Bit Coding Network Traffic Classification Through Encoded Bit
Bit. Coding Network Traffic Classification Through Encoded Bit Level Signatures Author: Neminath Hubballi, Mayank Swarnkar Publisher/Conference: IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 26, NO. 5, OCTOBER 2018 Referenced: Presenter: 林宇翔 Date: 2019/03/20 Department of Computer Science and Information Engineering National Cheng Kung University, Taiwan R. O. C.
Introduction l l In traditional deep-packet-inspection (DPI) methods, application specific signatures are generated with byte-level data from payload. Increasingly new data formats are being used to encode the application protocols with bit-level information which render the byte-level signatures ineffective. Bit. Coding, a bit-level DPI-based signature generation technique, uses only a small number of initial bits from a flow and identify invariant bits as signature. Subsequently, these bit signatures are encoded and transformed into a newly defined state transition machine transition constrained counting automata. We describe a method for signature similarity detection using a variant of Hamming Distance and propose to increase the length of signatures for a subset of protocols to avoid overlaps. National Cheng Kung University CSIE Computer & Internet Architecture Lab 2
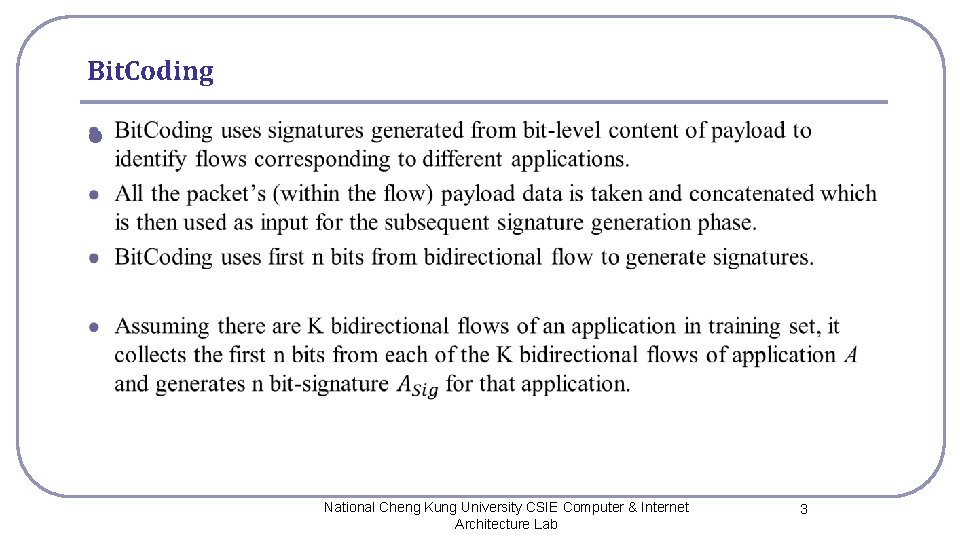
Bit. Coding l National Cheng Kung University CSIE Computer & Internet Architecture Lab 3

Bit-Signature Generation l l l In this example, there are 3 flows each with 20 bits and are used for signature generation. The