CCNA 2 v 3 1 Module 11 1












- Slides: 38

CCNA 2 v 3. 1 Module 11 1

CCNA 2 Module 11 Access Control Lists (ACLs) 2

Overview • Denying unwanted access to the network • ACL provides basic filtering capabilities based on source/destination IP addresses protocol types and port numbers • ACL lists permit or deny statements that apply to addresses or upper-layer protocols. 3

What are ACLs • Lists of acceptance/denial conditions applied to traffic across a router's interface Permit or deny traffic to and from the network based on Source IP address Destination IP addresses Port numbers Protocols can be created for all routed network protocols Example IP, IPX, Appletalk 4

What are ACLs • Primary reasons to create ACLs Limit network traffic and increase network performance Provide traffic flow control E. g. , Restrict the delivery of routing updates – conserve bandwidth Provide a basic level of security for network access Student Hosts can access Application package Network Student Hosts cannot access Administration Network 5

Decide which types of traffic are forwarded or blocked Permit e-mail traffic to be routed Block all telnet traffic Allow an administrator to control what areas a client can access on a network Screen certain hosts to either permit or deny access to part of a network Certain types of files – ftp, http etc 6

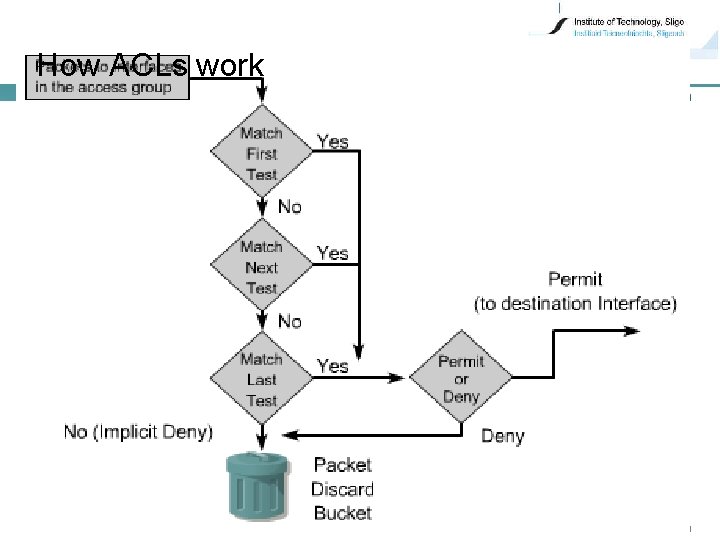
How ACLs work • IOS tests the packets by matching each condition statement in order from top of the list to the bottom • If a match is found, perform the accept or reject action defined in that statement No further ACL statements are checked for that packet The rest of the statements in the ACL is ignored The order in which ACL statements are placed is important 7

• If all the ACL statements are unmatched, implicit "deny any" statement is applied by default Deny always EXISTS and is APPLIED Any packets not matched in the ACL will be denied 8

How ACLs work 9

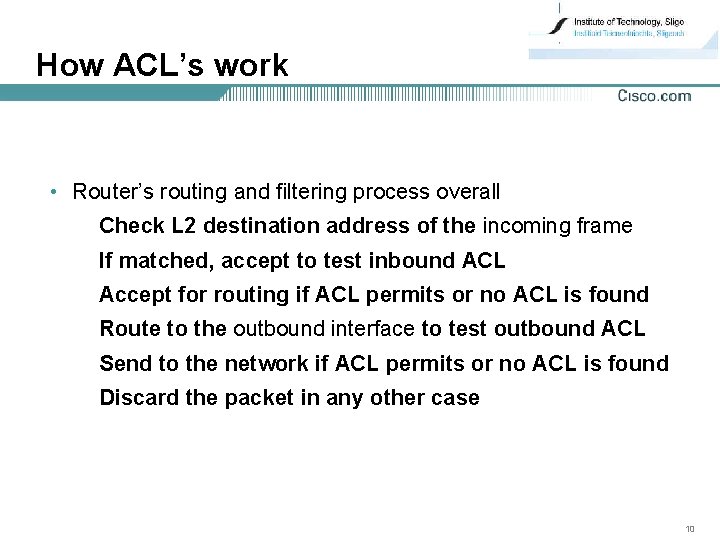
How ACL’s work • Router’s routing and filtering process overall Check L 2 destination address of the incoming frame If matched, accept to test inbound ACL Accept for routing if ACL permits or no ACL is found Route to the outbound interface to test outbound ACL Send to the network if ACL permits or no ACL is found Discard the packet in any other case 10

