Biometric standards An overview of biometrics and identity

Biometric standards An overview of biometrics and identity management February 2010

2 The need to identify • Every day we are required to identify ourselves § Using a bank card with a PIN at a cash machine § A password to log on to a computer § Using a key to open a door § Punching a code into a keypad to enter the workplace § Using passwords on the Internet § Providing a passport and driving licence as proof of identity • We need to be able to accurately IDENTIFY an individual to minimize current issues and threats

3 Current attributes used to identify • Name • Mother’s maiden name • Address • Passport • Postcode • Birth certificate • Date of Birth • Driving licence • Account no. • Credit cards • Passwords • Utility bills • PINs • Membership cards • Phone no. • Salary slip
4 Is biometrics the answer? • A biometric is part of the person and is not easily compromised through: § Theft § Collusion § Loss • Simplifies user management resulting in cost savings • Users do not need to remember passwords • Users do not need to remember PINs • User accounts cannot be shared • Easy to use
5 Biometric definition • The automated recognition of individuals based on their behavioural and biological characteristics § The general meaning of biometrics encompasses counting, measuring and statistical analysis of any kind of data in the biological sciences including the relevant medical sciences • The term is derived from the Greek words “bios” meaning life and “metron” meaning measure
6 Biological and behavioural • Biological § Fingerprint § Face (2 D & 3 D) § Iris § Vein pattern § Hand geometry § DNA • Behavioural § Signature § Gait § Voice § Keystroke dynamics
7 Iris • Captures the pattern of flecks on the iris • Uses conventional cameras • Average 2 seconds for identification • No physical contact between user and reader

8 Face • Based upon the geometric shape and position of features of the face • Resistant to changes in skin tone, facial hair, hair style, and eyeglasses • No active user involvement required in order to perform identification/verification • Limited success in practical applications

9 Voice • Analyses voice patterns and characteristics of speech e. g. pitch, tone, etc. • High user acceptance – perceived as least intrusive biometric technology • Easy for end users to implement • Ideal for telephone systems/mobile environments
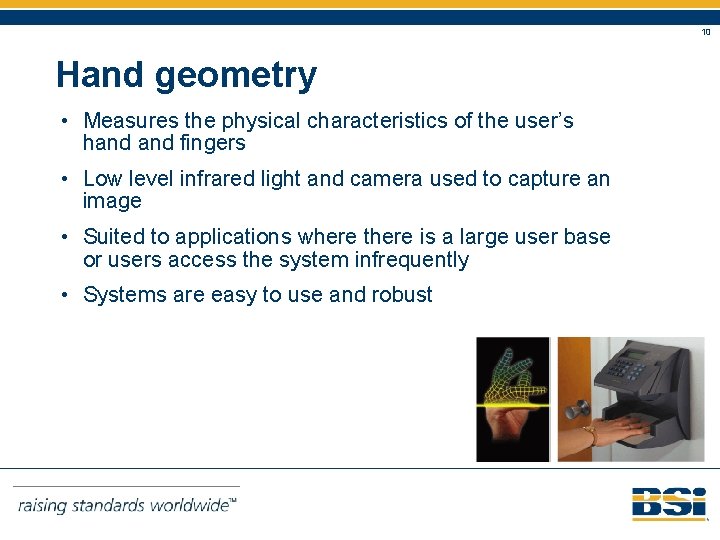
10 Hand geometry • Measures the physical characteristics of the user’s hand fingers • Low level infrared light and camera used to capture an image • Suited to applications where there is a large user base or users access the system infrequently • Systems are easy to use and robust

11 Signature • Based on analysis of the dynamics of a handwritten signature e. g. shape, speed, stroke order, pen pressure • Generally use pressure sensitive tablets or wired pens • User friendly • Non intrusive – minimal public acceptance issues • Captured signature can be used for digitally signing documents

