Azure AD signin The role of Azure AD



















- Slides: 57


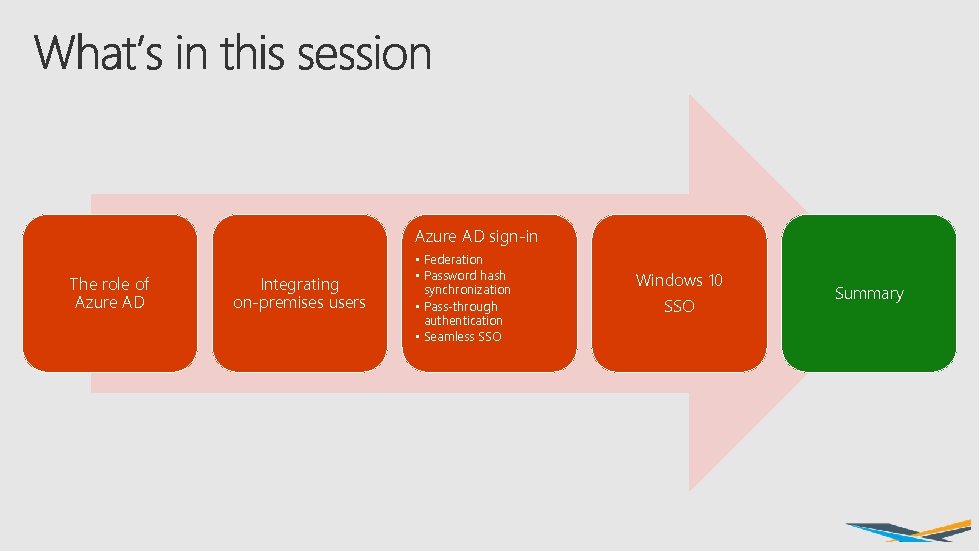
Azure AD sign-in The role of Azure AD Integrating on-premises users • Federation • Password hash synchronization • Pass-through authentication • Seamless SSO Windows 10 SSO Summary


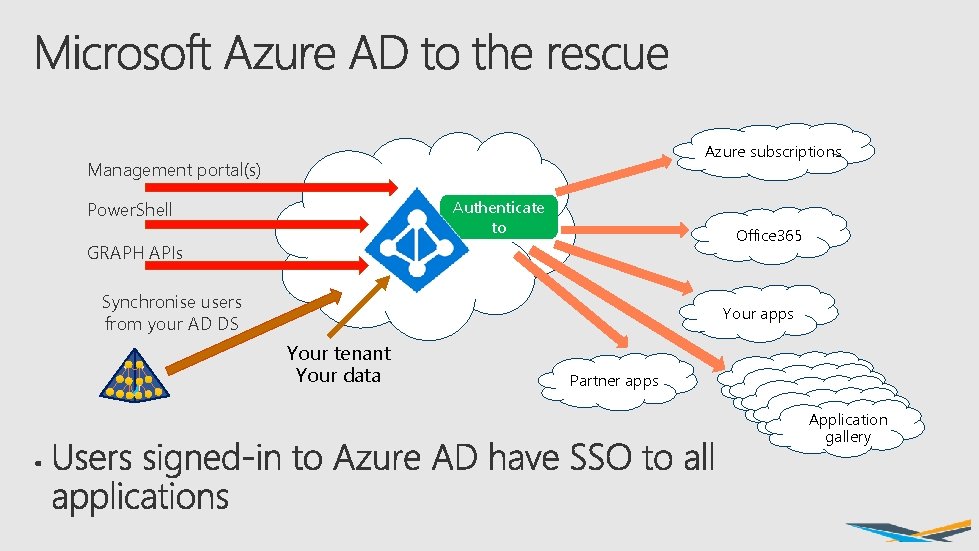
Azure subscriptions Azure AD Management portal(s) Authenticate to Power. Shell Office 365 GRAPH APIs Synchronise users from your AD DS Your apps Your tenant Your data Partner apps Application gallery


