Berkeley Data Authorization Process MATCHING DATA with IT
Berkeley Data Authorization Process MATCHING DATA with IT SERVICES CISPC, April 19, 2012 Lisa Ho, IT Policy Manager, Berkeley Privacy & Policy Office

Berkeley Data Authorization Process The Questions What is restricted and notice-triggering data? From Resource Proprietors (functional owners): � What service providers (on or off-campus) are appropriate for my data/system? From Resource Custodians who provide/manage IT services: � What kind of data is under my custodianship � What security controls are required? � Can I host restricted/notice-triggering data? From End Users: � Where can I store my restricted data?

Berkeley Data Authorization Process The Answers �Classify campus data Definitions and process �Secure campus data Authorize data use Approve services (on and off campus) for a data class �Develop an information bank Publish approved services Reduce duplication of work �Respond to the Business Finance Bulletin IS-2 Classify, inventory, and define appropriate security controls for institutional data
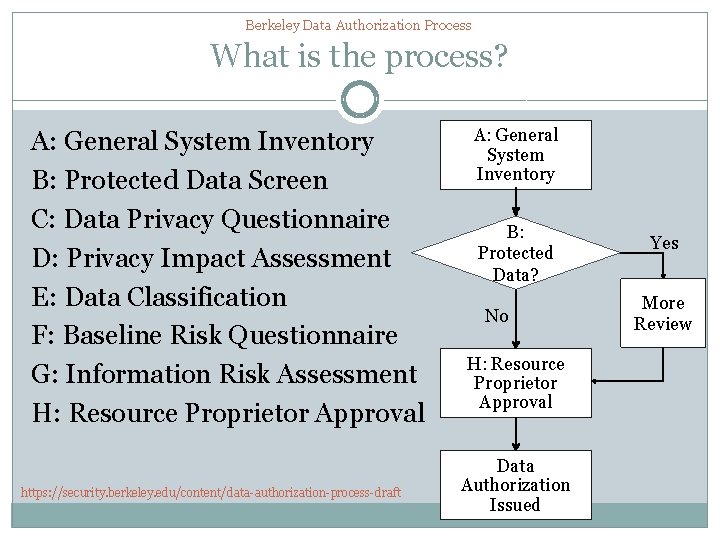
Berkeley Data Authorization Process What is the process? A: General System Inventory B: Protected Data Screen C: Data Privacy Questionnaire D: Privacy Impact Assessment E: Data Classification F: Baseline Risk Questionnaire G: Information Risk Assessment H: Resource Proprietor Approval https: //security. berkeley. edu/content/data-authorization-process-draft A: General System Inventory B: Protected Data? No H: Resource Proprietor Approval Data Authorization Issued Yes More Review

High-level Rollout Plan �Pilot Off-site hosting Systems in the spotlight �Expand to other systems �Eventually align with campus OE initiatives Berkeley Data Authorization Process
- Slides: 5