Beyond Corp Beyond fortress security OReilly Security Conference

Beyond. Corp: Beyond fortress security O’Reilly Security Conference 2017 Neal Mueller, Product Lead, Google Cloud @nealmueller, nealx@google. com Max Saltonstall, Office of CTO, Google Cloud salt@google. com

New cloud model: risks and threats

How some enterprises think of security But there are issues with this approach. . .
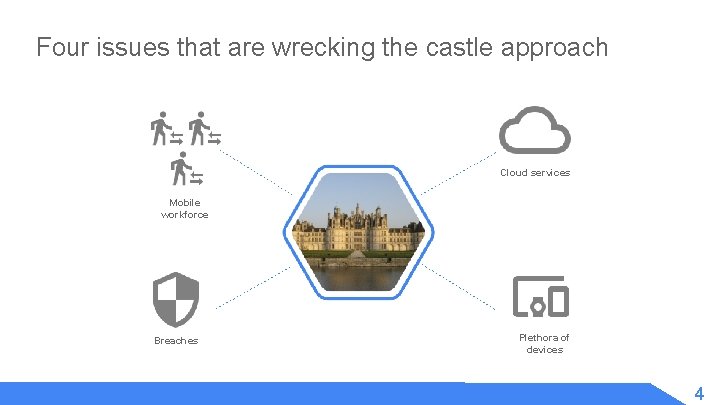
Four issues that are wrecking the castle approach Cloud services Mobile workforce Breaches Plethora of devices 4
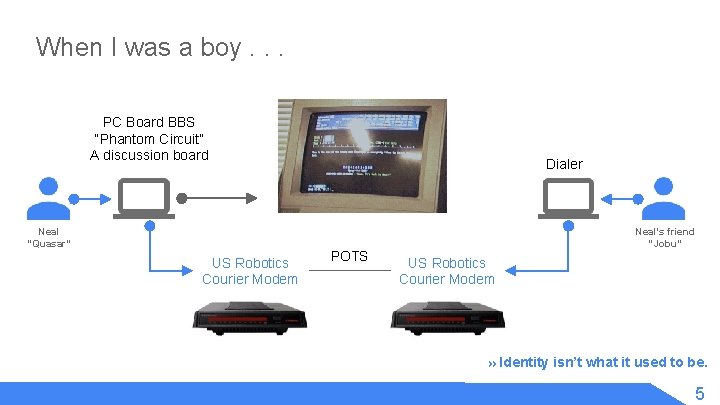
When I was a boy. . . PC Board BBS “Phantom Circuit” A discussion board Neal “Quasar” US Robotics Courier Modem Dialer POTS Neal’s friend “Jobu” US Robotics Courier Modem » Identity isn’t what it used to be. 5
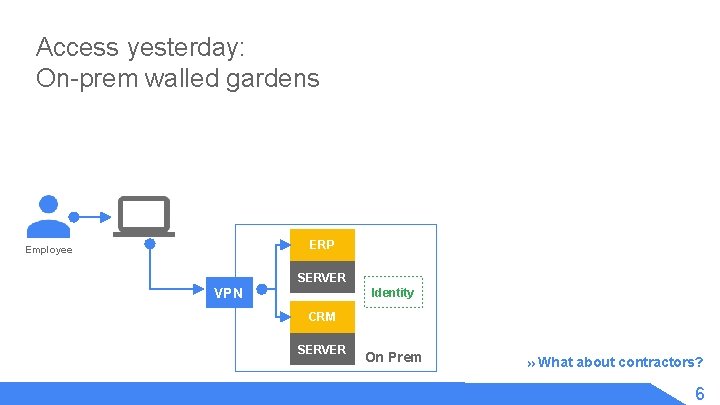
