Buffer Overflows Attack Lab 1 Many of the
Buffer Overflows Attack Lab 1 Many of the following slides are based on those from Complete Powerpoint Lecture Notes for Computer Systems: A Programmer's Perspective (CS: APP) Randal E. Bryant and David R. O'Hallaron http: //www. cs. cmu. edu/afs/cs/academic/class/15213 -f 15/www/schedule. html The book is used explicitly in CS 2505 and CS 3214 and as a reference in CS 2506. CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
Agenda Attack Lab 2 Stack review Attack lab overview – – CS@VT Phases 1 -3: Buffer overflow attacks Phases 4 -5: ROP attacks Computer Organization II © 2016 CS: APP & Mc. Quain
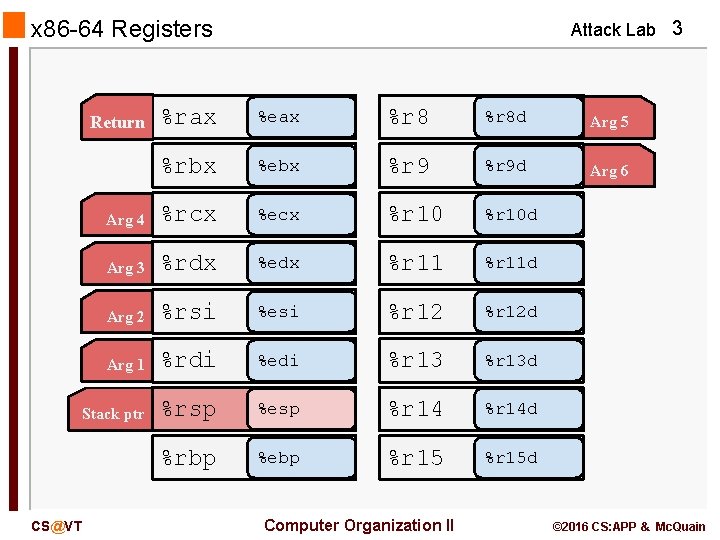
x 86 -64 Registers Attack Lab 3 %rax %eax %r 8 d Arg 5 %rbx %ebx %r 9 d Arg 6 Arg 4 %rcx %ecx %r 10 d Arg 3 %rdx %edx %r 11 d Arg 2 %rsi %esi %r 12 d Arg 1 %rdi %edi %r 13 d Stack ptr %rsp %esp %r 14 d %rbp %ebp %r 15 d Return CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
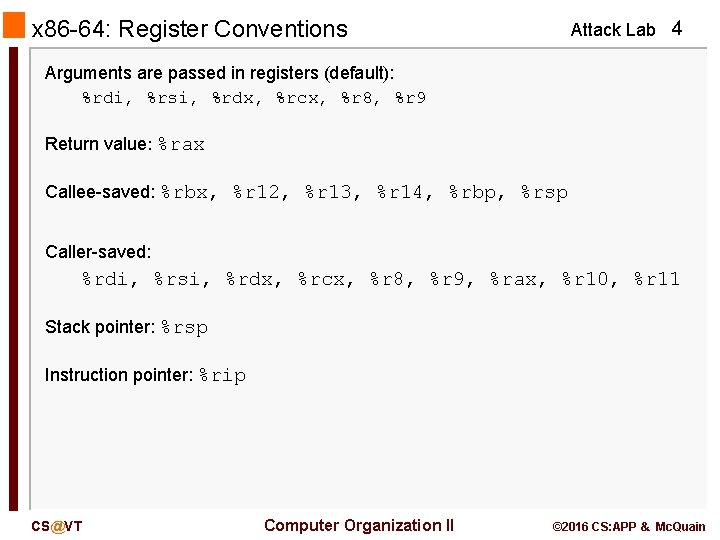
x 86 -64: Register Conventions Attack Lab 4 Arguments are passed in registers (default): %rdi, %rsi, %rdx, %rcx, %r 8, %r 9 Return value: %rax Callee-saved: %rbx, %r 12, %r 13, %r 14, %rbp, %rsp Caller-saved: %rdi, %rsi, %rdx, %rcx, %r 8, %r 9, %rax, %r 10, %r 11 Stack pointer: %rsp Instruction pointer: %rip CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
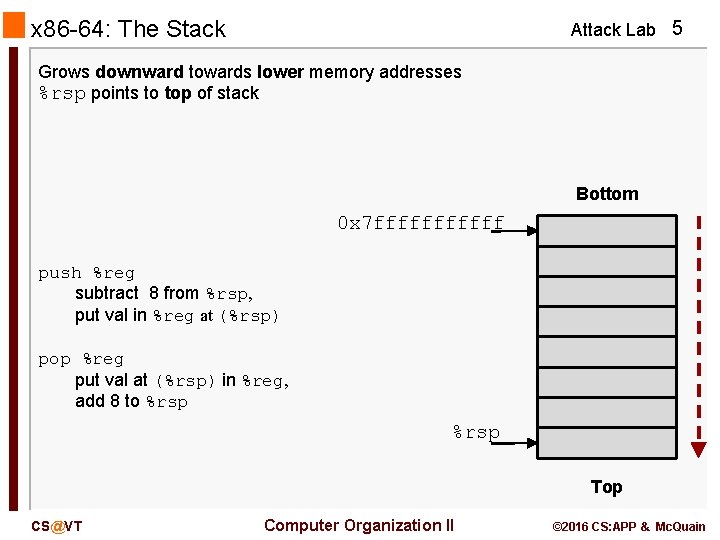