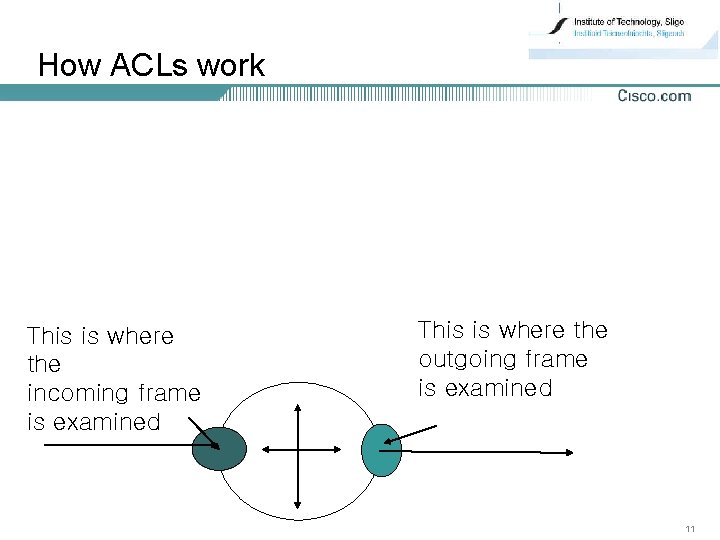
How ACLs work This is where the incoming frame is examined This is where the outgoing frame is examined 11

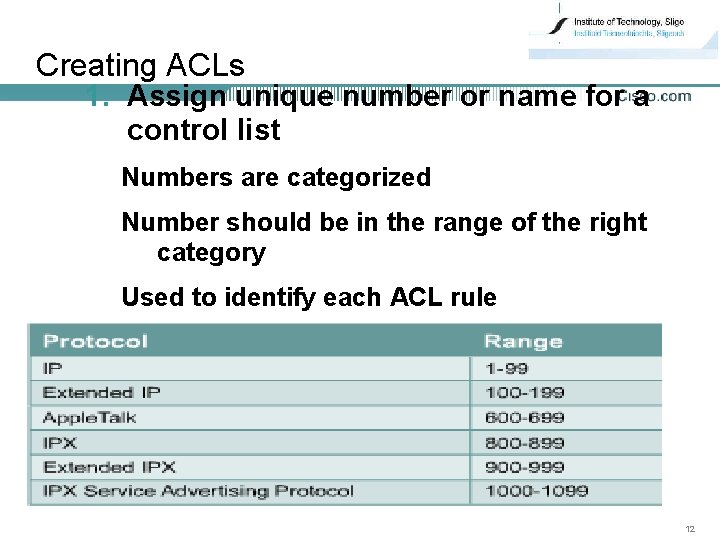
Creating ACLs 1. Assign unique number or name for a control list Numbers are categorized Number should be in the range of the right category Used to identify each ACL rule 12

Creating ACLs 2. Define the access list statements Router(config)#access-list-no {permit|deny} {test-condition} An access-list-no can be a name (named ACL) test-conditions are the targets to control 3. Assign them to the proper interface Router(config-if)#{protocol} access-group access-list no {in|out} In or out is defined looking at inside the router 13

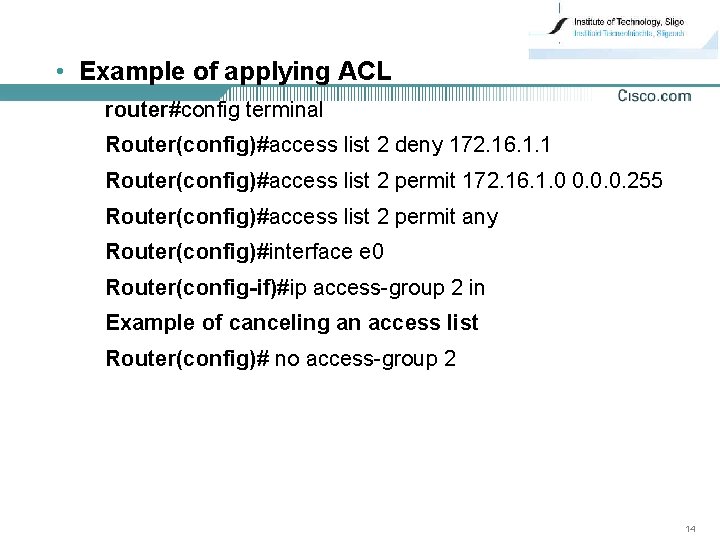
• Example of applying ACL router#config terminal Router(config)#access list 2 deny 172. 16. 1. 1 Router(config)#access list 2 permit 172. 16. 1. 0 0. 0. 0. 255 Router(config)#access list 2 permit any Router(config)#interface e 0 Router(config-if)#ip access-group 2 in Example of canceling an access list Router(config)# no access-group 2 14

