Basic Network Encryption CIS 6395 Incident Response Technologies

Basic Network Encryption CIS 6395, Incident Response Technologies Fall 2016, Dr. Cliff Zou

Acknowledgement Part of the slides come from slides provided in well-known networking book: ◦ Computer Networking: A Top Down Approach Featuring the Internet, J. Kurose & K. Ross, Addison Wesley, 6 th ed. , 2013
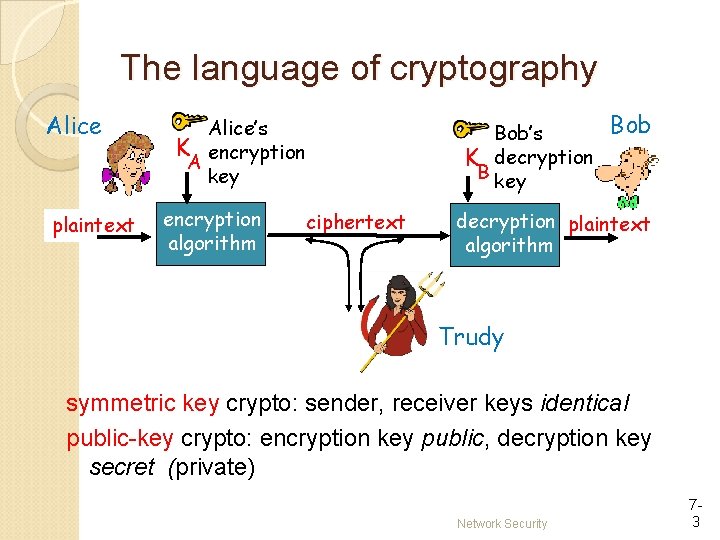
The language of cryptography Alice plaintext Alice’s K encryption A key encryption algorithm Bob’s K decryption B key ciphertext Bob decryption plaintext algorithm Trudy symmetric key crypto: sender, receiver keys identical public-key crypto: encryption key public, decryption key secret (private) Network Security 73
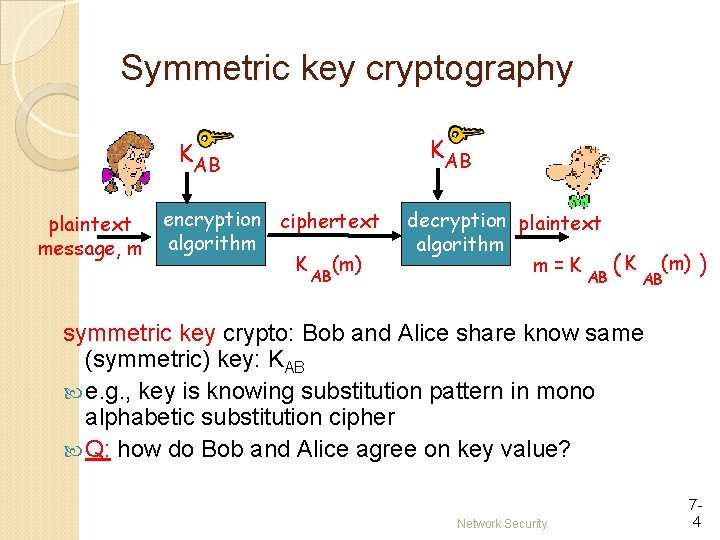
Symmetric key cryptography KAB plaintext message, m encryption ciphertext algorithm K (m) AB decryption plaintext algorithm m=K AB ( K (m) ) AB symmetric key crypto: Bob and Alice share know same (symmetric) key: KAB e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher Q: how do Bob and Alice agree on key value? Network Security 74