final signature generated is 1111000000***111. For efficient representation, storage and comparison purposes, we perform Run -length Encoding (RLE) of these n bits. RLE is a technique used in loss-less data compression. After encoding with RLE it is converted to 8 W 6 Z 3*3 W. National Cheng Kung University CSIE Computer & Internet Architecture Lab 4
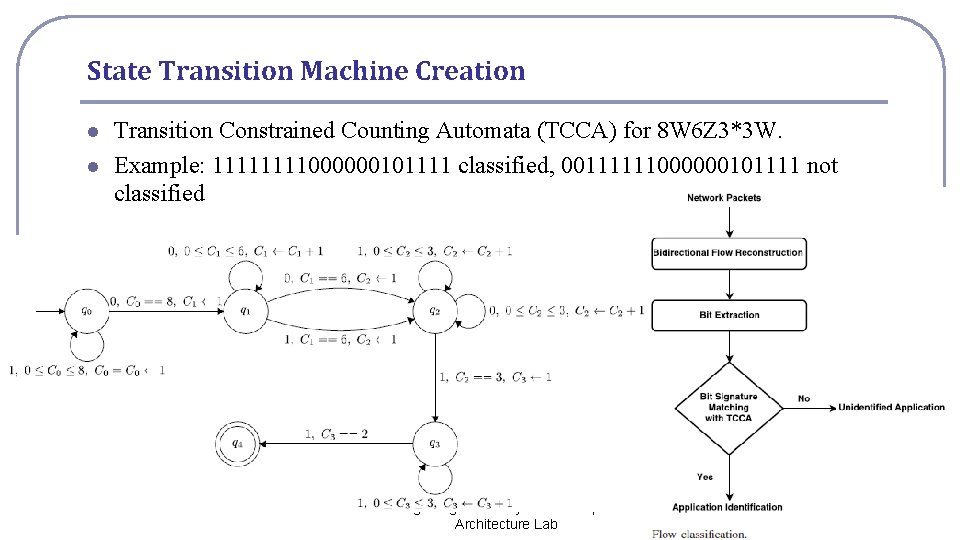
State Transition Machine Creation l l Transition Constrained Counting Automata (TCCA) for 8 W 6 Z 3*3 W. Example: 1111000000101111 classified, 00111111000000101111 not classified National Cheng Kung University CSIE Computer & Internet Architecture Lab 5
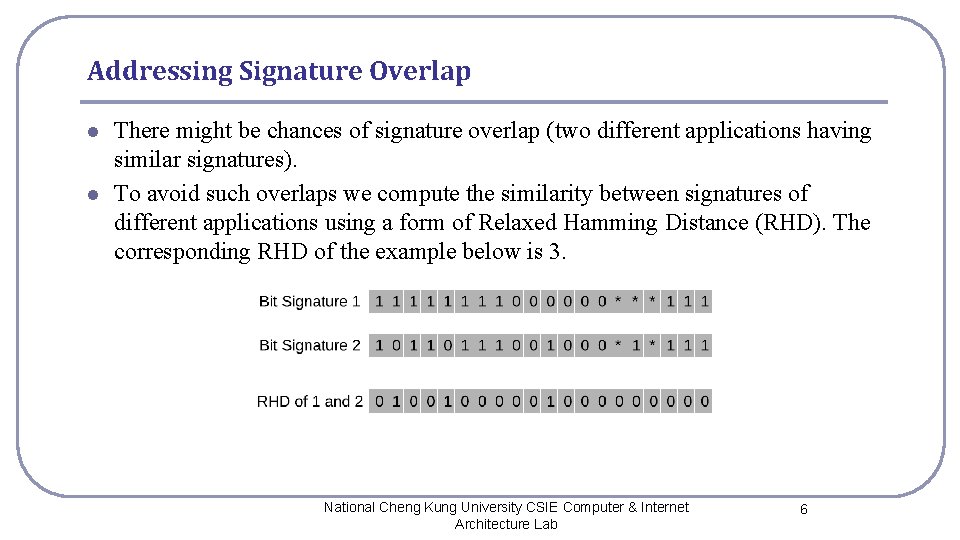
