Breaking The Cyber Attack Lifecycle Every Step Jamel

Breaking The Cyber Attack Lifecycle @ Every Step Jamel Lassoued Senior Systems Engineer Jlassoued@paloaltonetworks. com
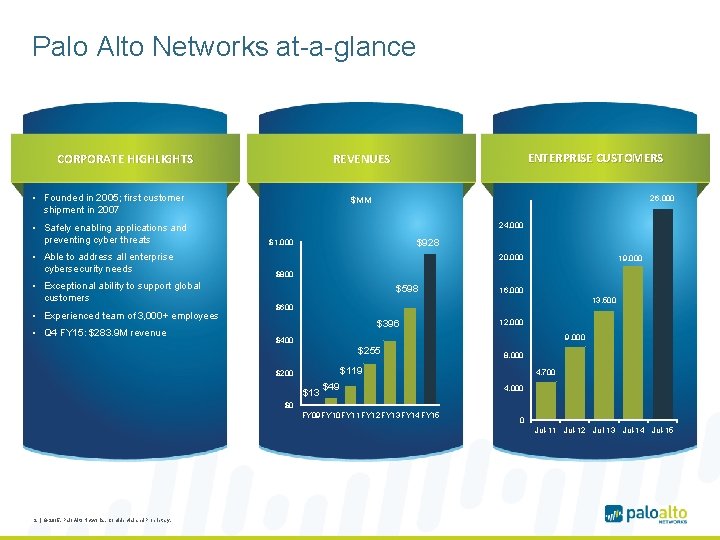
Palo Alto Networks at-a-glance CORPORATE HIGHLIGHTS • Founded in 2005; first customer shipment in 2007 • Safely enabling applications and preventing cyber threats • Able to address all enterprise cybersecurity needs • Exceptional ability to support global customers • Experienced team of 3, 000+ employees • Q 4 FY 15: $283. 9 M revenue ENTERPRISE CUSTOMERS REVENUES 26, 000 $MM 24, 000 $928 $1, 000 20, 000 19, 000 $800 $598 16, 000 13, 500 $600 $396 12, 000 9, 000 $400 $255 8, 000 $119 $200 $13 $49 4, 700 4, 000 $0 FY 09 FY 10 FY 11 FY 12 FY 13 FY 14 FY 15 0 Jul-11 Jul-12 Jul-13 Jul-14 Jul-15 2 | © 2015, Palo Alto Networks. Confidential and Proprietary.