Access yesterday: On-prem walled gardens ERP Employee SERVER VPN Identity CRM SERVER On Prem » What about contractors? 6
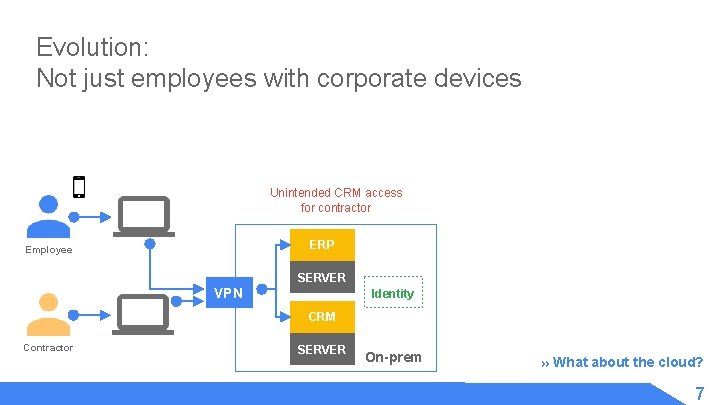
Evolution: Not just employees with corporate devices Unintended CRM access for contractor ERP Employee SERVER VPN Identity CRM Contractor SERVER On-prem » What about the cloud? 7
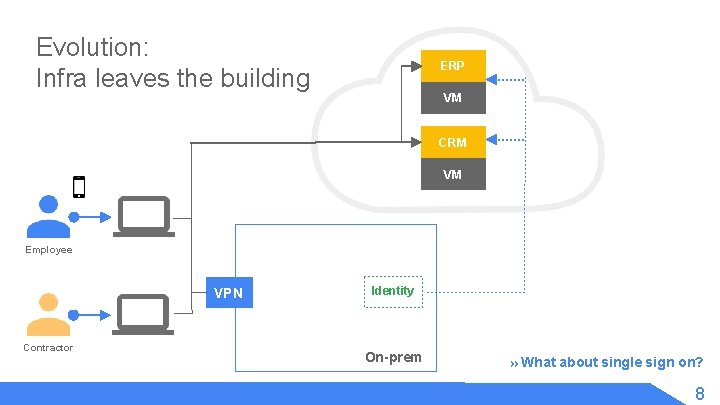
Evolution: Infra leaves the building ERP VM CRM VM Employee VPN Contractor Identity On-prem » What about single sign on? 8
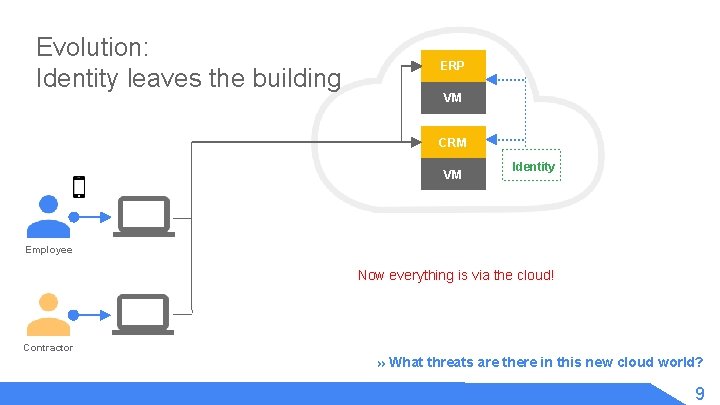
Evolution: Identity leaves the building ERP VM CRM VM Identity Employee Now everything is via the cloud! Contractor » What threats are there in this new cloud world? 9
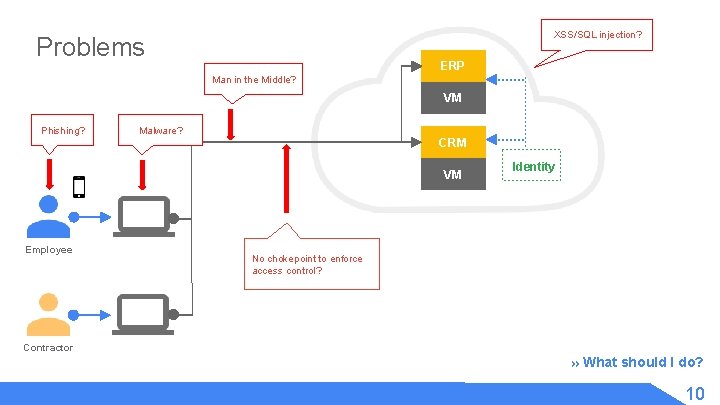
XSS/SQL injection? Problems ERP Man in the Middle? VM Phishing? Malware? CRM VM Employee Identity No chokepoint to enforce access control? Contractor » What should I do? 10

