CCNA Security Chapter Six Securing the Local Area


![CLI Commands Switch(config)# monitor session_number source {interface-id [, | -] [both | rx | CLI Commands Switch(config)# monitor session_number source {interface-id [, | -] [both | rx |](https://slidetodoc.com/presentation_image_h2/354a51e429ea66c77396558c4e965104/image-38.jpg)


- Slides: 45

CCNA Security Chapter Six Securing the Local Area Network © 2009 Cisco Learning Institute. 1

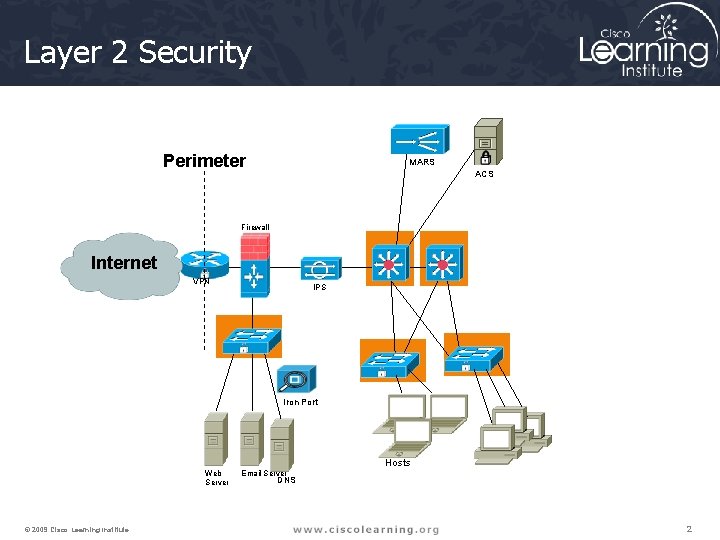
Layer 2 Security Perimeter MARS ACS Firewall Internet VPN IPS Iron Port Hosts Web Server © 2009 Cisco Learning Institute. Email Server DNS 2

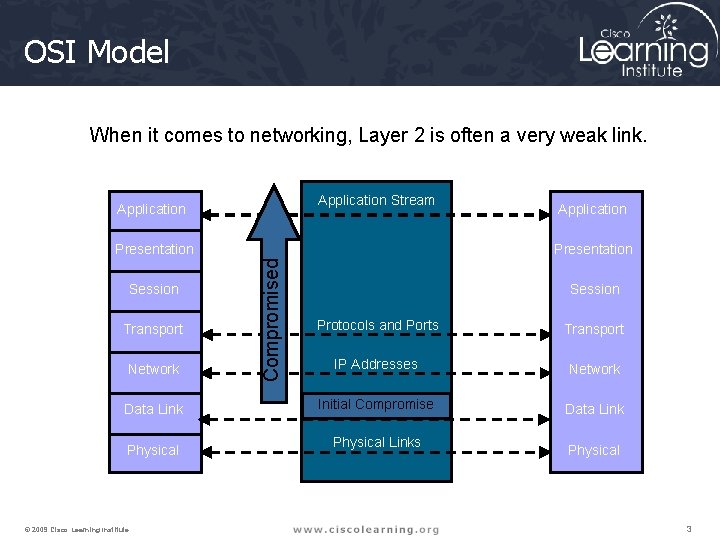
OSI Model When it comes to networking, Layer 2 is often a very weak link. Application Stream Application Presentation Transport Network Data Link Physical © 2009 Cisco Learning Institute. Compromised Presentation Session Application Session Protocols and Ports Transport IP Addresses Network Initial MACCompromise Addresses Data Link Physical Links Physical 3

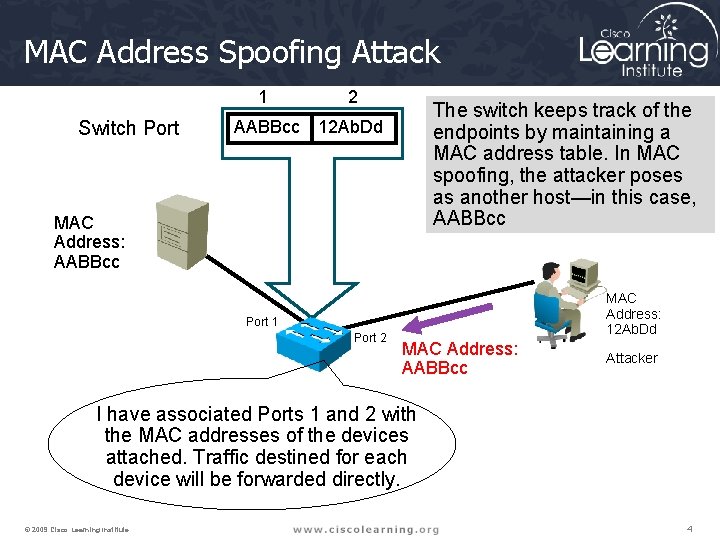
MAC Address Spoofing Attack Switch Port 1 2 AABBcc 12 Ab. Dd The switch keeps track of the endpoints by maintaining a MAC address table. In MAC spoofing, the attacker poses as another host—in this case, AABBcc MAC Address: 12 Ab. Dd Port 1 Port 2 MAC Address: AABBcc Attacker I have associated Ports 1 and 2 with the MAC addresses of the devices attached. Traffic destined for each device will be forwarded directly. © 2009 Cisco Learning Institute. 4

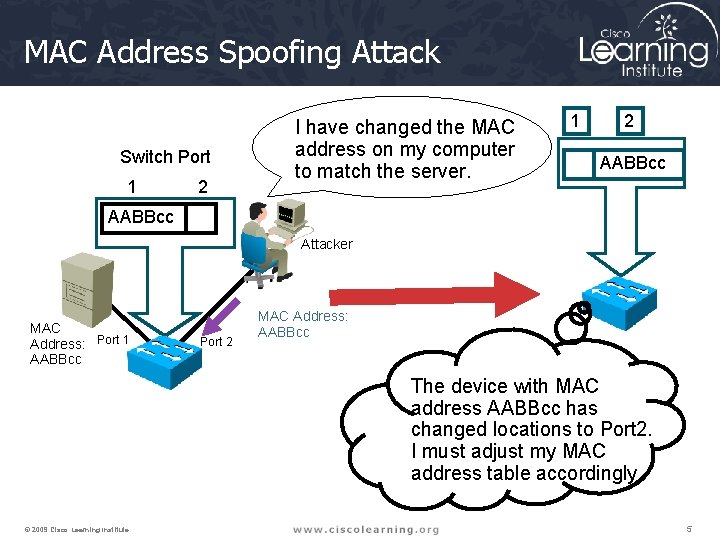
MAC Address Spoofing Attack Switch Port 1 2 I have changed the MAC address on my computer to match the server. 1 2 AABBcc Attacker MAC Address: Port 1 AABBcc Port 2 MAC Address: AABBcc The device with MAC address AABBcc has changed locations to Port 2. I must adjust my MAC address table accordingly. © 2009 Cisco Learning Institute. 5

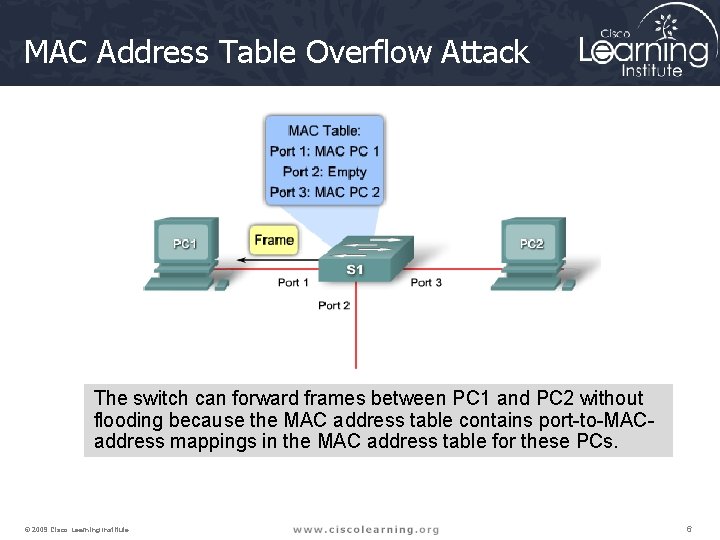
MAC Address Table Overflow Attack The switch can forward frames between PC 1 and PC 2 without flooding because the MAC address table contains port-to-MACaddress mappings in the MAC address table for these PCs. © 2009 Cisco Learning Institute. 6