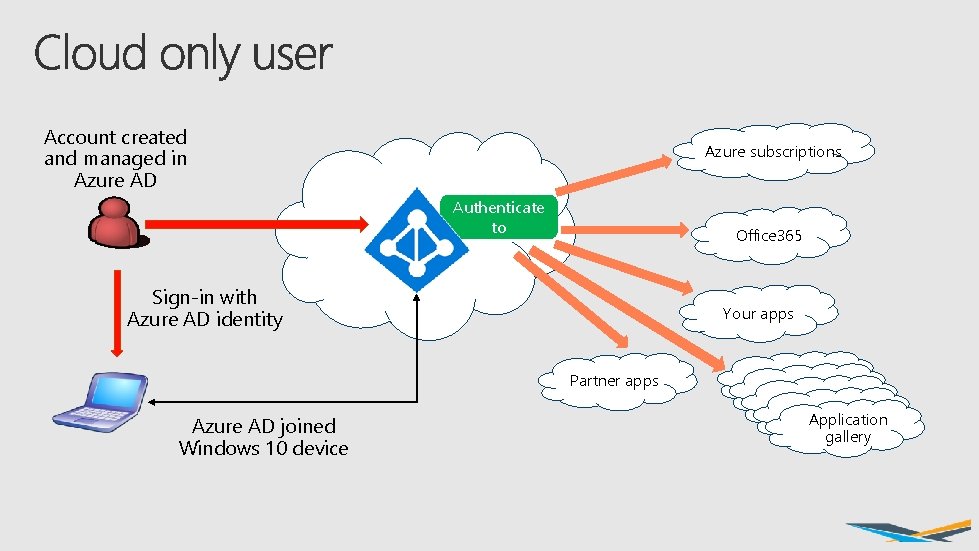
Account created and managed in Azure AD Azure subscriptions Azure AD Authenticate to Office 365 Sign-in with Azure AD identity Your apps Partner apps Azure AD joined Windows 10 device Application gallery

Azure AD sign-in The role of Azure AD Integrating on-premises users • Federation • Password hash synchronization • Pass-through authentication • Seamless SSO Windows 10 SSO Summary

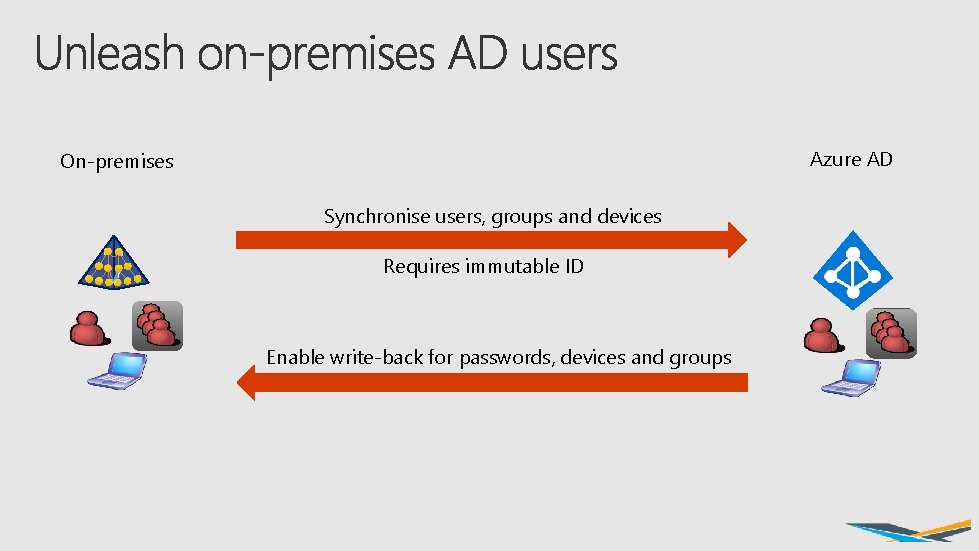
Azure AD On-premises Synchronise users, groups and devices Requires immutable ID Enable write-back for passwords, devices and groups

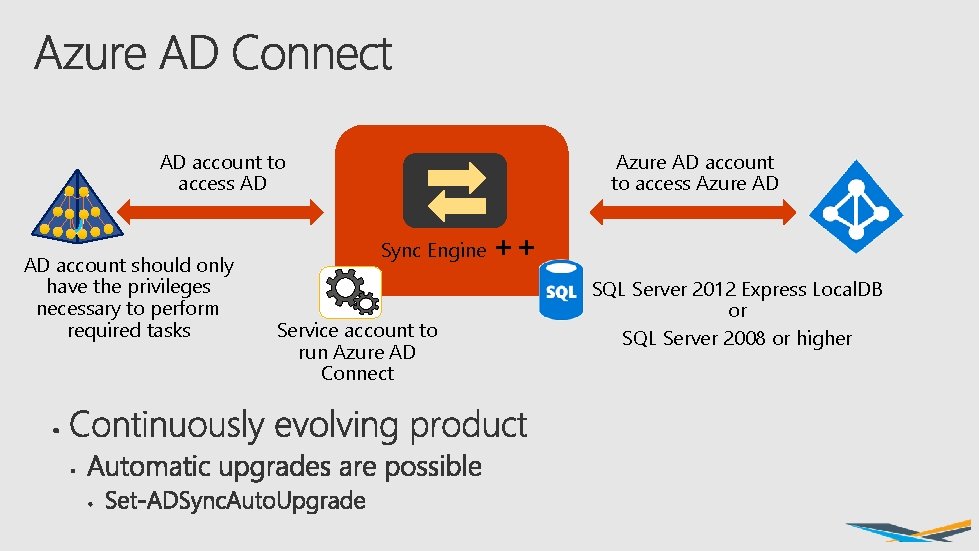
AD account to access AD AD account should only have the privileges necessary to perform required tasks Azure AD account to access Azure AD Sync Engine Service account to run Azure AD Connect ++ SQL Server 2012 Express Local. DB or SQL Server 2008 or higher



