Bart Miller October 22 nd 2012 Xoar Outline

Bart Miller – October 22 nd, 2012 Xoar

Outline �TCB & Threat Model �Xen Platform �Xoar Architecture Overview �Xoar Components �Design Goals �Results Security Vulnerability Mitigation Performance

TCB �Trusted Computing Base is defined as “the totality of protection mechanisms within a computer system – including hardware, firmware, and software – the combination of which is responsible for enforcing a security policy. ” �Xen, by virtue of privilege, is part of the TCB

TCB �In Xen, all components operate under a monolithic trust domain �Compromise of any component yields two benefits: Gain privilege level of component Access its interfaces to other components
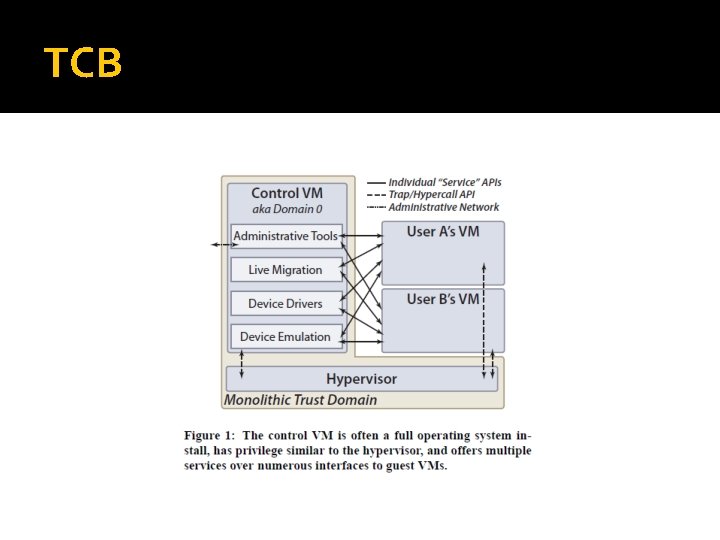
TCB

Threat Model �Assumption #1: Administrators are not a concern Business imperative �Assumption #2: Malicious guest VM Violate data integrity or confidentiality Exploiting code �Assumption #3: The control VM will contain bugs
Xen Platform – A brief revisit �Device drivers Virtualized, passed-through, or emulated �Xen. Store Hierarchical key-value store System-wide registry Most critical component ▪ Vulnerable to Do. S attacks ▪ Perform most administrative operations
Xen Platform �Toolstack Administrative functions Create, destroy, managing resources and privilege for guest VMs �System Boot Starts Dom. O process, initialize hardware
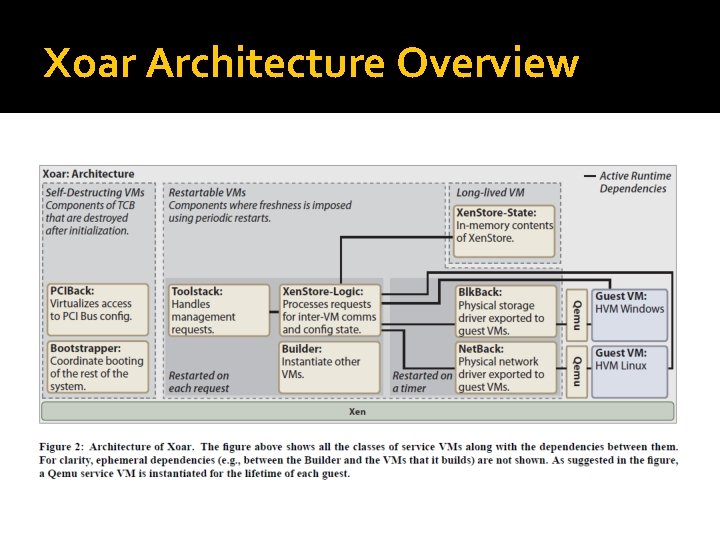
Xoar Architecture Overview
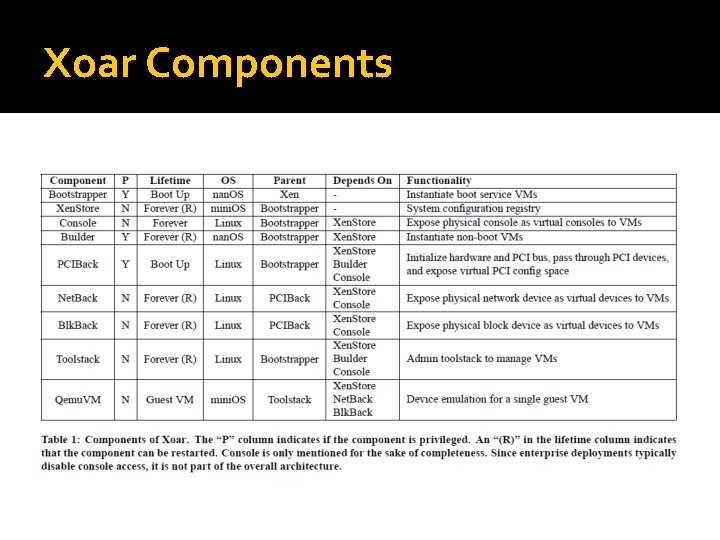
Xoar Components

