AZURE ENCRYPTION Anthony Turner anthturner com encryption to

![encryption [to change information from one form to another especially to hide its meaning] encryption [to change information from one form to another especially to hide its meaning]](https://slidetodoc.com/presentation_image_h/b59c97e8cad0906f9b290408c355cd6a/image-2.jpg)














- Slides: 27

AZURE ENCRYPTION Anthony Turner anthturner. com
![encryption to change information from one form to another especially to hide its meaning encryption [to change information from one form to another especially to hide its meaning]](https://slidetodoc.com/presentation_image_h/b59c97e8cad0906f9b290408c355cd6a/image-2.jpg)
encryption [to change information from one form to another especially to hide its meaning]

WHY DO I CARE? “I’m only one person on a planet of over 7 billion; no one is looking at me. ”

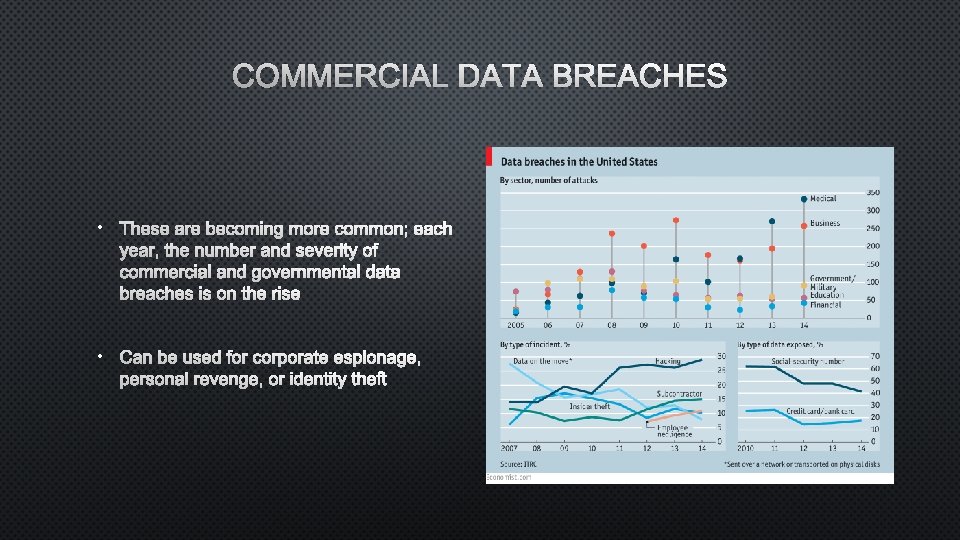
COMMERCIAL DATA BREACHES • THESE ARE BECOMING MORE COMMON; EACH YEAR, THE NUMBER AND SEVERITY OF COMMERCIAL AND GOVERNMENTAL DATA BREACHES IS ON THE RISE • CAN BE USED FOR CORPORATE ESPIONAGE, PERSONAL REVENGE, OR IDENTITY THEFT

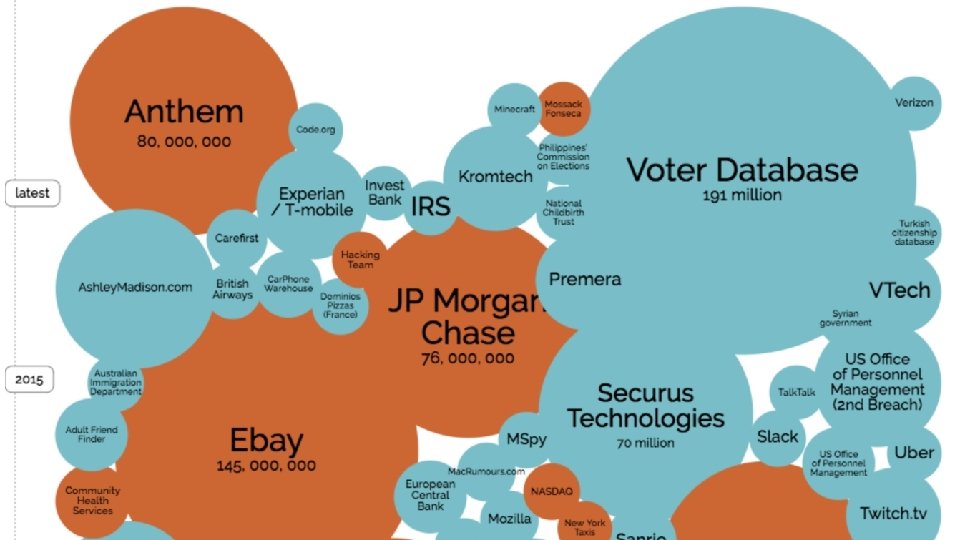
http: //www. informationisbeautiful. net/visualizations/worlds-biggest-data-breaches-hacks/