12 Keystroke dynamics • Monitors rate of typing and intervals between letters • Verification based on typing rhythm – intruders may guess password but fail to key in with correct rhythm • Neither enrolment nor verification disturbs the regular flow of work • Low cost – only hardware required is keyboard
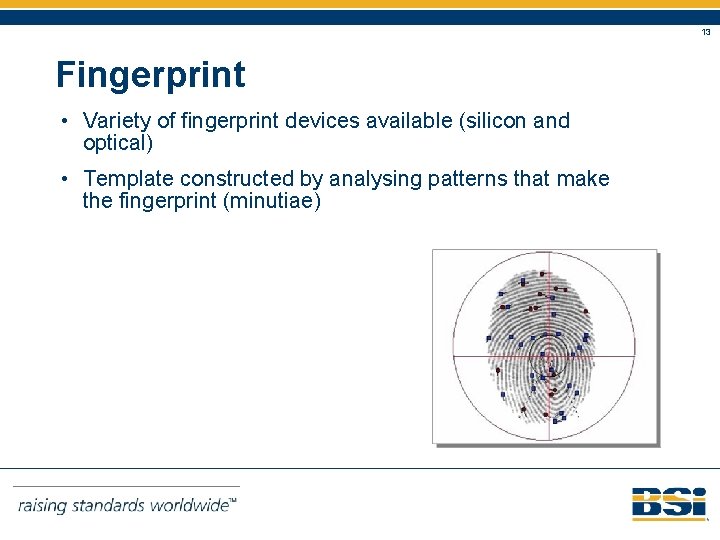
13 Fingerprint • Variety of fingerprint devices available (silicon and optical) • Template constructed by analysing patterns that make the fingerprint (minutiae)
14 DNA • Forensic genetics use deoxyribonucleic acid (DNA) profiling in a number of important human identity applications • 0. 01% of a person's entire genome is unique to each individual § This represents 3 million base pairs of DNA § 95% of the human genome are non-coding sequences (called junk DNA) • Standard profiling systems only exploit the junk DNA to maintain the privacy and civil rights of the donor
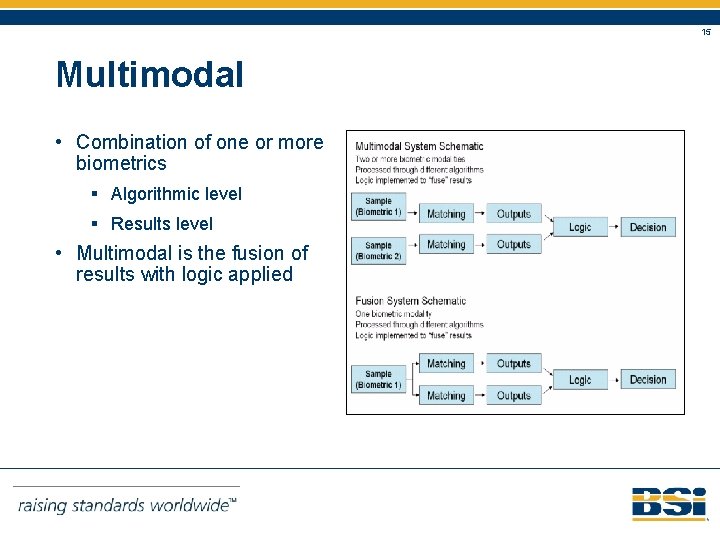
15 Multimodal • Combination of one or more biometrics § Algorithmic level § Results level • Multimodal is the fusion of results with logic applied
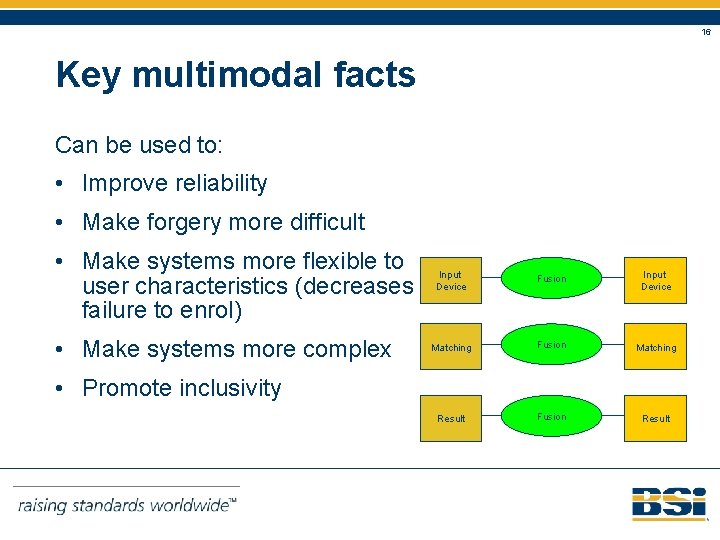
16 Key multimodal facts Can be used to: • Improve reliability • Make forgery more difficult • Make systems more flexible to user characteristics (decreases failure to enrol) • Make systems more complex Input Device Fusion Input Device Matching Fusion Matching Result Fusion Result • Promote inclusivity