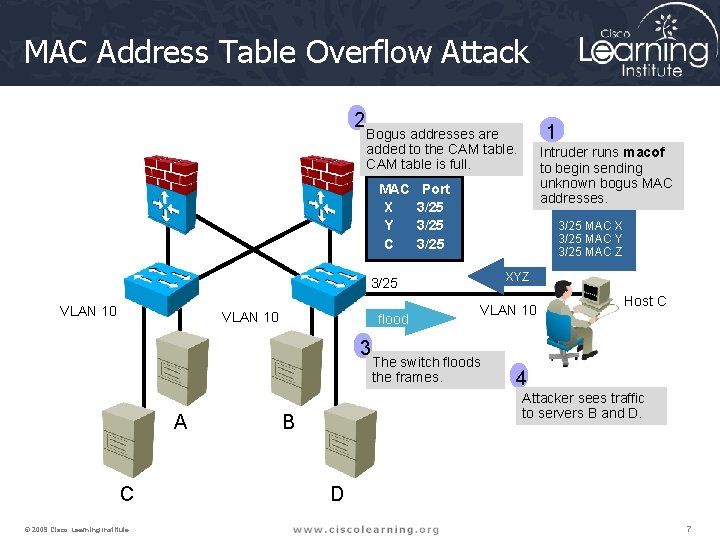
MAC Address Table Overflow Attack 2 MAC X Y C VLAN 10 flood 3 A C © 2009 Cisco Learning Institute. Intruder runs macof to begin sending unknown bogus MAC addresses. Port 3/25 MAC X 3/25 MAC Y 3/25 MAC Z XYZ 3/25 VLAN 10 1 Bogus addresses are added to the CAM table is full. VLAN 10 The switch floods the frames. Host C 4 Attacker sees traffic to servers B and D. B D 7

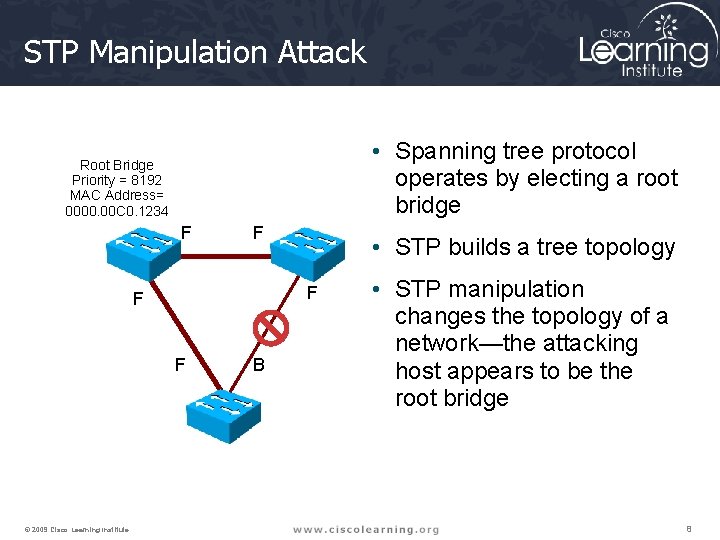
STP Manipulation Attack • Spanning tree protocol operates by electing a root bridge Root Bridge Priority = 8192 MAC Address= 0000. 00 C 0. 1234 F F F © 2009 Cisco Learning Institute. • STP builds a tree topology B • STP manipulation changes the topology of a network—the attacking host appears to be the root bridge 8

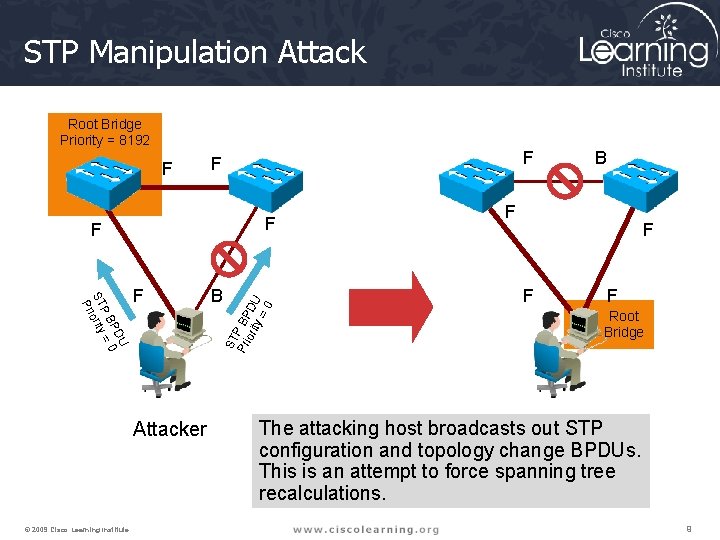
STP Manipulation Attack Root Bridge Priority = 8192 F F F B ST Pri P BP ori DU ty =0 U PD 0 PB = ST iority Pr F Attacker © 2009 Cisco Learning Institute. F F B F F Root Bridge The attacking host broadcasts out STP configuration and topology change BPDUs. This is an attempt to force spanning tree recalculations. 9

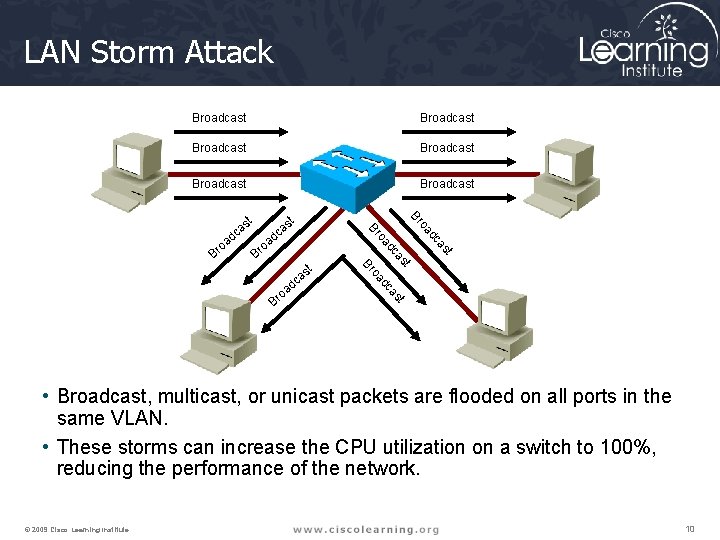
LAN Storm Attack Broadcast Broadcast oa Br t t st ca oa Br d oa Br t as c d as dc oa as Br dc oa Br t as c d st a dc • Broadcast, multicast, or unicast packets are flooded on all ports in the same VLAN. • These storms can increase the CPU utilization on a switch to 100%, reducing the performance of the network. © 2009 Cisco Learning Institute. 10

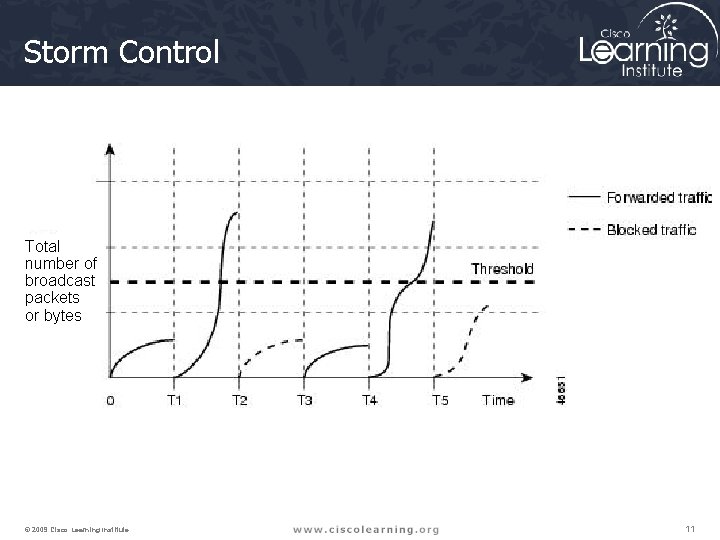
Storm Control Total number of broadcast packets or bytes © 2009 Cisco Learning Institute. 11