x 86 -64: The Stack Attack Lab 5 Grows downward towards lower memory addresses %rsp points to top of stack Bottom 0 x 7 ffffff push %reg subtract 8 from %rsp, put val in %reg at (%rsp) pop %reg put val at (%rsp) in %reg, add 8 to %rsp Top CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain

x 86 -64: Stack Frames Attack Lab 6 Every function call has its own stack frame. Think of a frame as a workspace for each call. - local variables - callee & caller-saved registers - optional arguments for a function call CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain

x 86 -64: Function Call Setup Attack Lab 7 Caller: - allocates stack frame large enough for saved registers, optional arguments - save any caller-saved registers in frame - save any optional arguments (in reverse order) in frame - call foo: push %rip to stack, jump to label foo Callee: - push any callee-saved registers, decrease %rsp to make room for new frame CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
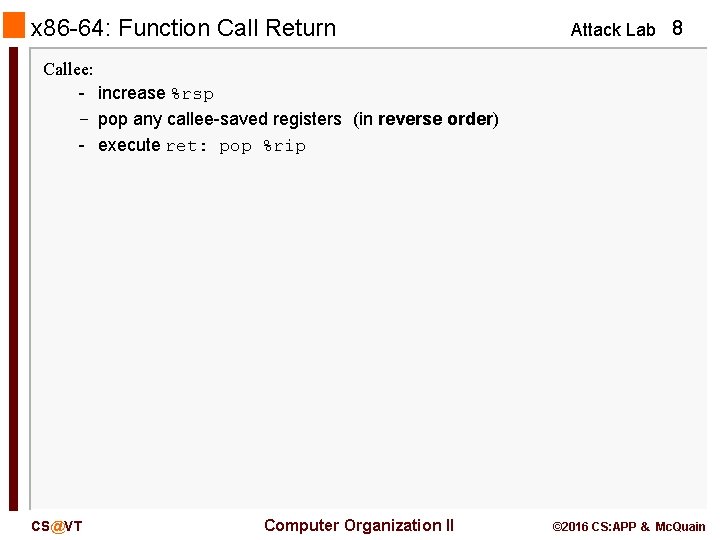
x 86 -64: Function Call Return Attack Lab 8 Callee: - increase %rsp - pop any callee-saved registers (in reverse order) - execute ret: pop %rip CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
Attack Lab Overview: Phases 1 -3 Attack Lab 9 Overview Exploit x 86 -64 by overwriting the stack Overflow a buffer, overwrite return address Execute injected code Key Advice Brush up on your x 86 -64 conventions! Use objdump –d to determine relevant offsets Use GDB to determine stack addresses CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
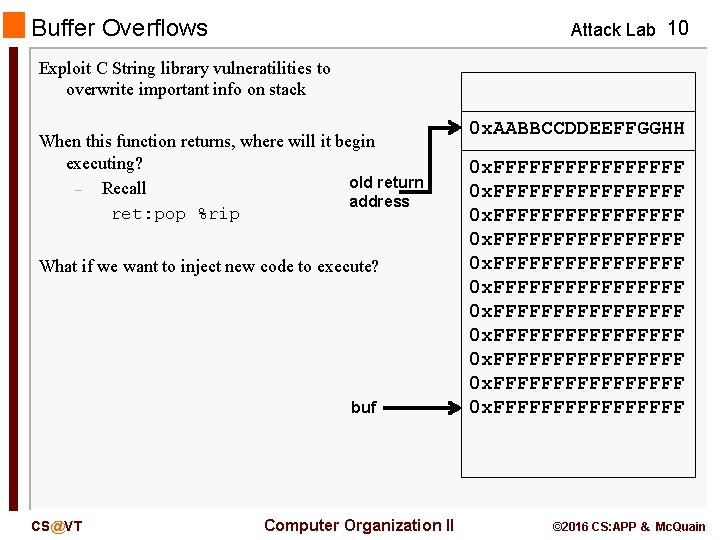
