Breaking and Fixing Authentication over TLS Reporter Pan

Breaking and Fixing Authentication over TLS Reporter: Pan Hao
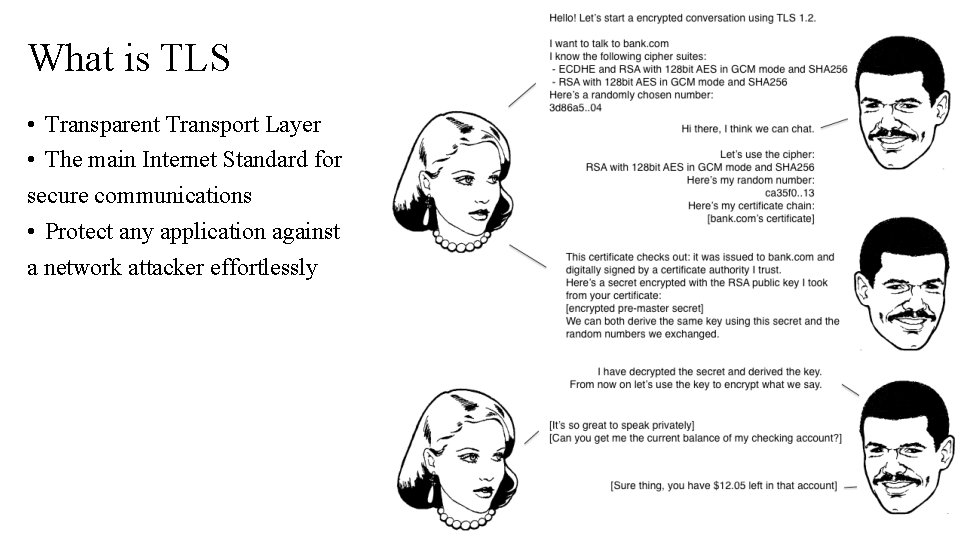
What is TLS • Transparent Transport Layer • The main Internet Standard for secure communications • Protect any application against a network attacker effortlessly
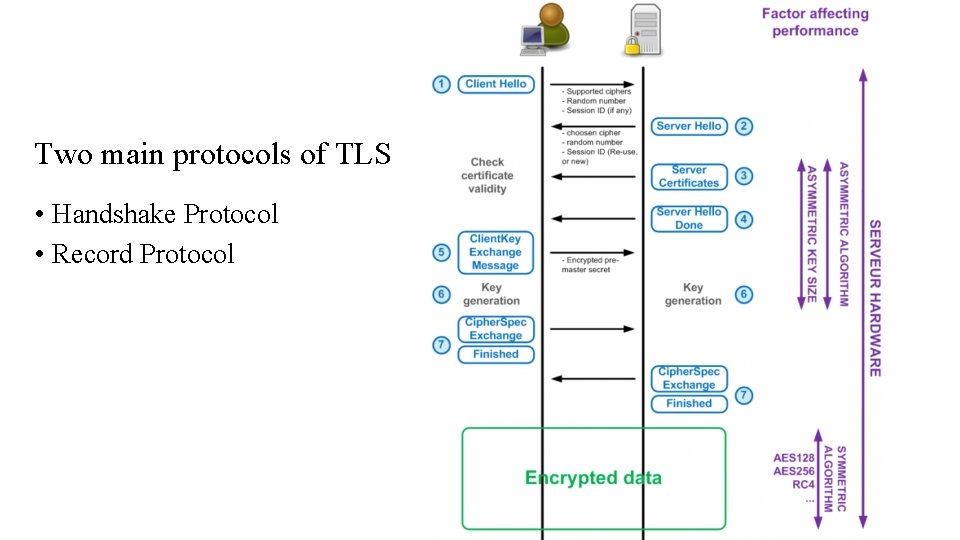
Two main protocols of TLS • Handshake Protocol • Record Protocol

Four myths about TLS • The principal at the other end cannot change • The master secret is shared only between the two peers, so it can be used to derive fresh application-level keys • The tls-unique channel binding uniquely identifies the connection • The connection authenticates the whole data stream, so it is safe to start processing application data as it arrives

