Bot Miner Guofei Gu Roberto Perdisci Junjie Zhang

Bot. Miner Guofei Gu, Roberto Perdisci, Junjie Zhang, and Wenke Lee College of Computing, Georgia Institute of Technology

Outline • Introduction to botnets • Bot. Miner Detection Framework • Experiments Setup • Results • Limitations • Other weaknesses • Questions
Introduction to botnets • Botnet background • Structure of botnets o Centralized botnet o Decentralized botnet • Botnet attack facilitator o Internet Relay Chat (IRC) o Fast-flux § Single-flux § Double-flux o Domain-flux

Botnet background ● Botnet is a network of compromised computers by malwares called bot ● Botmaster can command bots under his control to perform many activities ○ DDo. S attacks ○ Spamming ○ Stealing sensitive information ○ Click fraud ○ Fast flux ○ Recruiting other hosts
Structure of botnets (1) • Centralized botnet o Having a central point for exchanging command data called command control server (C&C server) o C&C server usually run service network such IRC or HTTP o Bots will connect to the C&C server and wait for the command
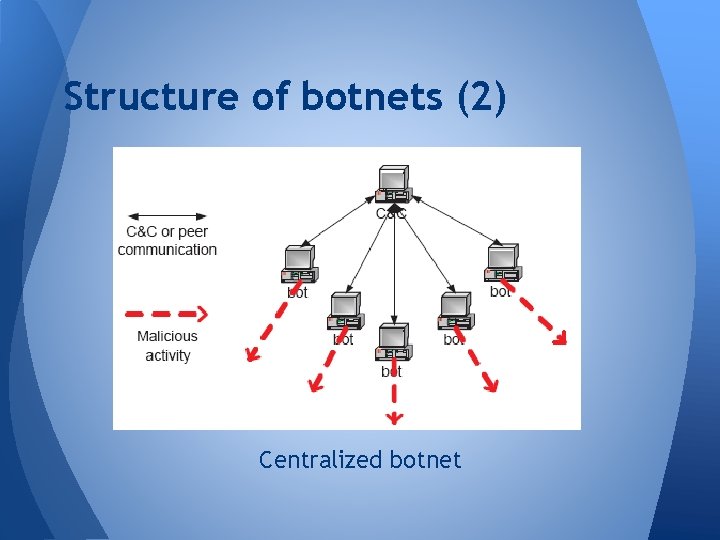
Structure of botnets (2) Centralized botnet
Structure of botnets (3) • Decentralized botnet o Each bot can act as both client and server by using the idea of Peer-to-peer (P 2 P) communication o Each bot have to connect to other bots o Still need some gathering place
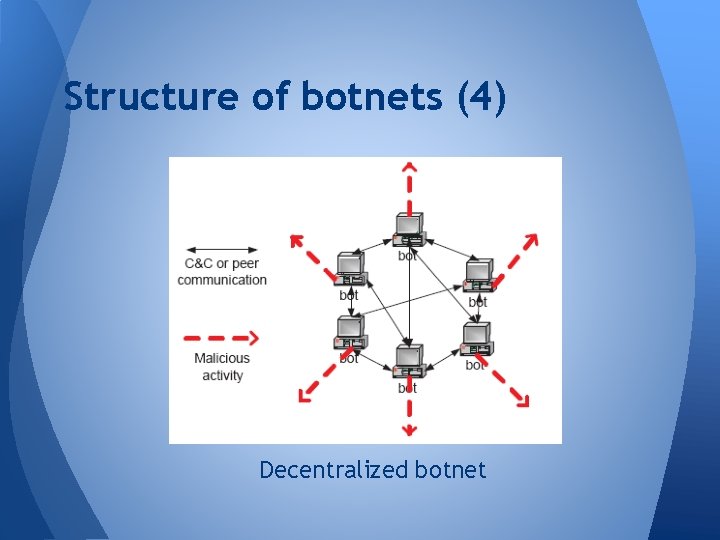
Structure of botnets (4) Decentralized botnet
Structure of botnets (5) • Pros o Centralized botnet § Small latency § High synchronization o Decentralized botnet § Hard to take down § Hard to detect
Structure of botnets (6) • Cons o Centralized botnet § Easy to take down § Easy to detect o Decentralized botnet § High latency § Poor synchronization

Botnet attack facilitator (1) • Internet Relay Chat (IRC) o It is a protocol for live chat o Mainly designed for group communication o Allow sending text message and file sharing o Clients have to connect to the IRC server o Clients can join or create a chat room in the server called channel

Botnet attack facilitator (2) o Fast-flux § Single-flux Having multiple IP address register to a single domain name Each IP address is registered and de-registered rapidly with short TTL, possible to be as short as 3 minutes • •