Buffer Overflows Attack Lab 10 Exploit C String library vulneratilities to overwrite important info on stack When this function returns, where will it begin executing? old return – Recall address ret: pop %rip What if we want to inject new code to execute? buf CS@VT Computer Organization II 0 x. AABBCCDDEEFFGGHH 0 x. FFFFFFFFFFFFFFFF 0 x. FFFFFFFF © 2016 CS: APP & Mc. Quain
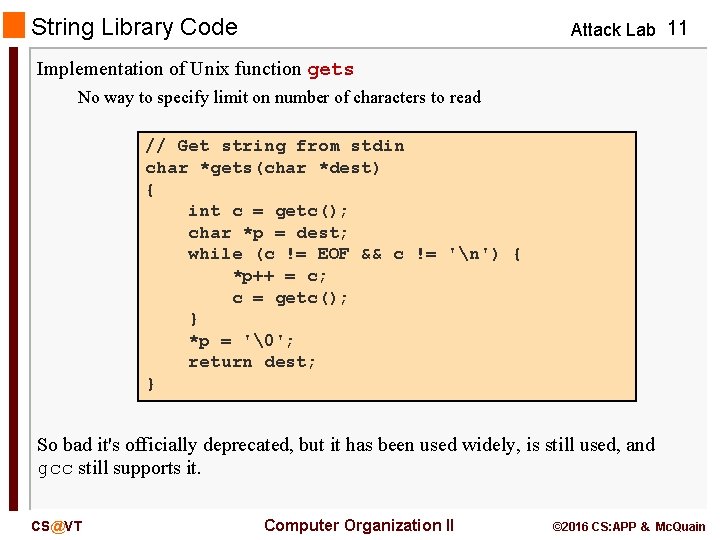
String Library Code Attack Lab 11 Implementation of Unix function gets No way to specify limit on number of characters to read // Get string from stdin char *gets(char *dest) { int c = getc(); char *p = dest; while (c != EOF && c != 'n') { *p++ = c; c = getc(); } *p = '�'; return dest; } So bad it's officially deprecated, but it has been used widely, is still used, and gcc still supports it. CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
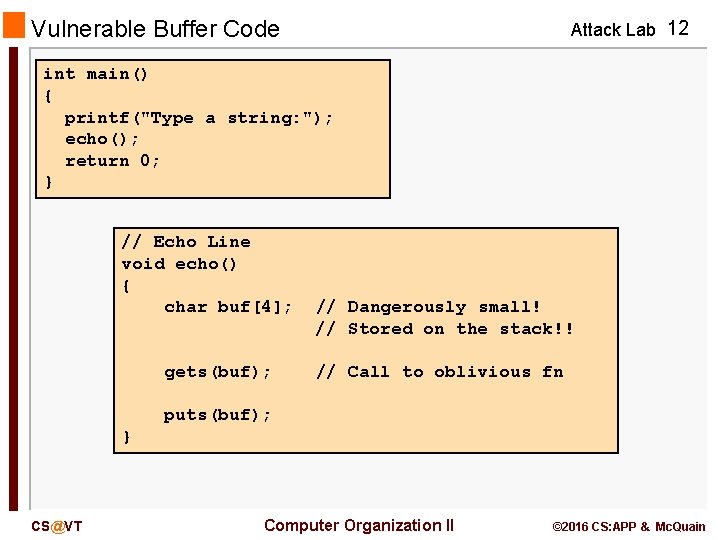
Vulnerable Buffer Code Attack Lab 12 int main() { printf("Type a string: "); echo(); return 0; } // Echo Line void echo() { char buf[4]; gets(buf); // Dangerously small! // Stored on the stack!! // Call to oblivious fn puts(buf); } CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
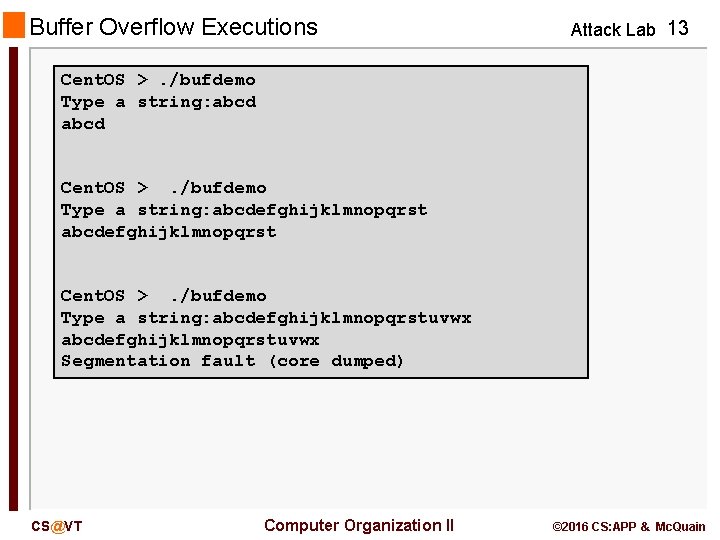
Buffer Overflow Executions Attack Lab 13 Cent. OS >. /bufdemo Type a string: abcdefghijklmnopqrst Cent. OS >. /bufdemo Type a string: abcdefghijklmnopqrstuvwx Segmentation fault (core dumped) CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
