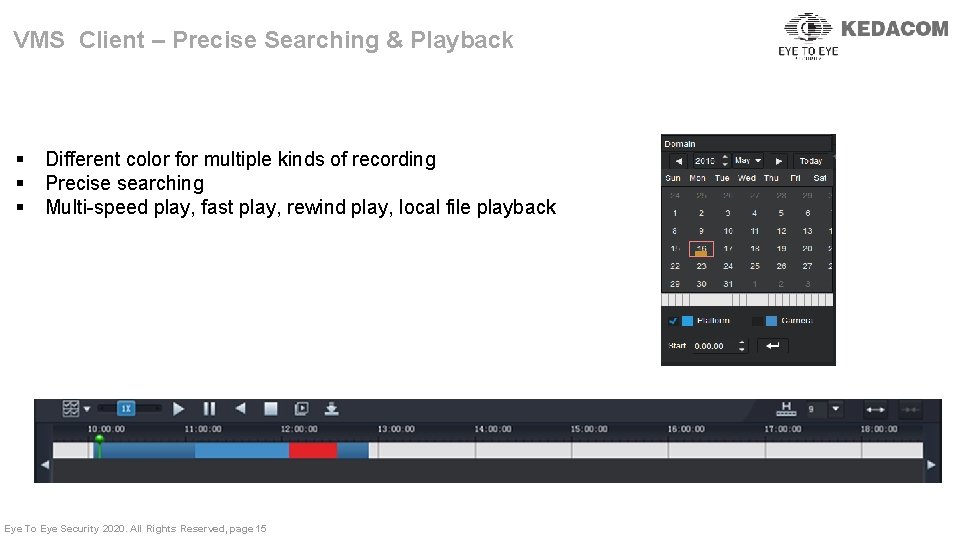
VMS Client – Precise Searching & Playback § § § Different color for multiple kinds of recording Precise searching Multi-speed play, fast play, rewind play, local file playback Eye To Eye Security 2020. All Rights Reserved, page 15

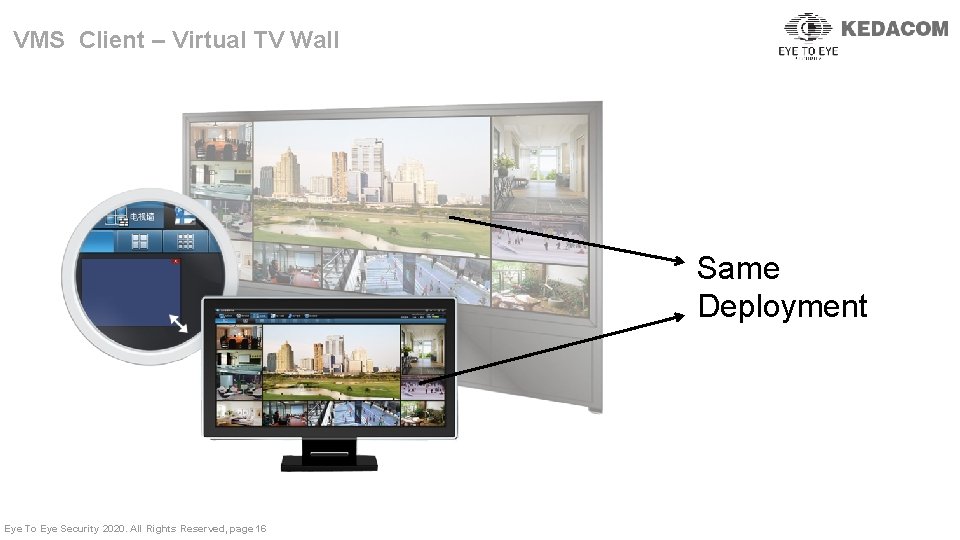
VMS Client – Virtual TV Wall Same Deployment Eye To Eye Security 2020. All Rights Reserved, page 16

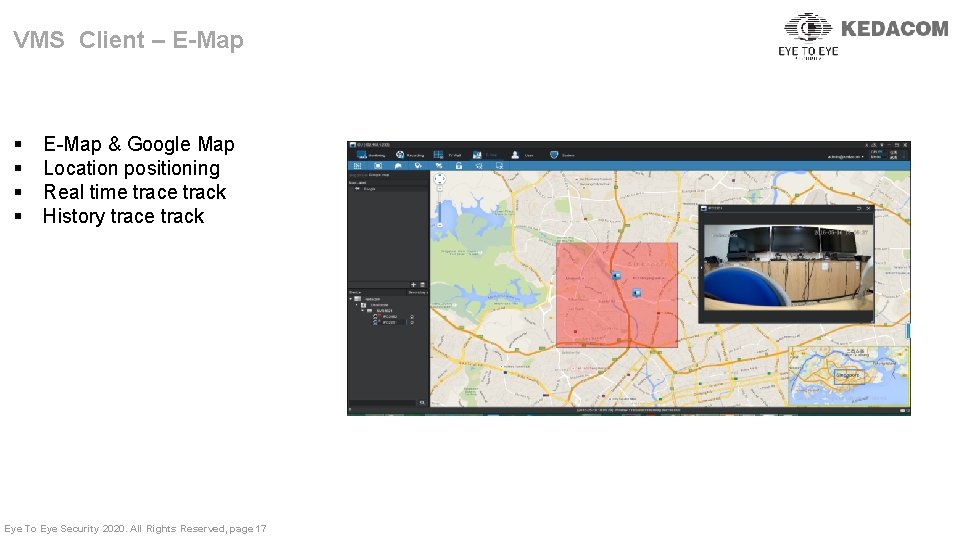
VMS Client – E-Map § § E-Map & Google Map Location positioning Real time track History trace track Eye To Eye Security 2020. All Rights Reserved, page 17