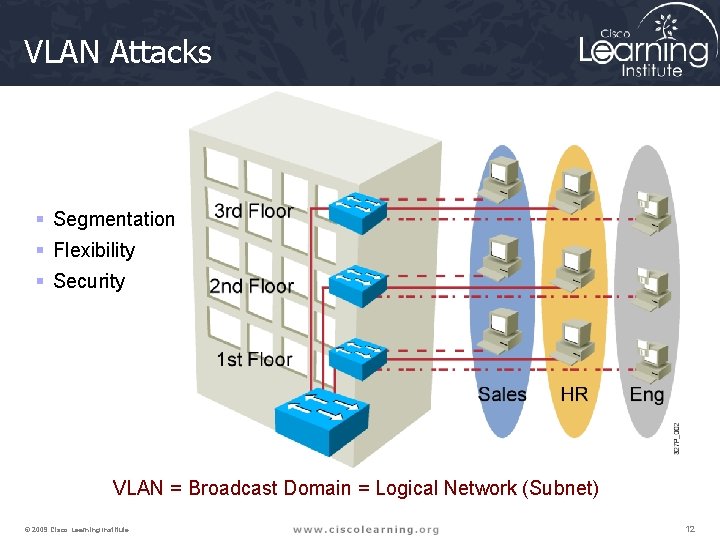
VLAN Attacks § Segmentation § Flexibility § Security VLAN = Broadcast Domain = Logical Network (Subnet) © 2009 Cisco Learning Institute. 12

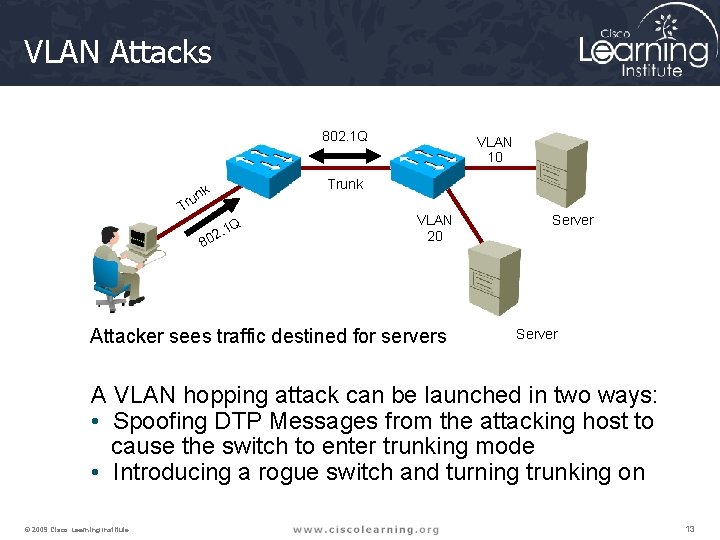
VLAN Attacks 802. 1 Q k run T 8 . 1 Q 2 0 VLAN 10 Trunk VLAN 20 Attacker sees traffic destined for servers Server A VLAN hopping attack can be launched in two ways: • Spoofing DTP Messages from the attacking host to cause the switch to enter trunking mode • Introducing a rogue switch and turning trunking on © 2009 Cisco Learning Institute. 13

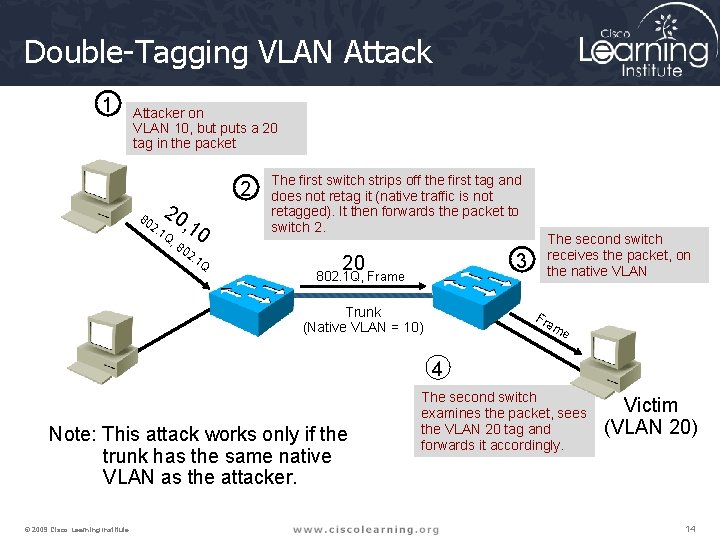
Double-Tagging VLAN Attack 1 Attacker on VLAN 10, but puts a 20 tag in the packet 80 2. 20 1 Q , 8 2 , 10 02 . 1 Q The first switch strips off the first tag and does not retag it (native traffic is not retagged). It then forwards the packet to switch 2. 3 20 802. 1 Q, Frame Trunk (Native VLAN = 10) The second switch receives the packet, on the native VLAN Fra me 4 Note: This attack works only if the trunk has the same native VLAN as the attacker. © 2009 Cisco Learning Institute. The second switch examines the packet, sees the VLAN 20 tag and forwards it accordingly. Victim (VLAN 20) 14

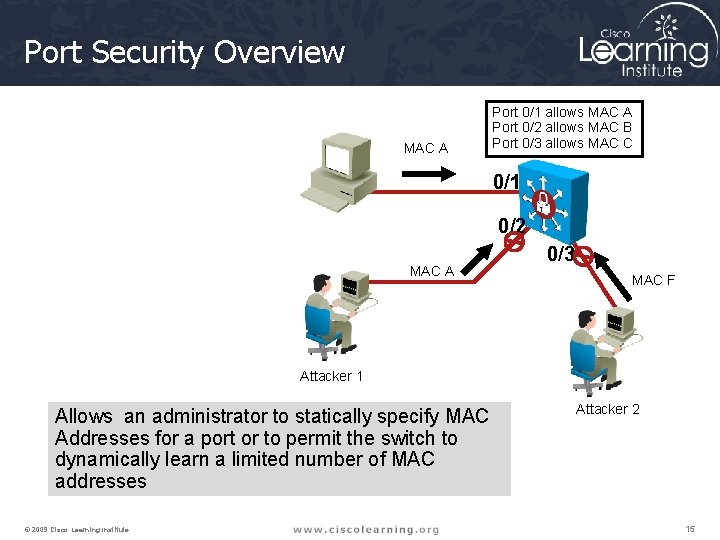
Port Security Overview MAC A Port 0/1 allows MAC A Port 0/2 allows MAC B Port 0/3 allows MAC C 0/1 0/2 MAC A 0/3 MAC F Attacker 1 Allows an administrator to statically specify MAC Addresses for a port or to permit the switch to dynamically learn a limited number of MAC addresses © 2009 Cisco Learning Institute. Attacker 2 15

CLI Commands Switch(config-if)# switchport mode access • Sets the interface mode as access Switch(config-if)# switchport-security • Enables port security on the interface Switch(config-if)# switchport-security maximum value • Sets the maximum number of secure MAC addresses for the interface (optional) © 2009 Cisco Learning Institute. 16

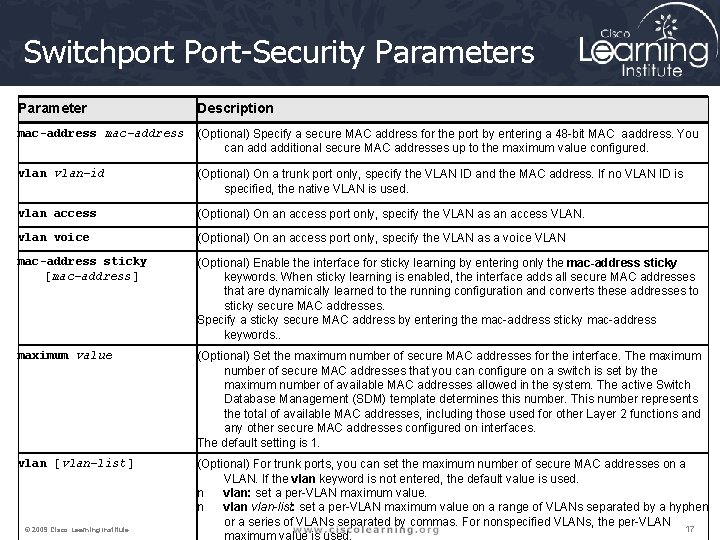
Switchport Port-Security Parameters Parameter Description mac-address (Optional) Specify a secure MAC address for the port by entering a 48 -bit MAC aaddress. You can additional secure MAC addresses up to the maximum value configured. vlan-id (Optional) On a trunk port only, specify the VLAN ID and the MAC address. If no VLAN ID is specified, the native VLAN is used. vlan access (Optional) On an access port only, specify the VLAN as an access VLAN. vlan voice (Optional) On an access port only, specify the VLAN as a voice VLAN mac-address sticky [mac-address] (Optional) Enable the interface for sticky learning by entering only the mac-address sticky keywords. When sticky learning is enabled, the interface adds all secure MAC addresses that are dynamically learned to the running configuration and converts these addresses to sticky secure MAC addresses. Specify a sticky secure MAC address by entering the mac-address sticky mac-address keywords. . maximum value (Optional) Set the maximum number of secure MAC addresses for the interface. The maximum number of secure MAC addresses that you can configure on a switch is set by the maximum number of available MAC addresses allowed in the system. The active Switch Database Management (SDM) template determines this number. This number represents the total of available MAC addresses, including those used for other Layer 2 functions and any other secure MAC addresses configured on interfaces. The default setting is 1. vlan [vlan-list] (Optional) For trunk ports, you can set the maximum number of secure MAC addresses on a VLAN. If the vlan keyword is not entered, the default value is used. n vlan: set a per-VLAN maximum value. n vlan-list: set a per-VLAN maximum value on a range of VLANs separated by a hyphen or a series of VLANs separated by commas. For nonspecified VLANs, the per-VLAN © 2009 Cisco Learning Institute. 17

