BuyerSeller Watermarking BSW Protocols Geong Sen Poh 31

Buyer-Seller Watermarking (BSW) Protocols Geong Sen Poh 31 Oct 2006

Outline Introduction Motivation Development of BSW Goals, Methodology and Assumptions Protocols Memon-Wong Protocol (MW) Lei et al. Protocol (Lei) Zhang et al. Protocol (Zhang) Analysis of Zhang et al. Protocol Summary 2
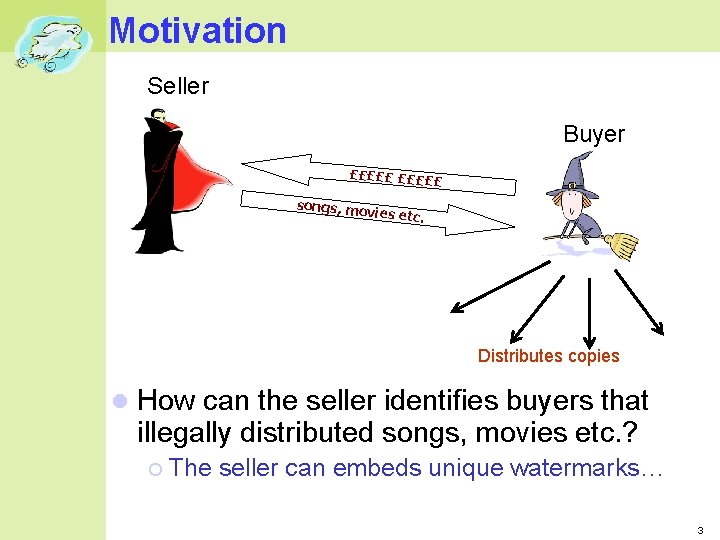
Motivation Seller Buyer £££££ £ songs, mo vies etc. Distributes copies How can the seller identifies buyers that illegally distributed songs, movies etc. ? The seller can embeds unique watermarks… 3
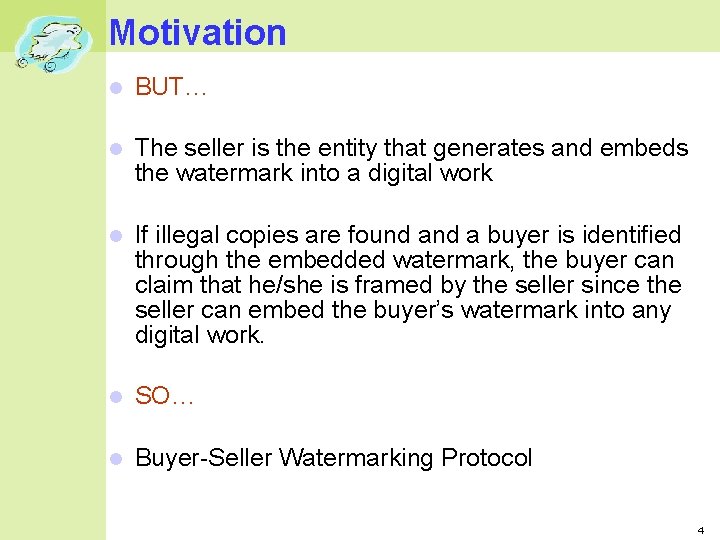
Motivation BUT… The seller is the entity that generates and embeds the watermark into a digital work If illegal copies are found a buyer is identified through the embedded watermark, the buyer can claim that he/she is framed by the seller since the seller can embed the buyer’s watermark into any digital work. SO… Buyer-Seller Watermarking Protocol 4
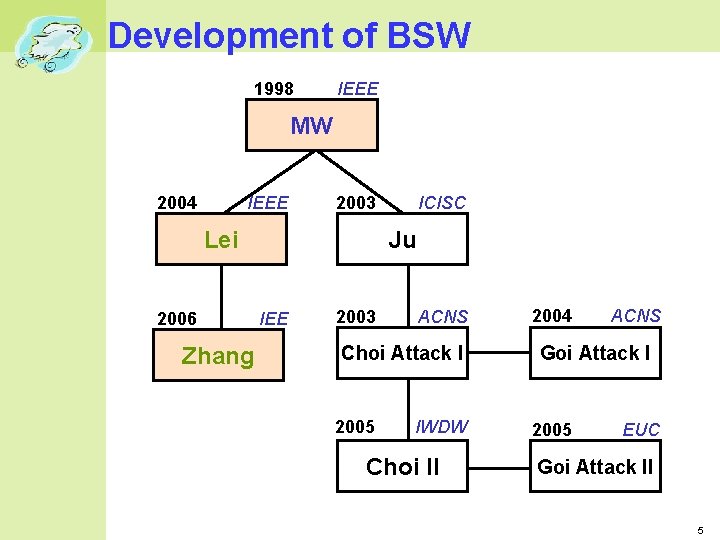
Development of BSW 1998 IEEE MW 2004 IEEE 2003 Ju Lei 2006 Zhang ICISC IEE 2003 ACNS Choi Attack I 2005 IWDW Choi II 2004 ACNS Goi Attack I 2005 EUC Goi Attack II 5