Design Goals �Reduce privilege Each component should only have the privileges essential to its purpose Each component should only expose interfaces when necessary

Design Goals �Reduce sharing Sharing components should be avoided wherever it is reasonable Any sharing of components must be explicit Allows for logging and auditing in the event of a compromise
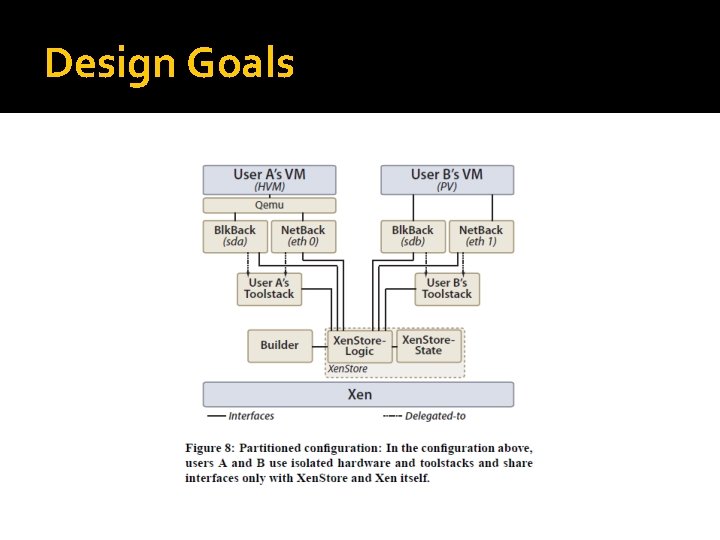
Design Goals
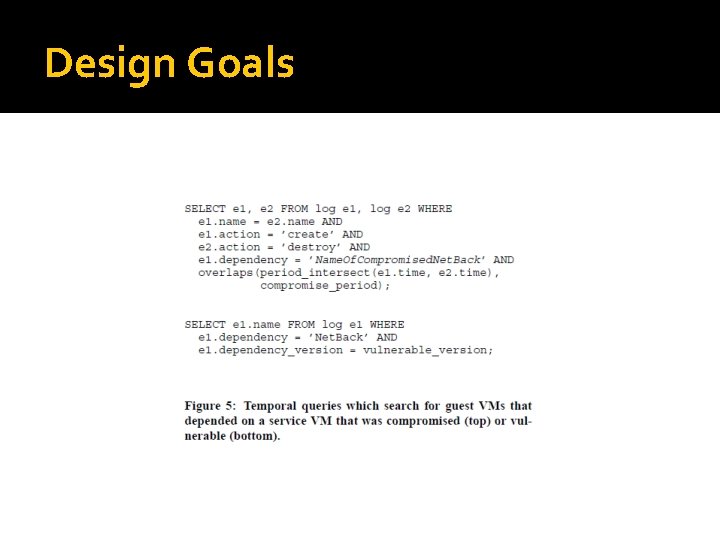
Design Goals
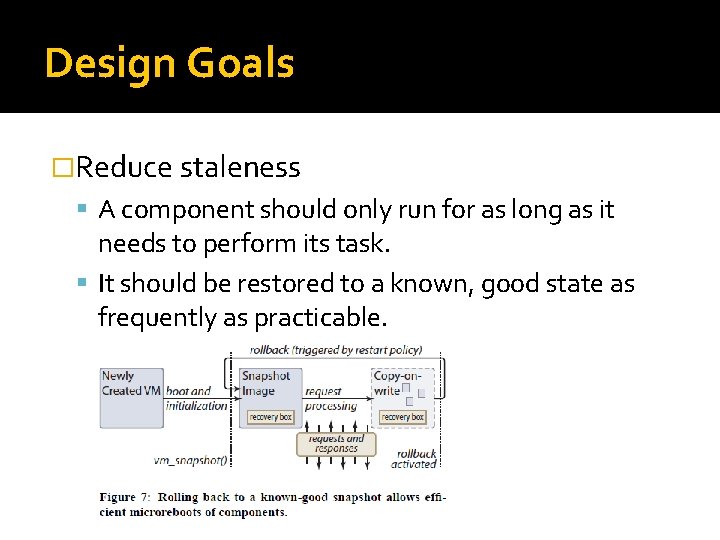
Design Goals �Reduce staleness A component should only run for as long as it needs to perform its task. It should be restored to a known, good state as frequently as practicable.