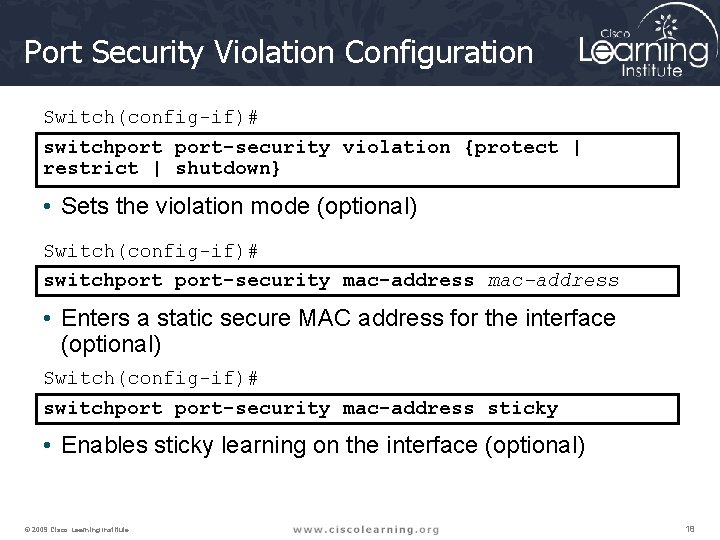
Port Security Violation Configuration Switch(config-if)# switchport-security violation {protect | restrict | shutdown} • Sets the violation mode (optional) Switch(config-if)# switchport-security mac-address • Enters a static secure MAC address for the interface (optional) Switch(config-if)# switchport-security mac-address sticky • Enables sticky learning on the interface (optional) © 2009 Cisco Learning Institute. 18

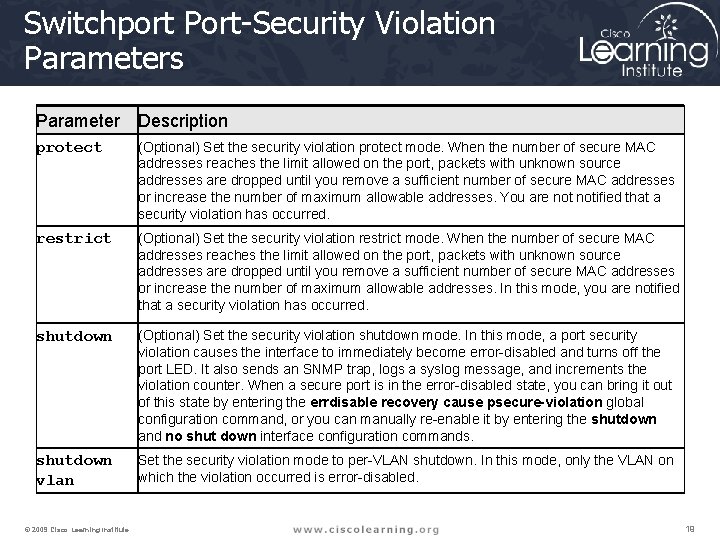
Switchport Port-Security Violation Parameters Parameter Description protect (Optional) Set the security violation protect mode. When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. You are notified that a security violation has occurred. restrict (Optional) Set the security violation restrict mode. When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. In this mode, you are notified that a security violation has occurred. shutdown (Optional) Set the security violation shutdown mode. In this mode, a port security violation causes the interface to immediately become error-disabled and turns off the port LED. It also sends an SNMP trap, logs a syslog message, and increments the violation counter. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command, or you can manually re-enable it by entering the shutdown and no shut down interface configuration commands. shutdown vlan Set the security violation mode to per-VLAN shutdown. In this mode, only the VLAN on which the violation occurred is error-disabled. © 2009 Cisco Learning Institute. 19

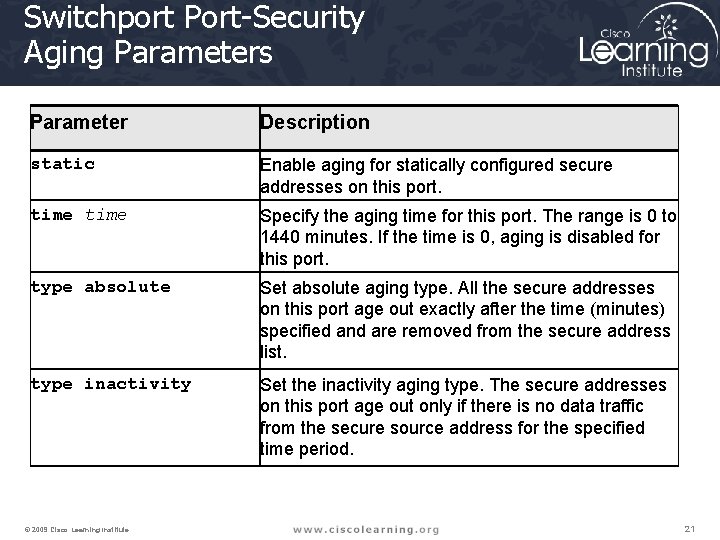
Port Security Aging Configuration Switch(config-if)# switchport-security aging {static | time | type {absolute | inactivity}} • Enables or disables static aging for the secure port or sets the aging time or type © 2009 Cisco Learning Institute. 20

Switchport Port-Security Aging Parameters Parameter Description static Enable aging for statically configured secure addresses on this port. time Specify the aging time for this port. The range is 0 to 1440 minutes. If the time is 0, aging is disabled for this port. type absolute Set absolute aging type. All the secure addresses on this port age out exactly after the time (minutes) specified and are removed from the secure address list. type inactivity Set the inactivity aging type. The secure addresses on this port age out only if there is no data traffic from the secure source address for the specified time period. © 2009 Cisco Learning Institute. 21

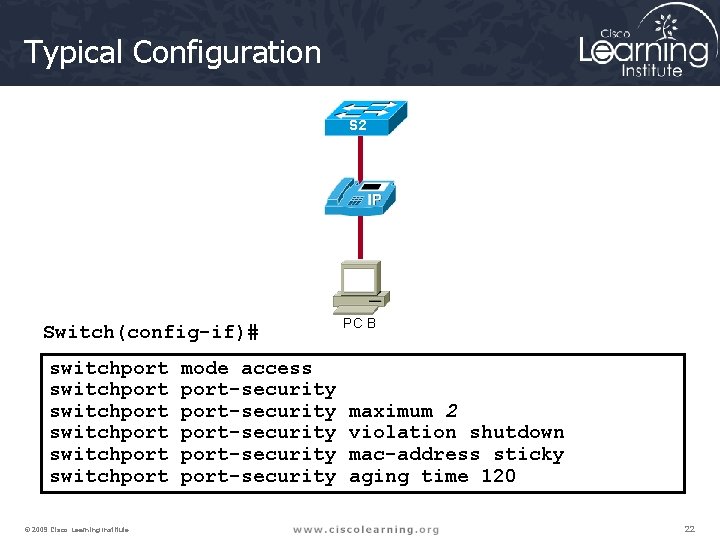
Typical Configuration S 2 Switch(config-if)# switchport switchport © 2009 Cisco Learning Institute. mode access port-security port-security PC B maximum 2 violation shutdown mac-address sticky aging time 120 22