![Symmetric key crypto: DES: Data Encryption Standard US encryption standard [NIST 1993] 56 -bit Symmetric key crypto: DES: Data Encryption Standard US encryption standard [NIST 1993] 56 -bit](http://slidetodoc.com/presentation_image/1434d1af844a3add3937171f24c1ae5d/image-5.jpg)
Symmetric key crypto: DES: Data Encryption Standard US encryption standard [NIST 1993] 56 -bit symmetric key, 64 -bit plaintext input ◦ no known “backdoor” decryption approach ◦ Too short for current computing power Making DES more secure while still using legacy software or hardware (3 DES): ◦ use three keys sequentially on each datum ◦ Key length increases three times Network Security 75
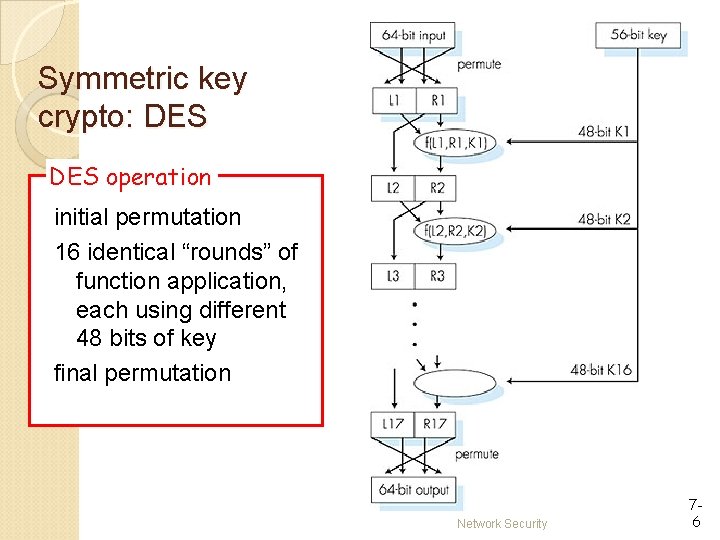
Symmetric key crypto: DES operation initial permutation 16 identical “rounds” of function application, each using different 48 bits of key final permutation Network Security 76