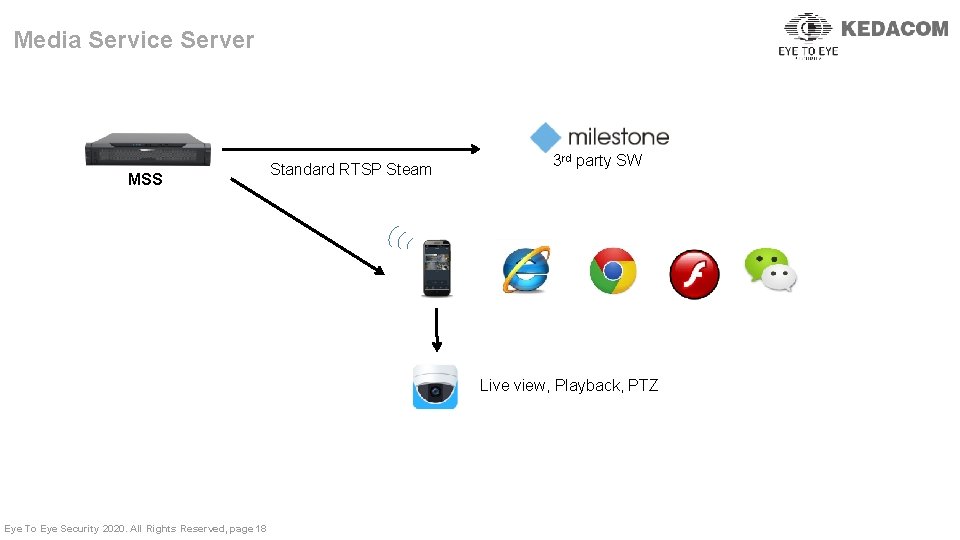
Media Service Server MSS Standard RTSP Steam 3 rd party SW Live view, Playback, PTZ Eye To Eye Security 2020. All Rights Reserved, page 18

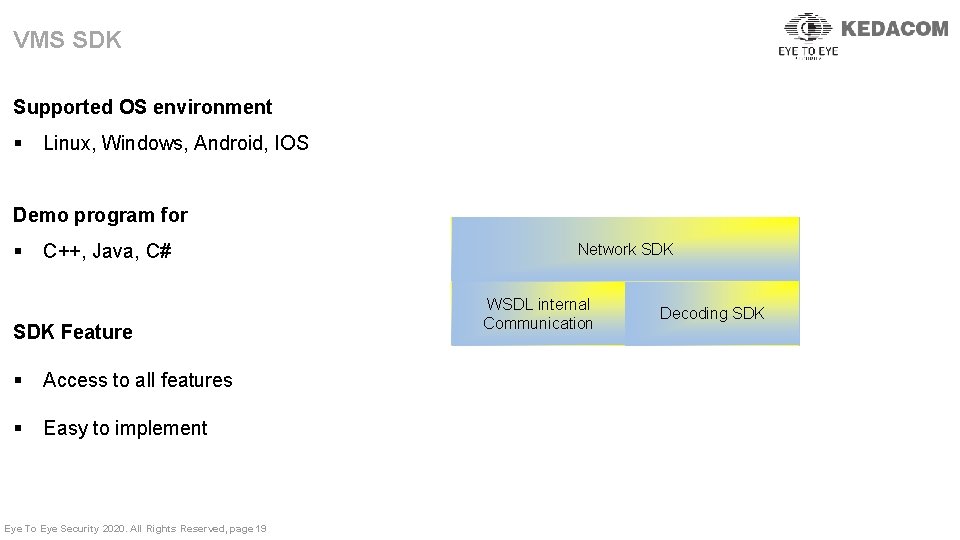
VMS SDK Supported OS environment § Linux, Windows, Android, IOS Demo program for § C++, Java, C# SDK Feature § Access to all features § Easy to implement Eye To Eye Security 2020. All Rights Reserved, page 19 Network SDK WSDL internal Communication Decoding SDK