Goals No Framing No Repudiation An attacker should not be able to find, generate, or delete the fingerprint by comparing the marked copies, even if they have access to a large number of copies Anonymity A buyer who has illegally distributed digital works can be traced Collusion Tolerance The buyer accused of reselling an unauthorised copy should not be able to claim that the copy was created by the seller or a security breach of the seller’s system Traceability An honest buyer should not be falsely accused by a malicious seller or other buyers A buyer should be able to buy anonymously Unlinkability Given two marked digital works, no one can decide whether or not they were bought by the same buyer B. M. Goi, R. C. -W. Phan, Y. Yang, F. Bao, R. H. Deng and M. U. Siddiqi, Cryptanalysis of Two Anonymous Buyer-Seller Watermarking Protocols and an Improvement for True Anonymity, ACNS 2004, LNCS 3089, pp. 369 -382, 2004 6
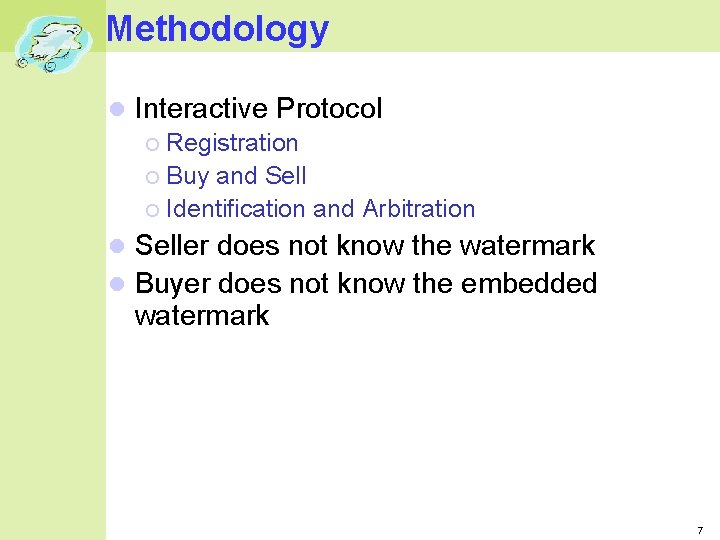
Methodology Interactive Protocol Registration Buy and Sell Identification and Arbitration Seller does not know the watermark Buyer does not know the embedded watermark 7
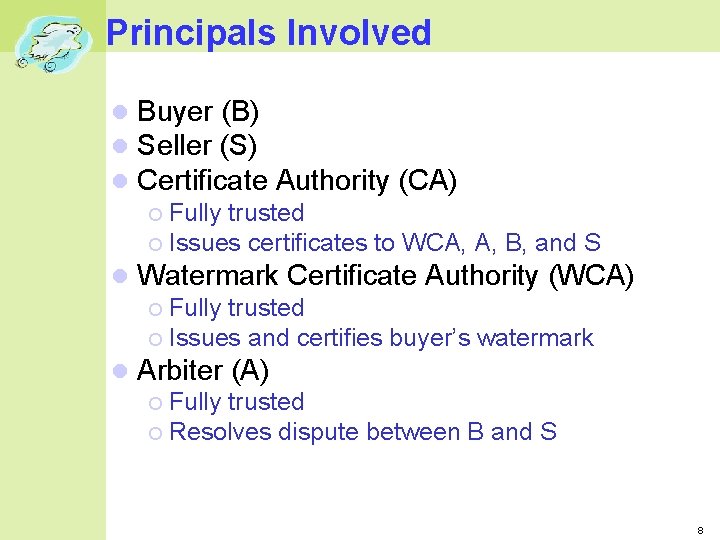
Principals Involved Buyer (B) Seller (S) Certificate Authority (CA) Fully trusted Issues certificates to WCA, A, B, and S Watermark Certificate Authority (WCA) Fully trusted Issues and certifies buyer’s watermark Arbiter (A) Fully trusted Resolves dispute between B and S 8

Assumptions Each of the principals involved (e. g. buyer and seller) has a CA certified public and private key pair, (PKi, SKi) for i the identity of the principal The public-key encryption algorithm is homomorphic 9