AES: Advanced Encryption Standard new (Nov. 2001) symmetric-key NIST standard, replacing DES processes data in 128 bit blocks 128, 192, or 256 bit keys There are many other similar and strong symmetric encryption algorithms: ◦ https: //en. wikipedia. org/wiki/Symmetric-key_algorithm ◦ Blowfish, twofish, serpent…. Network Security 77
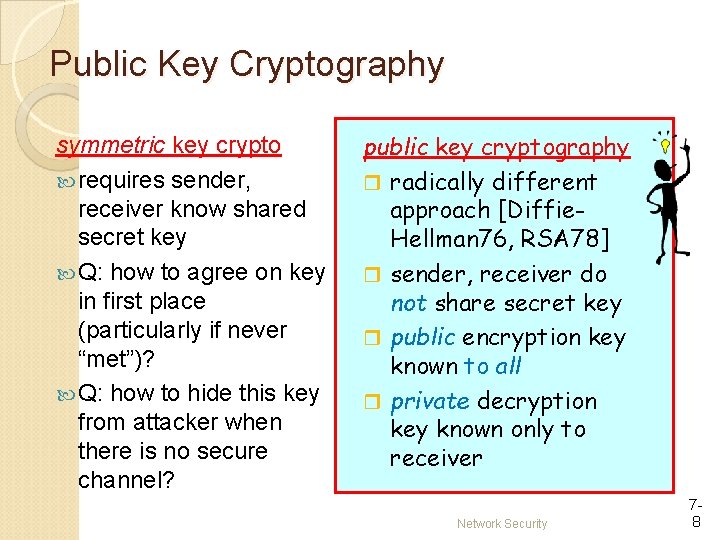
Public Key Cryptography symmetric key crypto requires sender, receiver know shared secret key Q: how to agree on key in first place (particularly if never “met”)? Q: how to hide this key from attacker when there is no secure channel? public key cryptography r radically different approach [Diffie. Hellman 76, RSA 78] r sender, receiver do not share secret key r public encryption key known to all r private decryption key known only to receiver Network Security 78
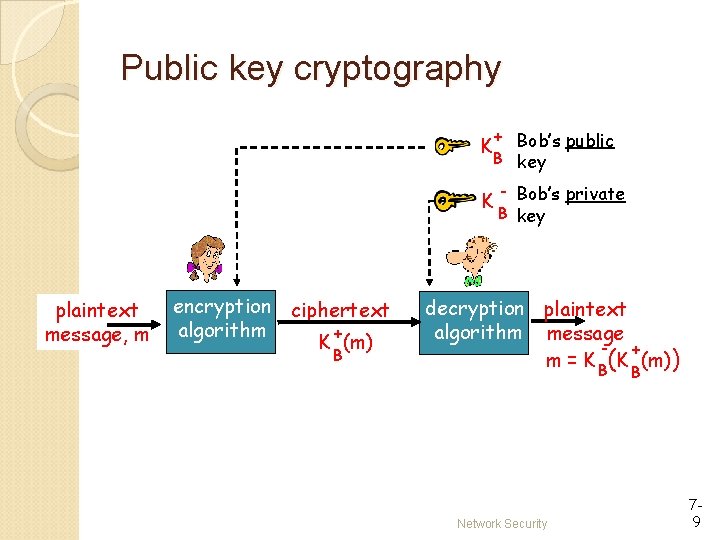
Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B Network Security 79
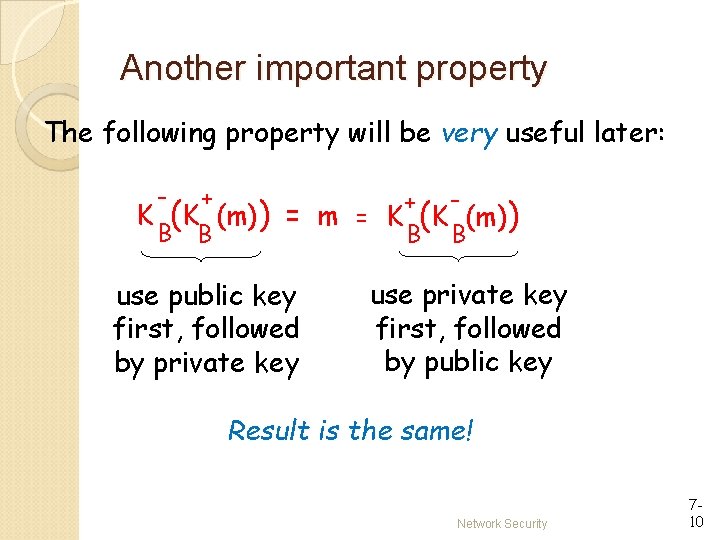
Another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! Network Security 710