Creating ACLs • Basic rules One access list per protocol per direction Standard access lists should be applied closest to the destination Extended access control lists should be applied closest to the source Use the inbound or outbound interface reference as if looking at the port from inside the router 15

Statements are processed sequentially from the top of list to the bottom until a match is found There is an implicit deny at the end of all access lists This will not appear in the configuration listing If no match is found then the packet is denied Access list entries should filter in the order from specific to general The match condition is examined first, then permit|deny 16

Creating ACLs • Basic rules (continued) It is not possible to selectively add and remove lines with numbered ACLs Remove the whole list using no access-list x command re-define the ACL New lines can be added @ named ACL always added to the end of the access list The router will discard the packet and send ICMP host unreachable message to the sender 17

Creating ACLs • Basic rules (continued) Care should be used when removing an access list In some version of IOS, default deny any may not be removed after the access list is removed at an interface Then all traffic will be halted Outbound filters do not affect traffic originating from the local router 18

The function of a wildcard mask • Designed to specify target individual or groups of IP addresses based on the given address Given with the specified IP address or the network number 32 bits long with 0’s and 1’s ‘ 1’ means No match needed Target address can have any bit value (wildcard; 0 or 1) at the position where the mask bits are 1 ‘ 0’ means Match needed Target address can only have the same bit value as in the given address at the position where the mask bits are 0 19

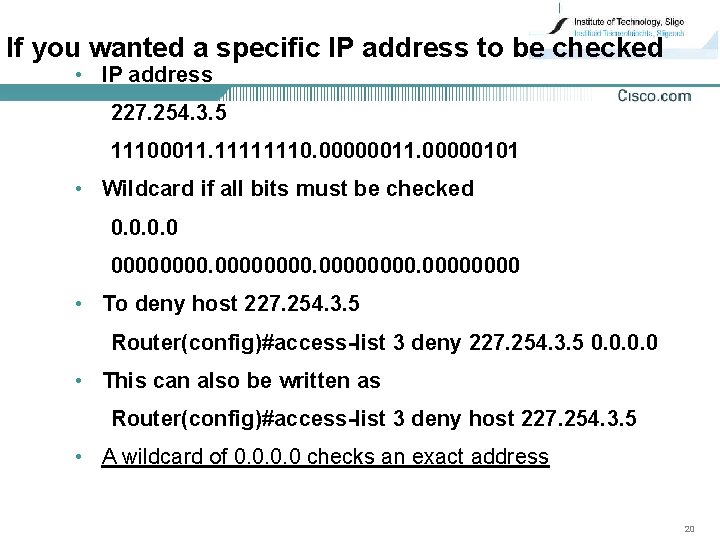
If you wanted a specific IP address to be checked • IP address 227. 254. 3. 5 11100011. 11111110. 00000011. 00000101 • Wildcard if all bits must be checked 0. 0 00000000. 0000 • To deny host 227. 254. 3. 5 Router(config)#access-list 3 deny 227. 254. 3. 5 0. 0 • This can also be written as Router(config)#access-list 3 deny host 227. 254. 3. 5 • A wildcard of 0. 0 checks an exact address 20

