Breaking with traditional OS abstraction Anjo VahldiekOberwagner Researcher

Breaking with traditional OS abstraction Anjo Vahldiek-Oberwagner Researcher at Intel Labs

2 Legal Disclaimers Intel provides these materials as-is, with no express or implied warranties. All products, dates, and figures specified are preliminary, based on current expectations, and are subject to change without notice. Intel processors, chipsets, and desktop boards may contain design defects or errors known as errata, which may cause the product to deviate from published specifications. Current characterized errata are available on request. Intel technologies' features and benefits depend on system configuration and may require enabled hardware, software or service activation. Performance varies depending on system configuration. No product or component can be absolutely secure. Check with your system manufacturer or retailer or learn more at http: //intel. com. Some results have been estimated or simulated using internal Intel analysis or architecture simulation or modeling and provided to you for informational purposes. Any differences in your system hardware, software or configuration may affect your actual performance. Intel and the Intel logo are trademarks of Intel Corporation in the United States and other countries. *Other names and brands may be claimed as the property of others. © Intel Corporation 2021 IIT KPG OS Lecture 2
Who am I? § Interested in full stack security (from hardware to application) § Researcher at Intel Labs in Datacenter Security group • Confidential Computing for datacenter workloads • Emerging uses of fine-grained in-process isolation § Ph. D at MPI-SWS • Design, build, evaluate software systems (with focus on system security) • Policy-compliance of data storage and data retrieval systems • In-process isolation IIT KPG OS Lecture 3
What OS abstractions did you learn about? ? IIT KPG OS Lecture 4
Why these abstractions? IIT KPG OS Lecture 5

History of OS abstractions § Abstractions based on HW • HDD/tapes • Multi-user interface § Portable Operating System Interface (POSIX) started in 1988 § Focus on: • Multiplex resources • Isolate programs into fault domains • Std. In/Out IIT KPG OS Lecture 6
Where did the Compute move to? IIT KPG OS Lecture 7
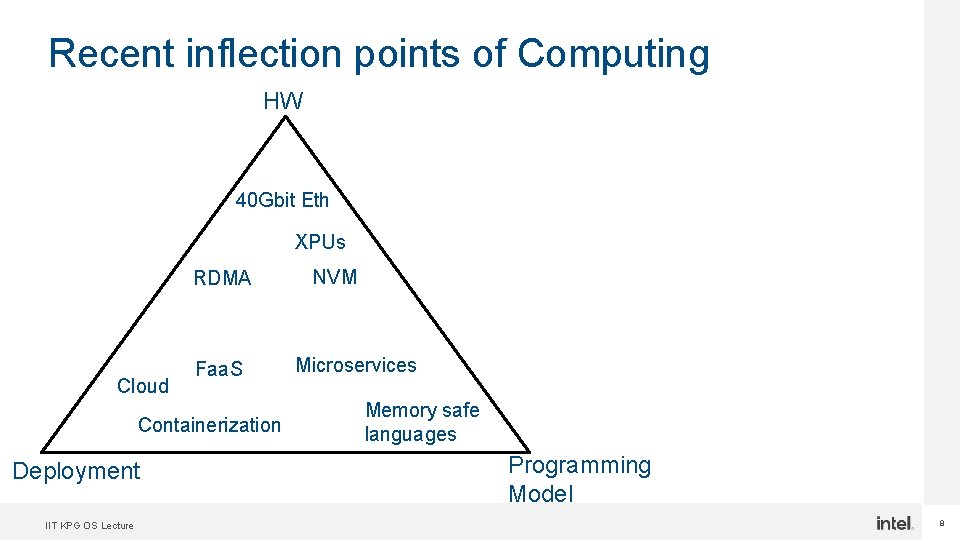
Recent inflection points of Computing HW 40 Gbit Eth XPUs RDMA Cloud Faa. S Containerization Deployment IIT KPG OS Lecture NVM Microservices Memory safe languages Programming Model 8
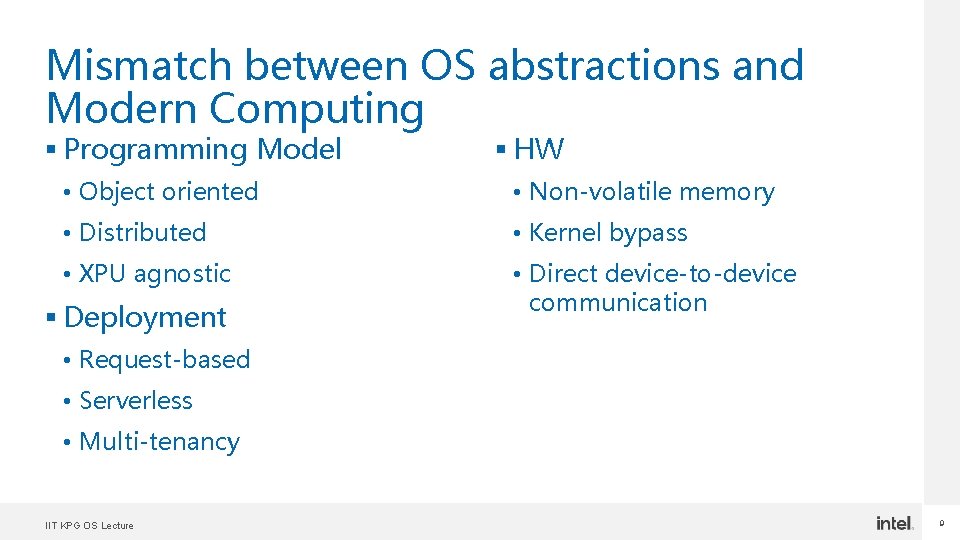
Mismatch between OS abstractions and Modern Computing § Programming Model § HW • Object oriented • Non-volatile memory • Distributed • Kernel bypass • XPU agnostic • Direct device-to-device communication § Deployment • Request-based • Serverless • Multi-tenancy IIT KPG OS Lecture 9