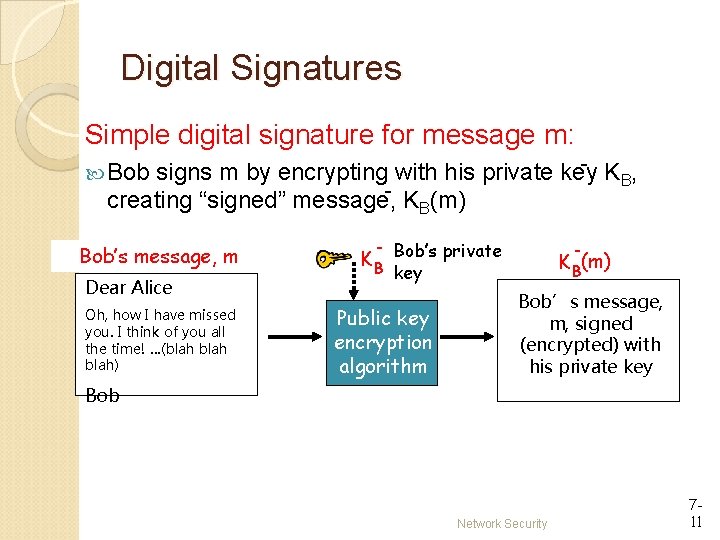
Digital Signatures Simple digital signature for message m: - K , signs m by encrypting with his private key B creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) K B Bob’s private K B(m) key Public key encryption algorithm Bob’s message, m, signed (encrypted) with his private key Bob Network Security 711

Digital Signatures (more) Suppose - Alice receives msg m, digital signature KB(m) Alice verifies m signed by Bob by applying Bob’s public + + key KB to KB(m) then checks- KB(KB(m) ) = m. If + - KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü No one else signed m. ü Bob signed m and not m’. Non-repudiation: ü Alice can take m, and signature- KB(m) to court and prove that Bob signed m. Network Security 712
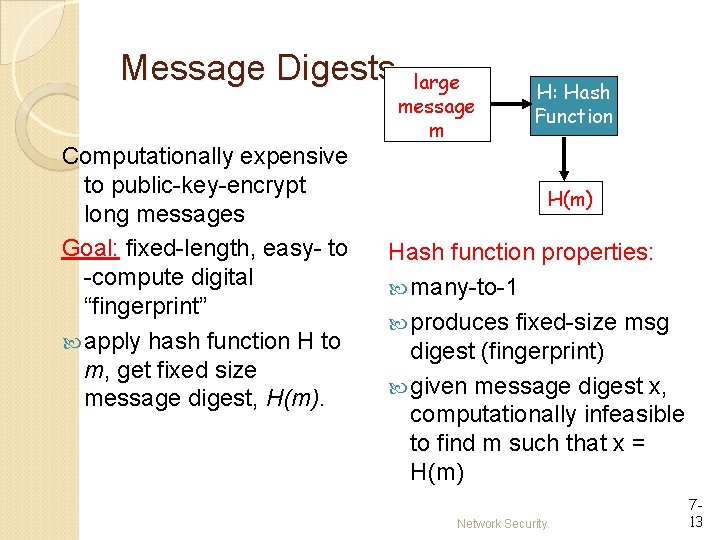
Message Digests Computationally expensive to public-key-encrypt long messages Goal: fixed-length, easy- to -compute digital “fingerprint” apply hash function H to m, get fixed size message digest, H(m). large