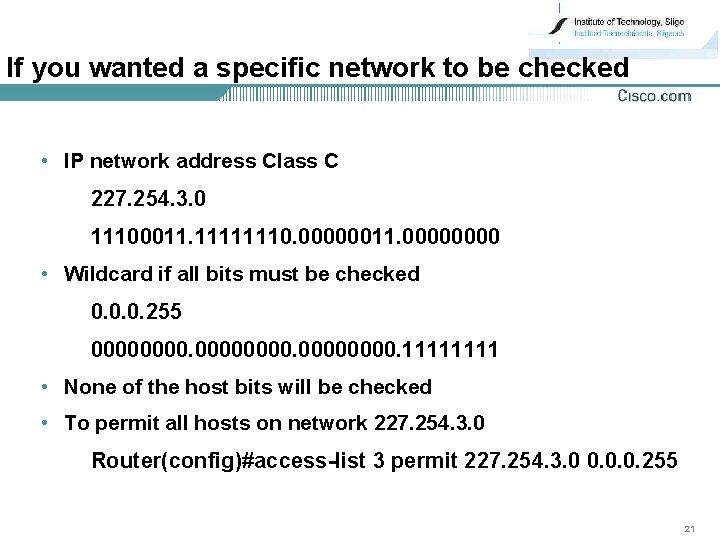
If you wanted a specific network to be checked • IP network address Class C 227. 254. 3. 0 11100011. 11111110. 00000011. 0000 • Wildcard if all bits must be checked 0. 0. 0. 255 00000000. 1111 • None of the host bits will be checked • To permit all hosts on network 227. 254. 3. 0 Router(config)#access-list 3 permit 227. 254. 3. 0 0. 0. 0. 255 21

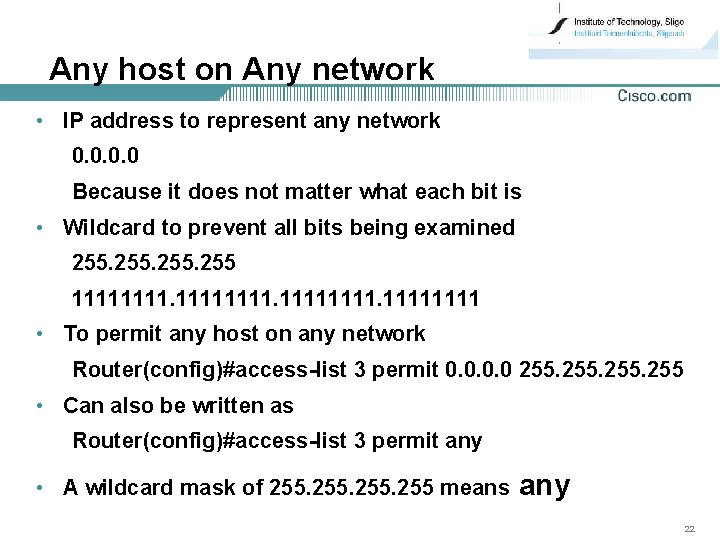
Any host on Any network • IP address to represent any network 0. 0 Because it does not matter what each bit is • Wildcard to prevent all bits being examined 255 11111111. 1111 • To permit any host on any network Router(config)#access-list 3 permit 0. 0 255 • Can also be written as Router(config)#access-list 3 permit any • A wildcard mask of 255 means any 22

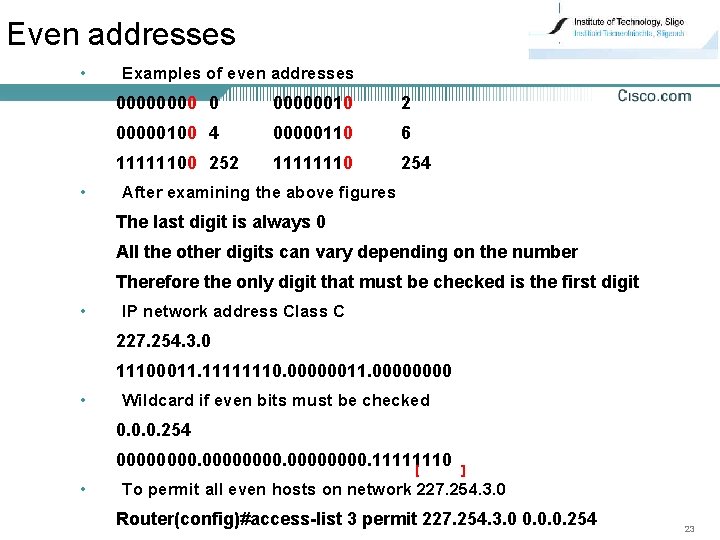
Even addresses • • Examples of even addresses 0000 0 00000010 2 00000100 4 00000110 6 11111100 252 11111110 254 After examining the above figures The last digit is always 0 All the other digits can vary depending on the number Therefore the only digit that must be checked is the first digit • IP network address Class C 227. 254. 3. 0 11100011. 11111110. 00000011. 0000 • Wildcard if even bits must be checked 0. 0. 0. 254 00000000. 11111110 [ • ] To permit all even hosts on network 227. 254. 3. 0 Router(config)#access-list 3 permit 227. 254. 3. 0 0. 0. 0. 254 23

