CEN 4021 Software Engineering II Software Project Planning
























- Slides: 33

CEN 4021 Software Engineering II Software Project Planning (POMA) Risk Analysis and Planning Instructor: Masoud Sadjadi http: //www. cs. fiu. edu/~sadjadi/ sadjadi@cs. fiu. edu CEN 4021 8 th Lecture

Acknowledgements Dr. Onyeka Ezenwoye Dr. Peter Clarke CEN 4021: Software Engineering II 9 th Lecture 2

Agenda Software Project Planning (POMA) – Risk Analysis and Planning CEN 4021: Software Engineering II 9 th Lecture

Risk Analysis and Planning What is “risk”? Definition: Risk – A problem that has a greater than 0% but less than 100% probability of occurrence. A problem is an event that has a negative value associated with it. If the probability a risk has a 100% of occurring it is a problem. Examples of risk include: losing a critical resource or using an unreliable new technology in a software project. CEN 4021: Software Engineering II 9 th Lecture

Risk Analysis and Planning Risk can be listed, categorized, and potentially managed. The earlier risk are handled, the better the chance of project success. CEN 4021: Software Engineering II 9 th Lecture

Sources of Risk Overly optimistic assumptions about the availability of some technology Misunderstanding of the real impact of some new methodology Miscalculation of the robustness (e. g. , extensibility) or constraints of software design Misunderstanding of customer requirements Uncontrolled continuous changes of customer requirements Unrealistic promises to customers made by overzealous sales people or company execs. CEN 4021: Software Engineering II 9 th Lecture

Sources of Risk Inadequate due diligence while choosing external sourcing Incompetence of key personnel Miscalculation of teamwork and group effectiveness Unrealistic expectations about the availability or productivity of special skilled human resources. CEN 4021: Software Engineering II 9 th Lecture

Risk Identification Steps in starting the risk list: 1. List those characteristics of the product that may not be well defined. 2. List all unresolved issues for the tasks that will be performed in conjunction with the software project. Start by asking whether any process is defined, documented, and practiced in the organization. CEN 4021: Software Engineering II 9 th Lecture

Risk Identification Steps in starting the risk list: 3. Identify risks associated with management of resources. For example, hardware and software systems required for the project, licenses needed etc. Tools may not be available when needed. Human resources represent a especially important type of resource for software projects. Obtaining the needed skilled people in a timely manner is always a problem. CEN 4021: Software Engineering II 9 th Lecture

Risk Identification Planning categories to identify risk: Deliverables and product specification Tasks and initial schedule Goals, metrics, and measurements Human resources Processes and methodologies Tools and equipment CEN 4021: Software Engineering II 9 th Lecture

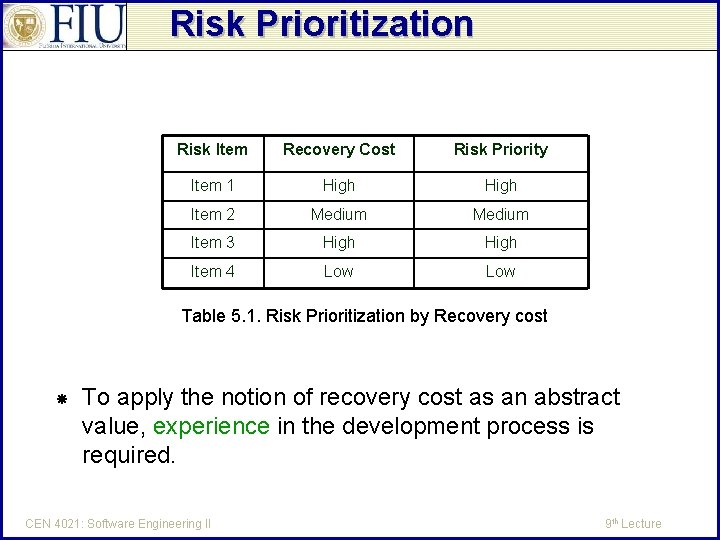
Risk Prioritization Definition: Risk prioritization - The activity of ordering risks based on some criterion or set of criteria. Recovery cost – The cost in terms of effort or financial expense to solve a problem should a risk materialize. The cost identified may not be exact but rather identified as merely high, medium, and low. The associated risk would have similar values. CEN 4021: Software Engineering II 9 th Lecture

Risk Prioritization Risk Item Recovery Cost Risk Priority Item 1 High Item 2 Medium Item 3 High Item 4 Low Table 5. 1. Risk Prioritization by Recovery cost To apply the notion of recovery cost as an abstract value, experience in the development process is required. CEN 4021: Software Engineering II 9 th Lecture