Results - Security �Reduced TCB Bootstrapper, PCIBack, and Builder are most privileged components Bootstrapper and PCIBack destroyed once initialized TCB reduced ▪ Linux: 7. 6 M Lo. C ▪ Builder: 13, 5 k Lo. C (Builder)
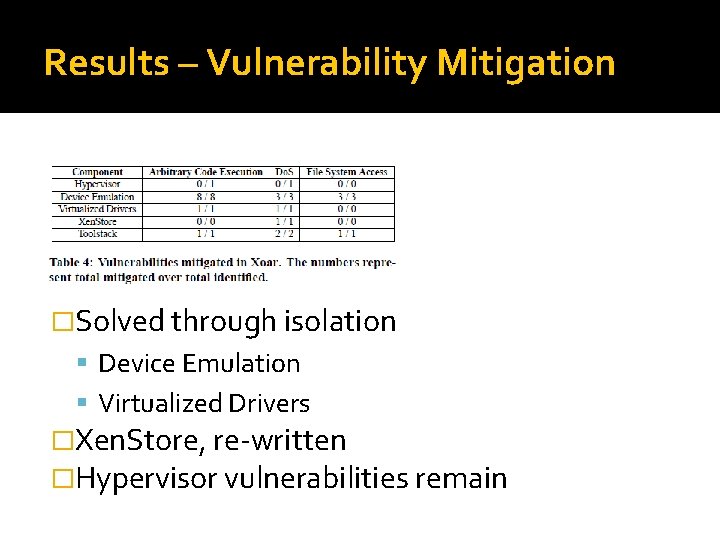
Results – Vulnerability Mitigation �Solved through isolation Device Emulation Virtualized Drivers �Xen. Store, re-written �Hypervisor vulnerabilities remain
Results - Performance �Test system Ca. 2011 server Quad-core Xeon, 4 Gb RAM All virtualization features enabled �Memory overhead 512 Mb – 896 Mb in Xoar vs. 750 Mb in Xen. Server
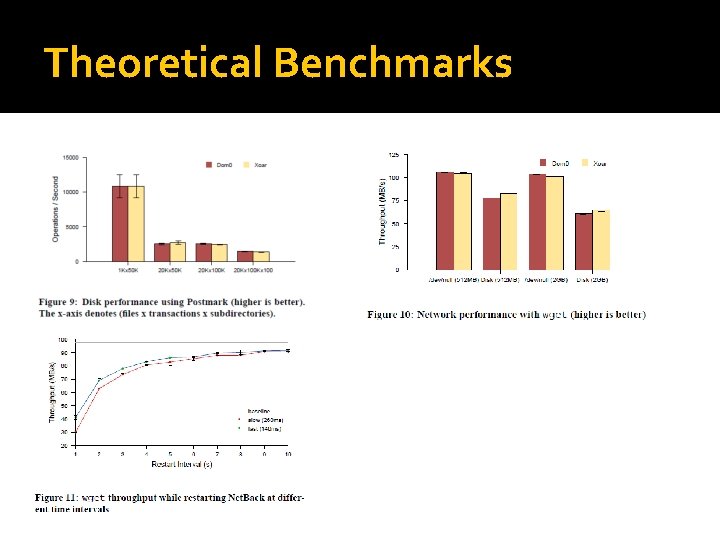
Theoretical Benchmarks
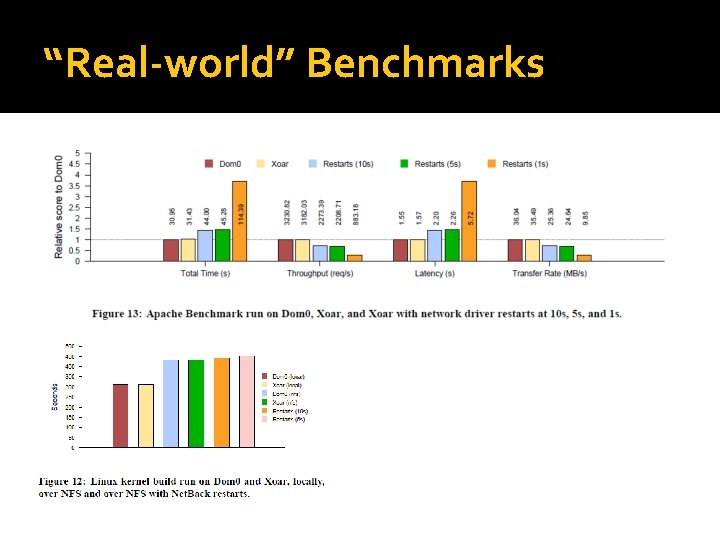
“Real-world” Benchmarks
Questions �Any questions?
- Slides: 21