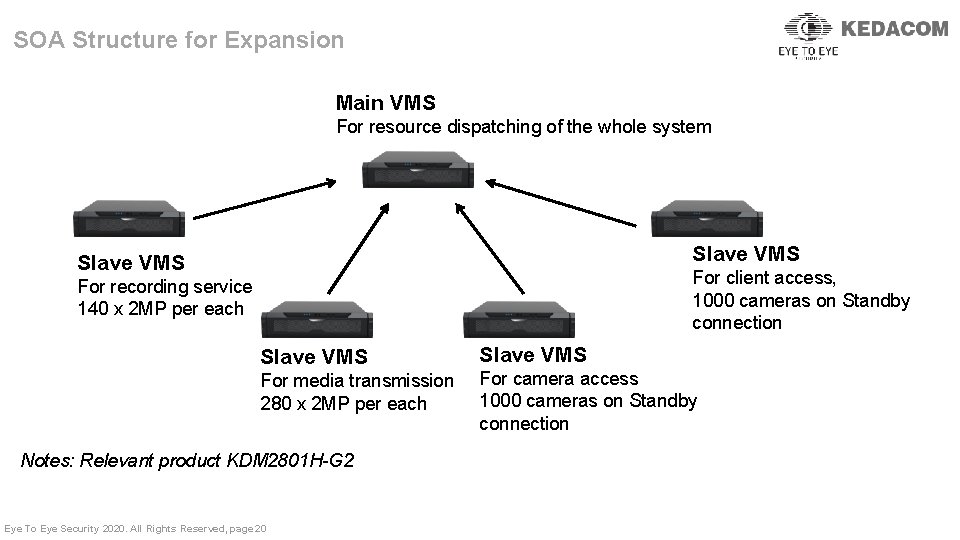
SOA Structure for Expansion 科达平台Phoenix版本采用SOA架构,采用分层的模块化设计,使各模块分 更加明确,功能更易扩 展,所有模块都支持分布式部署,更能够灵活适应不同的市场需求。PUI/CUI模块可以在从平台上分 Main VMS 布式部署,单级平台接入前端监控点数亦可根据需要进行扩容,极大提升平台接入能力。 For resource dispatching of the whole system Slave VMS 从平台 Slave VMS 专门负责录像服务 For recording service 140 x 2 MP per从平台 each 专门负责媒体转发 For client access, 1000 cameras on Standby 从平台 connection 专门接入监控前端 Slave VMS For media transmission 280 x 2 MP per each Notes: Relevant product KDM 2801 H-G 2 Eye To Eye Security 2020. All Rights Reserved, page 20 Slave VMS For camera access 1000 cameras on Standby connection

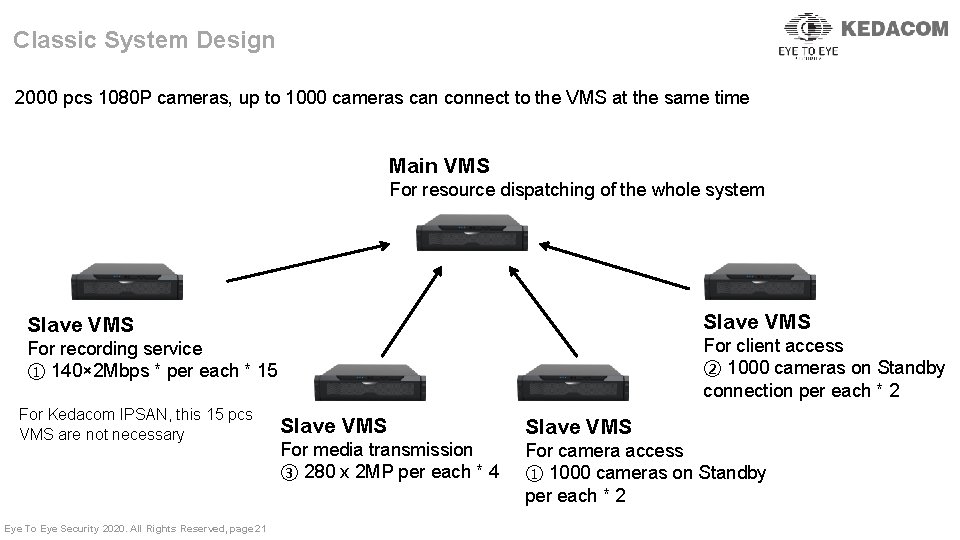
Classic System Design 2000 pcs 1080 P cameras, up to 1000 cameras can connect to the VMS at the same time更能够灵 活适应不同的市场需求。PUI/CUI模块可以在从平台上分布式部署,单级平台接入前端监控点数亦可 根据需要进行扩容,极大提升平台接入能力。 Main VMS For resource dispatching of the whole system Slave VMS For client access ② 1000 cameras on Standby connection per each * 2 For recording service ① 140× 2 Mbps * per each * 15 For Kedacom IPSAN, this 15 pcs VMS are not necessary Eye To Eye Security 2020. All Rights Reserved, page 21 Slave VMS For media transmission ③ 280 x 2 MP per each * 4 For camera access ① 1000 cameras on Standby per each * 2