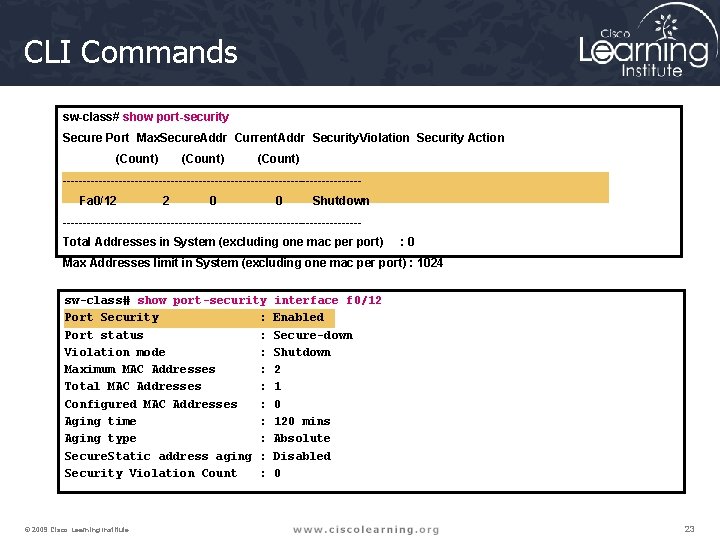
CLI Commands sw-class# show port-security Secure Port Max. Secure. Addr Current. Addr Security. Violation Security Action (Count) -------------------------------------Fa 0/12 2 0 0 Shutdown -------------------------------------Total Addresses in System (excluding one mac per port) : 0 Max Addresses limit in System (excluding one mac per port) : 1024 sw-class# show port-security Port Security : Port status : Violation mode : Maximum MAC Addresses : Total MAC Addresses : Configured MAC Addresses : Aging time : Aging type : Secure. Static address aging : Security Violation Count : © 2009 Cisco Learning Institute. interface f 0/12 Enabled Secure-down Shutdown 2 1 0 120 mins Absolute Disabled 0 23

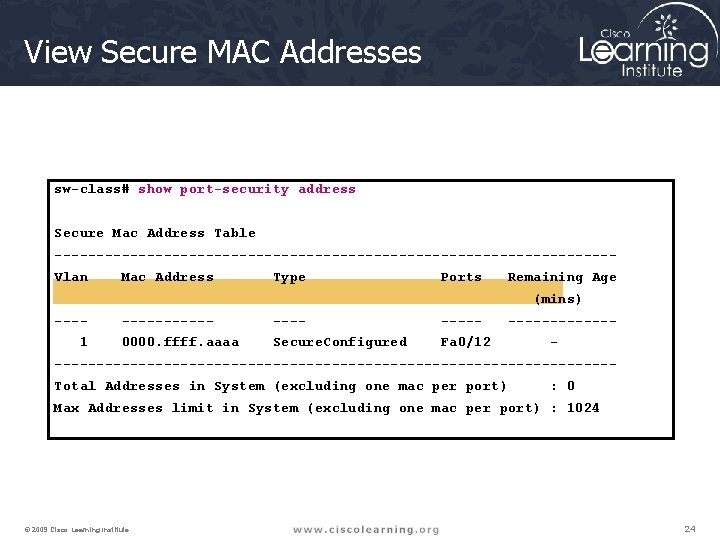
View Secure MAC Addresses sw-class# show port-security address Secure Mac Address Table ---------------------------------Vlan Mac Address Type Ports Remaining Age (mins) ---1 ------ 0000. ffff. aaaa Secure. Configured Fa 0/12 ----------------------------------------Total Addresses in System (excluding one mac per port) : 0 Max Addresses limit in System (excluding one mac per port) : 1024 © 2009 Cisco Learning Institute. 24

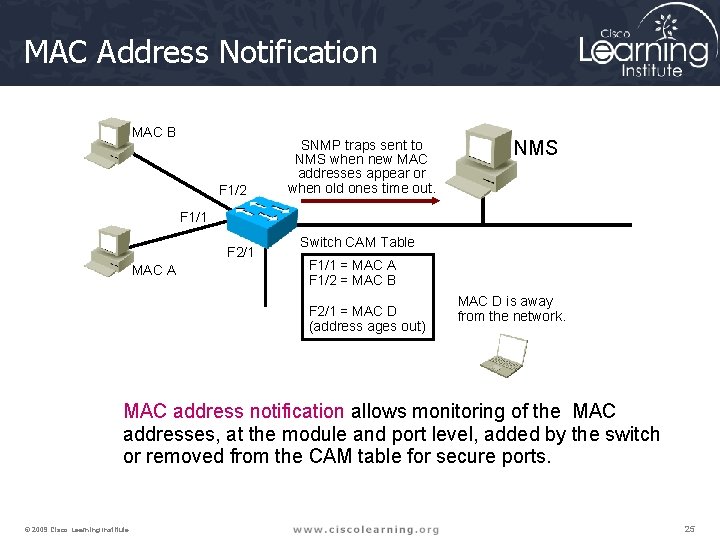
MAC Address Notification MAC B F 1/2 SNMP traps sent to NMS when new MAC addresses appear or when old ones time out. NMS F 1/1 F 2/1 MAC A Switch CAM Table F 1/1 = MAC A F 1/2 = MAC B F 2/1 = MAC D (address ages out) MAC D is away from the network. MAC address notification allows monitoring of the MAC addresses, at the module and port level, added by the switch or removed from the CAM table for secure ports. © 2009 Cisco Learning Institute. 25

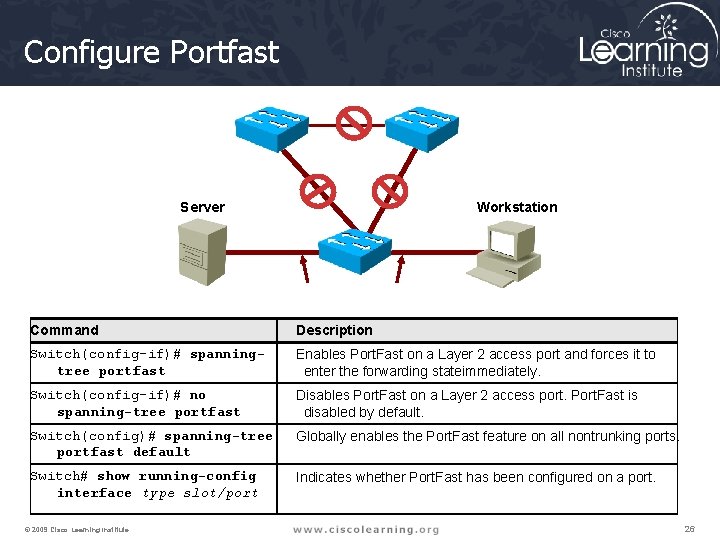
Configure Portfast Server Workstation Command Description Switch(config-if)# spanningtree portfast Enables Port. Fast on a Layer 2 access port and forces it to enter the forwarding stateimmediately. Switch(config-if)# no spanning-tree portfast Disables Port. Fast on a Layer 2 access port. Port. Fast is disabled by default. Switch(config)# spanning-tree portfast default Globally enables the Port. Fast feature on all nontrunking ports. Switch# show running-config interface type slot/port Indicates whether Port. Fast has been configured on a port. © 2009 Cisco Learning Institute. 26

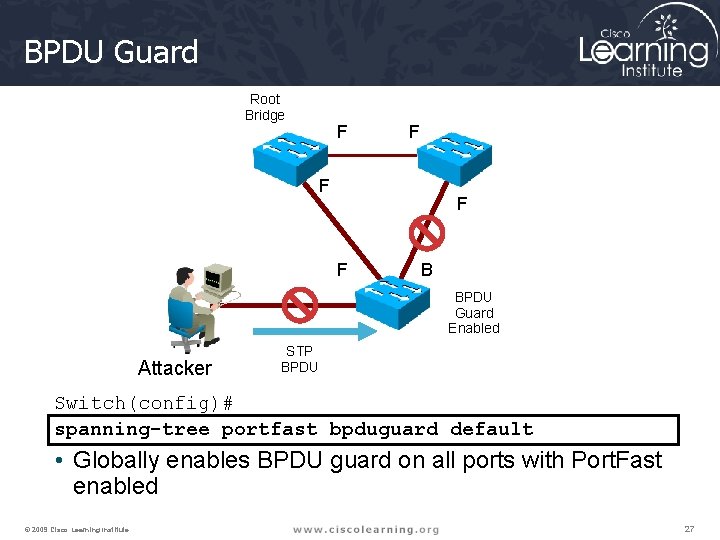
BPDU Guard Root Bridge F F F B BPDU Guard Enabled Attacker STP BPDU Switch(config)# spanning-tree portfast bpduguard default • Globally enables BPDU guard on all ports with Port. Fast enabled © 2009 Cisco Learning Institute. 27

