Brief introduction to group and role based access

Brief introduction to group and role based access control rule and evaluation Group Name: WG 2/WG 4 Source: Wei Zhou, CATT, zhouwei@catt. cn Meeting Date: <yyyy-mm-dd> Agenda Item: <agenda item topic name>
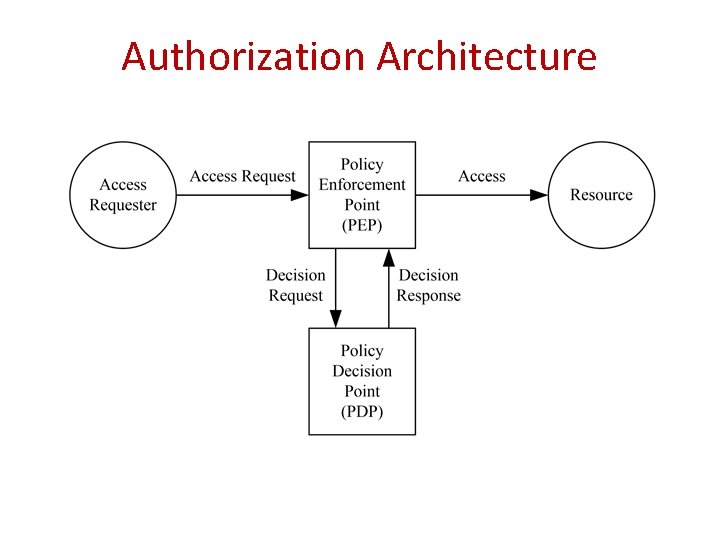
Authorization Architecture
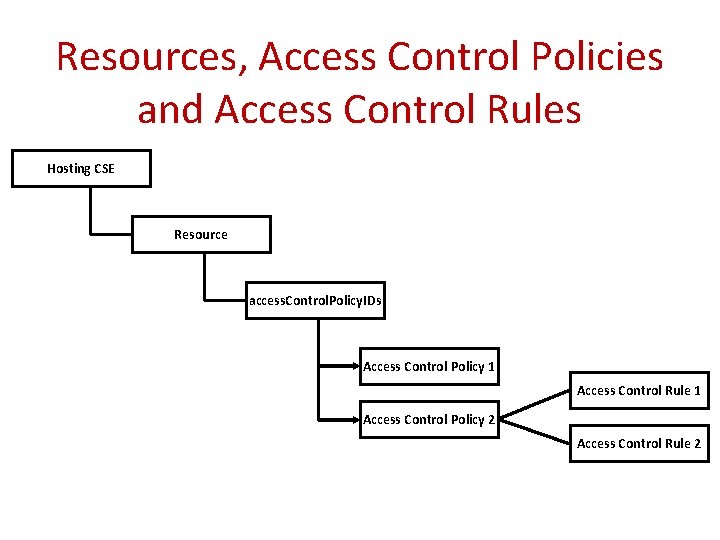
Resources, Access Control Policies and Access Control Rules Hosting CSE Resource access. Control. Policy. IDs Access Control Policy 1 Access Control Rule 1 Access Control Policy 2 Access Control Rule 2
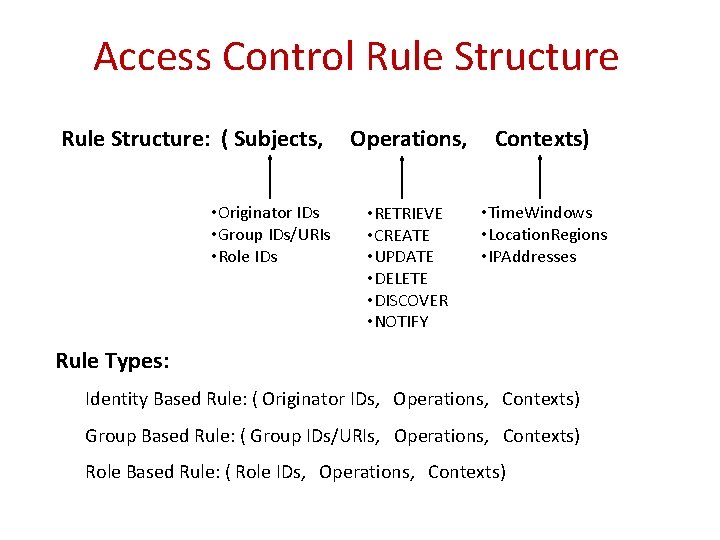
Access Control Rule Structure: ( Subjects, • Originator IDs • Group IDs/URIs • Role IDs Operations, Contexts) • RETRIEVE • CREATE • UPDATE • DELETE • DISCOVER • NOTIFY • Time. Windows • Location. Regions • IPAddresses Rule Types: Identity Based Rule: ( Originator IDs, Operations, Contexts) Group Based Rule: ( Group IDs/URIs, Operations, Contexts) Role Based Rule: ( Role IDs, Operations, Contexts)
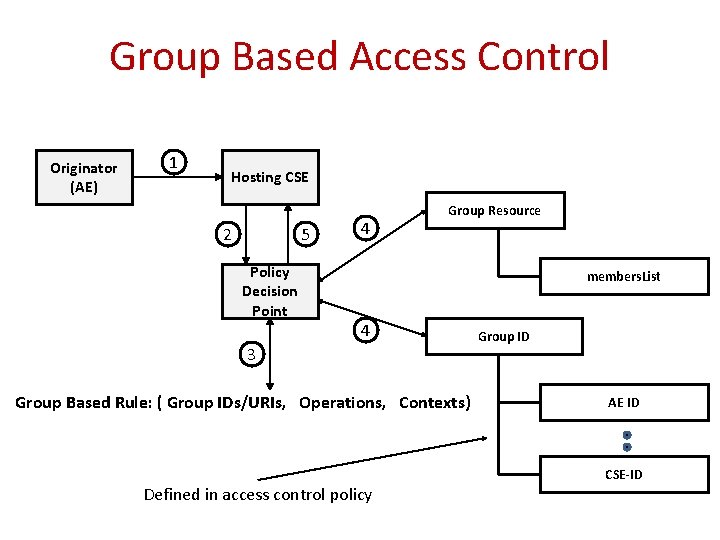
Group Based Access Control Originator (AE) 1 Hosting CSE 2 5 Policy Decision Point 4 Group Resource members. List 4 3 Group Based Rule: ( Group IDs/URIs, Operations, Contexts) Group ID AE ID CSE-ID Defined in access control policy
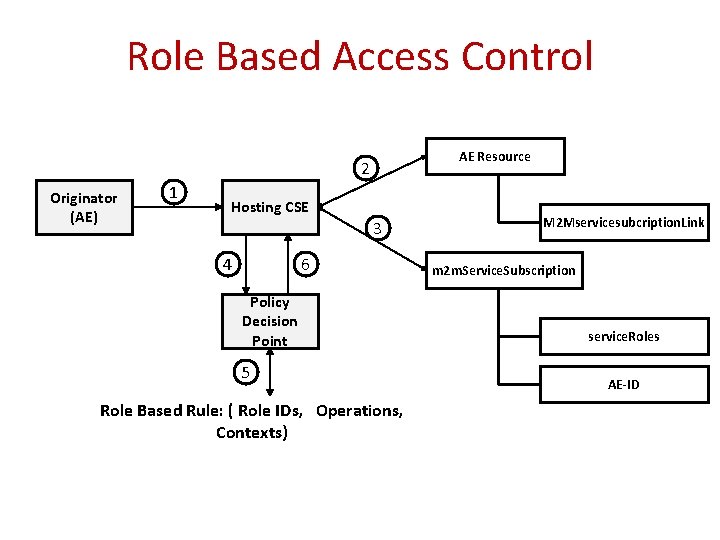
Role Based Access Control AE Resource 2 Originator (AE) 1 Hosting CSE 3 4 6 Policy Decision Point 5 Role Based Rule: ( Role IDs, Operations, Contexts) M 2 Mservicesubcription. Link m 2 m. Service. Subscription service. Roles AE-ID
- Slides: 6