Azure AD sign-in The role of Azure AD Integrating on-premises users • Federation • Password hash synchronization • Pass-through authentication • Seamless SSO Windows 10 SSO Summary

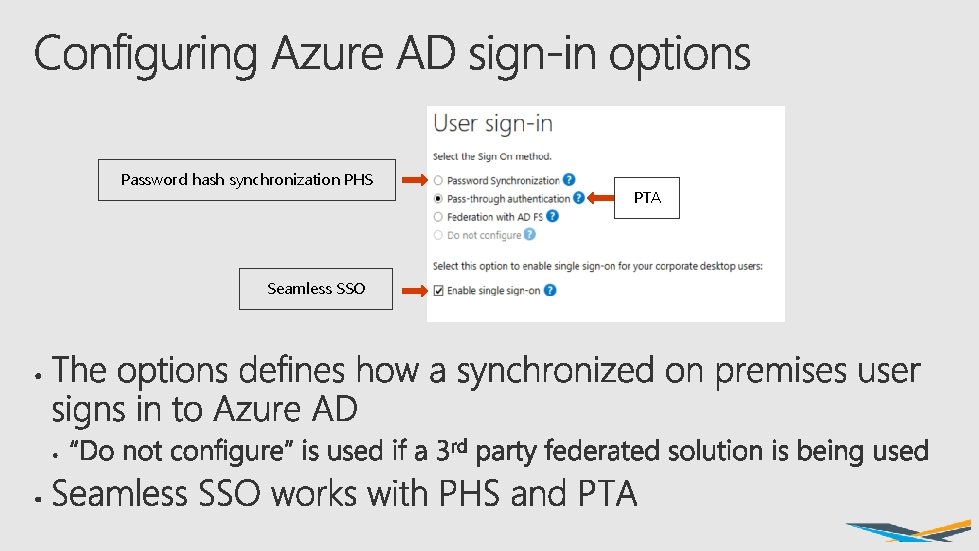
Password hash synchronization PHS Seamless SSO PTA