Homomorphic Encryption E(x) + E(y) = E(x + y) E(x) E(y) = E(x y) Example: RSA If the public key is: n, e then: E(x 1) E(x 2) = x 1 ex 2 e mod n = (x 1 x 2)e mod n = E(x 1 x 2) Paillier homomorphic encryption (in Zhang Protocol): E(x) E(y) = E(x + y) 10
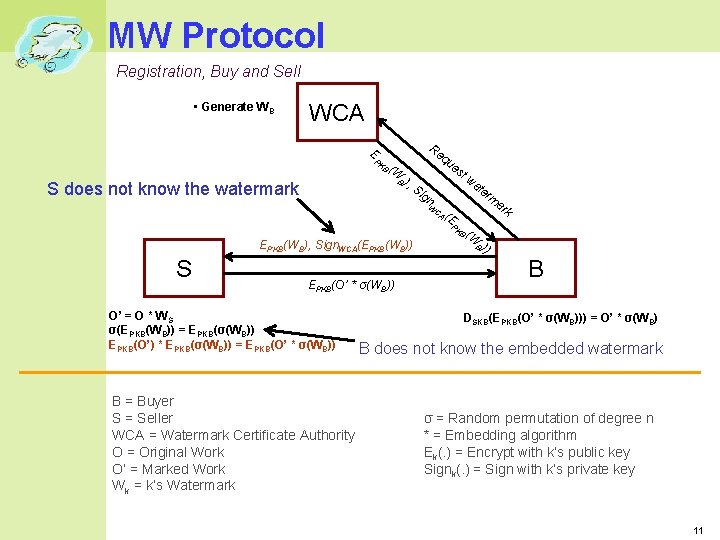
MW Protocol Registration, Buy and Sell • Generate WB WCA Re E PK B qu es (W B ), S does not know the watermark tw at Si gn W CA S EPKB(O’ * σ(WB)) O’ = O * W S σ(EPKB(WB)) = EPKB(σ(WB)) EPKB(O’) * EPKB(σ(WB)) = EPKB(O’ * σ(WB)) B = Buyer S = Seller WCA = Watermark Certificate Authority O = Original Work O’ = Marked Work Wk = k’s Watermark ar k (E PK B EPKB(WB), Sign. WCA(EPKB(WB)) er m (W B )) B DSKB(EPKB(O’ * σ(WB))) = O’ * σ(WB) B does not know the embedded watermark σ = Random permutation of degree n * = Embedding algorithm Ek(. ) = Encrypt with k’s public key Signk(. ) = Sign with k’s private key 11
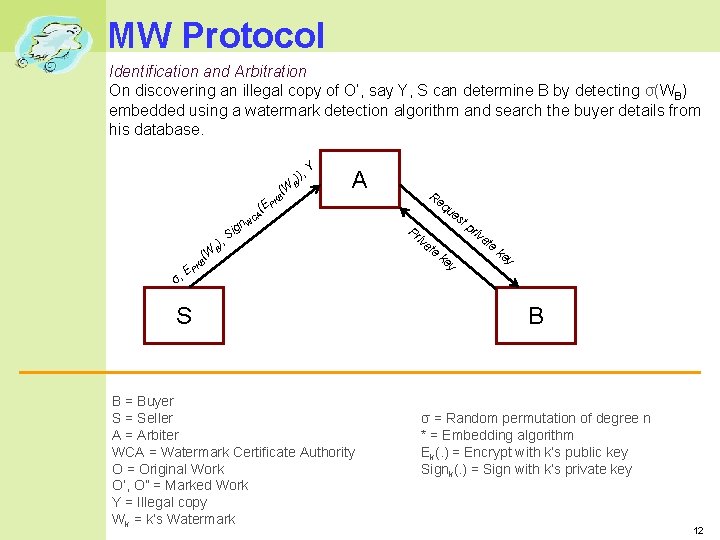
MW Protocol Identification and Arbitration On discovering an illegal copy of O’, say Y, S can determine B by detecting σ(WB) embedded using a watermark detection algorithm and search the buyer details from his database. (W )), B Y A Re KB qu es (E P CA n. W E σ, (W B ), g Si B PK S B = Buyer S = Seller A = Arbiter WCA = Watermark