message m H: Hash Function H(m) Hash function properties: many-to-1 produces fixed-size msg digest (fingerprint) given message digest x, computationally infeasible to find m such that x = H(m) Network Security 713
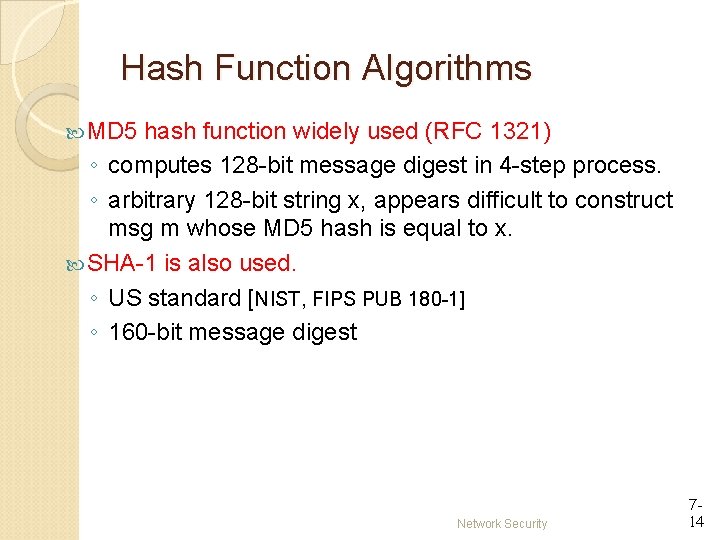
Hash Function Algorithms MD 5 hash function widely used (RFC 1321) ◦ computes 128 -bit message digest in 4 -step process. ◦ arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x. SHA-1 is also used. ◦ US standard [NIST, FIPS PUB 180 -1] ◦ 160 -bit message digest Network Security 714
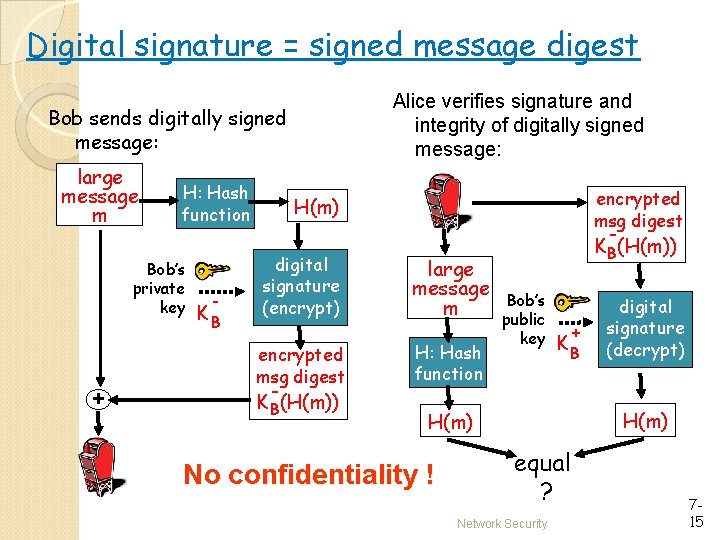
Digital signature = signed message digest Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: Hash function KB(H(m)) Bob’s public key H(m) No confidentiality ! + KB digital signature (decrypt) equal ? Network Security 715

Trusted Intermediaries Public key problem: When Alice obtains Bob’s public key (from web site, e-mail, diskette), how does she know it is Bob’s public key, not Trudy’s? Solution: trusted certification authority (CA) Network Security 716