Addressing Signature Overlap l l There might be chances of signature overlap (two different applications having similar signatures). To avoid such overlaps we compute the similarity between signatures of different applications using a form of Relaxed Hamming Distance (RHD). The corresponding RHD of the example below is 3. National Cheng Kung University CSIE Computer & Internet Architecture Lab 6
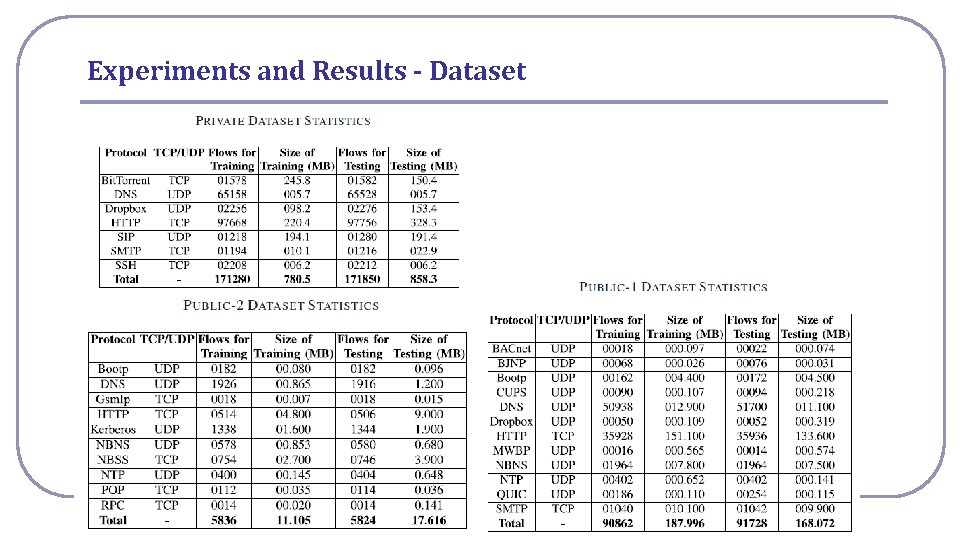
Experiments and Results - Dataset National Cheng Kung University CSIE Computer & Internet Architecture Lab 7
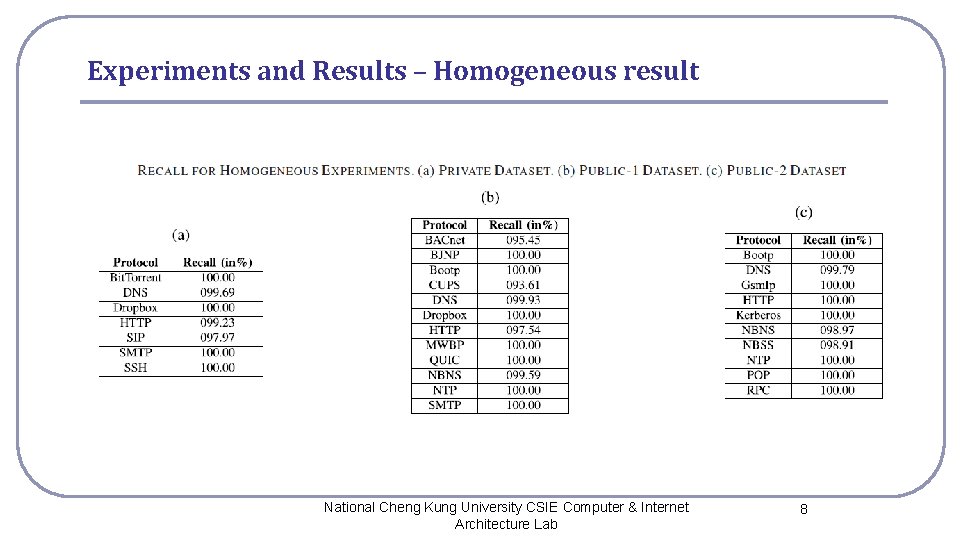
Experiments and Results – Homogeneous result National Cheng Kung University CSIE Computer & Internet Architecture Lab 8
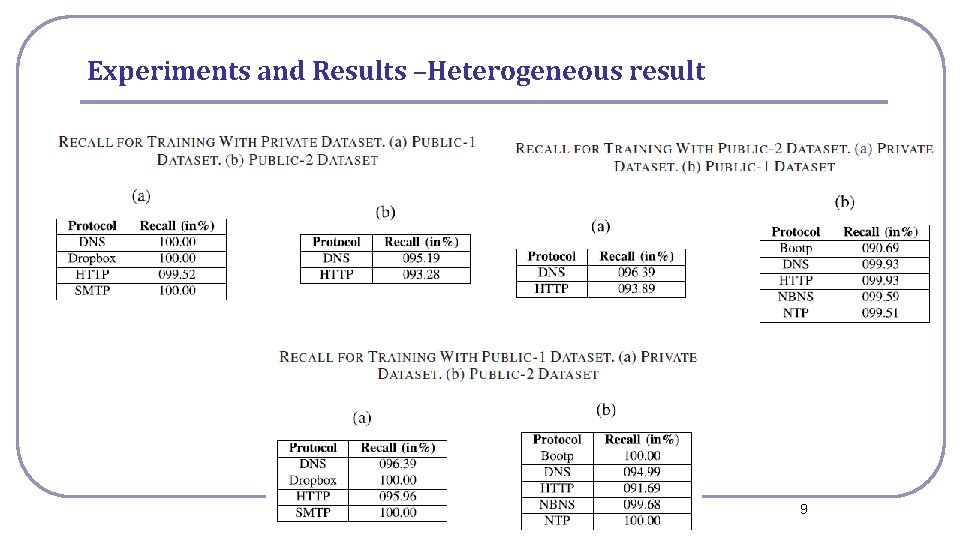
Experiments and Results –Heterogeneous result National Cheng Kung University CSIE Computer & Internet Architecture Lab 9
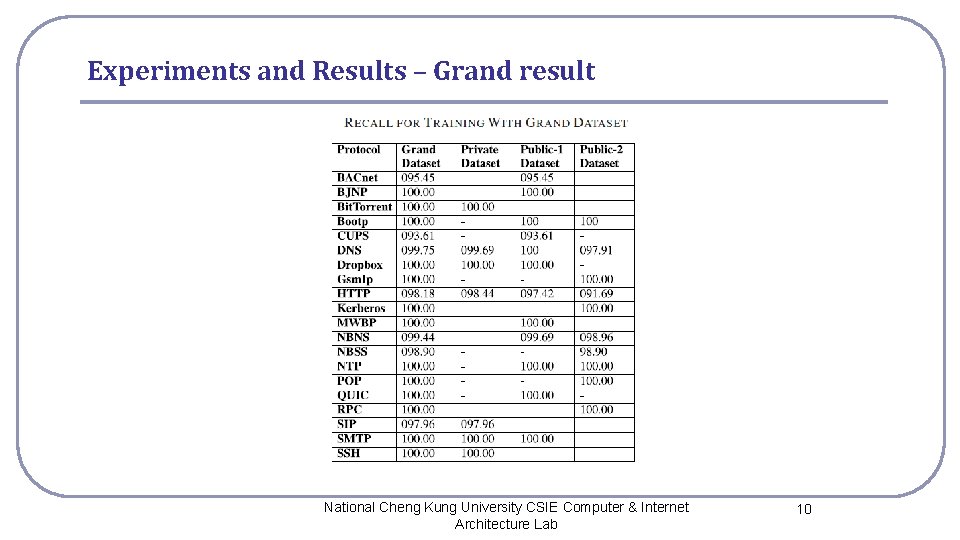