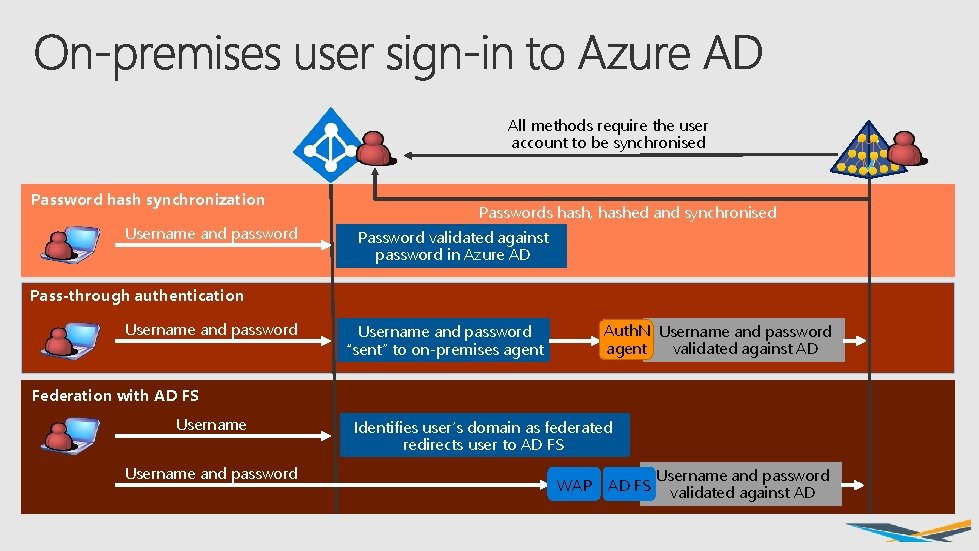
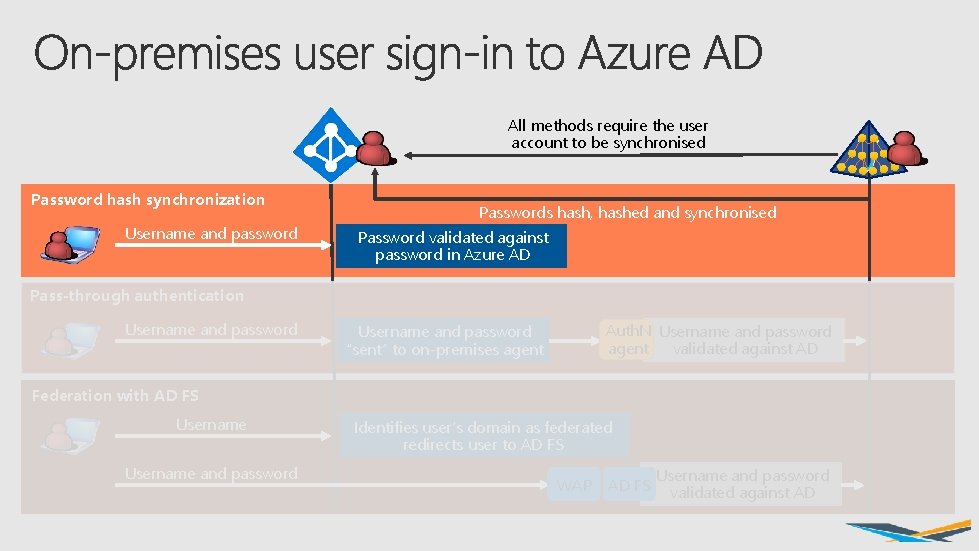
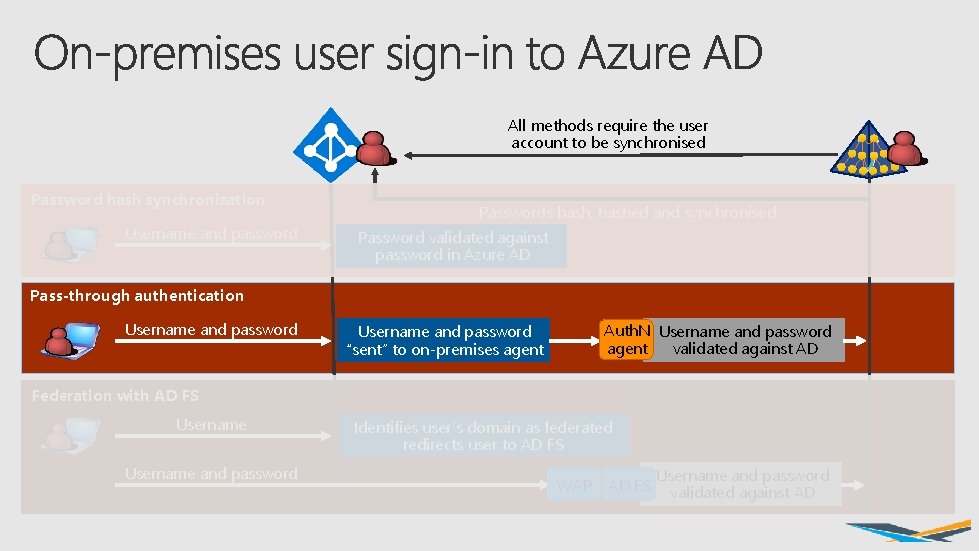
All methods require the user account to be synchronised Password hash synchronization Username and password Passwords hash, hashed and synchronised Password validated against password in Azure AD Pass-through authentication Username and password Auth. N Username and password agent validated against AD Username and password “sent” to on-premises agent Federation with AD FS Username and password Identifies user’s domain as federated redirects user to AD FS WAP AD FS Username and password validated against AD

All methods require the user account to be synchronised Password hash synchronization Username and password Passwords hash, hashed and synchronised Password validated against password in Azure AD Pass-through authentication Username and password Auth. N Username and password agent validated against AD Username and password “sent” to on-premises agent Federation with AD FS Username and password Identifies user’s domain as federated redirects user to AD FS WAP AD FS Username and password validated against AD