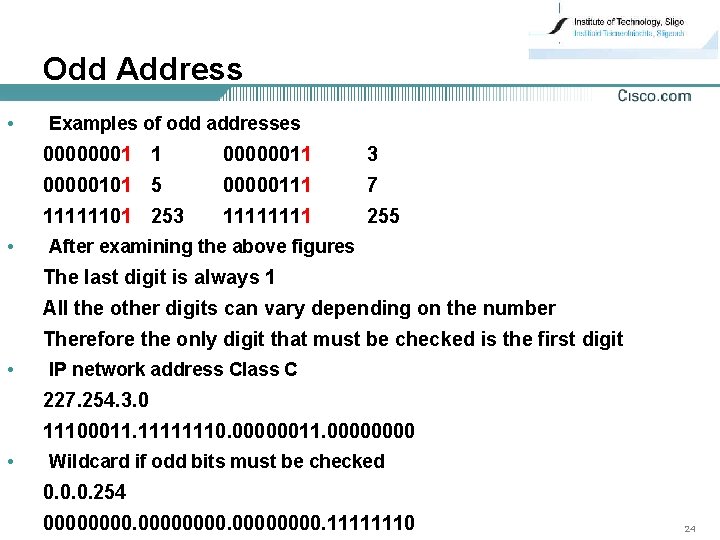
Odd Address • • Examples of odd addresses 00000001 1 00000011 3 00000101 5 00000111 7 11111101 253 1111 255 After examining the above figures The last digit is always 1 All the other digits can vary depending on the number Therefore the only digit that must be checked is the first digit • IP network address Class C 227. 254. 3. 0 11100011. 11111110. 00000011. 0000 • Wildcard if odd bits must be checked 0. 0. 0. 254 00000000. 11111110 24

Verifying ACLs • Show ip interface displays IP interface information and indicates whether any ACLs are set • Show access-lists displays the contents of all ACLs on the router • Show access-list 1 Displays the content of ACL 1 on the router • Show running config reveal the access lists on a router and the interface assignment information 25

Standard ACLs • Checks source IP address Host IP address, subnet, or network address • Affects entire protocol suit TCP, HTTP, IP etc. . • Valid numbers Standard IP ACL 1 -99 (1300 to 1999 in recent IOS) • Always applied to port closest to destination • Adding an ACL router(config)#access-list-number {permit|deny} source {source-wildcard} [log] Log sends information about matched packet to console • Removing an ACL Router(config)#no access-list-number 26

Extended ACLs • Provides a greater range of control and flexibility Checks the source and destination packet addresses Checks protocol types and port numbers • Valid numbers Extended IP ALC 100 -199 2000~2699 in recent IOS • Always applied to port closest to source • Adding an Extended ACL Router(config)#access-list-number {permit|deny} protocol source [source-mask destination-mask operator operand] [ established] Protocols - IP, TCP, UDP, ICMP, IGRP, GRE Operator is lt (<), gt (>), eq (=), or neq (≠) Operand is a port number or application layer protocol 27

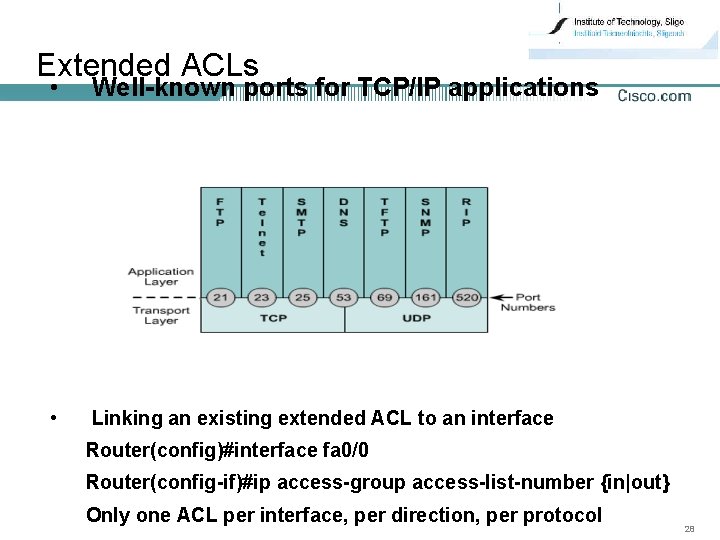
Extended ACLs • Well-known ports for TCP/IP applications • Linking an existing extended ACL to an interface Router(config)#interface fa 0/0 Router(config-if)#ip access-group access-list-number {in|out} Only one ACL per interface, per direction, per protocol 28