Risk Prioritization by Risk Value: The prioritization of risk can be more complex. It makes sense to view risks with a low chance of occurring as requiring less attention. We can define the risk value (RV) as follows: RV(j) = P(j) X RC(j) P(j) – the probability of risk item j becoming a real problem RC(j) – is the recovery cost for the risk item j when it turns into a real problem. CEN 4021: Software Engineering II 9 th Lecture

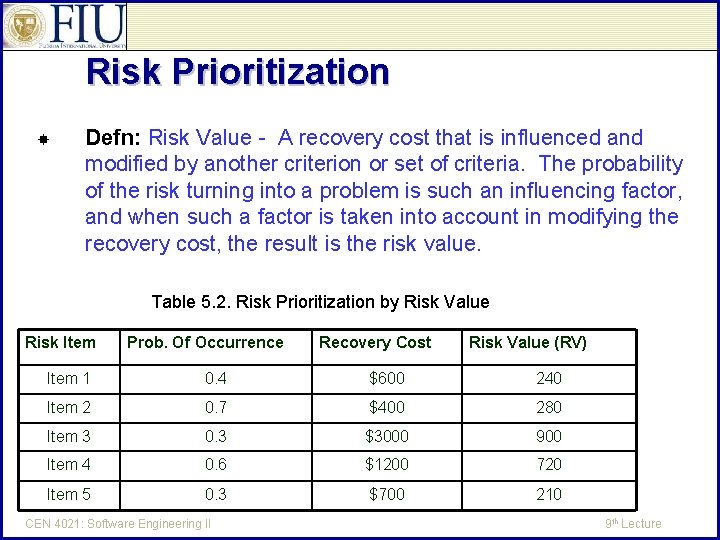
Risk Prioritization Defn: Risk Value - A recovery cost that is influenced and modified by another criterion or set of criteria. The probability of the risk turning into a problem is such an influencing factor, and when such a factor is taken into account in modifying the recovery cost, the result is the risk value. Table 5. 2. Risk Prioritization by Risk Value Risk Item Prob. Of Occurrence Recovery Cost Risk Value (RV) Item 1 0. 4 $600 240 Item 2 0. 7 $400 280 Item 3 0. 3 $3000 900 Item 4 0. 6 $1200 720 Item 5 0. 3 $700 210 CEN 4021: Software Engineering II 9 th Lecture

Risk Management Is the formal process in which risk factors are systematically identified, assessed and mitigated. Is about understanding the internal and external influences that can cause failure – Internal risk – within the control of project manager – External risk – outside the control the manager CEN 4021: Software Engineering II 9 th Lecture

Risk Management A subset of project management that includes the processes concerned with identifying, analyzing, and responding to project risk The result of the initial risk analysis is a risk plan that should be reviewed regularly and adjusted accordingly The purpose is to uncommon causes of project variation CEN 4021: Software Engineering II 9 th Lecture

Risk Management A good project manager is a good risk manager Risk management continues throughout the software process until the product is delivered Risk analysis and mitigation continue through the implementation stages of the software process. CEN 4021: Software Engineering II 9 th Lecture

Risk Management Risks are analyzed and prioritized on a weekly basis and the current “top-ten” risk list is presented at each weekly project status meeting. Mitigation occurs through working the risks with the project team. CEN 4021: Software Engineering II 9 th Lecture

Risk Management Negative impact of risk can include – – Diminished quality of product Increased cost Delayed completion Project failure CEN 4021: Software Engineering II 9 th Lecture

Risk Management Handling risk is a key skill for software project managers because so much can go wrong Software projects are thought to be more complex because the product is intangible The determined risk profile will affect any scheduling estimates CEN 4021: Software Engineering II 9 th Lecture