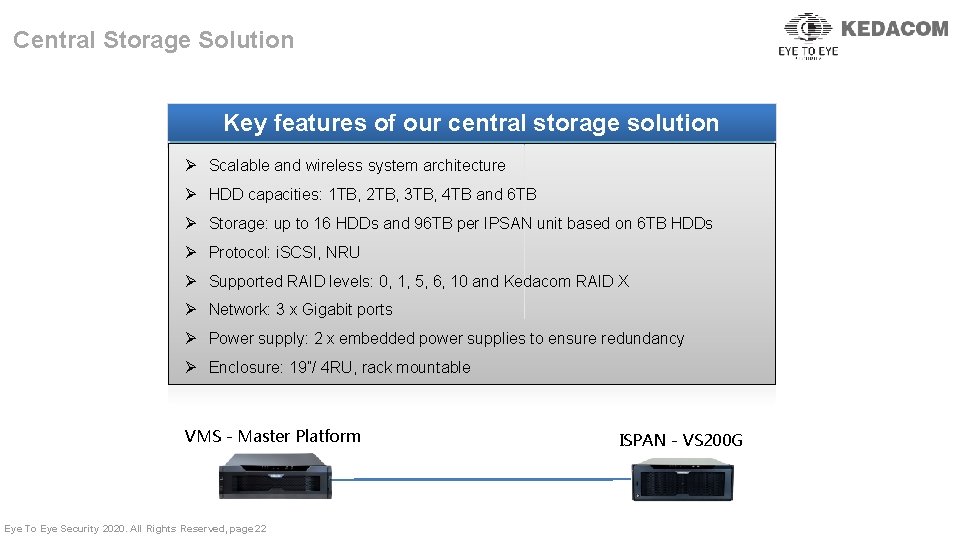
Central Storage Solution Key features of our central storage solution Ø Scalable and wireless system architecture Ø HDD capacities: 1 TB, 2 TB, 3 TB, 4 TB and 6 TB Ø Storage: up to 16 HDDs and 96 TB per IPSAN unit based on 6 TB HDDs Ø Protocol: i. SCSI, NRU Ø Supported RAID levels: 0, 1, 5, 6, 10 and Kedacom RAID X Ø Network: 3 x Gigabit ports Ø Power supply: 2 x embedded power supplies to ensure redundancy Ø Enclosure: 19”/ 4 RU, rack mountable VMS - Master Platform Eye To Eye Security 2020. All Rights Reserved, page 22 ISPAN - VS 200 G

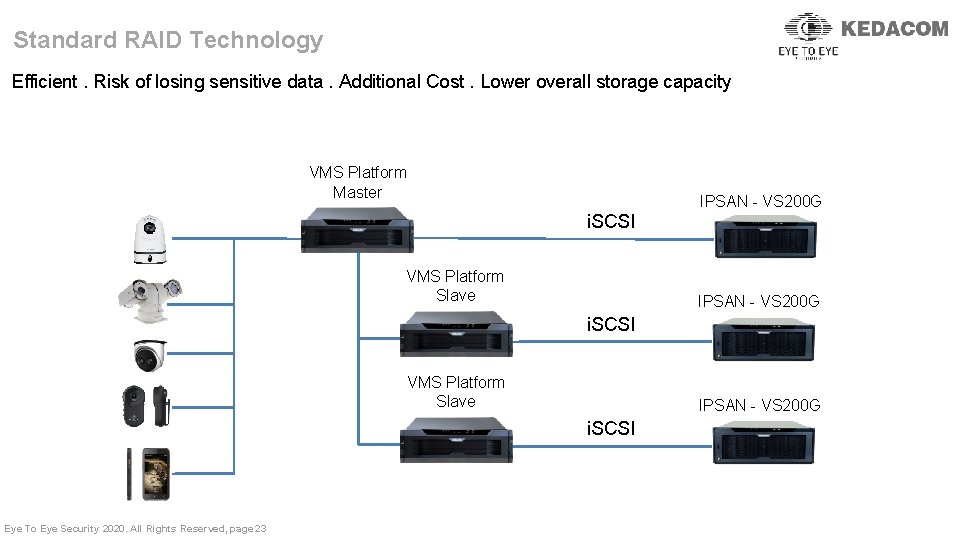
Standard RAID Technology Efficient. Risk of losing sensitive data. Additional Cost. Lower overall storage capacity VMS Platform Master IPSAN - VS 200 G i. SCSI VMS Platform Slave IPSAN - VS 200 G i. SCSI Eye To Eye Security 2020. All Rights Reserved, page 23