Botnet attack facilitator (3) o Fast-flux § Double-flux It is a more advance version of single flux by adding one layer of domain name server flux Multiple DNS servers are registered and de-registered Each DNS server also have multiple IP addresses for the domain name • • •
Botnet attack facilitator (4) • Domain-flux o It is a technique for botnets to hide its C&C server or gathering point for P 2 P botnet o Each bot will generate a list of domain name using certain algorithm and try to locate its central point to receive command in those list
Bot. Miner Detection Framework • Traffic monitor o A-plane monitor o C-plane monitor • A-plane clustering • Cross-plane correlation

Traffic monitor (1) • A-plane monitor o Monitor and log internal host activities o Using SCADE (Statistical s. Can Anomaly Detection Engine)from Bot. Hunter to detect high rate of scan activities and high rate of fail connection o Detect spam-related activities by checking Simple Mail Transfer Protocol (SMTP) connection to mail server o Detect suspicious binary download activities, IRC bot

Traffic monitor (2) • C-plane monitor o Monitor and log flow record § time § duration § source IP § source port § destination IP § destination port § number of packets and bytes transferred in both directions.

A-plane clustering (1) • Listing clients that perform suspicious activities • Clustering them by type of activities, scan, spam, binary downloading, exploit • Clustering each group of activity type
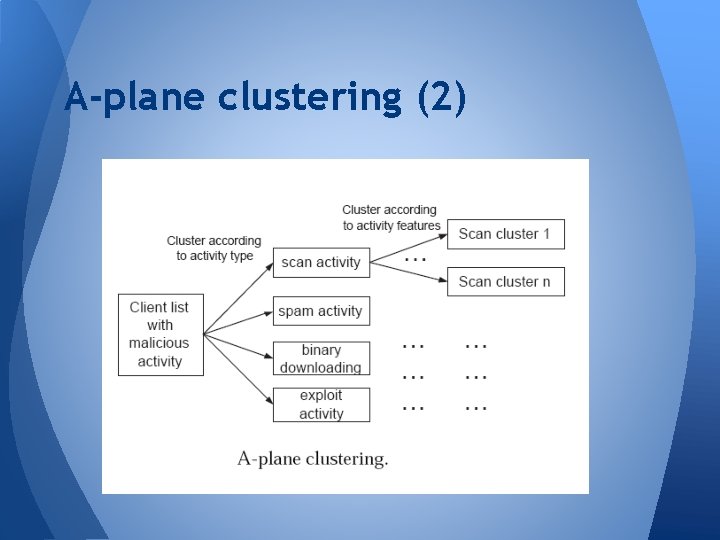
A-plane clustering (2)
C-plane clustering (1) • Reading and clustering the log from Cplane monitor • Clustering method o Basic filtering § filter out flows initiated by external hosts and flows between internal hosts o Whitelisting § Filter out flows to legitimate servers o Aggregation to C-Flow § All flows that share protocol, source and destination IP, port are group together
C-plane clustering (2) o Translating C-Flow to vectors § Computing 4 variables into vectors with 13 elements for each vector • • the the number of flows per hour (fph) number of packets per flow (ppf) average number of bytes per packets (bpp) average number of bytes per second (bps) o Reducing a total of 52 features into 8 features by computing the mean and variance of each vector

C-plane clustering (3) o Performing coarse-grained clustering with only 8 features as step 1 o Performing another clustering on each cluster from earlier step with complete 52 features as step 2
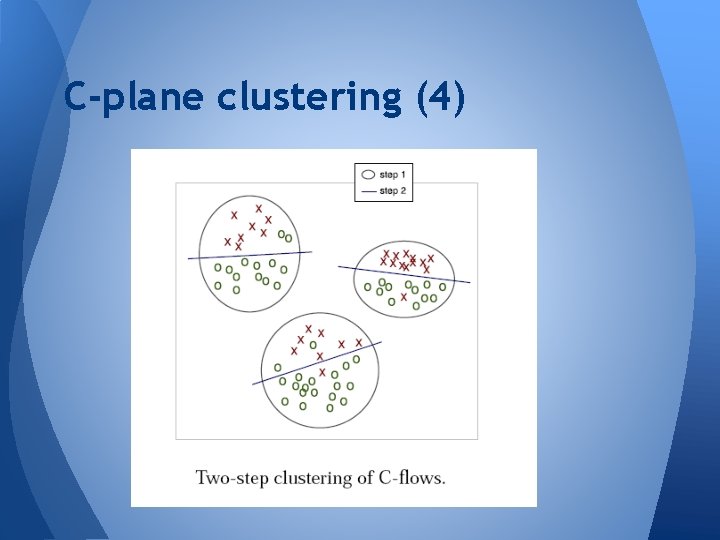
C-plane clustering (4)