![Attack Lab 14 Buffer Overflow Stack // Echo Line void echo() { char buf[4]; Attack Lab 14 Buffer Overflow Stack // Echo Line void echo() { char buf[4];](http://slidetodoc.com/presentation_image_h2/0bb0727fcdfbd55d1cc9847f5106f75a/image-14.jpg)
Attack Lab 14 Buffer Overflow Stack // Echo Line void echo() { char buf[4]; gets(buf); puts(buf); } // Way too small! echo: pushq %rbp # setup stack movq subq %rsp, %rbp $16, %rsp frame leaq movq Stack Frame -16(%rbp), %rax # calculate buf for main %rax, %rdi # set param for Stack frame for main buf movl call. . . $0, %eax gets %rbp Saved %rip # call gets Saved %rbp buf CS@VT Computer Organization II Stack frame for echo © 2016 CS: APP & Mc. Quain
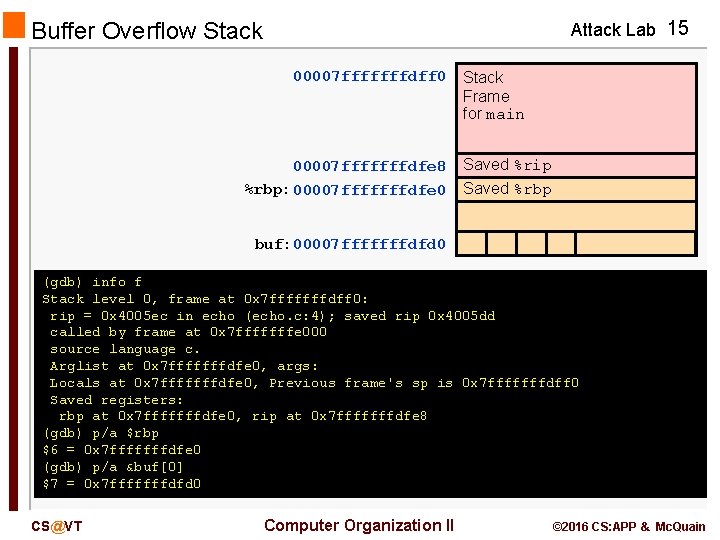
Attack Lab 15 Buffer Overflow Stack 00007 fffffffdff 0 00007 fffffffdfe 8 %rbp: 00007 fffffffdfe 0 Stack Frame for main Saved %rip Saved %rbp buf: 00007 fffffffdfd 0 (gdb) info f Stack level 0, frame at 0 x 7 fffffffdff 0: rip = 0 x 4005 ec in echo (echo. c: 4); saved rip 0 x 4005 dd called by frame at 0 x 7 fffffffe 000 source language c. Arglist at 0 x 7 fffffffdfe 0, args: Locals at 0 x 7 fffffffdfe 0, Previous frame's sp is 0 x 7 fffffffdff 0 Saved registers: rbp at 0 x 7 fffffffdfe 0, rip at 0 x 7 fffffffdfe 8 (gdb) p/a $rbp $6 = 0 x 7 fffffffdfe 0 (gdb) p/a &buf[0] $7 = 0 x 7 fffffffdfd 0 CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
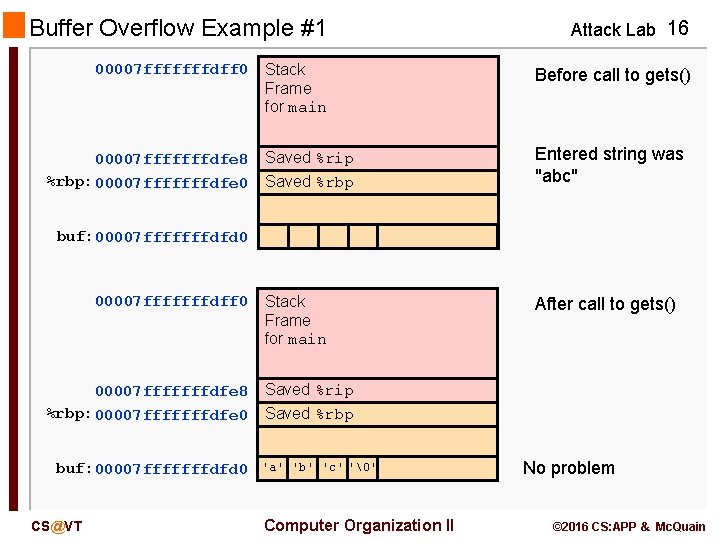