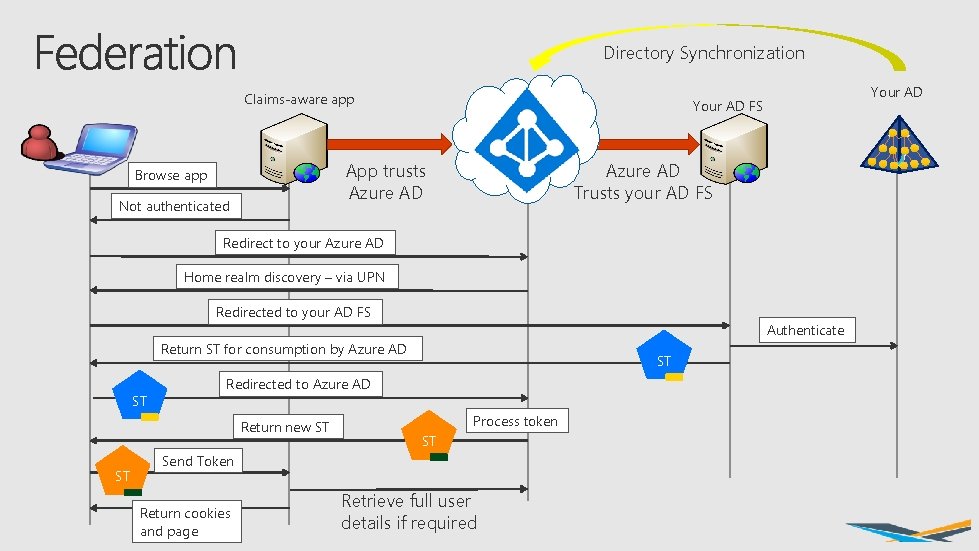
Directory Synchronization Claims-aware app App trusts Azure AD Browse app Not authenticated Your AD FS Azure AD Trusts your AD FS Redirect to your Azure AD Home realm discovery – via UPN Redirected to your AD FS Authenticate Return ST for consumption by Azure AD ST Redirected to Azure AD Return new ST ST ST Process token ST Send Token Return cookies and page Retrieve full user details if required


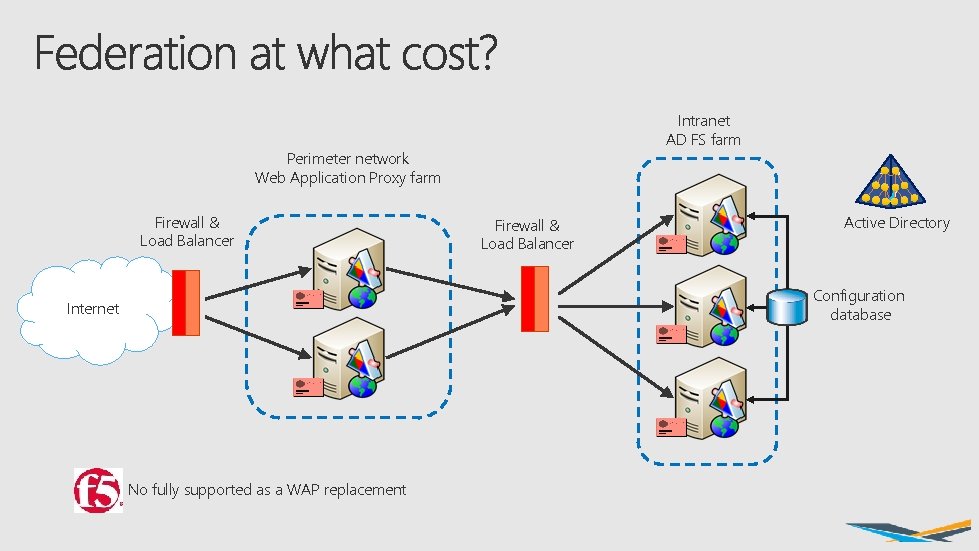
Intranet AD FS farm Perimeter network Web Application Proxy farm Firewall & Load Balancer Active Directory Configuration database Internet No fully supported as a WAP replacement

Now supported by Seamless SSO for PHS and PTA Now supported via PTA Capabilities++ provided by Azure AD