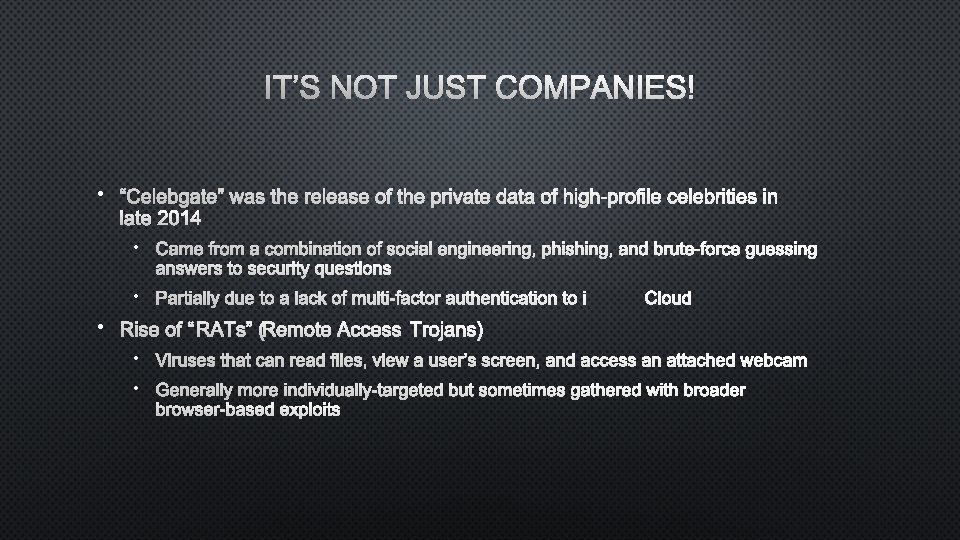
IT’S NOT JUST COMPANIES! • “CELEBGATE” WAS THE RELEASE OF THE PRIVATE DATA OF HIGH-PROFILE CELEBRITIES IN LATE 2014 • CAME FROM A COMBINATION OF SOCIAL ENGINEERING, PHISHING, AND BRUTE-FORCE GUESSING ANSWERS TO SECURITY QUESTIONS • PARTIALLY DUE TO A LACK OF MULTI-FACTOR AUTHENTICATION TOCI LOUD • RISE OF “RATS” (REMOTE ACCESS TROJANS) • VIRUSES THAT CAN READ FILES, VIEW A USER’S SCREEN, AND ACCESS AN ATTACHED WEBCAM • GENERALLY MORE INDIVIDUALLY-TARGETED BUT SOMETIMES GATHERED WITH BROADER BROWSER-BASED EXPLOITS

GOVERNMENTS CAN EVEN STORE YOUR DATA… • NSA $1. 5 B DATA CENTER INUTAH, COMPLETED CONSTRUCTION IN MAY 2014 • ARCHITECTED TO SUPPORT STORING 1 YOTTABYTE OF DATA • 1 YOTTABYTE IS OVER 5700 X THE ANNUAL HARD DRIVE PRODUCTION OF SEAGATE • DESIGNED TO STORE COMPLETE CONTENTS OF E-MAIL, CELL PHONE CALLS, GOOGLE SEARCHES, AND PERSONAL DATA TRAILS

… BUT CAN THEY PROTECT IT? • EDWARD SNOWDEN • RELEASED AROUND 1. 7 MILLIONNSA DOCUMENTS TO THE MEDIA IN 2013 • OFFICE OF PERSONNEL MANAGEMENT • HACKERS STOLE PERSONALLY IDENTIFIABLE INFORMATION FOR OVER 4 MILLION GOVERNMENT EMPLOYEES

https: //cybermap. kaspersky. com/

WHY DO I CARE? ENCRYPTION CAN LIMIT, MITIGATE, OR PREVENT DATA LEAKS FOR EVERYONE.