Buffer Overflow Example #1 00007 fffffffdff 0 00007 fffffffdfe 8 %rbp: 00007 fffffffdfe 0 Attack Lab 16 Stack Frame for main Before call to gets() Saved %rip Saved %rbp Entered string was "abc" Stack Frame for main After call to gets() buf: 00007 fffffffdfd 0 00007 fffffffdff 0 00007 fffffffdfe 8 %rbp: 00007 fffffffdfe 0 buf: 00007 fffffffdfd 0 CS@VT Saved %rip Saved %rbp 'a' 'b' 'c' '�' Computer Organization II No problem © 2016 CS: APP & Mc. Quain
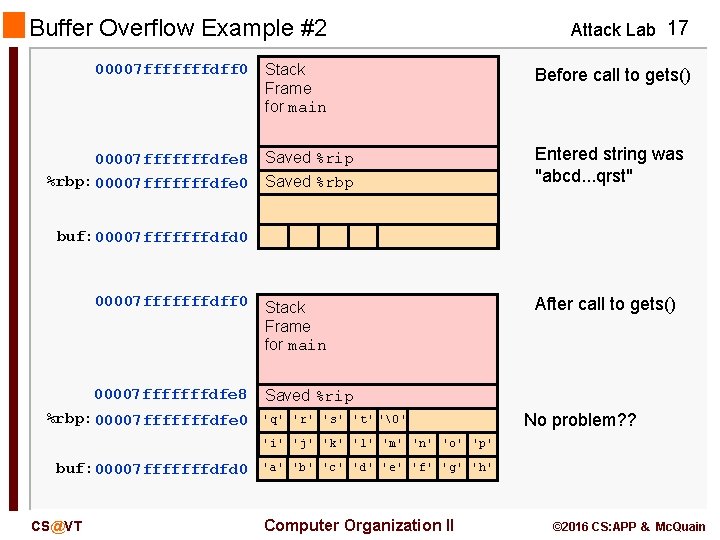
Buffer Overflow Example #2 00007 fffffffdff 0 Attack Lab 17 Stack Frame for main Before call to gets() Saved %rip Saved %rbp Entered string was "abcd. . . qrst" 00007 fffffffdff 0 Stack Frame for main After call to gets() 00007 fffffffdfe 8 Saved %rip 00007 fffffffdfe 8 %rbp: 00007 fffffffdfe 0 buf: 00007 fffffffdfd 0 %rbp: 00007 fffffffdfe 0 'q' 'r' 's' 't' '�' No problem? ? 'i' 'j' 'k' 'l' 'm' 'n' 'o' 'p' buf: 00007 fffffffdfd 0 CS@VT 'a' 'b' 'c' 'd' 'e' 'f' 'g' 'h' Computer Organization II © 2016 CS: APP & Mc. Quain
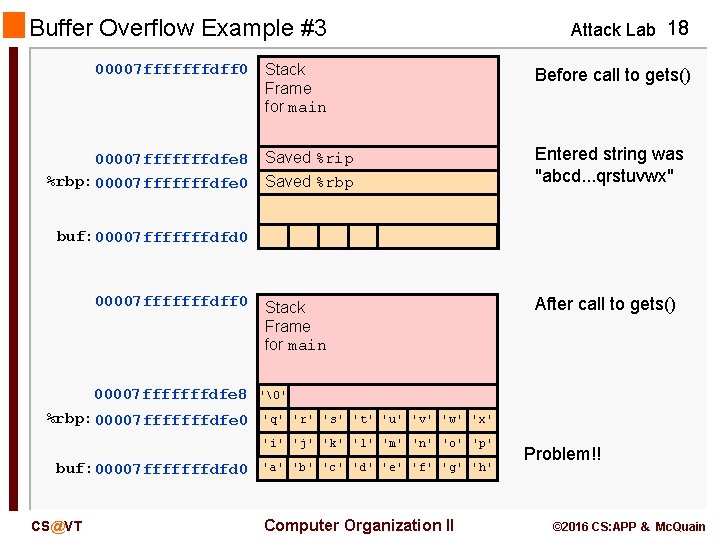
Buffer Overflow Example #3 00007 fffffffdff 0 00007 fffffffdfe 8 %rbp: 00007 fffffffdfe 0 Attack Lab 18 Stack Frame for main Before call to gets() Saved %rip Saved %rbp Entered string was "abcd. . . qrstuvwx" Stack Frame for main After call to gets() buf: 00007 fffffffdfd 0 00007 fffffffdff 0 00007 fffffffdfe 8 %rbp: 00007 fffffffdfe 0 '�' 'q' 'r' 's' 't' 'u' 'v' 'w' 'x' 'i' 'j' 'k' 'l' 'm' 'n' 'o' 'p' buf: 00007 fffffffdfd 0 CS@VT 'a' 'b' 'c' 'd' 'e' 'f' 'g' 'h' Computer Organization II Problem!! © 2016 CS: APP & Mc. Quain
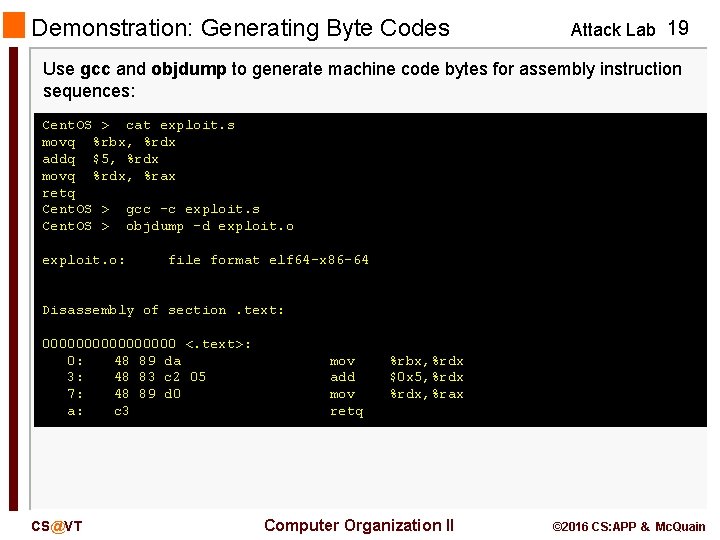