Palo Alto Networks : la reconnaissance du marché 3 | © 2016, Palo Alto Networks. Confidential and Proprietary.
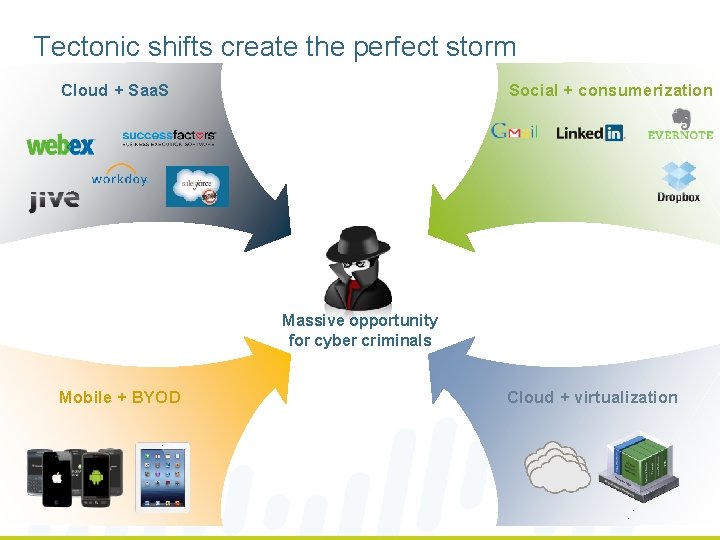
Tectonic shifts create the perfect storm Cloud + Saa. S Social + consumerization Massive opportunity for cyber criminals Mobile + BYOD Cloud + virtualization
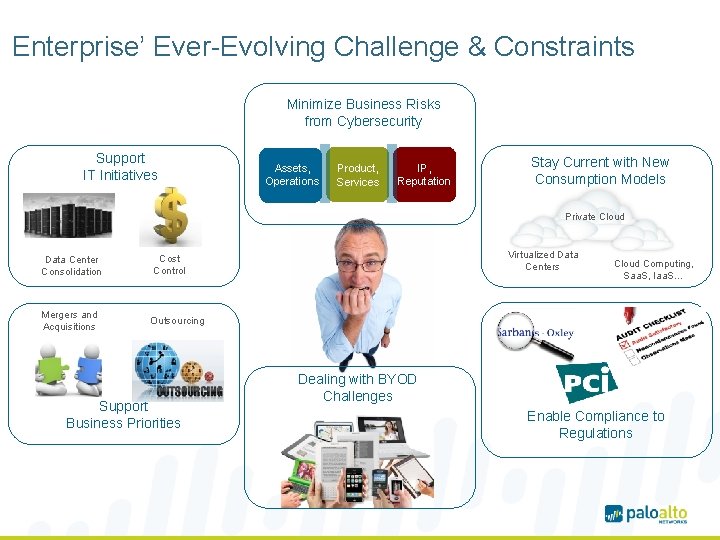
Enterprise’ Ever-Evolving Challenge & Constraints Minimize Business Risks from Cybersecurity Support IT Initiatives Assets, Operations Product, Services IP, Reputation Stay Current with New Consumption Models Private Cloud Data Center Consolidation Mergers and Acquisitions Virtualized Data Centers Cost Control Cloud Computing, Saa. S, Iaa. S… Outsourcing Support Business Priorities Dealing with BYOD Challenges Enable Compliance to Regulations
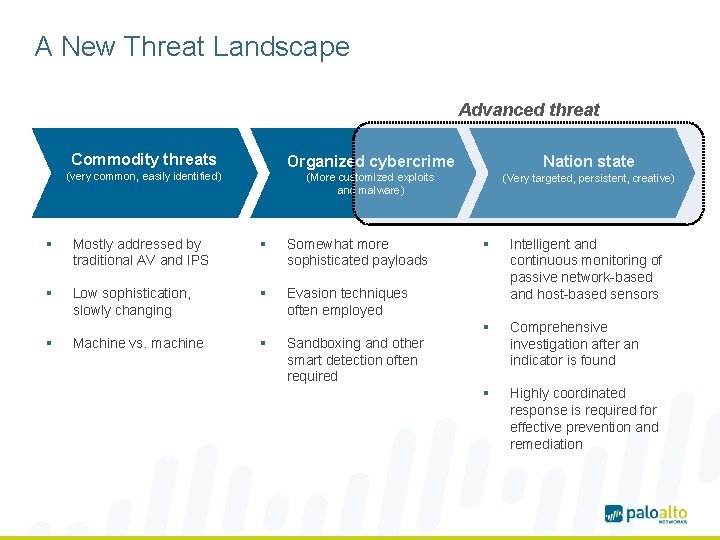
A New Threat Landscape Advanced threat Commodity threats (very common, easily identified) Organized cybercrime Nation state (More customized exploits and malware) (Very targeted, persistent, creative) § Mostly addressed by traditional AV and IPS § Somewhat more sophisticated payloads § Low sophistication, slowly changing § Evasion techniques often employed § Machine vs. machine § § Intelligent and continuous monitoring of passive network-based and host-based sensors § Comprehensive investigation after an indicator is found § Highly coordinated response is required for effective prevention and remediation Sandboxing and other smart detection often required
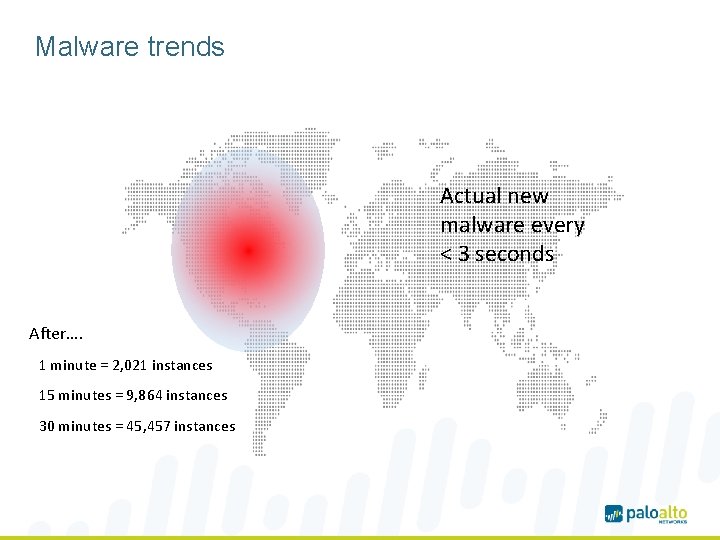
Malware trends Actual new malware every < 3 seconds After…. 1 minute = 2, 021 instances 15 minutes = 9, 864 instances 30 minutes = 45, 457 instances

Today Security Infrastructure… Best of Breed Products § Staffing and time to market § Operations § Accuracy Internet FW Network Your investment in SIEM for normalisation of disparate solutions or as strategic asset to help break the Attack Lifecycle?