TYPES OF ALGORITHMS

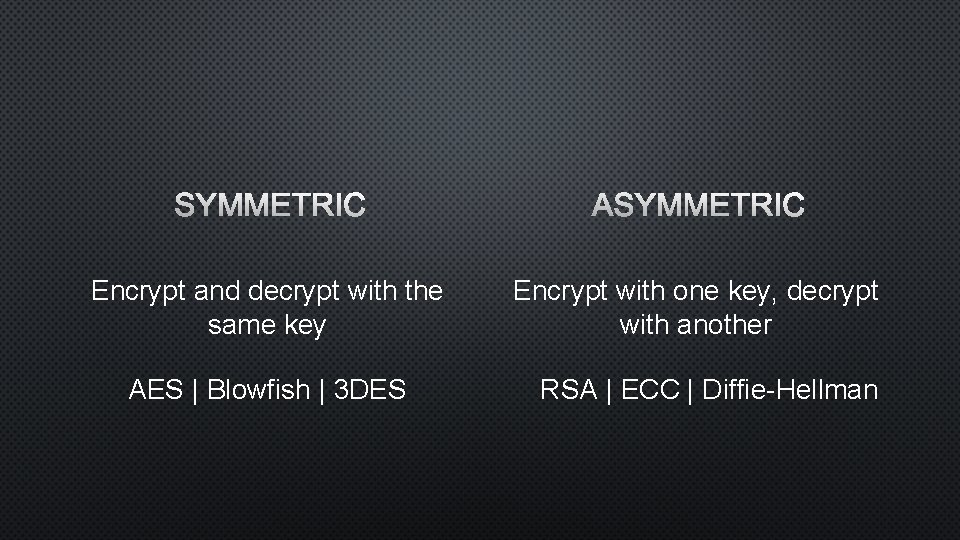
Encrypt and decrypt with the same key AES | Blowfish | 3 DES Encrypt with one key, decrypt with another RSA | ECC | Diffie-Hellman

Extremely fast conversion of data to cipher text If data is ever cracked the key is obtained, and all other encrypted data using this key can be deciphered. May be mitigated with salting techniques.

S o ort f Easy to compute in one direction, difficult in the opposite direction Allows flexibility in key management

Public Key Allows encryption but not decryption Can be safely shared without compromising encrypted data Often publicly indexed as “fingerprints” for people to search for others Private Key Allows decryption but not encryption Kept secure

COMBINING SPEED AND SECURITY: THE ENVELOPE TECHNIQUE • A SINGLE-USE, SYMMETRIC, VERY LONG/COMPLEX CONTENT ENCRYPTION KEY (CEK) IS GENERATED AND USED TO ENCRYPT THE DATA • A (POTENTIALLY) MULTI-USE, ASYMMETRIC KEY , ENCRYPTION KEY (KEK) IS USED TO ENCRYPT THE CEK • THE ENCRYPTED CEK IS STORED WITH THE ENCRYPTED DATA IN STORAGE • THE KEK IS STORED SOMEWHERE SAFE, AND USED TO DECRYPT CEK THE FOR FUTURE DATA ACCESS

You do not want to come up with your own implementation Rely on trusted implementations designed for your scenario

MAKE IT EASY WITH THE RIGHT TOOLS Client side encryption for Azure storage Key management with Azure Key Vault

CLIENT-SIDE ENCRYPTION WITH THE AZURE SDK. Net and Java Blobs | Tables | Queues Uses envelope technique https: //azure. microsoft. com/en-us/documentation/articles/storage-client-side-encryption/

AZURE KEY VAULT MANAGING YOUR KEYS FOR SECURE ACCESS, ANYWHERE

AZURE KEY VAULT • HOSTED IN AZURE ON DEDICATED SYSTEMS AND HSMS (HARDWARE SECURITY MODULES) • POWERS MOST OF THE ENCRYPTION-AWARE SERVICES PROVIDED BY AZURE • AVAILABLE TO DEVELOPERS FOR USE IN THEIR OWN APPLICATIONS

KEY VAULT STORAGE TYPES KEYS SECRETS • RSA-COMPATIBLE KEY MATERIAL • ANY STRING UP TO 25 KB • CAN ENCODE/DECODE DATA • DEVELOPER CAN SPECIFY A CONTENT TYPE • CAN DIGITALLY SIGN/VERIFY DATA TO HELP IDENTIFY THE DATA SCHEME ON RETRIEVAL • HIDES KEY MATERIAL FROM EVERYONE – KEYS ARE GENERATED AND STORED ONLY INKEY VAULT • SUPPORTS TIME-WINDOW ACCESS