Demonstration: Generating Byte Codes Attack Lab 19 Use gcc and objdump to generate machine code bytes for assembly instruction sequences: Cent. OS > cat exploit. s movq %rbx, %rdx addq $5, %rdx movq %rdx, %rax retq Cent. OS > gcc -c exploit. s Cent. OS > objdump -d exploit. o: file format elf 64 -x 86 -64 Disassembly of section. text: 00000000 <. text>: 0: 48 89 da 3: 48 83 c 2 05 7: 48 89 d 0 a: c 3 CS@VT mov add mov retq %rbx, %rdx $0 x 5, %rdx, %rax Computer Organization II © 2016 CS: APP & Mc. Quain
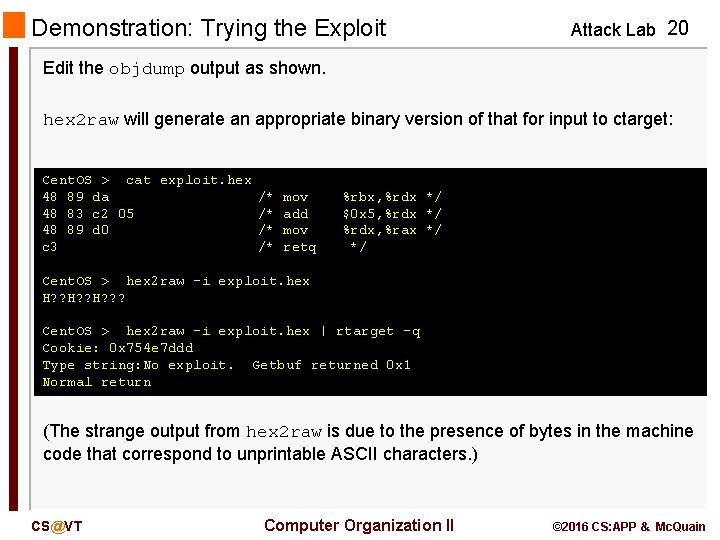
Demonstration: Trying the Exploit Attack Lab 20 Edit the objdump output as shown. hex 2 raw will generate an appropriate binary version of that for input to ctarget: Cent. OS > cat exploit. hex 48 89 da /* mov 48 83 c 2 05 /* add 48 89 d 0 /* mov c 3 /* retq %rbx, %rdx */ $0 x 5, %rdx */ %rdx, %rax */ */ Cent. OS > hex 2 raw -i exploit. hex H? ? ? Cent. OS > hex 2 raw -i exploit. hex | rtarget -q Cookie: 0 x 754 e 7 ddd Type string: No exploit. Getbuf returned 0 x 1 Normal return (The strange output from hex 2 raw is due to the presence of bytes in the machine code that correspond to unprintable ASCII characters. ) CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain

Attack Lab Overview: Phases 4 -5 Attack Lab 21 Overview Utilize return-oriented programming to execute arbitrary code Useful when stack is non-executable or randomized Find gadgets, string together to form injected code Key Advice - Use mixture of pop & mov instructions + constants to perform specific task CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
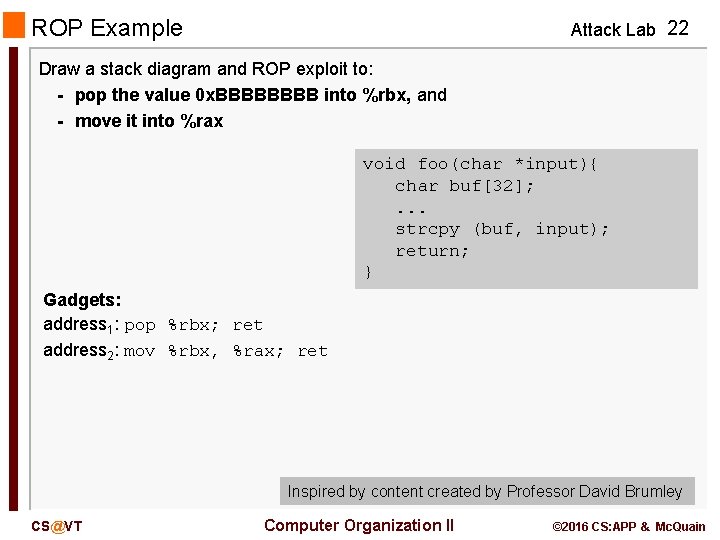