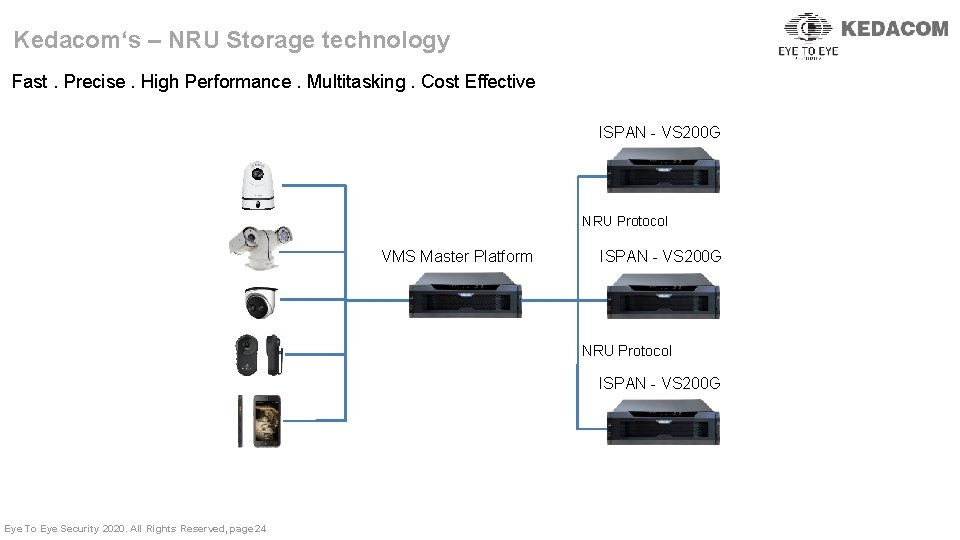
Kedacom‘s – NRU Storage technology Fast. Precise. High Performance. Multitasking. Cost Effective ISPAN - VS 200 G NRU Protocol VMS Master Platform ISPAN - VS 200 G NRU Protocol ISPAN - VS 200 G Eye To Eye Security 2020. All Rights Reserved, page 24

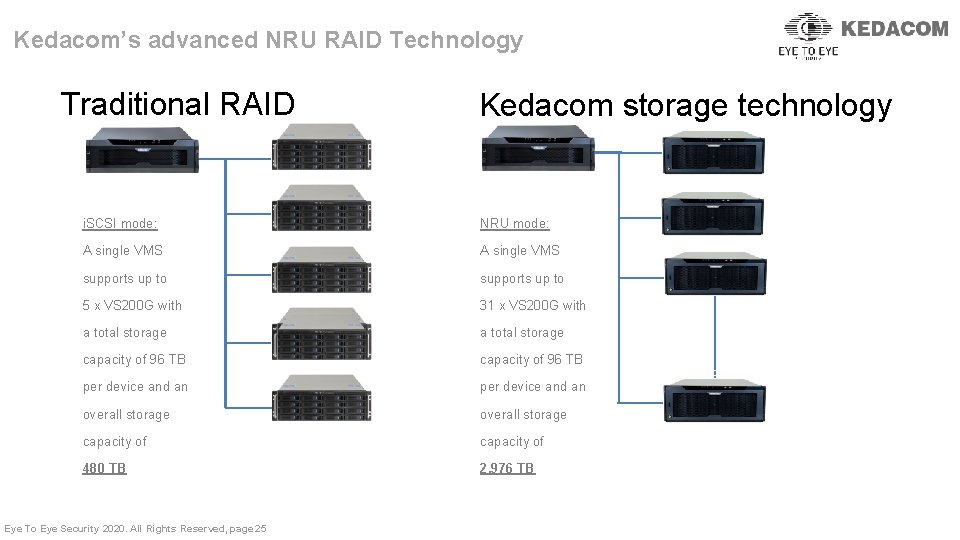
Kedacom’s advanced NRU RAID Technology Traditional RAID Kedacom storage technology i. SCSI mode: NRU mode: A single VMS supports up to 5 x VS 200 G with 31 x VS 200 G with a total storage capacity of 96 TB per device and an overall storage capacity of 480 TB 2, 976 TB Eye To Eye Security 2020. All Rights Reserved, page 25

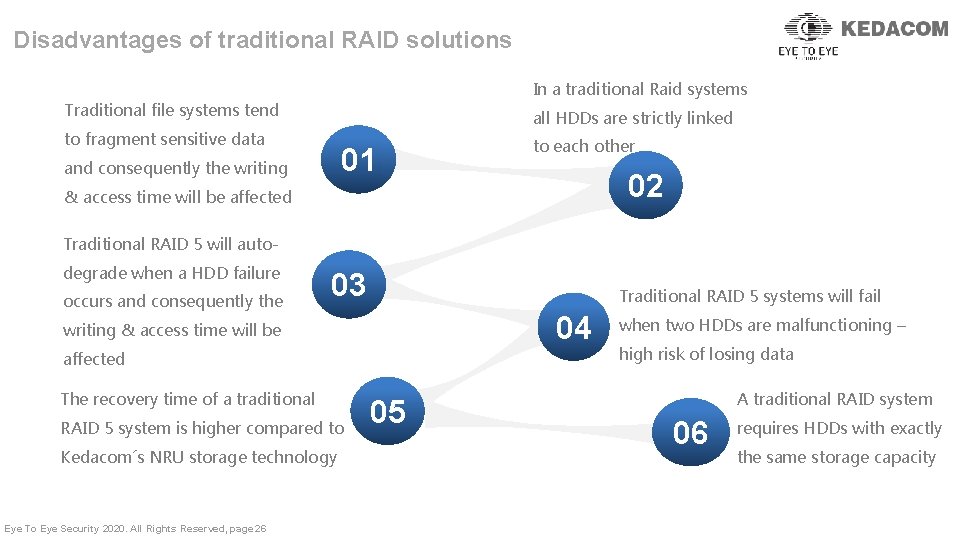
Disadvantages of traditional RAID solutions In a traditional Raid systems Traditional file systems tend all HDDs are strictly linked to fragment sensitive data 01 01 and consequently the writing to each other 02 02 & access time will be affected Traditional RAID 5 will autodegrade when a HDD failure occurs and consequently the 03 Traditional RAID 5 systems will fail 04 writing & access time will be affected The recovery time of a traditional RAID 5 system is higher compared to Kedacom´s NRU storage technology Eye To Eye Security 2020. All Rights Reserved, page 26 05 05 when two HDDs are malfunctioning – high risk of losing data A traditional RAID system 06 requires HDDs with exactly the same storage capacity