Experiments and Results – Grand result National Cheng Kung University CSIE Computer & Internet Architecture Lab 10
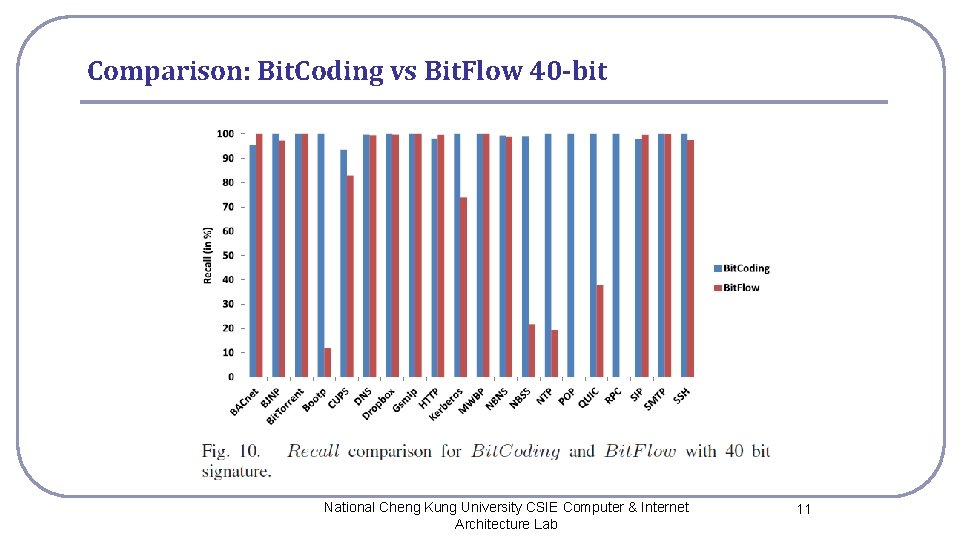
Comparison: Bit. Coding vs Bit. Flow 40 -bit National Cheng Kung University CSIE Computer & Internet Architecture Lab 11
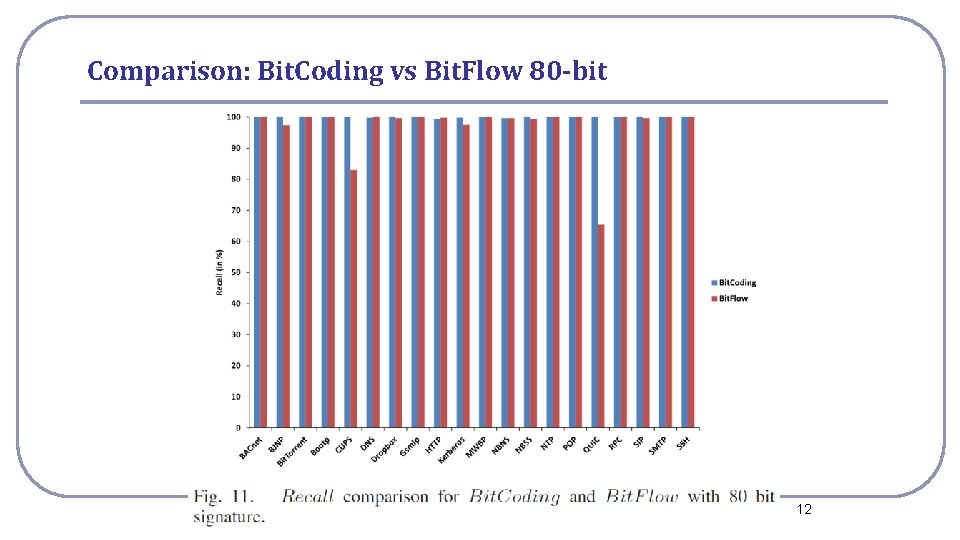
Comparison: Bit. Coding vs Bit. Flow 80 -bit National Cheng Kung University CSIE Computer & Internet Architecture Lab 12
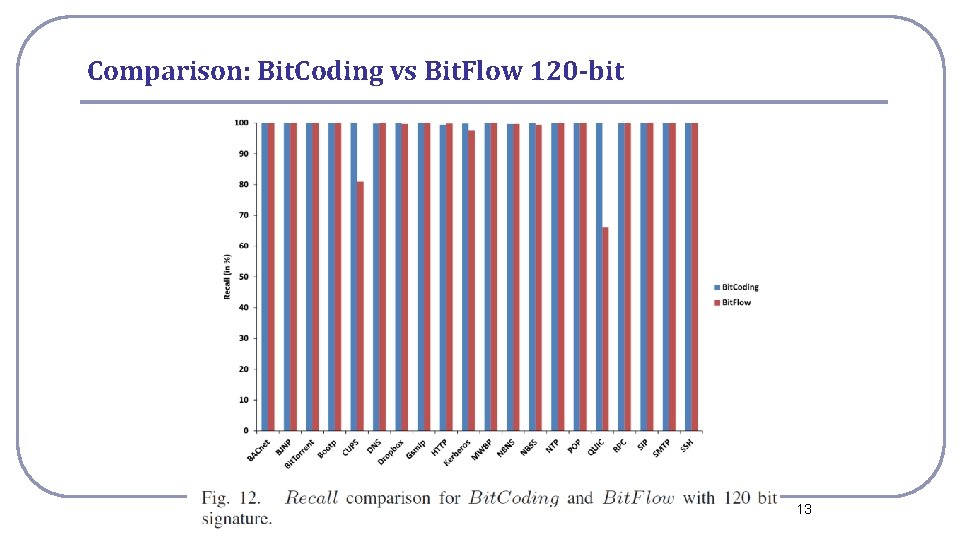
Comparison: Bit. Coding vs Bit. Flow 120 -bit National Cheng Kung University CSIE Computer & Internet Architecture Lab 13
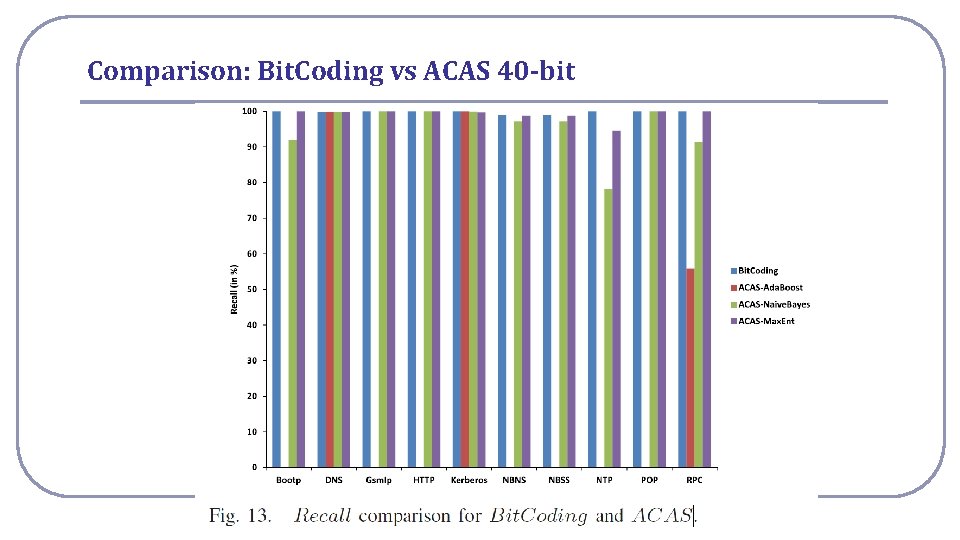
Comparison: Bit. Coding vs ACAS 40 -bit National Cheng Kung University CSIE Computer & Internet Architecture Lab 14
- Slides: 14