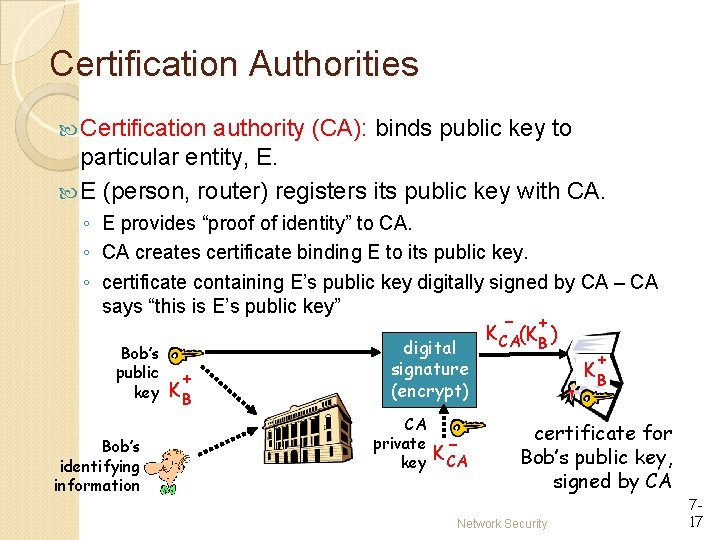
Certification Authorities Certification authority (CA): binds public key to particular entity, E. E (person, router) registers its public key with CA. ◦ E provides “proof of identity” to CA. ◦ CA creates certificate binding E to its public key. ◦ certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” - + K CA(KB ) Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA Network Security 717
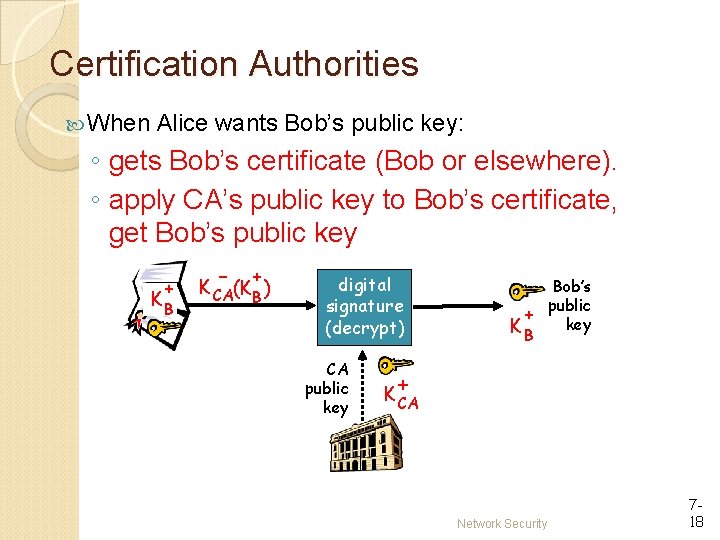
Certification Authorities When Alice wants Bob’s public key: ◦ gets Bob’s certificate (Bob or elsewhere). ◦ apply CA’s public key to Bob’s certificate, get Bob’s public key + KB - + K CA(KB ) digital signature (decrypt) CA public key Bob’s public + key KB + K CA Network Security 718
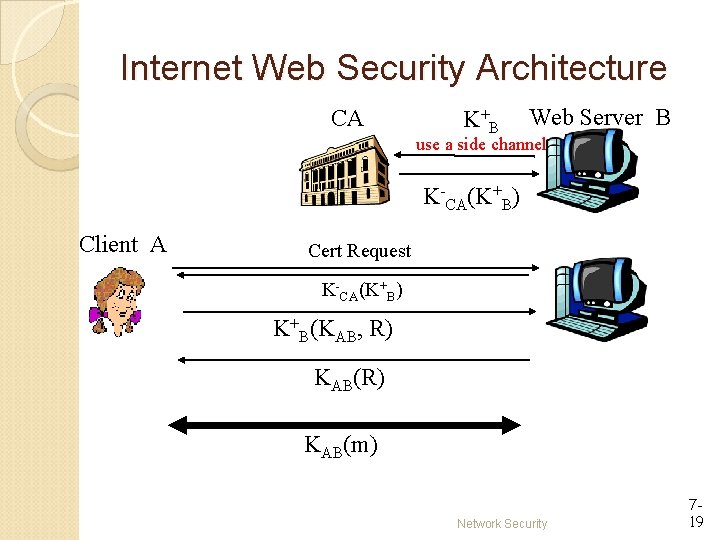
Internet Web Security Architecture CA K+ B Web Server B use a side channel K-CA(K+B) Client A Cert Request K-CA(K+B) K+B(KAB, R) KAB(m) Network Security 719