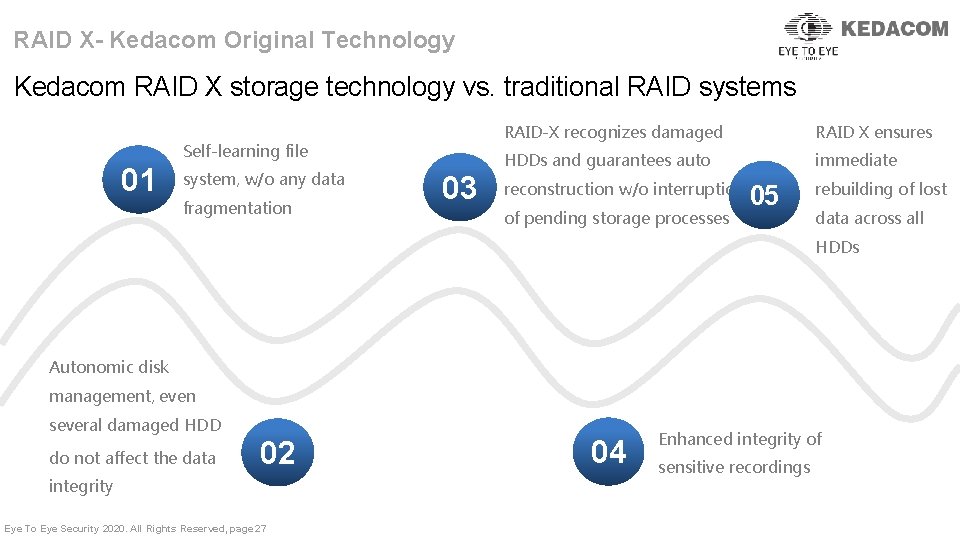
RAID X- Kedacom Original Technology Kedacom RAID X storage technology vs. traditional RAID systems Self-learning file 01 system, w/o any data fragmentation 03 RAID-X recognizes damaged RAID X ensures HDDs and guarantees auto immediate reconstruction w/o interruption of pending storage processes 05 rebuilding of lost data across all HDDs Autonomic disk management, even several damaged HDD do not affect the data 02 integrity Eye To Eye Security 2020. All Rights Reserved, page 27 04 Enhanced integrity of sensitive recordings

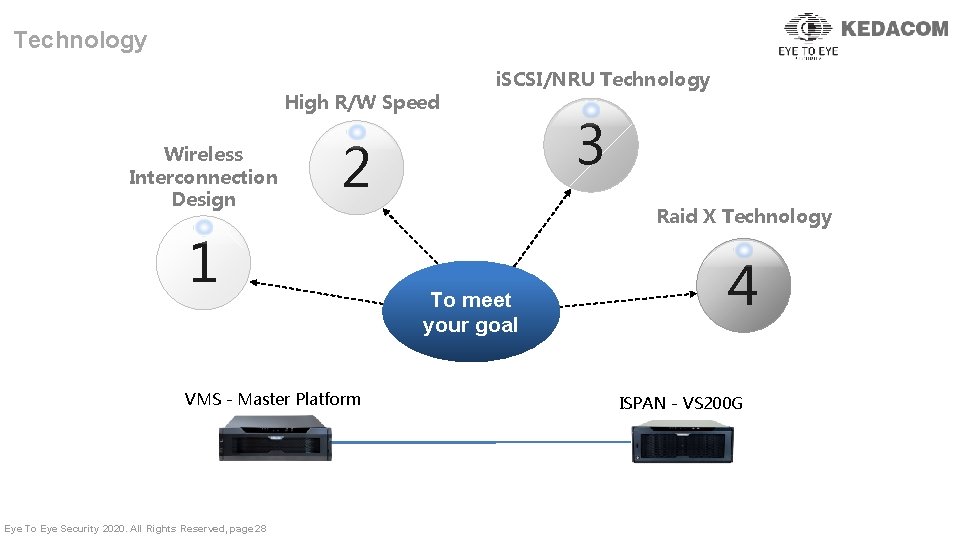
Technology High R/W Speed Wireless Interconnection Design 2 1 VMS - Master Platform Eye To Eye Security 2020. All Rights Reserved, page 28 i. SCSI/NRU Technology 3 Raid X Technology To meet your goal 4 ISPAN - VS 200 G