17 Verification versus Identification “Who are you? ” “Are you who you say you are? ” NOT
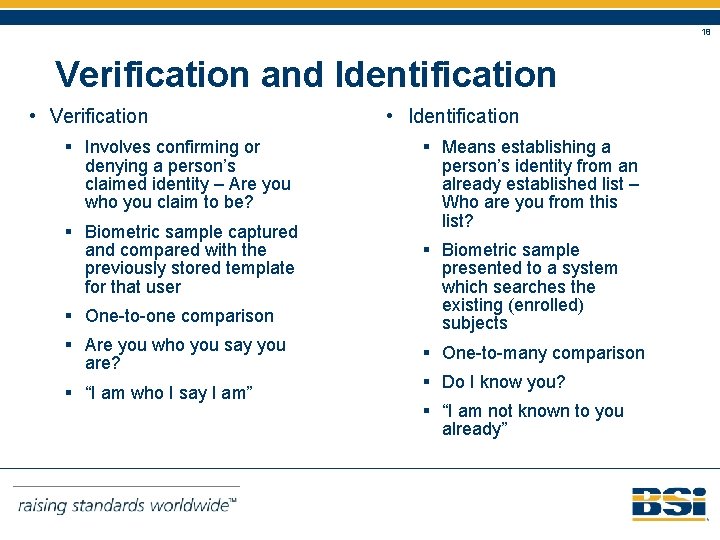
18 Verification and Identification • Verification § Involves confirming or denying a person’s claimed identity – Are you who you claim to be? § Biometric sample captured and compared with the previously stored template for that user § One-to-one comparison § Are you who you say you are? § “I am who I say I am” • Identification § Means establishing a person’s identity from an already established list – Who are you from this list? § Biometric sample presented to a system which searches the existing (enrolled) subjects § One-to-many comparison § Do I know you? § “I am not known to you already”
19 Identification before verification • To establish a ‘clean’ database of individuals each individual first needs to be identified § One-to-many match is performed against the central database to ensure the individual does not already exist under correct name or any other aliases • Once identity is established it can be sufficient to verify the individual as proof of identity only § One-to-one match is performed at the point of interface without the need to check back to the central database
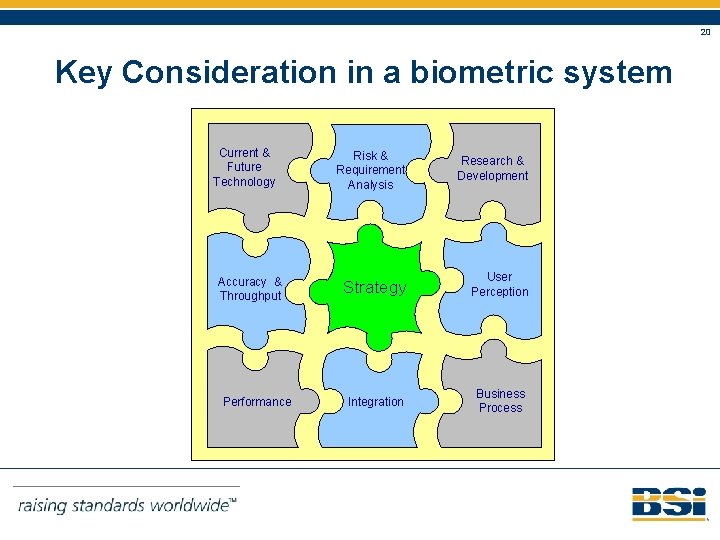
20 Key Consideration in a biometric system Current & Future Technology Accuracy & Throughput Performance Risk & Requirement Analysis Research & Development Strategy User Perception Integration Business Process
21 Considerations of adding a biometric system • Not all biometrics technologies suit all people • In many cases additional hardware is required • User co-operation is usually necessary • Privacy concerns must be addressed • Cost of personal devices in large systems can be significant • User education is required • Biometric revocation must be considered as biometric data is not secret

22 Capture the legal and political imperatives • Ask what additional considerations are there with a biometric application as opposed to any other IT deliverable § Privacy? § Data access considerations (who and why)? § Sensitivity of data? § Legislative limitations? § User acceptance? § Standards compliance?
23 ISO/IEC JTC 1 SC 37 Biometrics • Currently 25 participating countries and 7 observer countries • Liaisons with: § JTC 1/SC 17 Cards and Personal Identification. § JTC 1/SC 24 Computer Graphics and Imaging § JTC 1/SC 27 Information Technology Security Techniques. § JTC 1/SC 29 Coding of Audio, Picture and Multimedia and Hypermedia Information. § JTC 1/SC 31 Automatic Identification and Data Capture Techniques § JTC 1/SC 32 Data Management and Interchange § JTC 1/SC 36 Information Technology for Learning, Education and Training. § ITU-T SG 17 Telecommunication Standardization Sector Study Group on Data Networks and Telecommunications Software. § Bio. API Consortium § IBIA International Biometrics Industry Association (IBIA) § ILO International Labour Office of the UN
24 The benefits of standards for biometrics • They foster wide spread utilization of the technology • They are a sign of industry maturity • They reduce time-to-market • They facilitate interchange and/or interoperability • They reduce risk to integrators and end users • They reduce vendor “lock-in” effect

25
- Slides: 25