Certificate Authority O = Original Work O’, O” = Marked Work Y = Illegal copy Wk = k’s Watermark Pr iva te tp riv at e ke y B σ = Random permutation of degree n * = Embedding algorithm Ek(. ) = Encrypt with k’s public key Signk(. ) = Sign with k’s private key 12
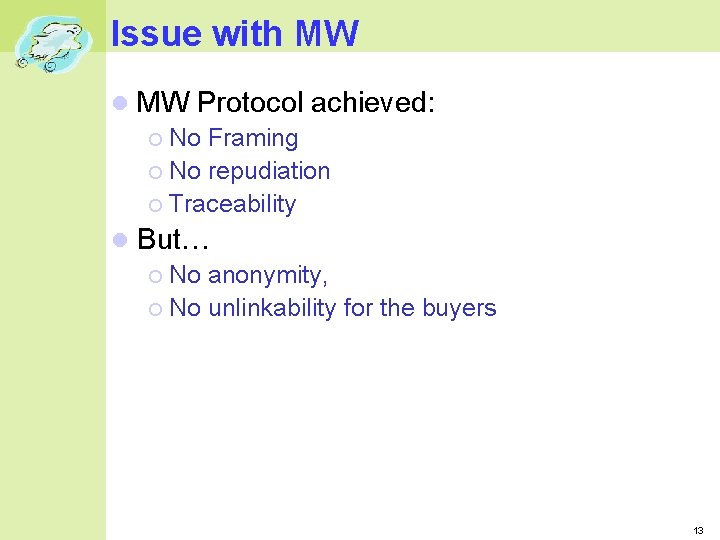
Issue with MW Protocol achieved: No Framing No repudiation Traceability But… No anonymity, No unlinkability for the buyers 13
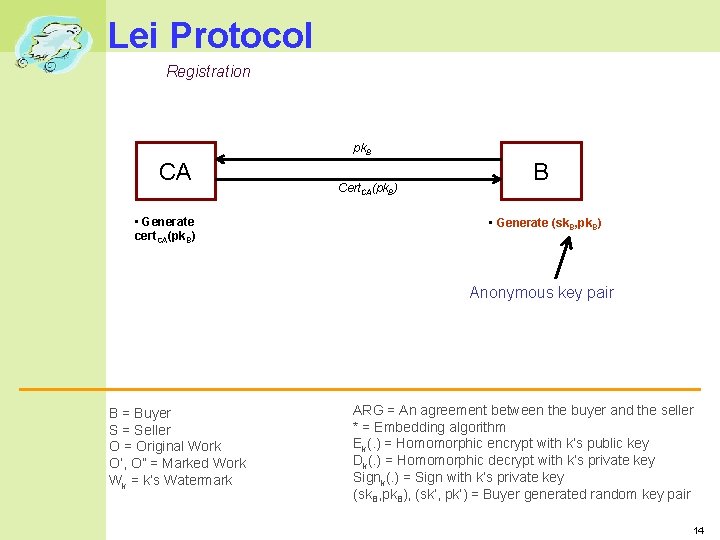
Lei Protocol Registration pk. B CA • Generate cert. CA(pk. B) Cert. CA(pk. B) B • Generate (sk. B, pk. B) Anonymous key pair B = Buyer S = Seller O = Original Work O’, O” = Marked Work Wk = k’s Watermark ARG = An agreement between the buyer and the seller * = Embedding algorithm Ek(. ) = Homomorphic encrypt with k’s public key Dk(. ) = Homomorphic decrypt with k’s private key Signk(. ) = Sign with k’s private key (sk. B, pk. B), (sk’, pk’) = Buyer generated random key pair 14
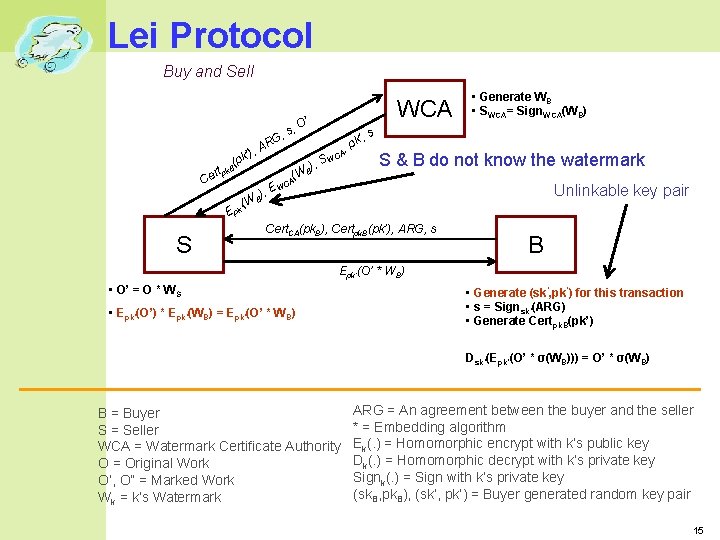
Lei Protocol Buy and Sell ’), pk ( B k ert p C (W k’ , RG s A ), E B WCA ’ , O (W A ), S B WC ’, s pk , A • Generate WB • SWCA= Sign. WCA(WB) S & B do not know the watermark WC Unlinkable key pair Ep S Cert. CA(pk. B), Certpk. B(pk’), ARG, s B Epk’(O’ * WB) • O’ = O * W S • Epk’(O’) * Epk’(WB) = Epk’(O’ * WB) • Generate (sk’, pk’) for this transaction • s = Signsk’(ARG) • Generate