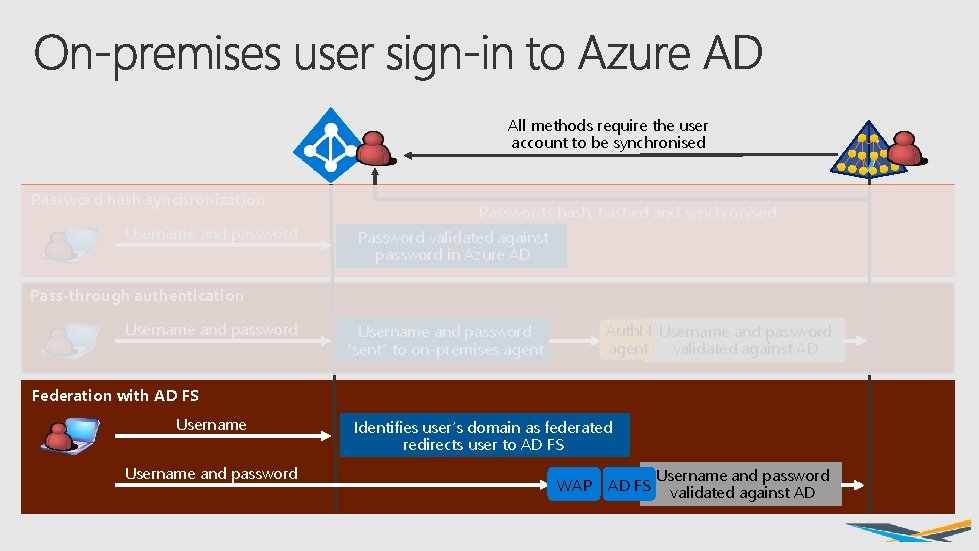
All methods require the user account to be synchronised Password hash synchronization Username and password Passwords hash, hashed and synchronised Password validated against password in Azure AD Pass-through authentication Username and password Auth. N Username and password agent validated against AD Username and password “sent” to on-premises agent Federation with AD FS Username and password Identifies user’s domain as federated redirects user to AD FS WAP AD FS Username and password validated against AD

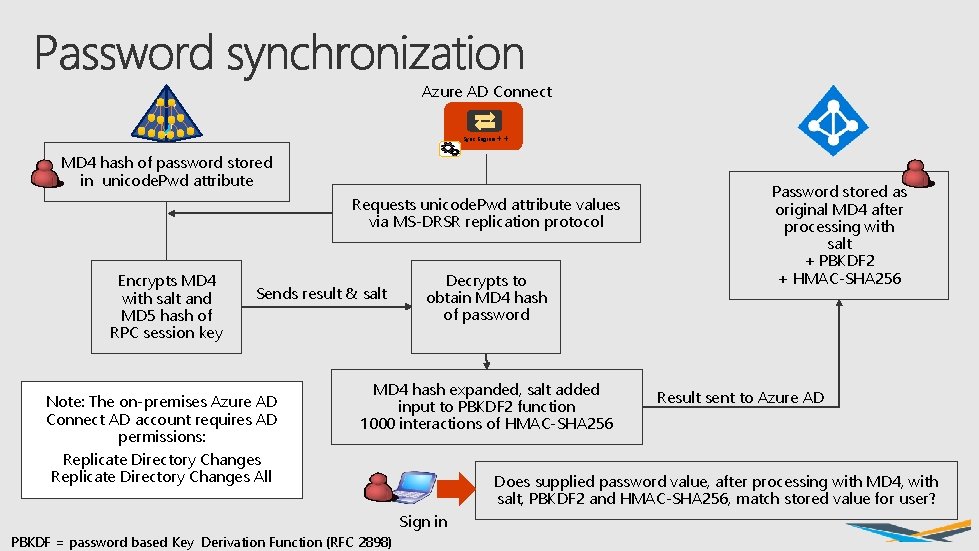
Azure AD Connect Sync Engine ++ MD 4 hash of password stored in unicode. Pwd attribute Requests unicode. Pwd attribute values via MS-DRSR replication protocol Encrypts MD 4 with salt and MD 5 hash of RPC session key Sends result & salt Note: The on-premises Azure AD Connect AD account requires AD permissions: Replicate Directory Changes All Decrypts to obtain MD 4 hash of password MD 4 hash expanded, salt added input to PBKDF 2 function 1000 interactions of HMAC-SHA 256 Result sent to Azure AD Does supplied password value, after processing with MD 4, with salt, PBKDF 2 and HMAC-SHA 256, match stored value for user? Sign in PBKDF = password based Key Derivation Function (RFC 2898) Password stored as original MD 4 after processing with salt + PBKDF 2 + HMAC-SHA 256