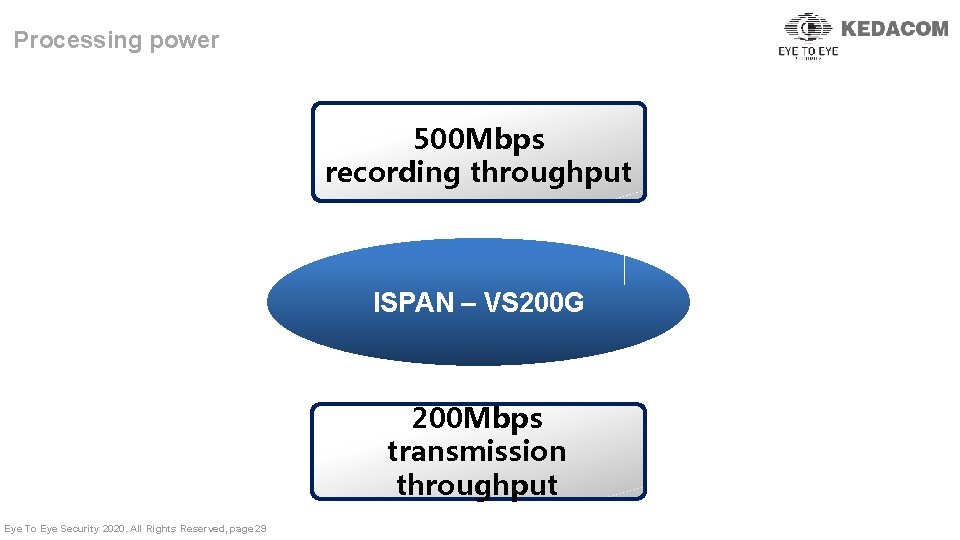
Processing power 500 Mbps recording throughput ISPAN – VS 200 G 200 Mbps transmission throughput Eye To Eye Security 2020. All Rights Reserved, page 29

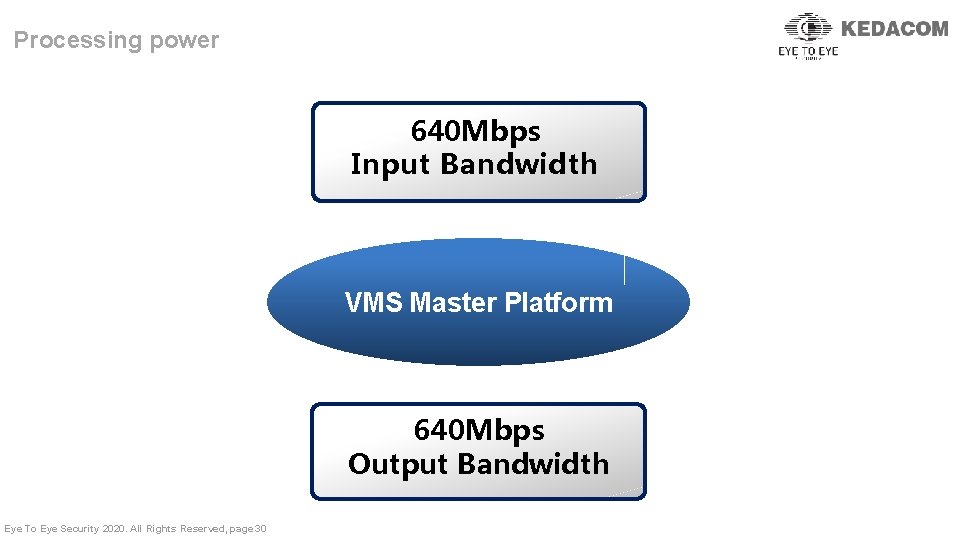
Processing power 640 Mbps Input Bandwidth VMS Master Platform 640 Mbps Output Bandwidth Eye To Eye Security 2020. All Rights Reserved, page 30