ROP Example Attack Lab 22 Draw a stack diagram and ROP exploit to: - pop the value 0 x. BBBB into %rbx, and - move it into %rax void foo(char *input){ char buf[32]; . . . strcpy (buf, input); return; } Gadgets: address 1: pop %rbx; ret address 2: mov %rbx, %rax; ret Inspired by content created by Professor David Brumley CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
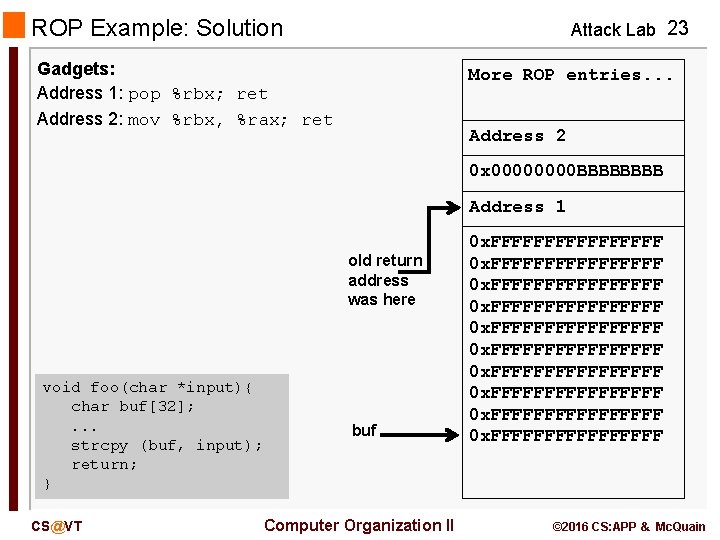
ROP Example: Solution Attack Lab 23 Gadgets: Address 1: pop %rbx; ret Address 2: mov %rbx, %rax; ret More ROP entries. . . Address 2 0 x 0000 BBBB Address 1 old return address was here void foo(char *input){ char buf[32]; . . . strcpy (buf, input); return; } CS@VT buf Computer Organization II 0 x. FFFFFFFFFFFFFFFF 0 x. FFFFFFFFFFFFFFFF © 2016 CS: APP & Mc. Quain
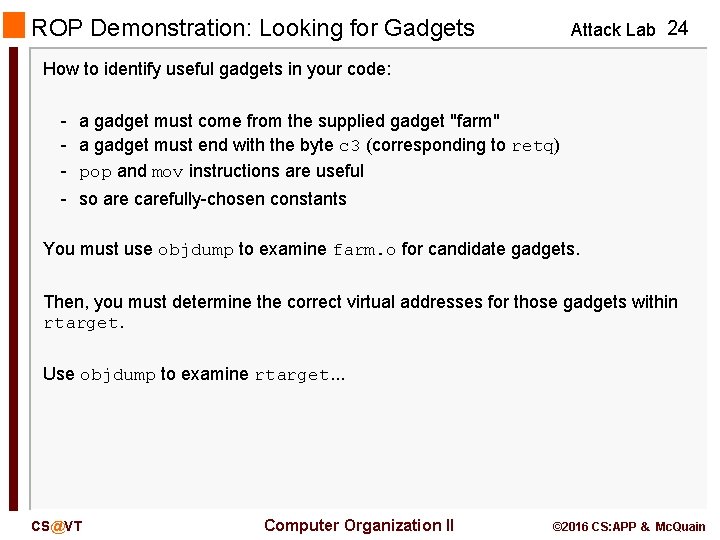
ROP Demonstration: Looking for Gadgets Attack Lab 24 How to identify useful gadgets in your code: - a gadget must come from the supplied gadget "farm" - a gadget must end with the byte c 3 (corresponding to retq) - pop and mov instructions are useful - so are carefully-chosen constants You must use objdump to examine farm. o for candidate gadgets. Then, you must determine the correct virtual addresses for those gadgets within rtarget. Use objdump to examine rtarget. . . CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
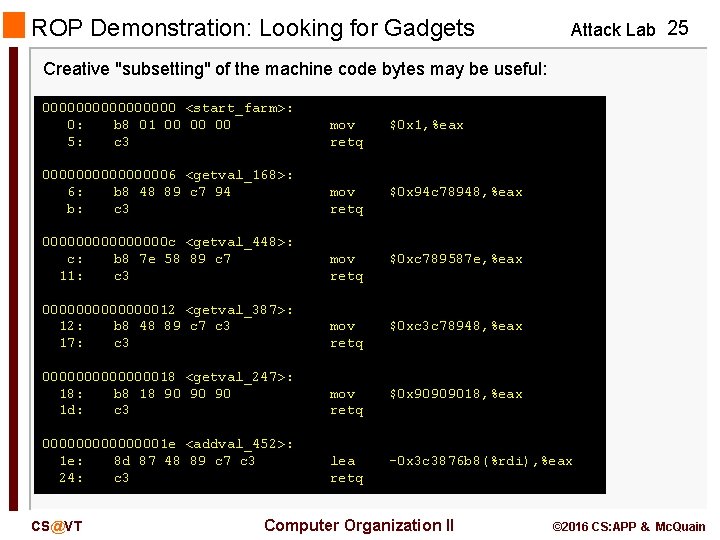
