Before After Strategies for increasing engagement during cybersecurity

Before & After Strategies for increasing engagement during cybersecurity training Louise Flinn NC State University, Office of Information Technology

Me • NC State Office of Information Technology • Graphic Designer & Trainer We
Me We • Outreach, Communications and Consulting • Cybersecurity Awareness and Training group (CSAT)

Today: • Tweaks for increasing engagement • After & Before examples • Mostly phishing-related • Workshop: Improve our slides

Engagement? • Qualitative, not quantitative • Face-to-face trainings

Why?
Program Goals • Change behavior/take action
Engagement Motivation

MY Goals: • Understand the “why” • Empower • Transform into advocates

Biggest hurdle: Learner self-perception

#1 way to increase engagement…

Make it relevant!

Relevancy= • Local • Specific • Relatable

Specific Strategies:
#1: Quizzing
After

You’re the target: % 50 _____ of daily mail traffic is spam or attack

You’re the target: 500, 000 ________ How many emails is that?

A well-crafted phishing message tricks % 42 _____ of recipients

What I like: • Gets their attention! • Sets up a problem to solve

Two-Factor Authentication blocks: % 98 _____ of phishers from accessing email accounts
Before

Email Security • • • Spam • ½ of NC State mail traffic is spam or attack Phishing • Well-crafted messages trick 42% of recipients Viruses and attachments • Don’t open attachments you’re not expecting • Be careful about downloads

Tips for Quizzes • Make it okay not to know • Use local stats when possible • Get comfortable with silence
Quiz Variant Thumbs up/thumbs down

Question 1: True or false: Before going on extended leave, you should share your password with your supervisor in case something comes up.

#2: Storytelling
After

https: //www. youtube. com/watch? v=b 7 EU 0 c. Oyv. Xc
What I like: • Hardwired to remember them • Availability heuristic • Relatable • Sets up a problem to solve
Before

Security Tips • • Enroll now in BOTH Two-Factor solutions: • Google 2 -Step & Duo • go. ncsu. edu/2 FA One phish, Two-step Record serial numbers Free engraving from campus police Phishing attacks are common. NEVER share your password!

Storytelling Variant Doesn’t have to be fancy!
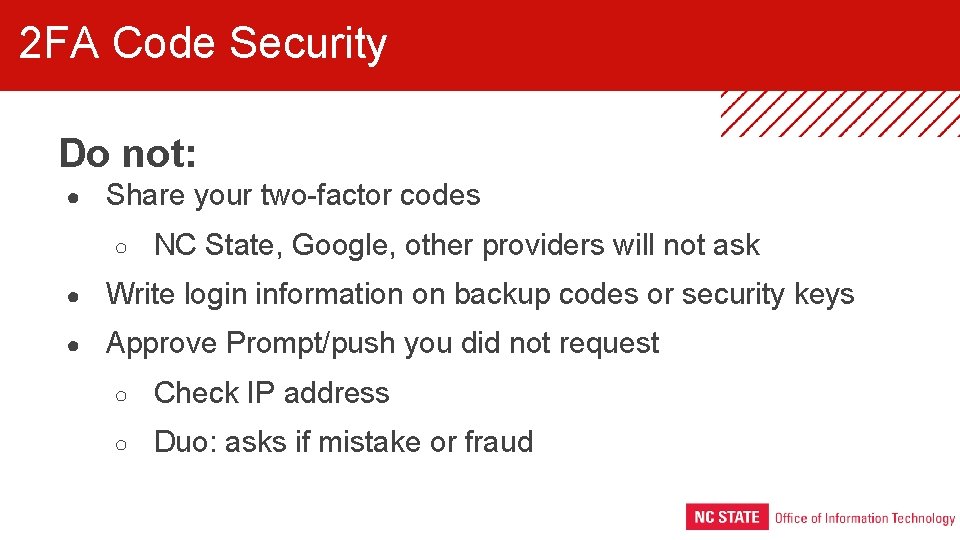
2 FA Code Security Do not: ● Share your two-factor codes ○ NC State, Google, other providers will not ask ● Write login information on backup codes or security keys ● Approve Prompt/push you did not request ○ Check IP address ○ Duo: asks if mistake or fraud