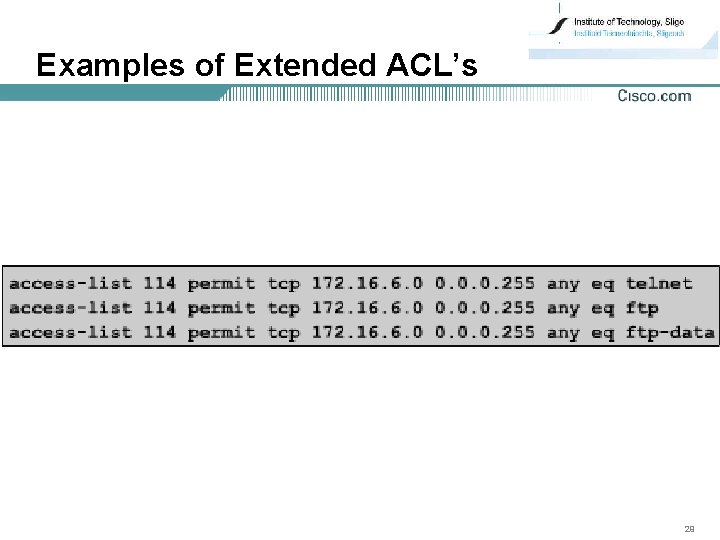
Examples of Extended ACL’s 29

Named ACLs • Introduced in IOS 11. 2 Give standard and extend ACLs names instead of numbers • Procedure for defining a named ACL Define a named ACL 1. Router(config)#ip access-list {extended|standard} name 2. router(config)#ip access-list extended test Add each permit/deny statement router(config-ext-nacl)#access-list permit…. . Apply the named access list to the interface 1. Router(config)#interface serial 0/0 2. Router(config-if)#ip access-group test out 30

Named ACLs • Advantages Intuitively identify an ACL using an alphanumeric name. Eliminate the limit of 798 simple and 799 extended ACLs Can modify ACLs without deleting and then reconfiguring them allow the deletion of statements only allow for statements to be inserted at the end of a list it is a good idea to use a text editor to create them 31

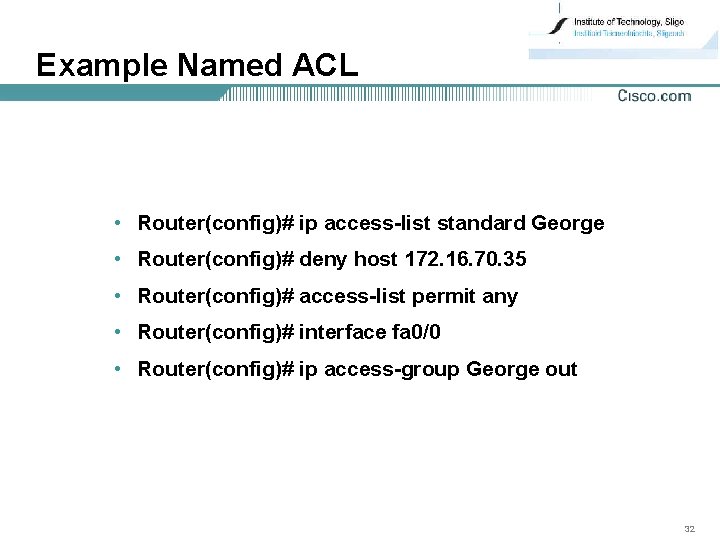
Example Named ACL • Router(config)# ip access-list standard George • Router(config)# deny host 172. 16. 70. 35 • Router(config)# access-list permit any • Router(config)# interface fa 0/0 • Router(config)# ip access-group George out 32

Placing ACLs • General rules in placing ACLs Place ACLs where it can maximize increasing efficiency Put the extended ACLs as close as possible to the source of the traffic denied Unnecessary traffic will be minimized Standard ACLs should be placed as close to the destination as possible ACL does not know the destination 33