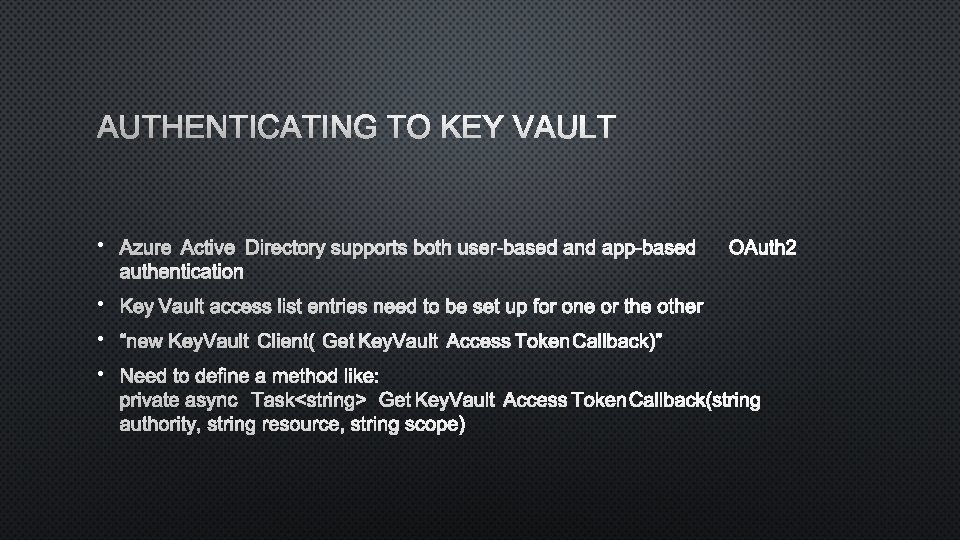
AUTHENTICATING TO KEY VAULT • AZURE ACTIVE DIRECTORY SUPPORTS BOTH USER-BASED AND APP-BASEDOAUTH 2 AUTHENTICATION • KEY VAULT ACCESS LIST ENTRIES NEED TO BE SET UP FOR ONE OR THE OTHER • “NEW KEYVAULTCLIENT(GETKEYVAULTACCESSTOKENCALLBACK)” • NEED TO DEFINE A METHOD LIKE: PRIVATE ASYNC TASK<STRING>GETKEYVAULTACCESSTOKENCALLBACK(STRING AUTHORITY, STRING RESOURCE, STRING SCOPE)

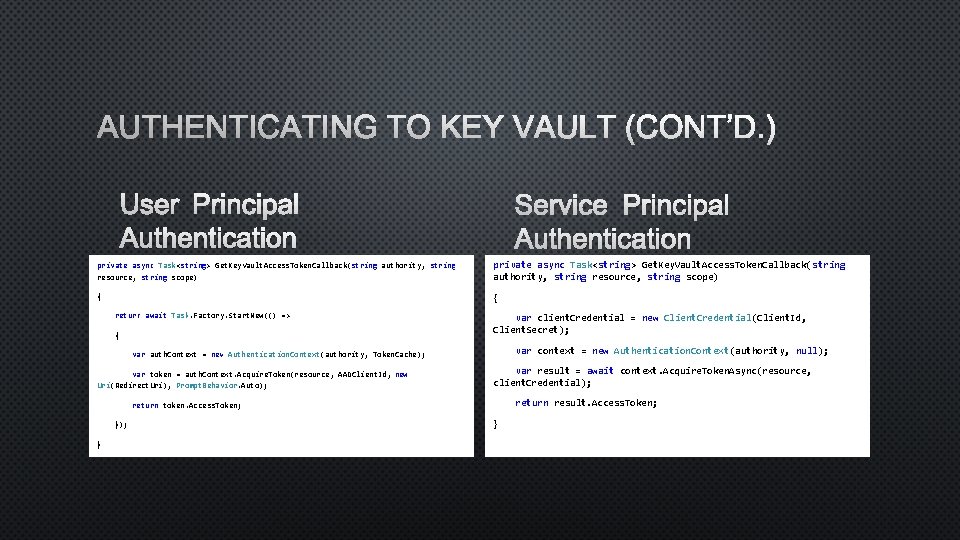
AUTHENTICATING TO KEY VAULT (CONT’D. ) USER PRINCIPAL AUTHENTICATION SERVICE PRINCIPAL AUTHENTICATION private async Task<string> Get. Key. Vault. Access. Token. Callback(string authority, string resource, string scope) { { return await Task. Factory. Start. New(() => { var client. Credential = new Client. Credential(Client. Id, Client. Secret); var context = new Authentication. Context(authority, null); var auth. Context = new Authentication. Context(authority, Token. Cache); var token = auth. Context. Acquire. Token(resource, AADClient. Id, new Uri(Redirect. Uri), Prompt. Behavior. Auto); var result = await context. Acquire. Token. Async(resource, client. Credential); return result. Access. Token; return token. Access. Token; }); } }