The Cyber attack Lifecycle Gather intelligence Plan the attack Exploit Deliver malware C 2 Steal data Silent infection Malicious file delivered Malware communicates with attacker High-value intellectual property stolen

Breaking the Attack Lifecycle at Multiple Points 1. Segment your network with a “zero-trust” model as the foundation for defense § Only allow content to be accessed § By a limited and identifiable set of users § Through a well-defined set of applications § Blocking everything else 2. Block all known threats: § Threat Prevention would have identified and stopped parts of the attack § Across known vulnerability exploits, malware, URLs, DNS queries § And command-control activity 3. Identify and block all unknown threats: § Using the Sandboxing Solution § Using Behavioral characteristics such as § § Communicating over often-abused ports (139 or 445) Using Web. Dev to share information, Changing the security settings of Internet Explorer Modifying Windows registries and many more 10 | © 2013, Palo Alto Networks. Confidential and Proprietary.
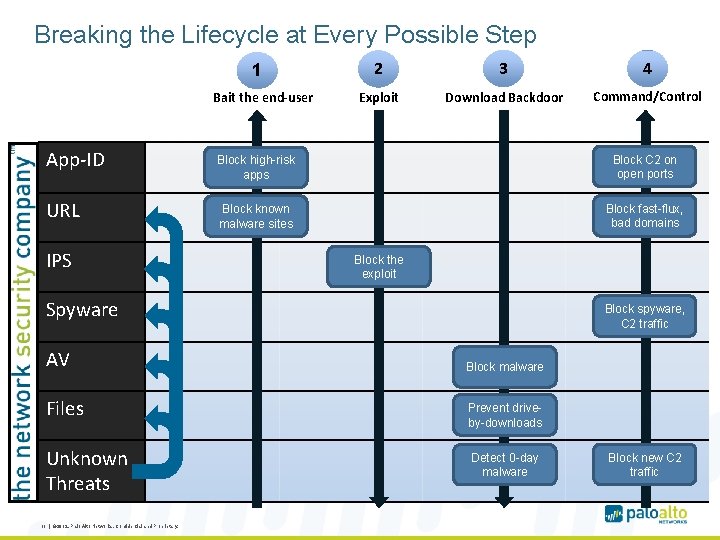
Breaking the Lifecycle at Every Possible Step 1 Bait the end-user App-ID URL IPS 2 3 4 Exploit Download Backdoor Command/Control Block high-risk apps Block C 2 on open ports Block known malware sites Block fast-flux, bad domains Block the exploit Spyware AV Files Unknown Threats 11 | © 2012, Palo Alto Networks. Confidential and Proprietary. Block spyware, C 2 traffic Block malware Prevent driveby-downloads Detect 0 -day malware Block new C 2 traffic
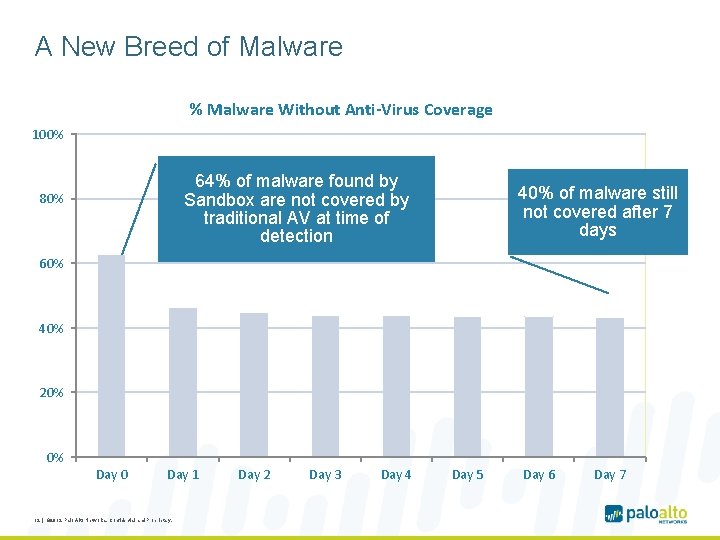