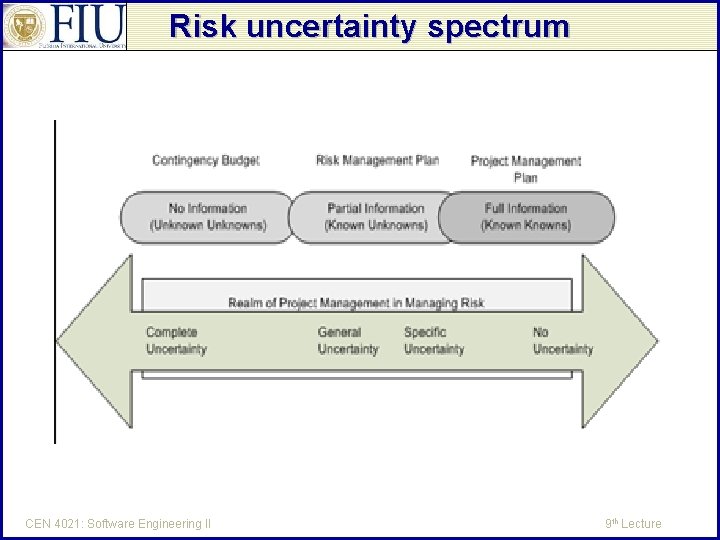
Risk Management Project manager deal with 3 general categories of risks – Known knowns: know to the project team, e. g. , not having a funding source. Risk is noted and in project plan. – Known unknowns: know to the project team but not know as a reality to the project. E. g. , not having access to the enduser may lead to incorrect requirements. These are described in the plan, prioritized and updated on a weekly basis CEN 4021: Software Engineering II 9 th Lecture

Risk Management Project manager deal with 3 general categories of risks (continued) – unknowns: these are unknown to the project team as both a category of risk and as a reality to this project. E. g. , when a specific technology is used because it is dictated by the terms of the contract. These can be addressed by setting a budget for contingencies. Also consider risk transfer, a. k. a insurance CEN 4021: Software Engineering II 9 th Lecture

Risk uncertainty spectrum CEN 4021: Software Engineering II 9 th Lecture

Risk Management Part of risk management is about risk quantification Concepts of risk quantification: – Risk Event (item): precise description of what might happen to the project – Risk probability: the degree to which the risk event is likely to occur – Amount at stake (recovery cost): the loss if the outcome is unsatisfactory – Risk exposure (risk value): the overall liability (quantified) potential of the risk CEN 4021: Software Engineering II 9 th Lecture

Risk Management Model Risk management is made up of: – Risk identification Identify potential risk event (thru checklists, problem decomposition, experience, etc) – Risk quantification Qualitative analysis: non-measurable data e. g. , morale Quantitative analysis – Response planning Identify resource reserves, and how mitigation can occur – Monitoring and control Correction action plans and monitoring their implementation CEN 4021: Software Engineering II 9 th Lecture

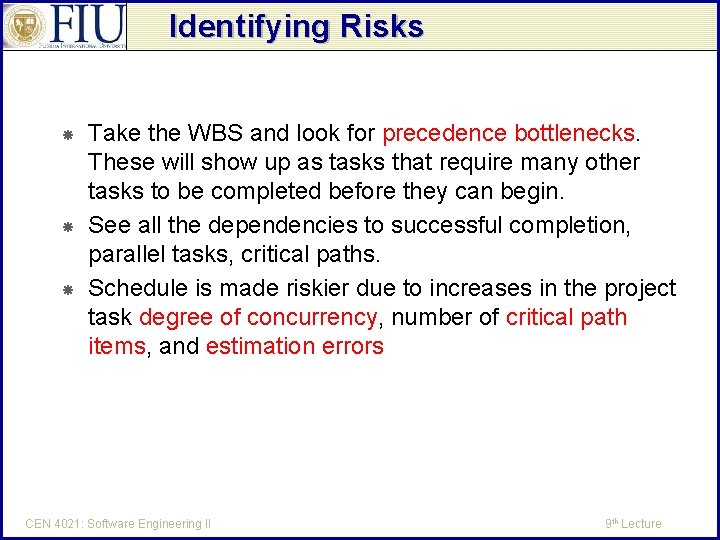
Identifying Risks Take the WBS and look for precedence bottlenecks. These will show up as tasks that require many other tasks to be completed before they can begin. See all the dependencies to successful completion, parallel tasks, critical paths. Schedule is made riskier due to increases in the project task degree of concurrency, number of critical path items, and estimation errors CEN 4021: Software Engineering II 9 th Lecture

Risk Mitigation Defn: Risk mitigation – An activity that may reduce minimize, or totally avoid a risk. Risk item: not being able to complete a system integration task with a specific tool because only one person posses that special skill. Alt. 1 – Hire an extra person with the needed skill as a backup helper Alt. 2 – Provide extra incentives to persuade the current employer to stay Alt. 3 – Use an alternative system integration method that does not require this specific tool CEN 4021: Software Engineering II 9 th Lecture

Cost-base mitigation Which mitigation alternative should be chosen when several choices are available? Which criteria should be used in decision making? One of any several parameters as the basis for decision making including the ease of mitigation, probability of success of mitigation, and the cost of mitigation. CEN 4021: Software Engineering II 9 th Lecture