Internet Web Security Conditions Clients’ web browsers have built-in CAs are trustable Web servers have certificates in CAs. Q: What if a server has no certificate? ◦ Example: SSH servers Network Security 720
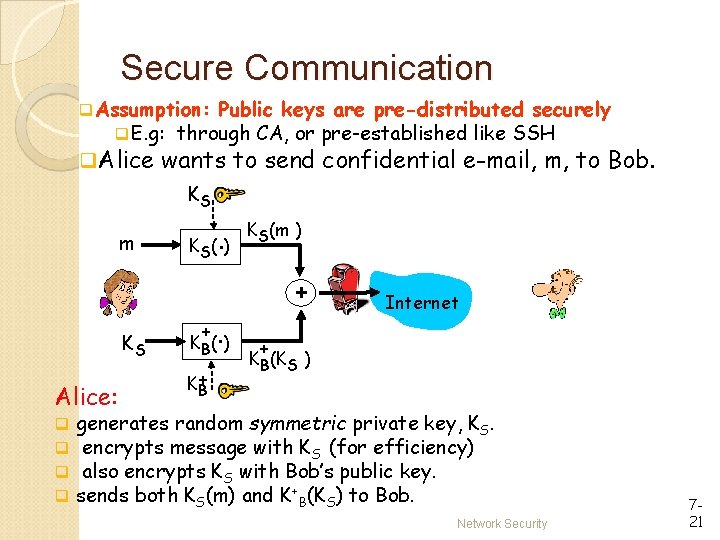
Secure Communication q. Assumption: Public keys are pre-distributed securely q. E. g: through CA, or pre-established like SSH q. Alice wants to send confidential e-mail, m, to Bob. KS m KS Alice: q q . K S( ) + . K B( ) K+ B KS(m ) + Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and K+B(KS) to Bob. Network Security 721
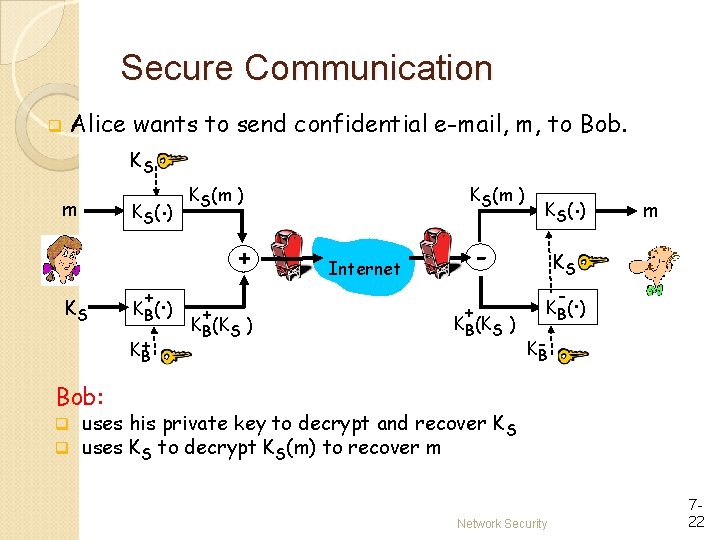
Secure Communication q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m Network Security 722
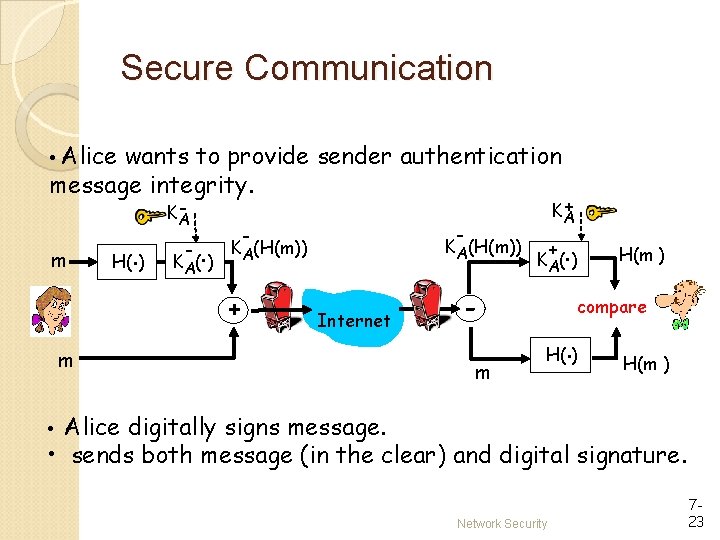
Secure Communication • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m + m . K A( ) H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. Network Security 723
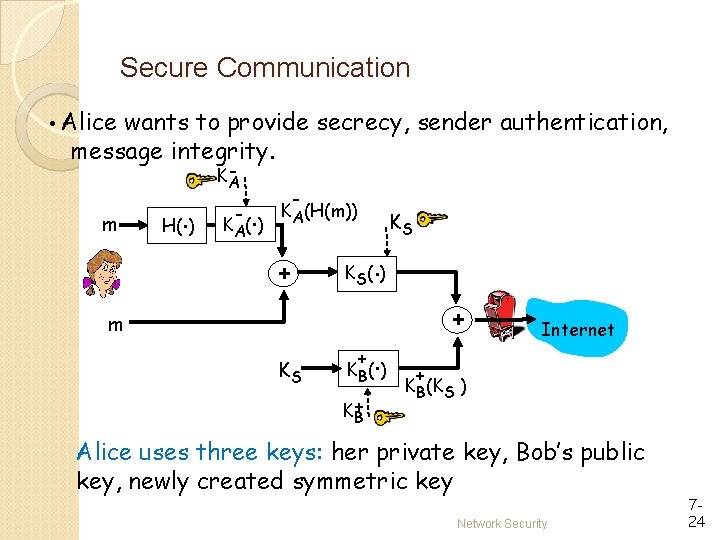
Secure Communication • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key Network Security 724
- Slides: 24