Certpk. B(pk’) Dsk’(Epk’(O’ * σ(WB))) = O’ * σ(WB) B = Buyer S = Seller WCA = Watermark Certificate Authority O = Original Work O’, O” = Marked Work Wk = k’s Watermark ARG = An agreement between the buyer and the seller * = Embedding algorithm Ek(. ) = Homomorphic encrypt with k’s public key Dk(. ) = Homomorphic decrypt with k’s private key Signk(. ) = Sign with k’s private key (sk. B, pk. B), (sk’, pk’) = Buyer generated random key pair 15
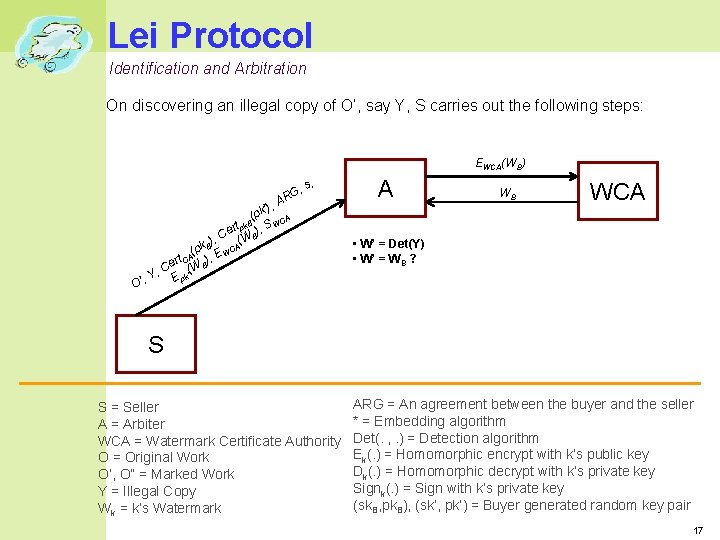
Lei Protocol Identification and Arbitration On discovering an illegal copy of O’, say Y, S carries out the following steps: EWCA(WB) , RG s, A ’), k p ( CA rt pk. B ), S W e ), C A(W B B k (p E WC , t CA r e (W B) C , ’ ’, Y E pk A WB WCA • W’ = Det(Y) • W’ = WB ? O S S = Seller A = Arbiter WCA = Watermark Certificate Authority O = Original Work O’, O” = Marked Work Y = Illegal Copy Wk = k’s Watermark ARG = An agreement between the buyer and the seller * = Embedding algorithm Det(. , . ) = Detection algorithm Ek(. ) = Homomorphic encrypt with k’s public key Dk(. ) = Homomorphic decrypt with k’s private key Signk(. ) = Sign with k’s private key (sk. B, pk. B), (sk’, pk’) = Buyer generated random key pair 17

Zhang Protocol Similar to Lei Protocol except that there is no WCA No need WCA to generate and certify watermark: S generates his part of the watermark B generates his part of the watermark The final watermark embedded in the digital work is the combination of S and B’s watermarks 18