How do we know OS abstractions are good? IIT KPG OS Lecture 10

Ask yourself § Are these abstractions easy to use? § Can they be implemented efficiently? § Can they be efficiently used? § Do they encourage simplicity in programs? § Are they flexible? § Are they complete? IIT KPG OS Lecture 11
Rethinking OS abstractions … IIT KPG OS Lecture 12

Breaking with the traditional OS Abstractions § Programming model & Deployment • System Calls should be focused on application needs • Do we need modularity for different applications? § Improved HW performance • Do we need process boundaries to improve memory sharing and device access? • Privilege levels/Rings? IIT KPG OS Lecture 13

Suggestion: A Cloud-Native OS § Reconsider Single Address-Space OSes • No ring transitions • Enables sharing between services • Fast access to XPUs § Modular set of abstractions • Provides access to distributed objects • POSIX Abstraction layer for legacy applications IIT KPG OS Lecture 14
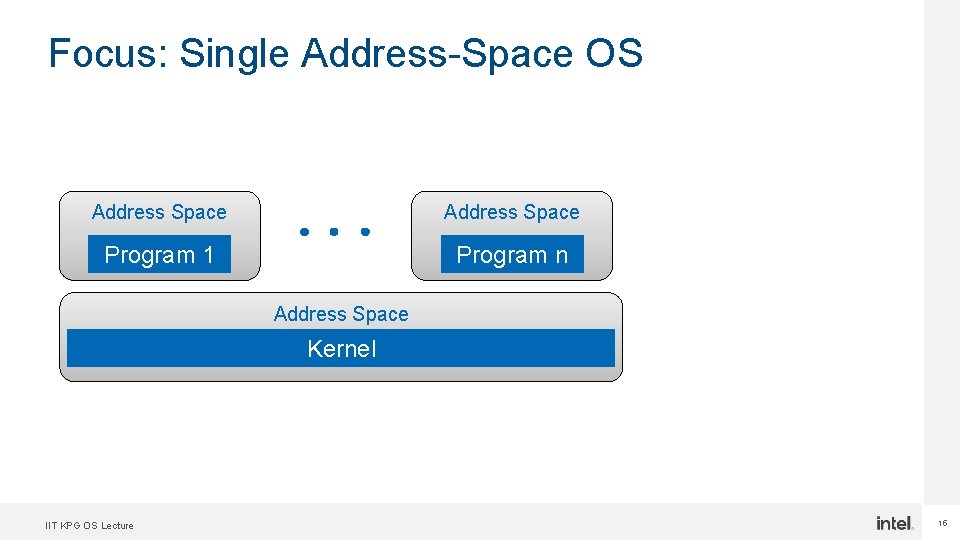
Focus: Single Address-Space OS Address Space Program 1 Program n Address Space Kernel IIT KPG OS Lecture 15

Overload of Address-Space/Page-tables § Security boundary (e. g. , for side-channels) § Memory permissions § Virtualize memory • Paging • Memory-mapped files • Virtual to physical mapping § Privileged instruction capabilities IIT KPG OS Lecture 16

Focus: Single Address-Space OS Address Space Service 1 Service n Serverless/Microservice Framework Kernel IIT KPG OS Lecture 17

Overload of Address-Space/Page-tables § Security boundary (e. g. , for side-channels) § Memory permissions § Virtualize memory • Paging • Deep/large tables for virtual to physical mapping § Privileged instruction capabilities IIT KPG OS Lecture 18

Opportunities of SAOS § Shared data between services § Fast communication/invocation of components § Less costly transitions/system calls § Direct access to kernel memory/devices IIT KPG OS Lecture 19

Downsides of SAOS § Security • Side-channels on today’s HW • Failure domains • Memory corruption § Need replacements for • virtual memory • memory permissions • privileged instructions IIT KPG OS Lecture 20
Regaining Security § Simplified page tables for virtual memory § Memory capabilities • Memory-safe language or runtime • Compiler enforced access of memory to predefined region/objects • Flexibly extend capabilities to access memory regions § Instruction capabilities • Enforce control flow • Entrypoints of components • Disallow arbitrary jumps within programs • Compiler enforced limited set of instructions IIT KPG OS Lecture 21

Summary § What makes a good OS abstraction? § Constantly consider inflection points in HW, deployment, and programming models. § Evaluate existing OS abstractions and rethink alternatives. IIT KPG OS Lecture 22
Questions? ? https: //vahldiek. github. io IIT KPG OS Lecture 23
- Slides: 23