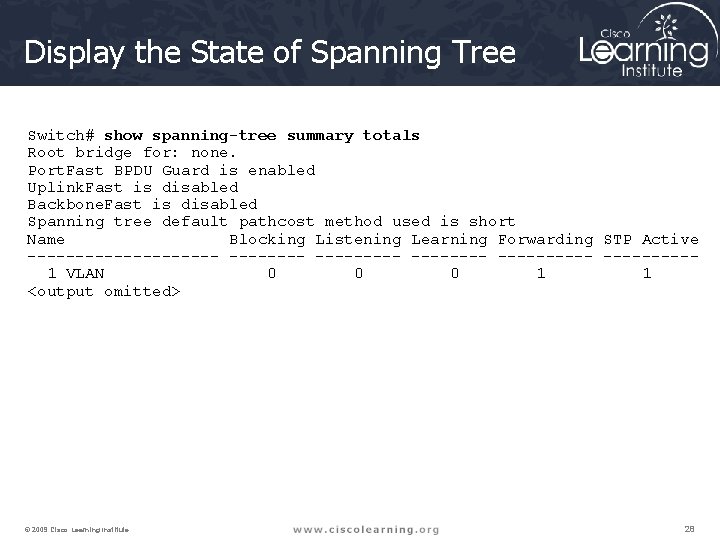
Display the State of Spanning Tree Switch# show spanning-tree summary totals Root bridge for: none. Port. Fast BPDU Guard is enabled Uplink. Fast is disabled Backbone. Fast is disabled Spanning tree default pathcost method used is short Name Blocking Listening Learning Forwarding STP Active ---------- ----------1 VLAN 0 0 0 1 1 <output omitted> © 2009 Cisco Learning Institute. 28

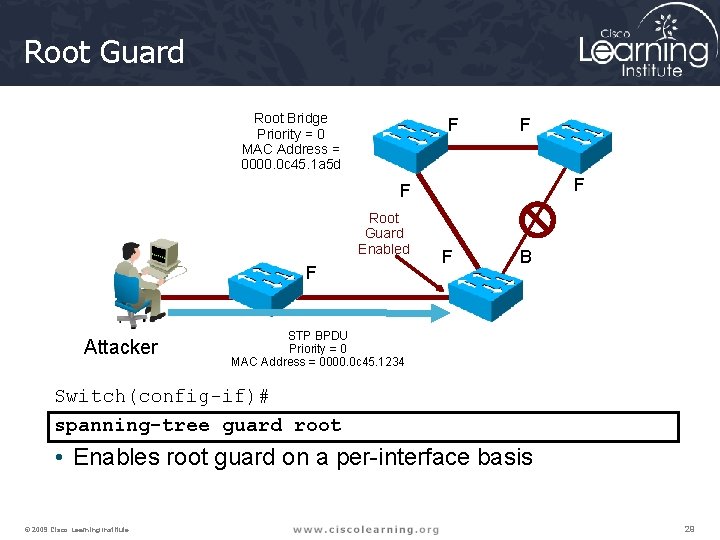
Root Guard Root Bridge Priority = 0 MAC Address = 0000. 0 c 45. 1 a 5 d F F Root Guard Enabled F Attacker F B STP BPDU Priority = 0 MAC Address = 0000. 0 c 45. 1234 Switch(config-if)# spanning-tree guard root • Enables root guard on a per-interface basis © 2009 Cisco Learning Institute. 29

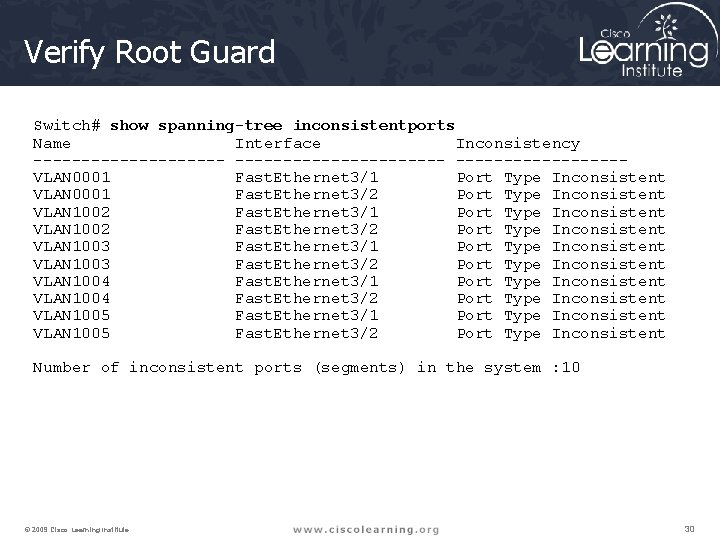
Verify Root Guard Switch# show spanning-tree inconsistentports Name Interface Inconsistency ----------------------VLAN 0001 Fast. Ethernet 3/1 Port Type Inconsistent VLAN 0001 Fast. Ethernet 3/2 Port Type Inconsistent VLAN 1002 Fast. Ethernet 3/1 Port Type Inconsistent VLAN 1002 Fast. Ethernet 3/2 Port Type Inconsistent VLAN 1003 Fast. Ethernet 3/1 Port Type Inconsistent VLAN 1003 Fast. Ethernet 3/2 Port Type Inconsistent VLAN 1004 Fast. Ethernet 3/1 Port Type Inconsistent VLAN 1004 Fast. Ethernet 3/2 Port Type Inconsistent VLAN 1005 Fast. Ethernet 3/1 Port Type Inconsistent VLAN 1005 Fast. Ethernet 3/2 Port Type Inconsistent Number of inconsistent ports (segments) in the system : 10 © 2009 Cisco Learning Institute. 30

Storm Control Methods • Bandwidth as a percentage of the total available bandwidth of the port that can be used by the broadcast, multicast, or unicast traffic • Traffic rate in packets per second at which broadcast, multicast, or unicast packets are received • Traffic rate in bits per second at which broadcast, multicast, or unicast packets are received • Traffic rate in packets per second and for small frames. This feature is enabled globally. The threshold for small frames is configured for each interface. © 2009 Cisco Learning Institute. 31

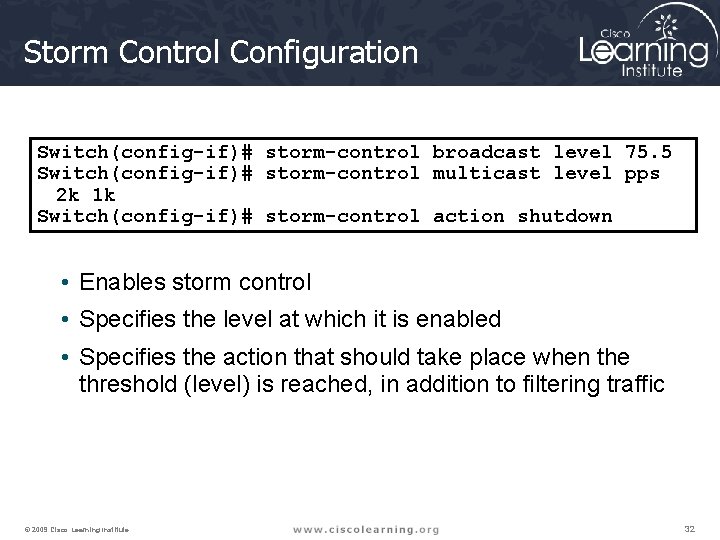
Storm Control Configuration Switch(config-if)# storm-control broadcast level 75. 5 Switch(config-if)# storm-control multicast level pps 2 k 1 k Switch(config-if)# storm-control action shutdown • Enables storm control • Specifies the level at which it is enabled • Specifies the action that should take place when the threshold (level) is reached, in addition to filtering traffic © 2009 Cisco Learning Institute. 32

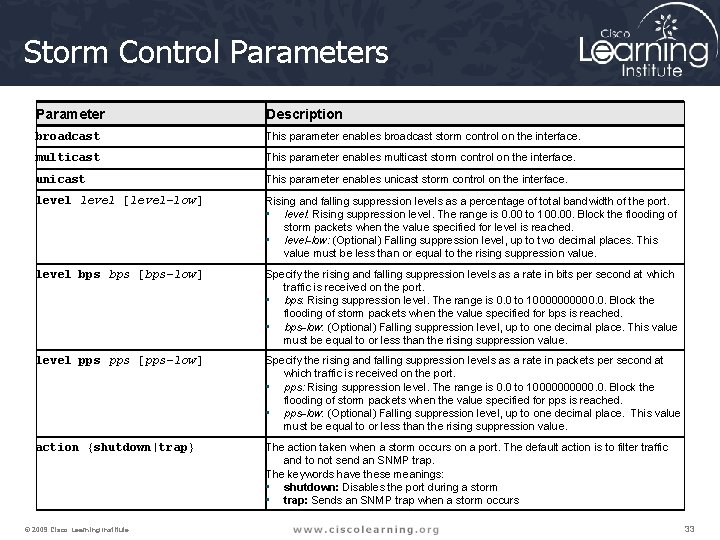
Storm Control Parameters Parameter Description broadcast This parameter enables broadcast storm control on the interface. multicast This parameter enables multicast storm control on the interface. unicast This parameter enables unicast storm control on the interface. level [level-low] Rising and falling suppression levels as a percentage of total bandwidth of the port. • level: Rising suppression level. The range is 0. 00 to 100. Block the flooding of storm packets when the value specified for level is reached. • level-low: (Optional) Falling suppression level, up to two decimal places. This value must be less than or equal to the rising suppression value. level bps [bps-low] Specify the rising and falling suppression levels as a rate in bits per second at which traffic is received on the port. • bps: Rising suppression level. The range is 0. 0 to 100000. 0. Block the flooding of storm packets when the value specified for bps is reached. • bps-low: (Optional) Falling suppression level, up to one decimal place. This value must be equal to or less than the rising suppression value. level pps [pps-low] Specify the rising and falling suppression levels as a rate in packets per second at which traffic is received on the port. • pps: Rising suppression level. The range is 0. 0 to 100000. 0. Block the flooding of storm packets when the value specified for pps is reached. • pps-low: (Optional) Falling suppression level, up to one decimal place. This value must be equal to or less than the rising suppression value. action {shutdown|trap} The action taken when a storm occurs on a port. The default action is to filter traffic and to not send an SNMP trap. The keywords have these meanings: • shutdown: Disables the port during a storm • trap: Sends an SNMP trap when a storm occurs © 2009 Cisco Learning Institute. 33

