Basics Of Symmetric Encryption Network Security 1 Basics
Basics Of Symmetric Encryption Network Security 1
Basics Of Symmetric Encryption Objectives of the Topic • After completing this topic, a student will be able to – describe basics of symmetric encryption. 2
Basics Of Symmetric Encryption Figures and material in this topic have been • adapted from “Network Security Essentials: Applications and Standards”, 2014, by William Stallings. 3
Basics Of Symmetric Encryption • Symmetric encryption, or single-key encryption, was the only type of encryption in use prior to the development of public key encryption in the 1970 s. 4
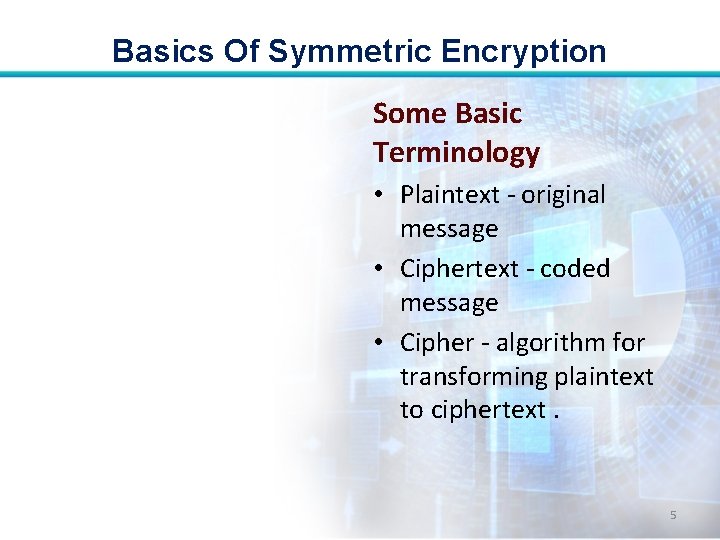
Basics Of Symmetric Encryption Some Basic Terminology • Plaintext - original message • Ciphertext - coded message • Cipher - algorithm for transforming plaintext to ciphertext. 5
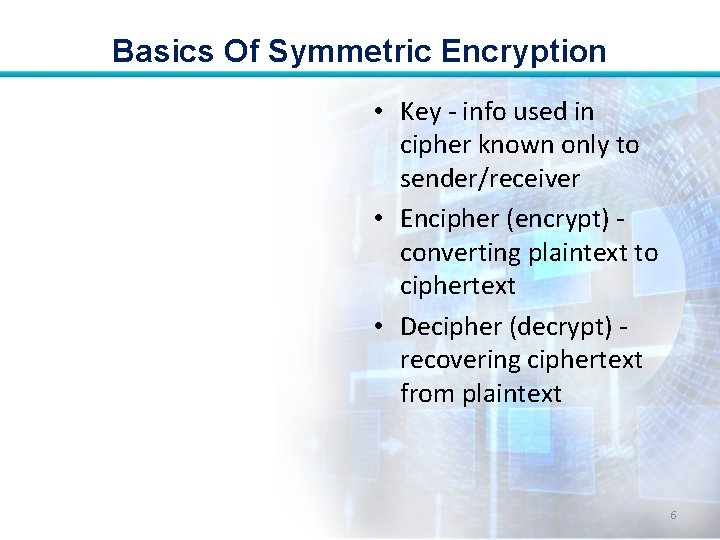
Basics Of Symmetric Encryption • Key - info used in cipher known only to sender/receiver • Encipher (encrypt) converting plaintext to ciphertext • Decipher (decrypt) recovering ciphertext from plaintext 6
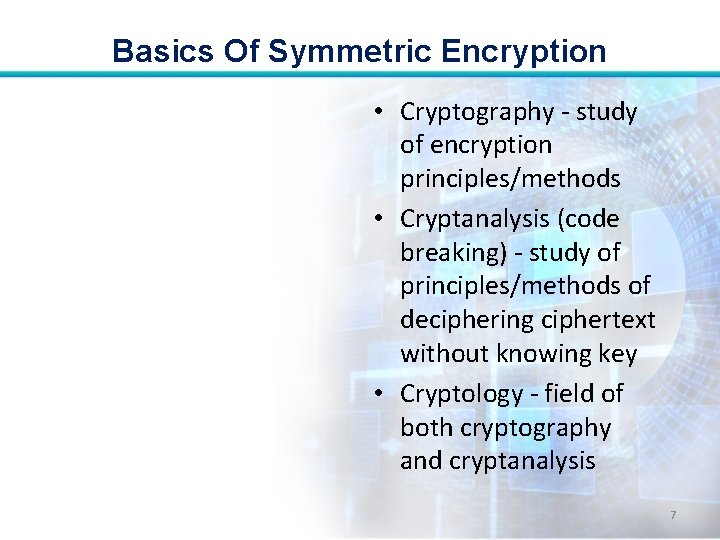
Basics Of Symmetric Encryption • Cryptography - study of encryption principles/methods • Cryptanalysis (code breaking) - study of principles/methods of deciphering ciphertext without knowing key • Cryptology - field of both cryptography and cryptanalysis 7
Basics Of Symmetric Encryption Principles • A symmetric encryption scheme has five ingredients 8
Basics Of Symmetric Encryption Plaintext • This is the original intelligible message or data that is fed into the algorithm as input. Encryption Algorithm • It performs various substitutions and transformations on the plaintext. 9
Basics Of Symmetric Encryption Secret Key • It is also input to the encryption algorithm. The key is a value independent of the plaintext and of the algorithm. 10