ROP Demonstration: Looking for Gadgets Attack Lab 25 Creative "subsetting" of the machine code bytes may be useful: 00000000 <start_farm>: 0: b 8 01 00 00 00 5: c 3 mov retq $0 x 1, %eax 000000006 <getval_168>: 6: b 8 48 89 c 7 94 b: c 3 mov retq $0 x 94 c 78948, %eax 00000000 c <getval_448>: c: b 8 7 e 58 89 c 7 11: c 3 mov retq $0 xc 789587 e, %eax 000000012 <getval_387>: 12: b 8 48 89 c 7 c 3 17: c 3 mov retq $0 xc 3 c 78948, %eax 000000018 <getval_247>: 18: b 8 18 90 90 90 1 d: c 3 mov retq $0 x 90909018, %eax 00000001 e <addval_452>: 1 e: 8 d 87 48 89 c 7 c 3 24: c 3 lea retq -0 x 3 c 3876 b 8(%rdi), %eax CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
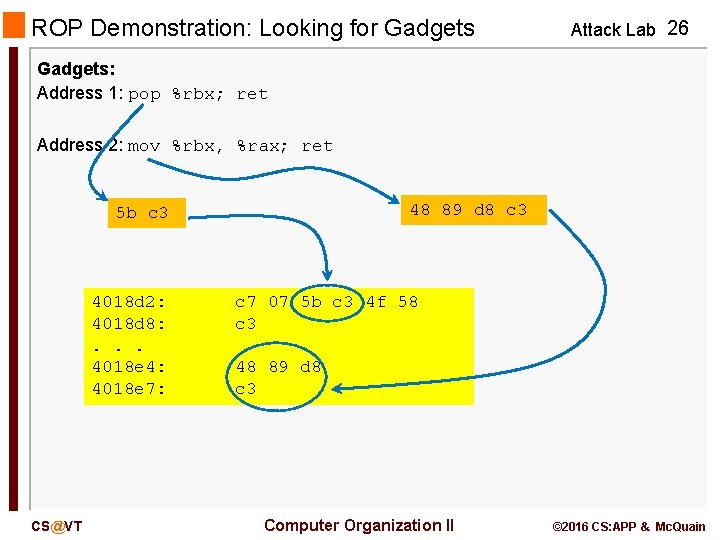
ROP Demonstration: Looking for Gadgets Attack Lab 26 Gadgets: Address 1: pop %rbx; ret Address 2: mov %rbx, %rax; ret 48 89 d 8 c 3 5 b c 3 4018 d 2: 4018 d 8: . . . 4018 e 4: 4018 e 7: CS@VT c 7 07 5 b c 3 4 f 58 c 3 48 89 d 8 c 3 Computer Organization II © 2016 CS: APP & Mc. Quain

Tools Attack Lab 27 objdump –d – View byte code and assembly instructions, determine stack offsets . /hex 2 raw – Pass raw ASCII strings to targets gdb – Step through execution, determine stack addresses gcc –c – CS@VT Generate object file from assembly language file Computer Organization II © 2016 CS: APP & Mc. Quain
More Tips Attack Lab 28 Draw stack diagrams Be careful of byte ordering (little endian) READ the assignment specification! A video presentation of CMU's version is available as Recitation 5 at the link below: https: //scs. hosted. panopto. com/Panopto/Pages/Viewer. aspx? id=60 c 65748 -2026 -463 f-8 c 57134 fd 6661 cdf CS@VT Computer Organization II © 2016 CS: APP & Mc. Quain
- Slides: 28