All methods require the user account to be synchronised Password hash synchronization Username and password Passwords hash, hashed and synchronised Password validated against password in Azure AD Pass-through authentication Username and password Auth. N Username and password agent validated against AD Username and password “sent” to on-premises agent Federation with AD FS Username and password Identifies user’s domain as federated redirects user to AD FS WAP AD FS Username and password validated against AD

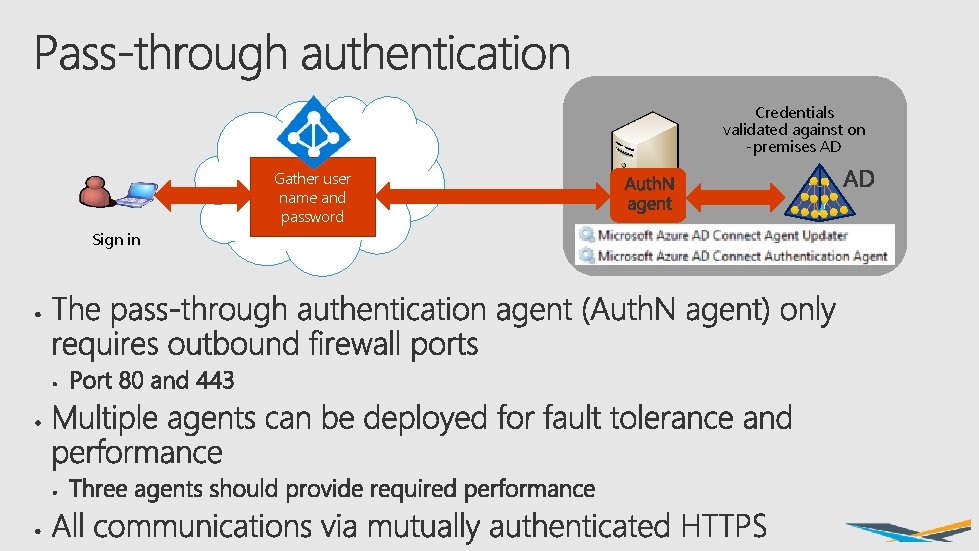
Credentials validated against on -premises AD Gather user name and password Sign in

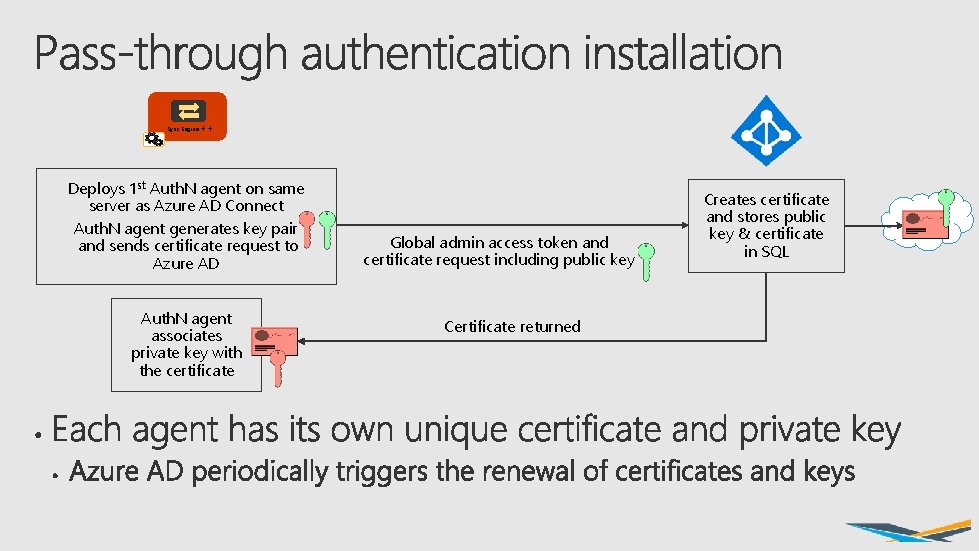
Sync Engine ++ Deploys 1 st Auth. N agent on same server as Azure AD Connect Auth. N agent generates key pair and sends certificate request to Azure AD Auth. N agent associates private key with the certificate Global admin access token and certificate request including public key Certificate returned Creates certificate and stores public key & certificate in SQL