A New Breed of Malware % Malware Without Anti-Virus Coverage 100% 64% of malware found by Sandbox are not covered by traditional AV at time of detection 80% 40% of malware still not covered after 7 days 60% 40% 20% 0% Day 0 Day 1 12 | © 2012, Palo Alto Networks. Confidential and Proprietary. Day 2 Day 3 Day 4 Day 5 Day 6 Day 7
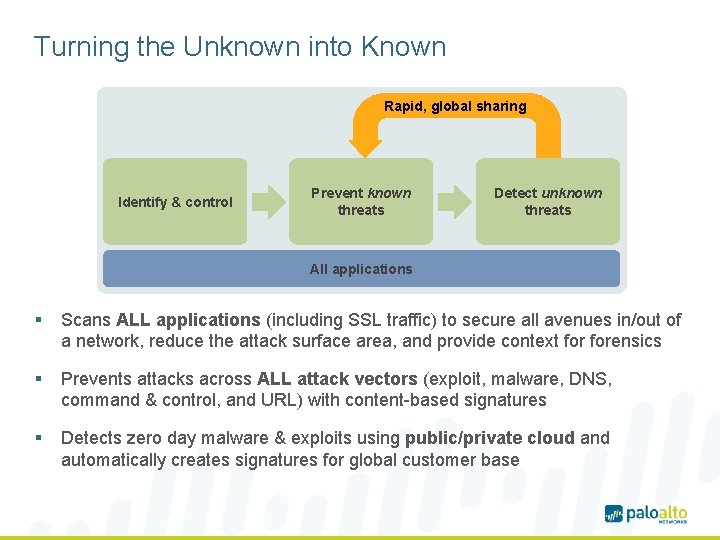
Turning the Unknown into Known Rapid, global sharing Identify & control Prevent known threats Detect unknown threats All applications § Scans ALL applications (including SSL traffic) to secure all avenues in/out of a network, reduce the attack surface area, and provide context forensics § Prevents attacks across ALL attack vectors (exploit, malware, DNS, command & control, and URL) with content-based signatures § Detects zero day malware & exploits using public/private cloud and automatically creates signatures for global customer base
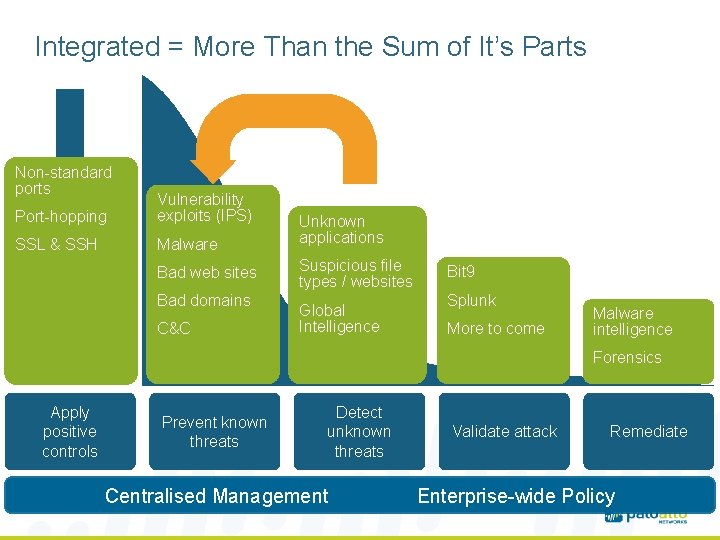
Integrated = More Than the Sum of It’s Parts Non-standard ports Port-hopping Attack Vulnerability exploits (IPS) surface SSL & SSH Malware Bad web sites Bad domains C&C Unknown applications Suspicious file types / websites Global Intelligence Bit 9 Splunk More to come Malware intelligence Forensics Apply positive controls Prevent known threats Detect unknown threats Validate attack Remediate Centralised Management Enterprise-wide Policy

Summary § Evolution of your Network Security § It’s a new Threat Landscape § Need for an integrated approach § Traditional solutions no longer suffice § Focus on breaking the Attack Lifecycle, not just on the pointattack 15 | © 2013, Palo Alto Networks. Confidential and Proprietary.

16 | © 2012, Palo Alto Networks. Confidential and Proprietary.
- Slides: 16