Tips for Stories • Make them human • Be careful with Goofus

#3: Simulations
After

Typical Phish • Spelling/grammar mistakes • “Doom and gloom” • Hidden links • Not addressed to you • Looks “off” • Suspicious senders
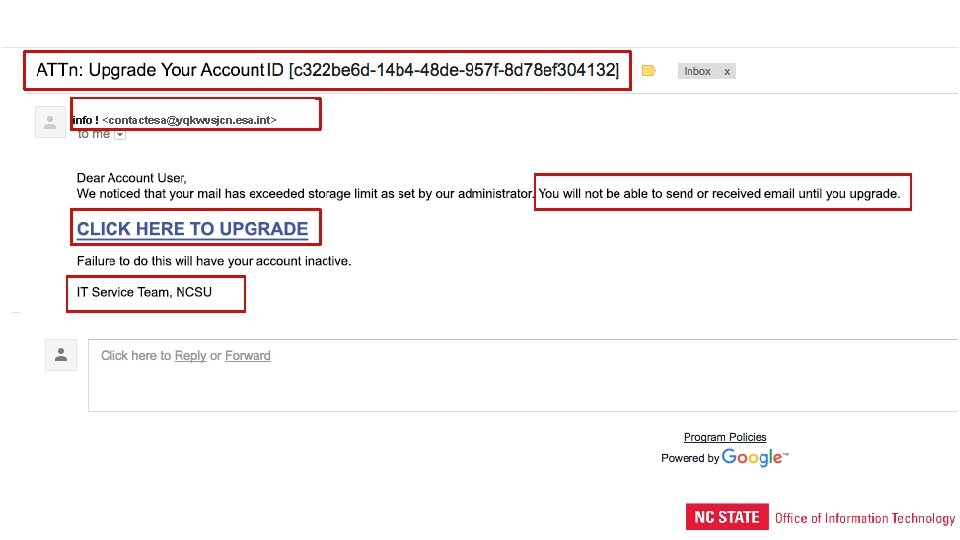
info ! <contactesa@yqkwvsjcn. esa. int>
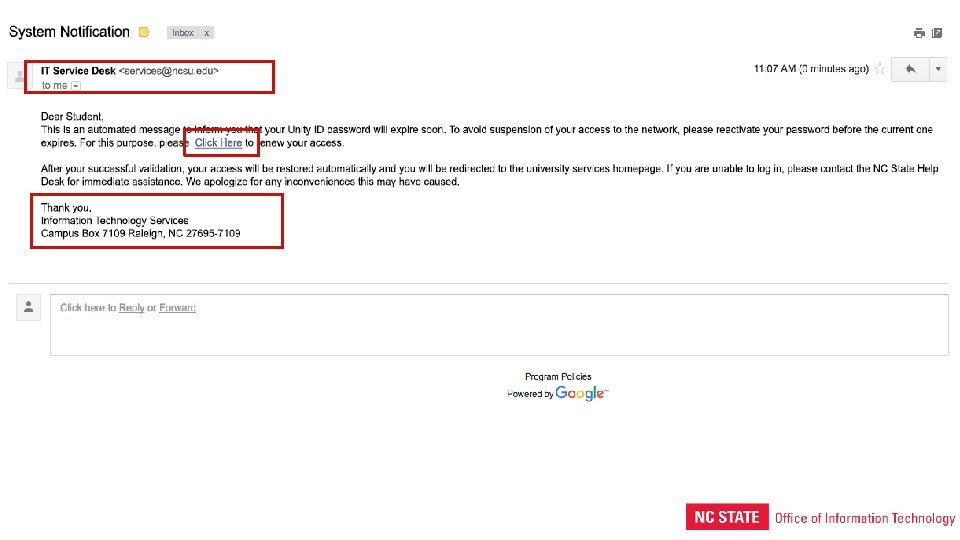
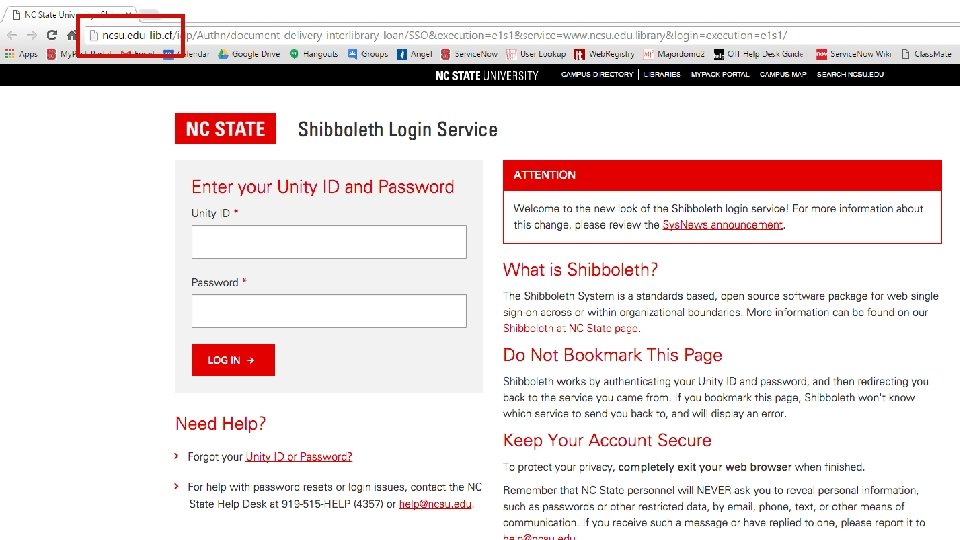

