Boundary detection in sensor networks for phenomenon classification
Boundary detection in sensor networks for phenomenon classification GROUP MEMBERS : AKSHAY BALASUBRAMANIAN NANDAKUMAR P VENUGOPAL SATISH RAMASWAMI SALEM INSTRUCTOR : Dr Pao-Lo Liu TA : Mr Saurav Bandyopadhyay

Presentation overview o o o o Objective Optimization criterion Where it can be used Simulation tool and protocol used Actual overview of Simulation Results Future Improvements Questions
OBJECTIVE o o To identify whether a Target Sensor is a part of the edge To identify the boundary of the Phenomenon being measured
Optimization Criterion o o Throughput in the Network layer Routing overhead in the MAC layer Assumptions: General class of boundaries Mild regularity Achievable Performance

Where it can be used? o o o Landmine detection Contouring Unit monitoring and surveillance
Simulation tool and Protocol used o q Choice of environment - Glo. Mo. Sim Choice of Protocol -Ad. Hoc On Demand Vector Routing Protocol (AODV)
What is Glo. Mo. Sim q Glo. Mo. Sim is a simulation environment for wireless systems. q Source Code is written primarily in C and uses the Parsec compiler to create executable. q Layer Models : Physical Data Link Network Transport Application
Classification of routing Protocols q o Proactive – When a packet needs to be forwarded, the route is already known. *Each node maintains routing information to all other nodes in the network. *When updates are made it is propagated throughout the network. Reactive – Determine a route only when data has to be sent. each node *Nodes that are not selected in the path do not maintain routing information. *The route discovery process is initiated by the source node.

What is AODV o o o It is a reactive type of routing protocol. Packet types Used RREQ - broadcast route discovery message RREP - unicast message to validate a path RERR - Error message to inform nodes of link failure Routing information stored at the nodes When a route to a new destination is needed, the node broadcasts a RREQ to find a route to the destination Routing table stores only active routes, unused routes are removed
Protocol modifications o Novelty involved -Is it my packet? -Do I have to stay awake!! I am better of sleeping Power-off mode in MAC layer
Results to Substantiate Claim Ø Throughput Ø Power Constraint
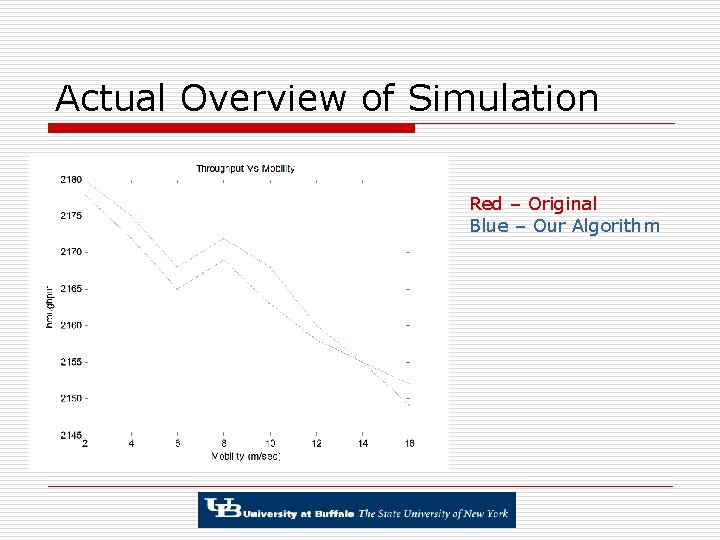
Actual Overview of Simulation Red – Original Blue – Our Algorithm
Power versus Time Red – Original Blue – Our Algorithm

Scope for Improvement o Resilience to security threats and Attacks ü Denial of Service Packet flooding ü Impersonation ü Black hole problem ü

o QUESTIONS ?
- Slides: 16