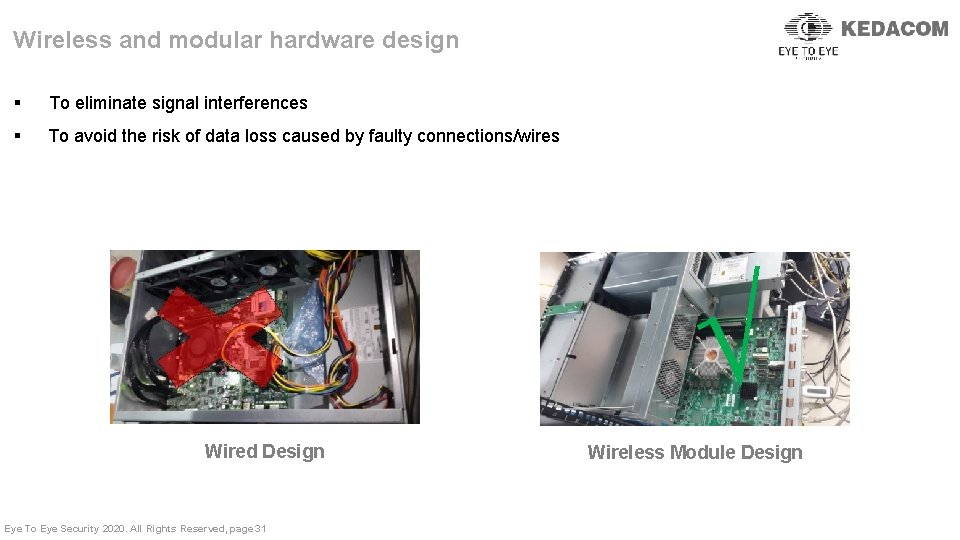
Wireless and modular hardware design § To eliminate signal interferences § To avoid the risk of data loss caused by faulty connections/wires √ Wired Design Eye To Eye Security 2020. All Rights Reserved, page 31 Wireless Module Design

Contents System Structure Product Overview Main Features Case Study References Eye To Eye Security 2020. All Rights Reserved, page 32

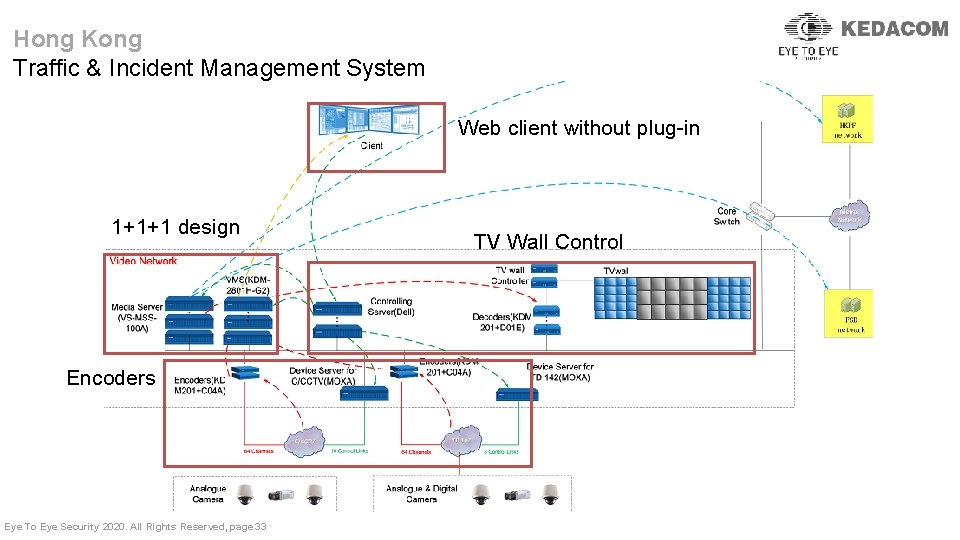
Hong Kong Traffic & Incident Management System Web client without plug-in 1+1+1 design Encoders Eye To Eye Security 2020. All Rights Reserved, page 33 TV Wall Control

Deep learning artificial intelligence Precise facial-, number plate-, behavior- recognition based on deep self learning algorithms Considering facts, changes and conditions fully embedded into our edge devices combined with instant central computing analysis Proved analytic Accuracy is 99% plus Exclusively Offered by KEDACOM & Eye To Eye Security

Contents System Structure Product Overview Main Features Case Study References Eye To Eye Security 2020. All Rights Reserved, page 35

References We know that references are important to prove the competence and overall performance of your suppliers. Eye To Eye Security trust that you understand that we have to respect the decision of our clients not to share any sensitive project related information without permission. Upon request we will provide exemplary block diagrams, application specific guidelines, individual competitive analysis and tailor-made handover plans to ensure that our clients are satisfied with the final implementation. This approach is in our core being combined with Trust. Respect. Loyalty Eye To Eye Security 2020. All Rights Reserved, page 36 Our Expertise's

Dear Partners, Eye To Eye Security Trading DWC-LLC, established in January 2017 with a Security background of more than 38 years provides a tailor-made product portfolio to suite a wide range of Mobile Surveillance Applications. Before we do anything, we start with our clients in mind and this enables us to develop solutions which create tangible benefits and deliver excellent Return on Investment. We are intrinsically R&D and Service oriented in spirit and for this reason we invest a large part of our annual revenue to develop more innovative products and mobile solutions. We take to heart the adage that excellence is a journey and cordially invite you to join us through a progressive future. Warmest welcome, Your trusted Eye To Eye Security team for Versatile Moving Surveillance, Bodyworn Walking Surveillance, Border Control and Central Monitoring Eye To Eye Security 2020. All Rights Reserved, page 37