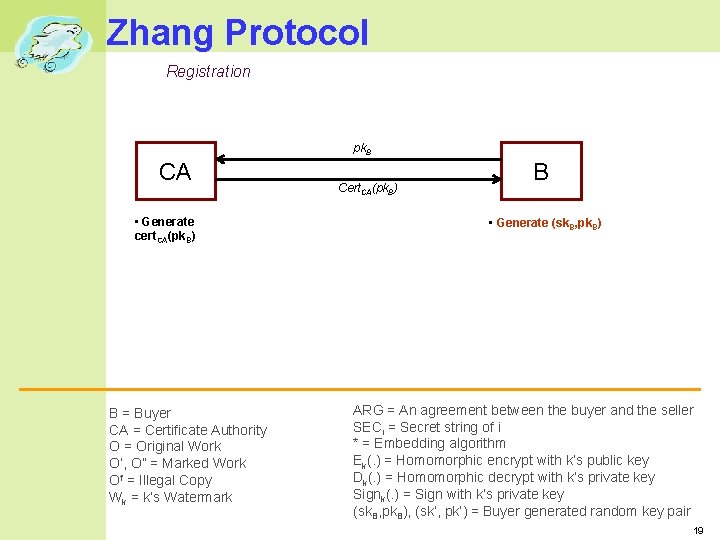
Zhang Protocol Registration pk. B CA • Generate cert. CA(pk. B) B = Buyer CA = Certificate Authority O = Original Work O’, O” = Marked Work Of = Illegal Copy Wk = k’s Watermark Cert. CA(pk. B) B • Generate (sk. B, pk. B) ARG = An agreement between the buyer and the seller SECi = Secret string of i * = Embedding algorithm Ek(. ) = Homomorphic encrypt with k’s public key Dk(. ) = Homomorphic decrypt with k’s private key Signk(. ) = Sign with k’s private key (sk. B, pk. B), (sk’, pk’) = Buyer generated random key pair 19
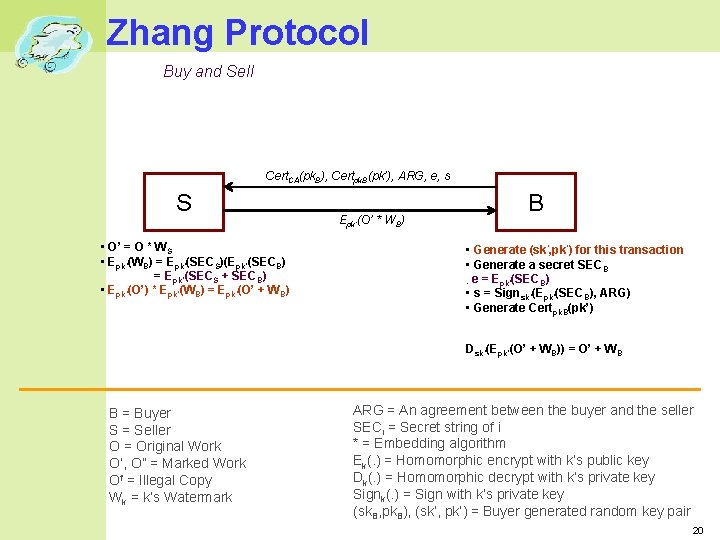
Zhang Protocol Buy and Sell Cert. CA(pk. B), Certpk. B(pk’), ARG, e, s S • O’ = O * W S • Epk’(WB) = Epk’(SECS)(Epk’(SECB) = Epk’(SECS + SECB) • Epk’(O’) * Epk’(WB) = Epk’(O’ + WB) Epk’(O’ * WB) B • Generate (sk’, pk’) for this transaction • Generate a secret SECB • e = Epk’(SECB) • s = Signsk’(Epk’(SECB), ARG) • Generate Certpk. B(pk’) Dsk’(Epk’(O’ + WB)) = O’ + W B B = Buyer S = Seller O = Original Work O’, O” = Marked Work Of = Illegal Copy Wk = k’s Watermark ARG = An agreement between the buyer and the seller SECi = Secret string of i * = Embedding algorithm Ek(. ) = Homomorphic encrypt with k’s public key Dk(. ) = Homomorphic decrypt with k’s private key Signk(. ) = Sign with k’s private key (sk. B, pk. B), (sk’, pk’) = Buyer generated random key pair 20