What I like: • Active learning • High applicability • Empowering
Before

Typical Phish • Spelling/grammar mistakes • “Doom and gloom” • Hidden links • Not addressed to you • Looks “off” • Suspicious senders
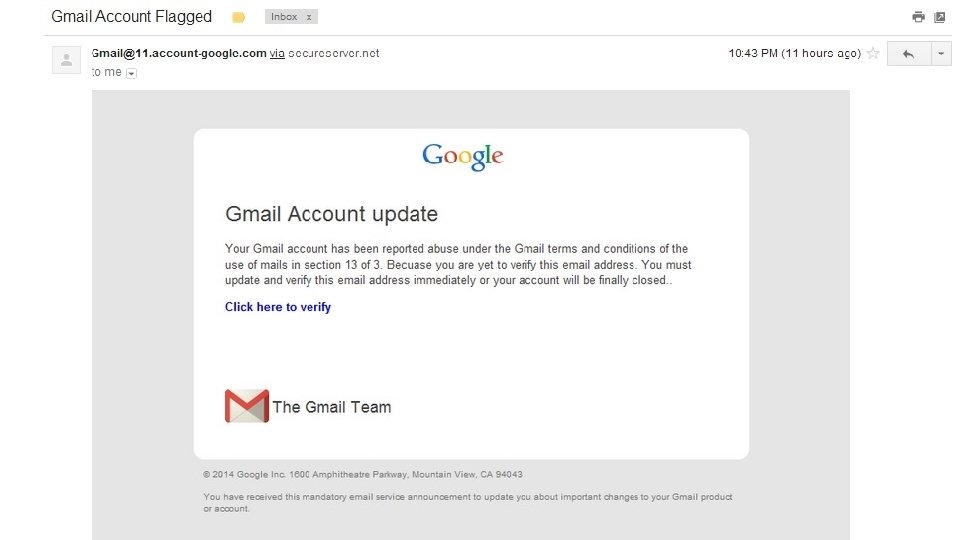

Tips for Simulations • Make (some of) them hard! • Use local examples • Be encouraging & humanizing

Simulation Variants

Spot the Phish https: //www. opendns. com/phishing-quiz/ https: //www. sonicwall. com/en-us/phishing-iq-test https: //www. phishingbox. com/phishing-test

#4: Solve the Problem

Non-negotiable! • Concrete & actionable solutions • Capitalize on motivation

Drawbacks? • Might take longer • Easy to derail • Be careful with Goofus

Questions? (we’re not done yet)

Workshop!