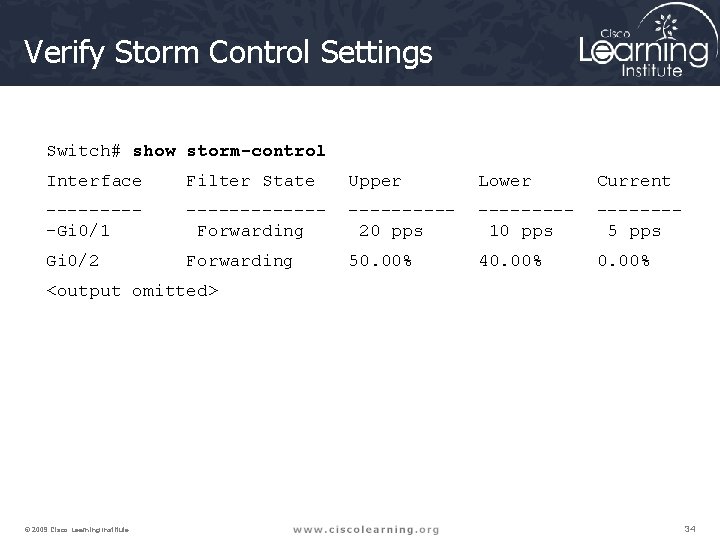
Verify Storm Control Settings Switch# show storm-control Interface Filter State Upper Lower Current -----Gi 0/1 ------Forwarding -----20 pps ----10 pps -------5 pps Gi 0/2 Forwarding 50. 00% 40. 00% <output omitted> © 2009 Cisco Learning Institute. 34

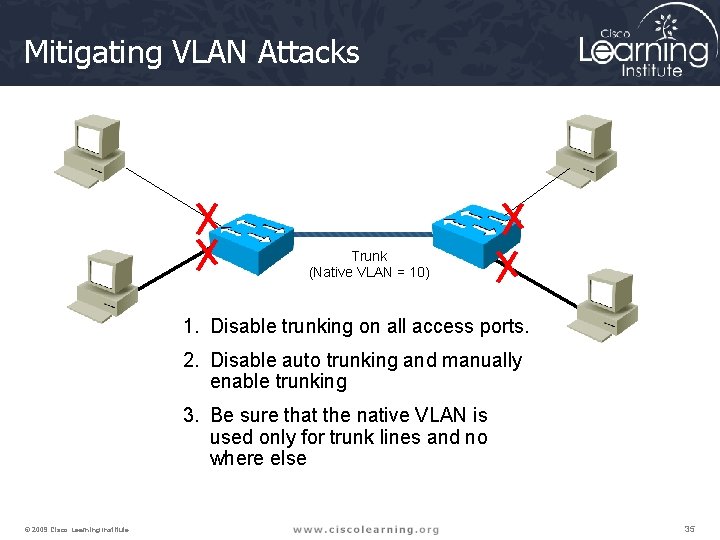
Mitigating VLAN Attacks Trunk (Native VLAN = 10) 1. Disable trunking on all access ports. 2. Disable auto trunking and manually enable trunking 3. Be sure that the native VLAN is used only for trunk lines and no where else © 2009 Cisco Learning Institute. 35

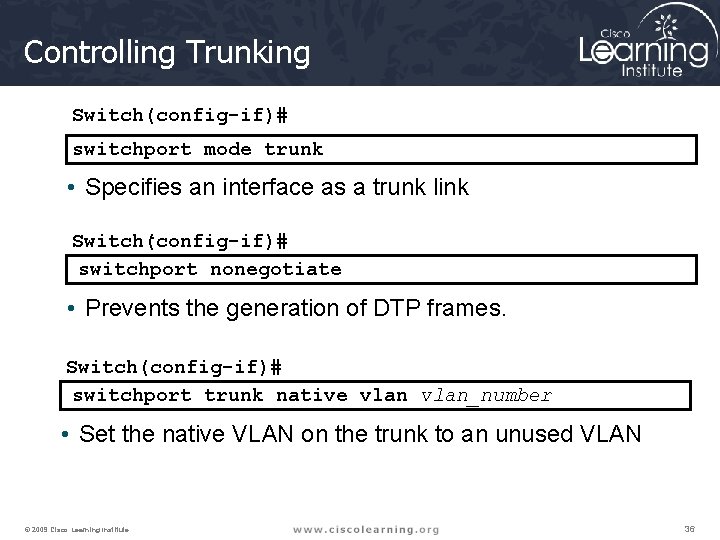
Controlling Trunking Switch(config-if)# switchport mode trunk • Specifies an interface as a trunk link. Switch(config-if)# switchport nonegotiate • Prevents the generation of DTP frames. Switch(config-if)# switchport trunk native vlan_number • Set the native VLAN on the trunk to an unused VLAN © 2009 Cisco Learning Institute. 36

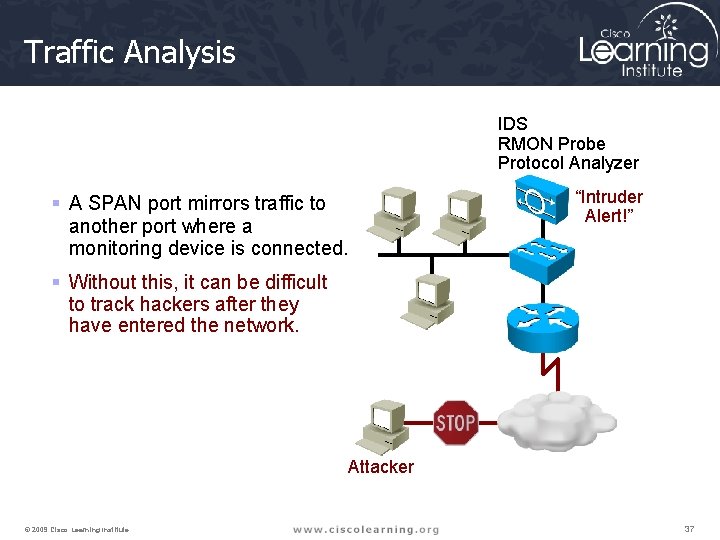
Traffic Analysis IDS RMON Probe Protocol Analyzer § A SPAN port mirrors traffic to another port where a monitoring device is connected. “Intruder Alert!” § Without this, it can be difficult to track hackers after they have entered the network. Attacker © 2009 Cisco Learning Institute. 37
![CLI Commands Switchconfig monitor sessionnumber source interfaceid both rx CLI Commands Switch(config)# monitor session_number source {interface-id [, | -] [both | rx |](https://slidetodoc.com/presentation_image_h2/354a51e429ea66c77396558c4e965104/image-38.jpg)
CLI Commands Switch(config)# monitor session_number source {interface-id [, | -] [both | rx | tx]} | {vlan -id [, | -] [both | rx | tx]}| {remote vlan-id} Switch(config)# monitor session_number destination {interface-id [, | -] [encapsulation replicate] [ingress {dot 1 q vlan-id | isl | untagged vlan-id | vlan-id}]} | {remote vlan-id} © 2009 Cisco Learning Institute. 38