Beyond. Corp’s realization WALLS DON’T WORK
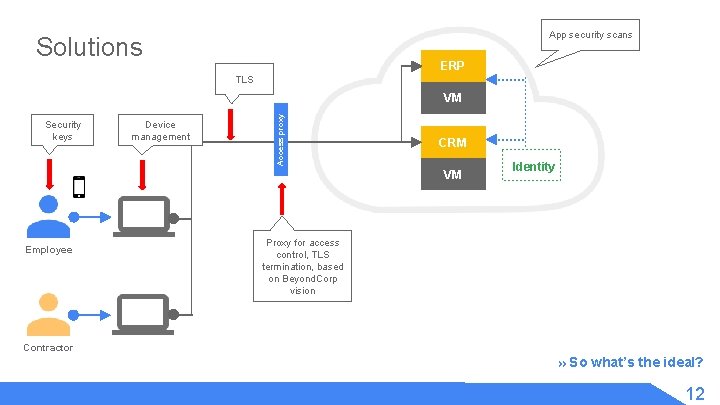
App security scans Solutions ERP TLS Security keys Device management Access proxy VM CRM VM Employee Identity Proxy for access control, TLS termination, based on Beyond. Corp vision Contractor » So what’s the ideal? 12

I want my ERP application service to be: ● Accessed only by finance employees ● From well-managed client devices ● In home country ● Using strong user authentication ● And proper transport encryption and ● Hardened against application attacks 13

Two ways to migrate Oracle EBS to the cloud: hard way vs. easy way
Migrating Oracle EBC to the cloud The hard way 2 weeks ● ● ● Configure cloud network Configure on premise vpn Test vpn access
Migrating Oracle EBC to the cloud The easy way 2 minutes ● ● ● Setup Google Cloud Load Balancer Activate IAP Add email addresses bit. ly/oracleeasy

Implementing Beyond. Corp at Google
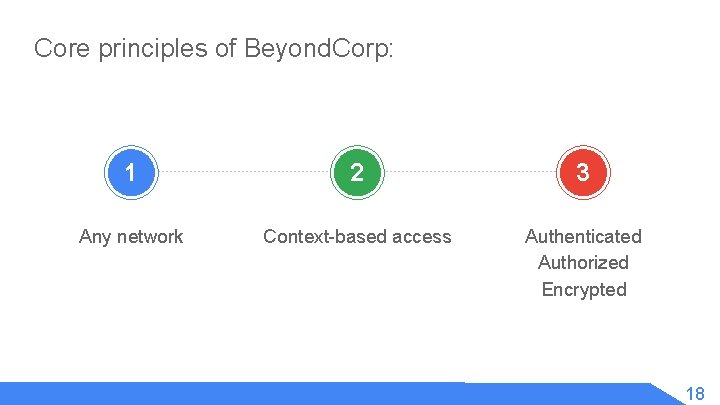
Core principles of Beyond. Corp: 1 2 3 Any network Context-based access Authenticated Authorized Encrypted v 18