New Attacks Over TLS • Triple Handshakes considered harmful • • Client-authenticated TLS renegotiation Compound authentication in tunneled protocols Channel bindings for app-level challenge-response protocols Channel bindings for bearer tokens • Truncating Headers & Forcing Cookies • Defeat cookie-based authentication • Cookie-forcing and used for login CSRF • Building new app-level protocols such as sign-on and synchronization protocols using cookies is foolhardy
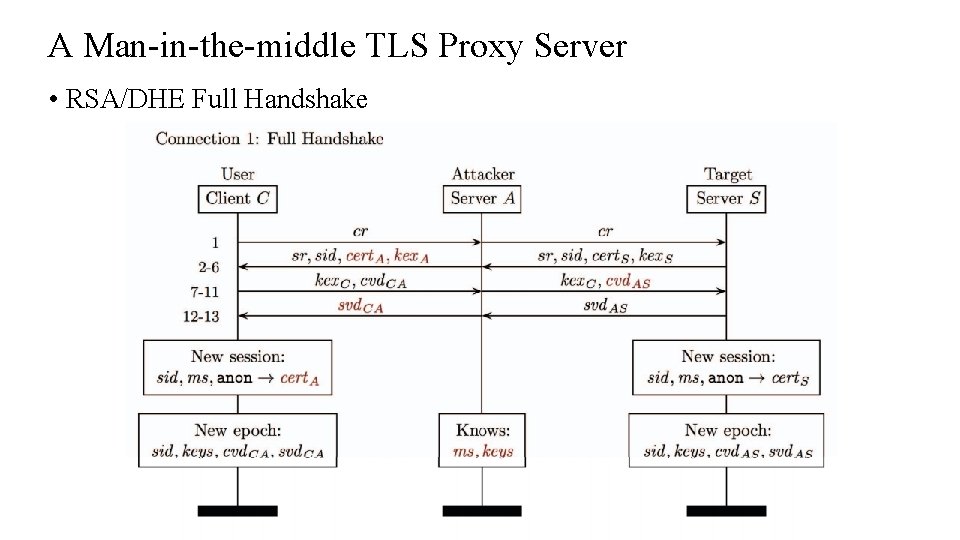
A Man-in-the-middle TLS Proxy Server • RSA/DHE Full Handshake
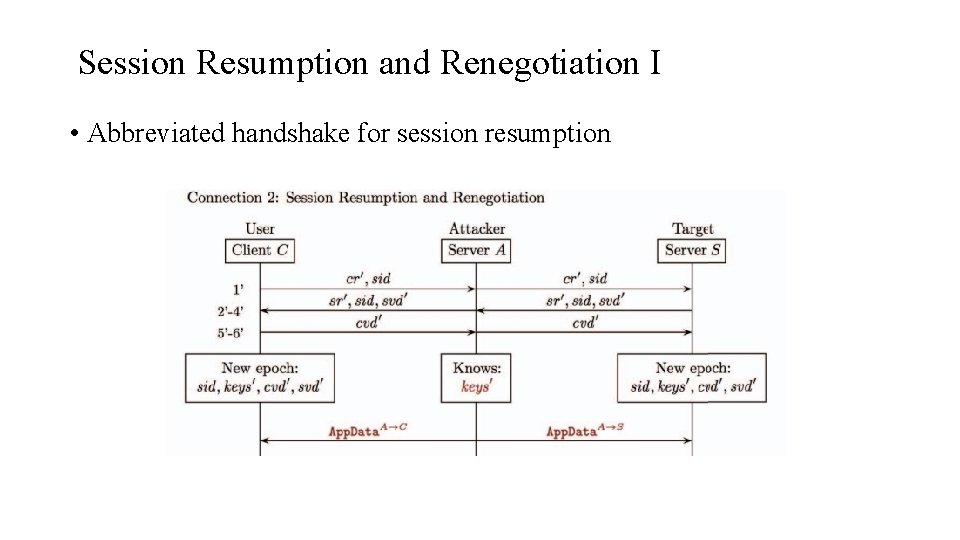
Session Resumption and Renegotiation I • Abbreviated handshake for session resumption
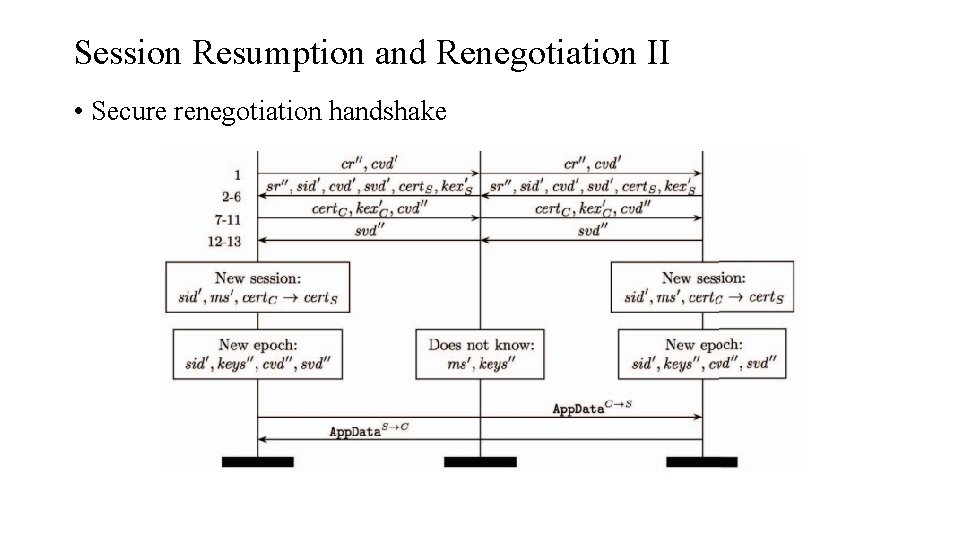
Session Resumption and Renegotiation II • Secure renegotiation handshake

Summary of Mitigations • Do not allow the peer to renegotiate its certificate • Do not use tls-unique after session resumption • To derive application keys from the TLS master secret, hash the session’s certificates into the derivation • Buffer application data until its semantics is unambiguous; discard it if the TLS connection is torn down. • Do not share secret cookies between HTTP and HTTPS connections, or between different origins

Towards Verified Application Security • Proposed TLS Extensions • Propose two new TLS extensions that prevent the attacks without the need to change applications • Apply to all protocol versions from SSL 3 to TLS 1. 2 as well as DTLS • Simple Verified HTTP over TLS • Carefully-written applications can defend against these attacks • Program mi. HTTPs, which is a proof-of-concept: • Does not nearly provide the flexibility required by modern browsers and web services • But automatically handles all the details of the underlying TLS connections, including multiple handshakes, resumption and negotiation, and trunction

Conclusion • Describe a new class of man-in-the-middle attacks against authentication over TLS, targeting the resumption and renegotiation features of the handshake • Present new exploits on HTTPS sessions based on cookie-forcing and truncation • Apply these attacks to break the expected authentication guarantees of several state-of-art protocols, libraries, applications, and web services • Present TLSlevel proposals which are consolidated in patches for Open. SSL and mi. TLS, also build and verify a basic high-level HTTPS API on top of mi. TLS
- Slides: 11