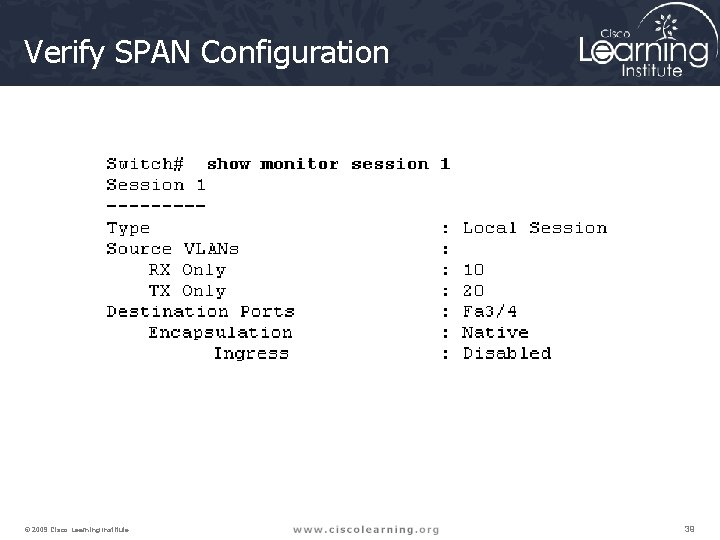
Verify SPAN Configuration © 2009 Cisco Learning Institute. 39

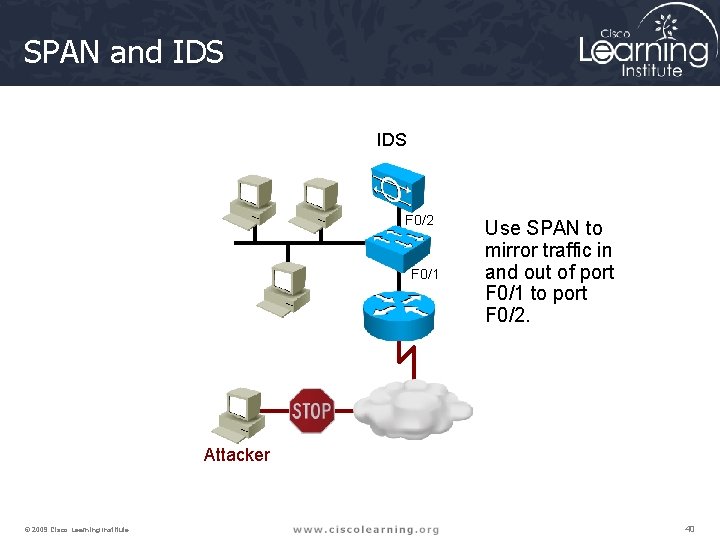
SPAN and IDS F 0/2 F 0/1 Use SPAN to mirror traffic in and out of port F 0/1 to port F 0/2. Attacker © 2009 Cisco Learning Institute. 40

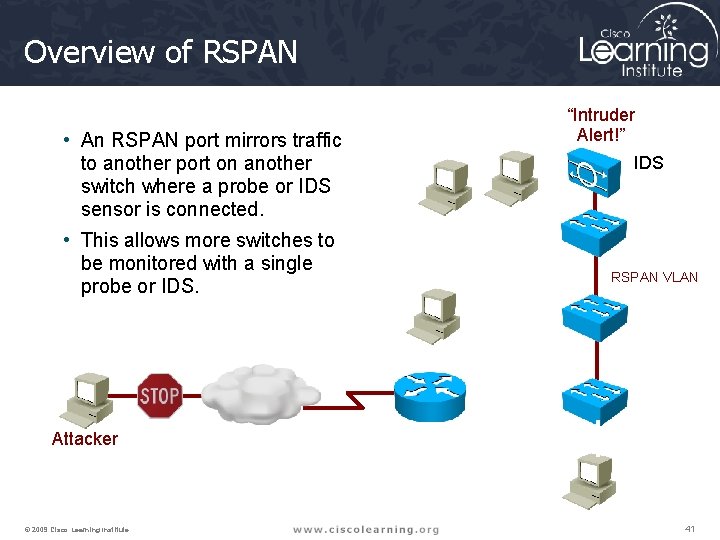
Overview of RSPAN “Intruder Alert!” • An RSPAN port mirrors traffic to another port on another switch where a probe or IDS sensor is connected. • This allows more switches to be monitored with a single probe or IDS Source VLAN RSPAN VLAN Source VLAN Attacker © 2009 Cisco Learning Institute. Source VLAN 41

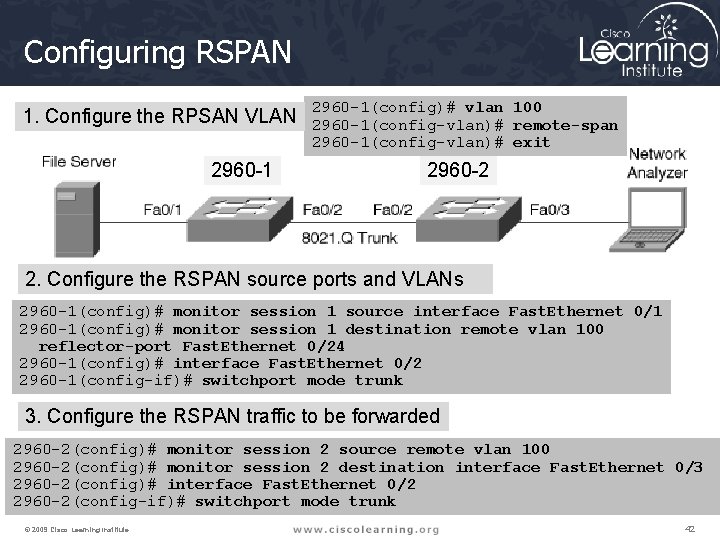
Configuring RSPAN 1. Configure the RPSAN VLAN 2960 -1(config)# vlan 100 2960 -1(config-vlan)# remote-span 2960 -1(config-vlan)# exit 2960 -2 2. Configure the RSPAN source ports and VLANs 2960 -1(config)# monitor session 1 source interface Fast. Ethernet 0/1 2960 -1(config)# monitor session 1 destination remote vlan 100 reflector-port Fast. Ethernet 0/24 2960 -1(config)# interface Fast. Ethernet 0/2 2960 -1(config-if)# switchport mode trunk 3. Configure the RSPAN traffic to be forwarded 2960 -2(config)# monitor session 2 source remote vlan 100 2960 -2(config)# monitor session 2 destination interface Fast. Ethernet 0/3 2960 -2(config)# interface Fast. Ethernet 0/2 2960 -2(config-if)# switchport mode trunk © 2009 Cisco Learning Institute. 42

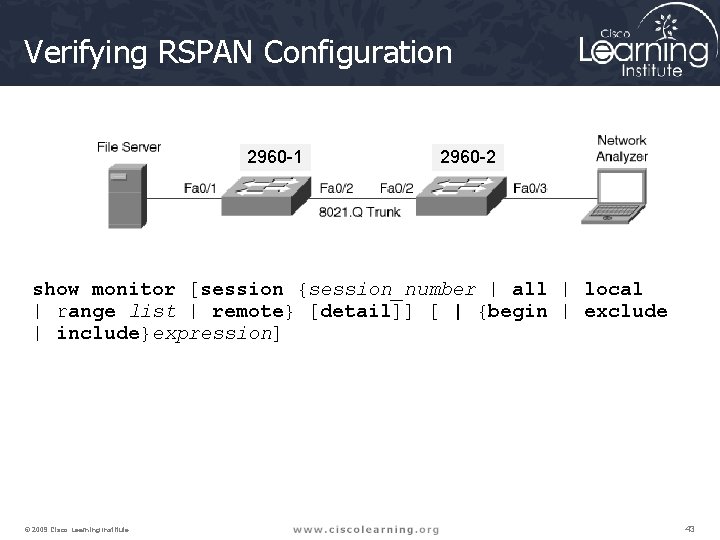
Verifying RSPAN Configuration 2960 -1 2960 -2 show monitor [session {session_number | all | local | range list | remote} [detail]] [ | {begin | exclude | include}expression] © 2009 Cisco Learning Institute. 43

Layer 2 Guidelines • Manage switches in as secure a manner as possible (SSH, out-of-band management, ACLs, etc. ) • Set all user ports to non-trunking mode (except if using Cisco Vo. IP) • Use port security where possible for access ports • Enable STP attack mitigation (BPDU guard, root guard) • Use Cisco Discovery Protocol only where necessary – with phones it is useful • Configure Port. Fast on all non-trunking ports • Configure root guard on STP root ports • Configure BPDU guard on all non-trunking ports © 2009 Cisco Learning Institute. 44

VLAN Practices • Always use a dedicated, unused native VLAN ID for trunk ports • Do not use VLAN 1 for anything • Disable all unused ports and put them in an unused VLAN • Manually configure all trunk ports and disable DTP on trunk ports • Configure all non-trunking ports with switchport mode access © 2009 Cisco Learning Institute. 45