Seven year Beyond. Corp mission (2011 -2017) To have every employee work from untrusted networks without a VPN
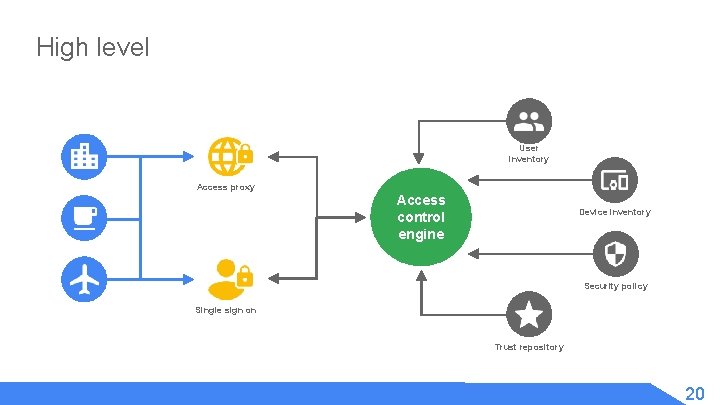
High level User inventory Access proxy Access control engine Device inventory Security policy Single sign on Trust repository 20
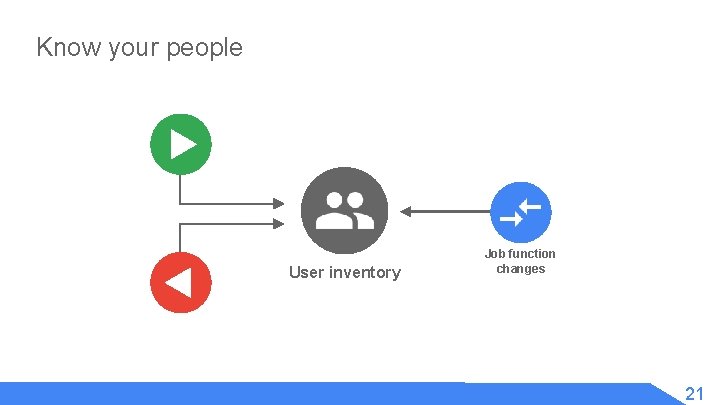
Know your people User inventory Job function changes 21
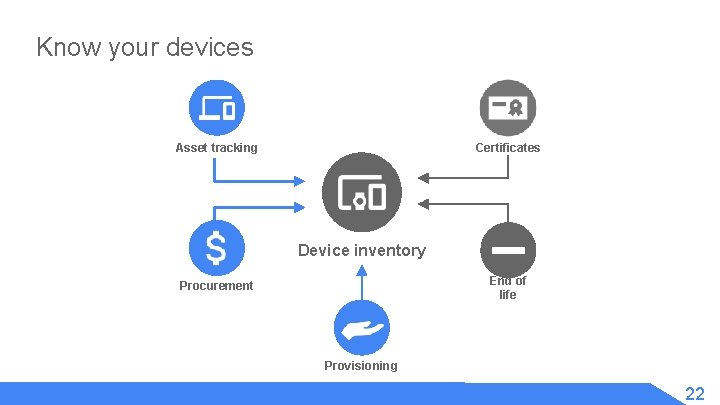
Know your devices Certificates Asset tracking Device inventory End of life Procurement Provisioning 22
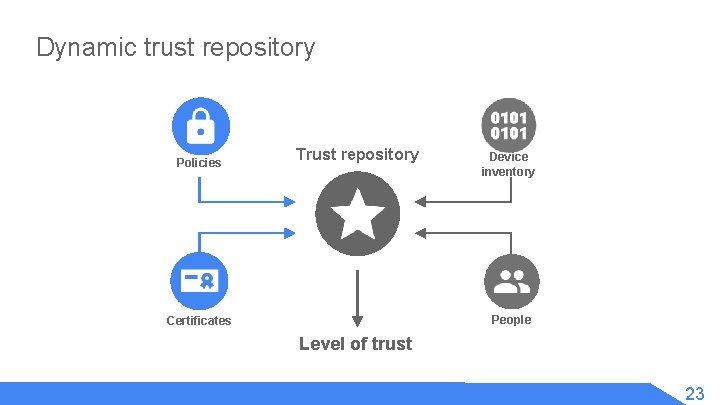
Dynamic trust repository Policies Trust repository Device inventory People Certificates Level of trust 23
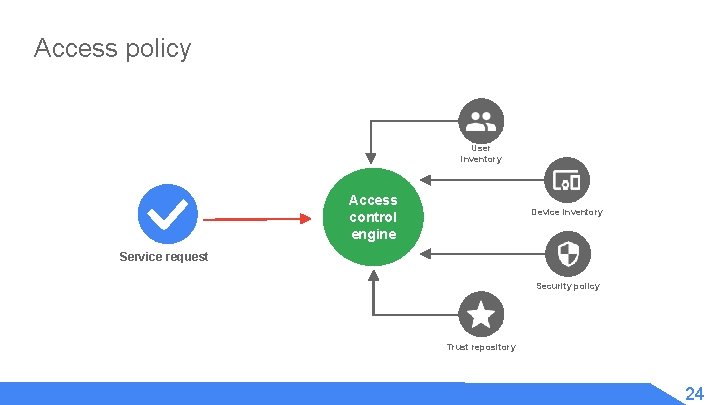
Access policy User inventory Access control engine Device inventory Service request Security policy Trust repository 24
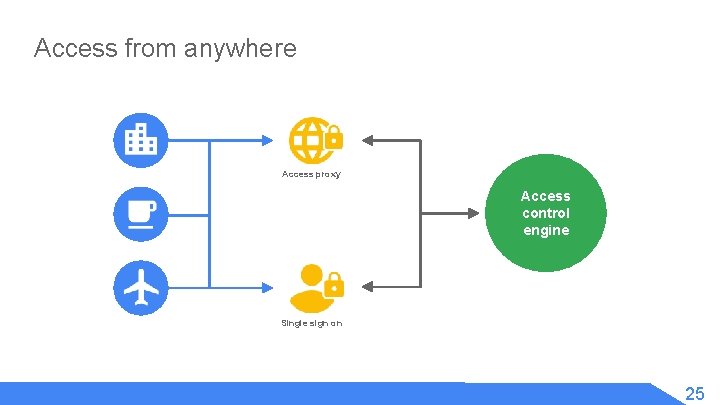
Access from anywhere Access proxy Access control engine Single sign on 25

What Google did to get there

Migrating to Beyond. Corp
New unprivileged network + New VLAN + Add devices Deploy 28
Traffic analysis 29
Safely migrate devices 30

Better loaners

Outreach

Beyond. Corp Papers ● An overview: A New Approach to Enterprise Security ● How Google did it: Design to Deployment at Google ● Google’s front-end infrastructure: The Access Proxy ● Migrating to Beyond. Corp: Maintaining Productivity While Improving Security ● The Human Element: The User Experience 33

Lessons learned: What 7 years taught us about migrating services to the cloud

Lessons learned migrating to cloud Get, and retain, executive support Enable painless migration Run highly reliable systems 35

Lessons learned migrating to cloud Get, and retain, executive support Enable painless migration Run highly reliable systems 36

Lessons learned migrating to cloud Get, and retain, executive support Enable painless migration Run highly reliable systems 37
Remember: 1 2 3 Have zero trust in your network Base all access decisions on what you know about the user and their device Migrate carefully so as not to break existing users v 38

Thank you
- Slides: 39