Cost of mitigation Mitigation alternative Cost of mitigation Alternative 1 $65, 000 Alternative 2 $50, 000 Alternative 3 $120, 000 Table 5. 3: Estimated Mitigation Costs for Risk Item J CEN 4021: Software Engineering II 9 th Lecture

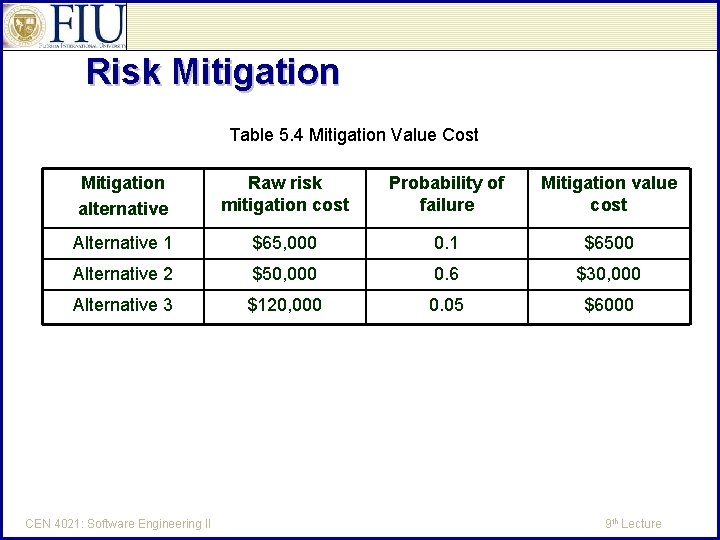
Mitigation Value Cost The mitigation cost value is defined as follows: MVC(k) = P(k) X MC(k) MVC(K) – mitigation cost value of alternative k P(k) – probability of failure for alternative k MC(k) – raw cost of mitigation for alternative k See Table 5. 4 in the next slide. Mitigation value cost – the cost of risk mitigation after taking into account another criterion or a set of criteria, such as probability of mitigation success CEN 4021: Software Engineering II 9 th Lecture

Risk Mitigation Table 5. 4 Mitigation Value Cost Mitigation alternative Raw risk mitigation cost Probability of failure Mitigation value cost Alternative 1 $65, 000 0. 1 $6500 Alternative 2 $50, 000 0. 6 $30, 000 Alternative 3 $120, 000 0. 05 $6000 CEN 4021: Software Engineering II 9 th Lecture

Risk Mitigation Value Cost Note that if P(k) is changed from the probability of failure to the probability of success, then the highest mitigation value cost would be the proper choice. Sometimes the project manager faces the prospect of planning with a fixed budget for risk mitigation. Therefore the risk items must be ranked. See Table 5. 5 in textbook. CEN 4021: Software Engineering II 9 th Lecture

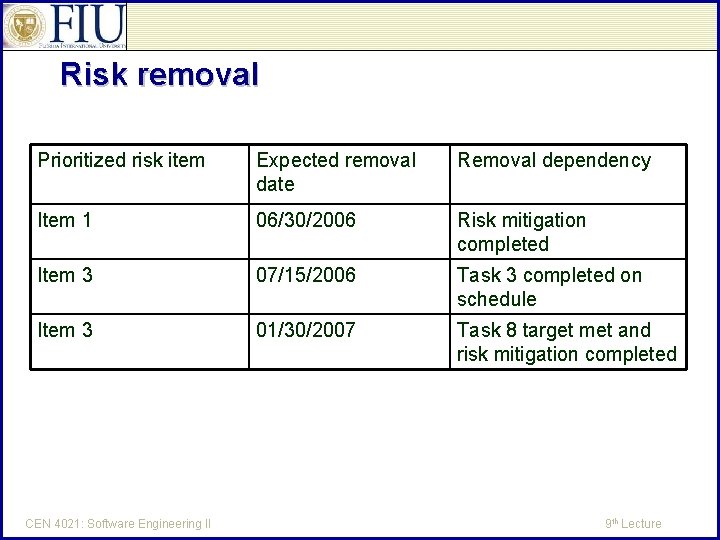
Risk removal Prioritized risk item Expected removal date Removal dependency Item 1 06/30/2006 Risk mitigation completed Item 3 07/15/2006 Task 3 completed on schedule Item 3 01/30/2007 Task 8 target met and risk mitigation completed CEN 4021: Software Engineering II 9 th Lecture