How it works: • Brainstorm multiple ideas! • 30 seconds to think of 3 ideas • 3 minutes to discuss with table • Share with room
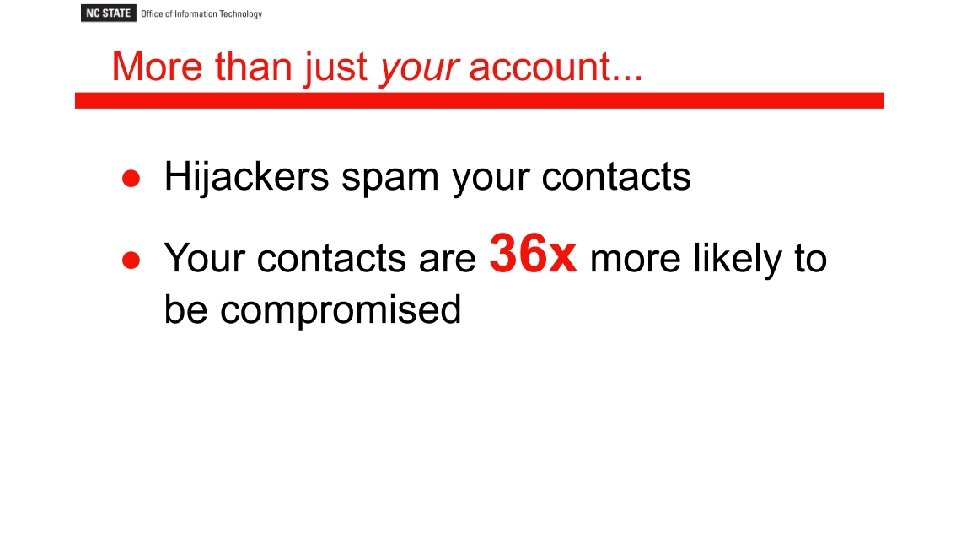

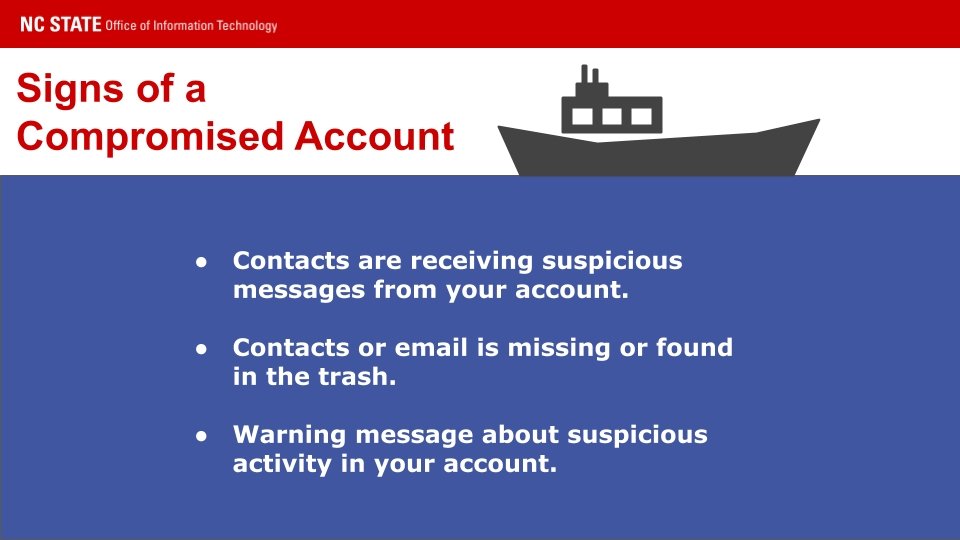
- Slides: 57