Basics Of Symmetric Encryption Secret Key … • The algorithm will produce a different output depending on the specific key being used at the time. • The exact substitutions and transformations performed depend on the key. 11
Basics Of Symmetric Encryption Ciphertext • This is the scrambled message produced as output. It depends on the plaintext and the secret key. For a given message, two different keys will produce two different ciphertexts ( is unintelligible). 12
Basics Of Symmetric Encryption Decryption algorithm • This is essentially the encryption algorithm run in reverse. • It takes the ciphertext and the secret key and produces the original plaintext. 13
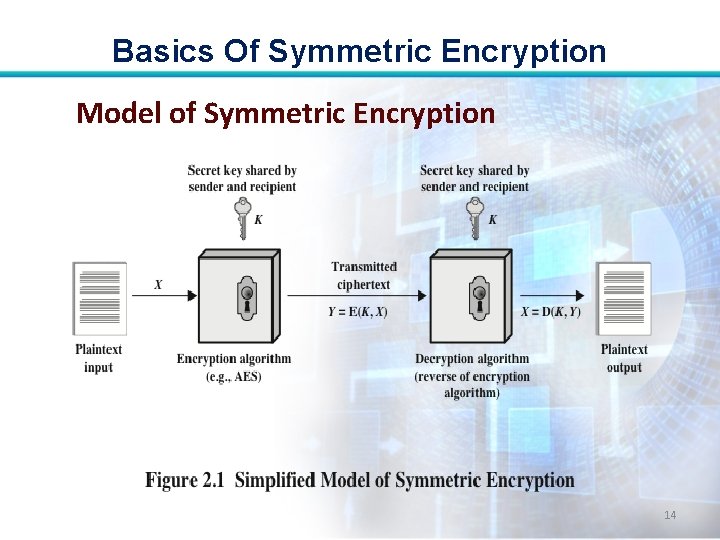
Basics Of Symmetric Encryption Model of Symmetric Encryption 14
Basics Of Symmetric Encryption Requirements • Two requirements for secure use of symmetric encryption 15
Basics Of Symmetric Encryption • 1. We need a strong encryption algorithm. • An opponent should be unable to decrypt ciphertext or discover the key even if he is in possession of a no. of ciphertexts together with the plaintext that produced each ciphertext. 16
Basics Of Symmetric Encryption • 2. Sender and receiver must have obtained copies of the secret key in a secure fashion and must keep the key secure. • If someone discovers the key and knows the algorithm, all communication using this key is readable. 17
Basics Of Symmetric Encryption • The security of symmetric encryption depends on the secrecy of the key, not the secrecy of the algorithm 18
Basics Of Symmetric Encryption • It is impractical to decrypt a message on the basis of the ciphertext plus knowledge of the encryption/decryption algorithm. • This makes it feasible for widespread use. 19
Basics Of Symmetric Encryption End • Manufacturers can and have developed low-cost chip implementations of data encryption algorithms. • These chips are widely available and incorporated into a number of products. 20
- Slides: 20