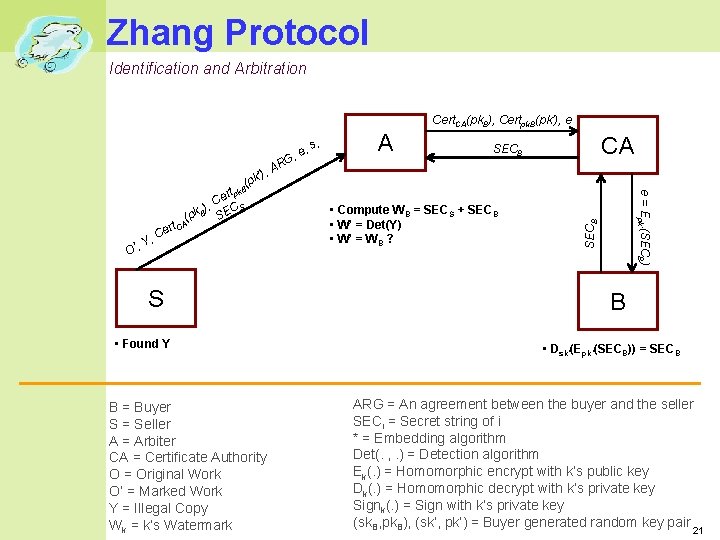
Zhang Protocol Identification and Arbitration Cert. CA(pk. B), Certpk. B(pk’), e S • Found Y B = Buyer S = Seller A = Arbiter CA = Certificate Authority O = Original Work O’ = Marked Work Y = Illegal Copy Wk = k’s Watermark A CA SECB • Compute WB = SECS + SECB • W’ = Det(Y) • W’ = WB ? SECB rt CA e C Y, , ’ O k ert p C ), CS (pk B SE s, e = Epk’(SECB) ’), pk ( B G AR , , e B • Dsk’(Epk’(SECB)) = SECB ARG = An agreement between the buyer and the seller SECi = Secret string of i * = Embedding algorithm Det(. , . ) = Detection algorithm Ek(. ) = Homomorphic encrypt with k’s public key Dk(. ) = Homomorphic decrypt with k’s private key Signk(. ) = Sign with k’s private key (sk. B, pk. B), (sk’, pk’) = Buyer generated random key pair 21

Analysis of Zhang et al. Protocols Issues Buyer can remove his part of the watermark easily since… O’ + WB = O’ + SECS + SECB and Buyer knows SECB, to remove… O’ + SECS + SECB – SECB 22
Summary The motivation of BSW The proposals to date The issues MW, Lei and Zhang No formal security model, protocols designed in ad hoc manner Current focus To continue analyse other proposals (Ju, Choi, Goi), with issues when parties collude with each others (Seller colludes with WCA etc. ) 23

Thank You
- Slides: 23