Cross-plane correlation • Cross-check clusters to find out intersections • Computing botnet score on clients with suspicious activities o High score for spam and exploit activities o Low score for scan and binary download activities o High score for performing more than 1 type of suspicious activities o Filter out clients with score less than

Experiment Setup (1) • • Monitor traffic at the College of Computing at Georgia Tech. Traffic contain many protocols such as HTTP, SMTP, Post Office Protocol (POP), FTP, Secure Shell (SSH), Simple Network Management Protocol (SNMP), Instant Message (IM), DNS, P 2 P, IRC
Experiment Setup (2) • Collection of botnets traces o IRC bots § Botnet-IRC-spybot § Botnet-IRC-sdbot § Botnet-IRC-rbot § Botnet-IRC-N o HTTP bots § Botnet-HTTP-1 § Botnet-HTTP-2 o P 2 P bots § Botnet-P 2 P-Storm
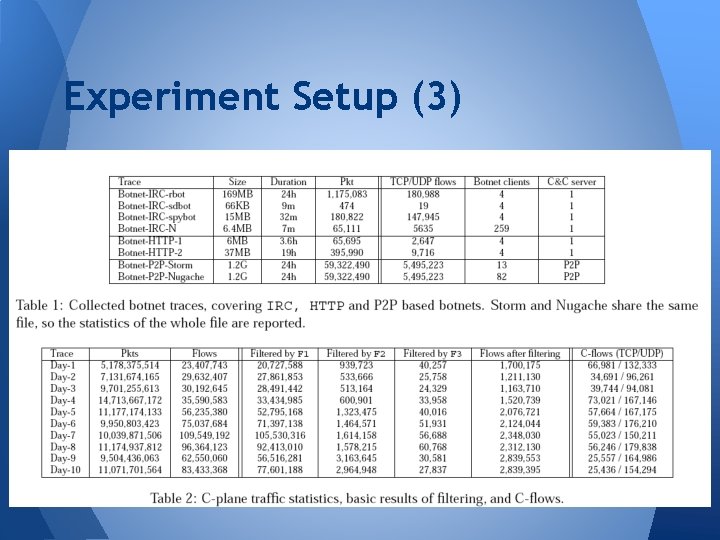
Experiment Setup (3)
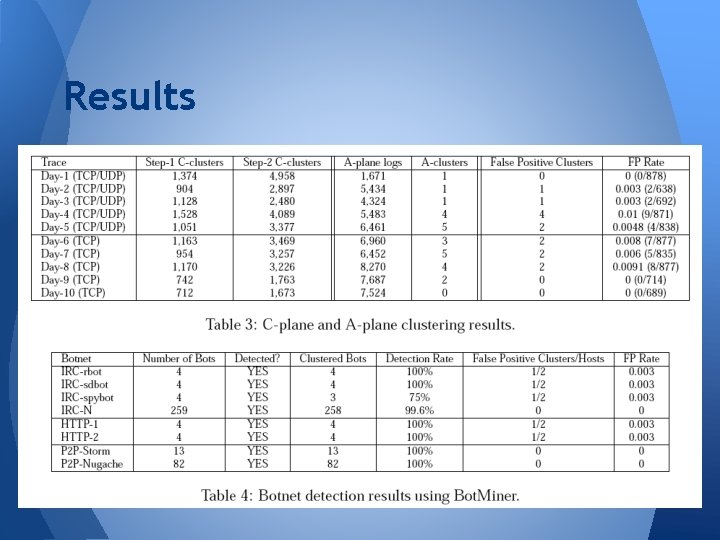
Results

Limitations and solutions • Evading C-plane Monitoring and Clustering • Evading A-plane Monitoring and Clustering • Evading Cross-plane Analysis

Evading C-plane Monitoring and Clustering • Botnet may use legitimate website for their C&C lookup o Don’t perform whitelisting • Using multiple C&C servers o Can do the same as P 2 P clustering • Randomize communication pattern o Randomization may provide some similarities o Randomized pattern may rise suspicious • Mimic normal communication pattern

Evading A-plane Monitoring and Clustering • Botnet can evade detection at the cost of its own efficiency o Having low rate of suspicious activities o Performing randomly and individually task

Evading Cross-plane Analysis • Delaying command execution o Checking data back several days

Other weaknesses • A-plane monitoring is useless against botnet with encrypted communication • Be able to detect botnet in only attack phase

Questions
- Slides: 34