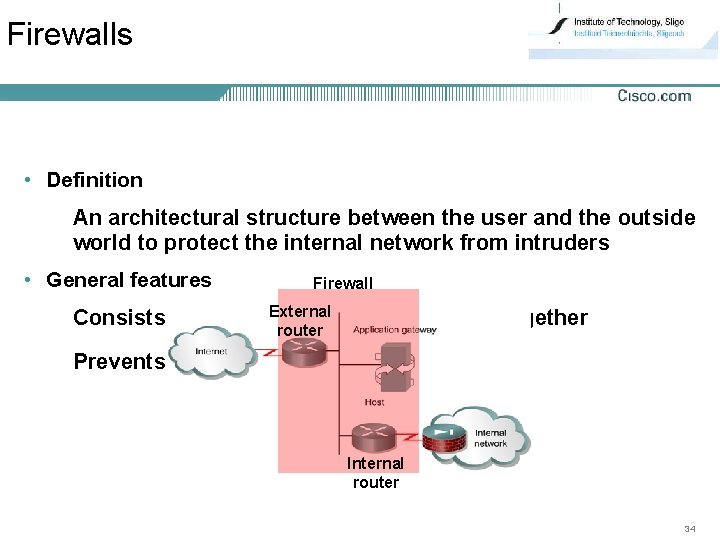
Firewalls • Definition An architectural structure between the user and the outside world to protect the internal network from intruders • General features Firewall Consists of several. External equipments working together router Prevents unwanted and illegal access Internal router 34

Firewalls • Operation of the firewall The external router directs all traffic to the application gateway The internal router accepts packets only from the application gateway The gateway controls the delivery of network-based services both into and from the internal network Processes every packet to block or pass according to the filtering rule 35

Firewalls • Use of ACLs in the firewall routers Control traffic entering or exiting a specific part of the internal network Provides basic security from the outside network into a more private area of the network Ex) If the only application that is permitted is mail, then configure ACL so that only mail packets can be allowed through the router. This protects the application gateway and avoids overwhelming it with packets that it would otherwise discard. 36

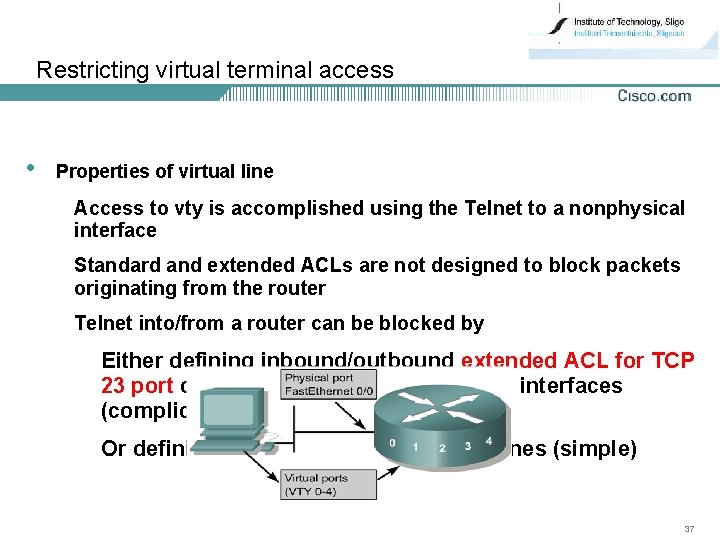
Restricting virtual terminal access • Properties of virtual line Access to vty is accomplished using the Telnet to a nonphysical interface Standard and extended ACLs are not designed to block packets originating from the router Telnet into/from a router can be blocked by Either defining inbound/outbound extended ACL for TCP 23 port on each of the physical network interfaces (complicated) Or defining the vty ACL on the virtual lines (simple) 37

Restricting virtual terminal access • Blocking packets to vty using vty ACL There is only one type of vty access list Only numbered ACL can be applied to virtual lines Identical restrictions should be placed on all vty lines A user can attempt to connect to any of them Defining an ACL Router(config)#access-list 2 permit 172. 16. 1. 0 0. 0 Router(config)#access-list 2 deny any Apply ACL to vty line Router(config)#line vty 0 4 Router(config-line)#password cisco Router(config-line)#login Router(config-line)#access-class 2 in 38