COMMANDS • CREATE OR UPDATE A SECRET BY NAME • await key. Vault. Client. Secret. Async("Contoso. Users", "Jane. Doe", "Janes. Password 123!"); • CREATE A KEY • await key. Vault. Client. Create. Key. Async("Contoso. Keys", "Jane. Doe", "rsa"); • RETRIEVE THE PUBLIC COMPONENT OF THE KEY • await key. Vault. Client. Get. Key. Async("Contoso. Users", "Jane. Doe. Email");

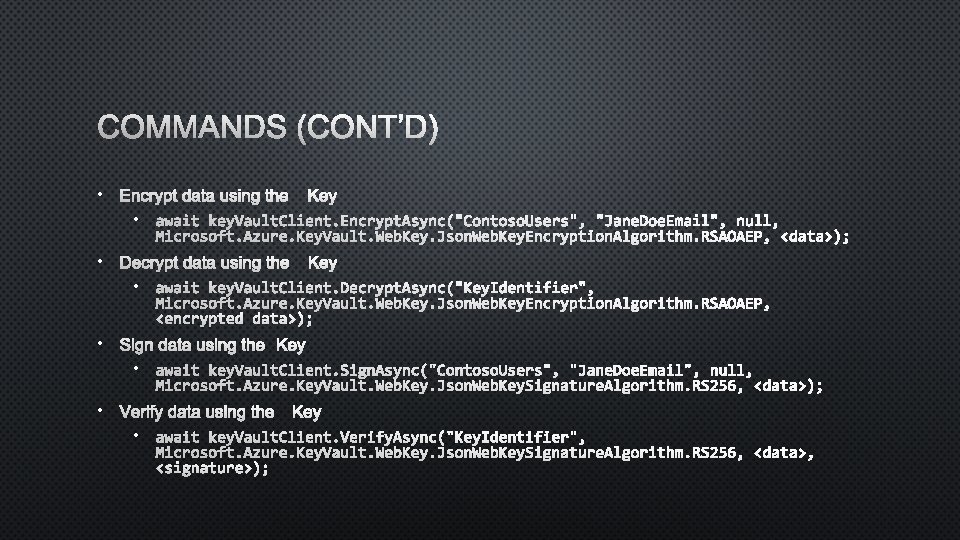
COMMANDS (CONT’D) • ENCRYPT DATA USING THE KEY • await key. Vault. Client. Encrypt. Async("Contoso. Users", "Jane. Doe. Email", null, Microsoft. Azure. Key. Vault. Web. Key. Json. Web. Key. Encryption. Algorithm. RSAOAEP, <data>); • DECRYPT DATA USING THE KEY • await key. Vault. Client. Decrypt. Async("Key. Identifier", Microsoft. Azure. Key. Vault. Web. Key. Json. Web. Key. Encryption. Algorithm. RSAOAEP, <encrypted data>); • SIGN DATA USING THE KEY • await key. Vault. Client. Sign. Async("Contoso. Users", "Jane. Doe. Email", null, Microsoft. Azure. Key. Vault. Web. Key. Json. Web. Key. Signature. Algorithm. RS 256, <data>); • VERIFY DATA USING THE KEY • await key. Vault. Client. Verify. Async("Key. Identifier", Microsoft. Azure. Key. Vault. Web. Key. Json. Web. Key. Signature. Algorithm. RS 256, <data>, <signature>);

KEY VAULT MANAGEMENT • POWERSHELL • C# SDK (NON-UWP) • HTTP: //WWW. GITHUB. COM/MZXGIANTA / ZUREKEYVAULTMANAGER