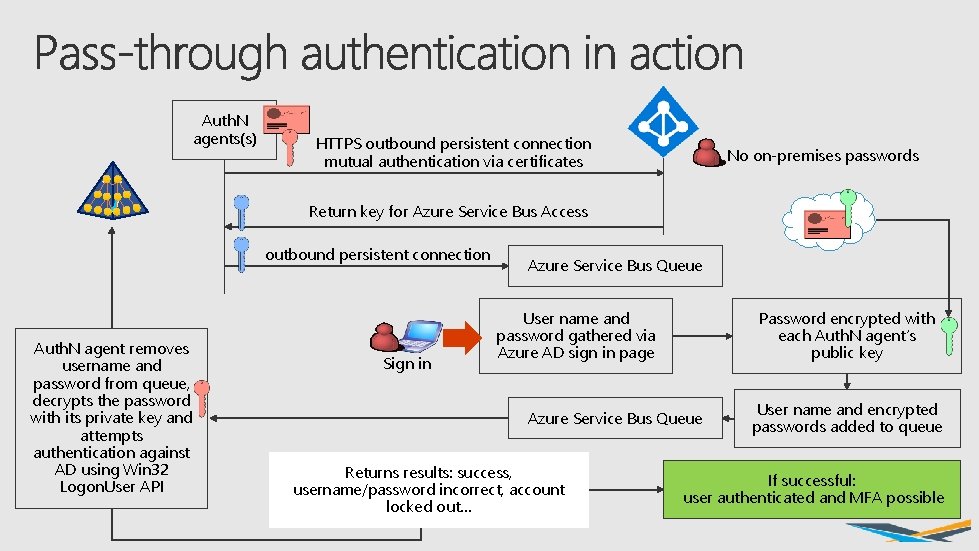
Auth. N agents(s) HTTPS outbound persistent connection mutual authentication via certificates No on-premises passwords Return key for Azure Service Bus Access outbound persistent connection Auth. N agent removes username and password from queue, decrypts the password with its private key and attempts authentication against AD using Win 32 Logon. User API Sign in Azure Service Bus Queue User name and password gathered via Azure AD sign in page Password encrypted with each Auth. N agent’s public key Azure Service Bus Queue Returns results: success, username/password incorrect, account locked out… User name and encrypted passwords added to queue If successful: user authenticated and MFA possible






Azure AD sign-in The role of Azure AD Integrating on-premises users • Federation • Password hash synchronization • Pass-through authentication • Seamless SSO Windows 10 SSO Summary


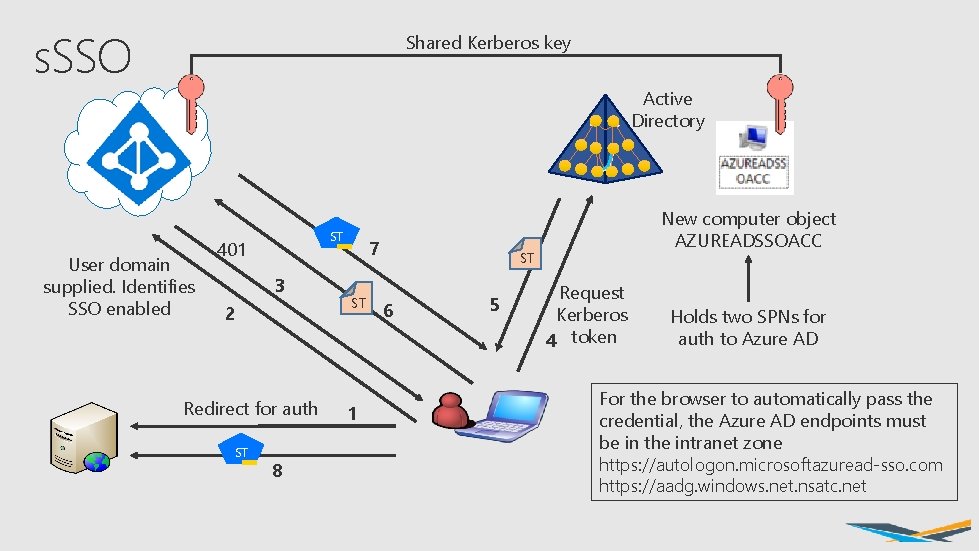
s. SSO Shared Kerberos key Active Directory User domain supplied. Identifies SSO enabled ST 401 3 2 Redirect for auth ST 8 7 ST 1 New computer object AZUREADSSOACC ST 6 5 Request Kerberos 4 token Holds two SPNs for auth to Azure AD For the browser to automatically pass the credential, the Azure AD endpoints must be in the intranet zone https: //autologon. microsoftazuread-sso. com https: //aadg. windows. net. nsatc. net




Azure AD sign-in The role of Azure AD Integrating on-premises users • Federation • Password hash synchronization • Pass-through authentication • Seamless SSO Windows 10 SSO Summary

43

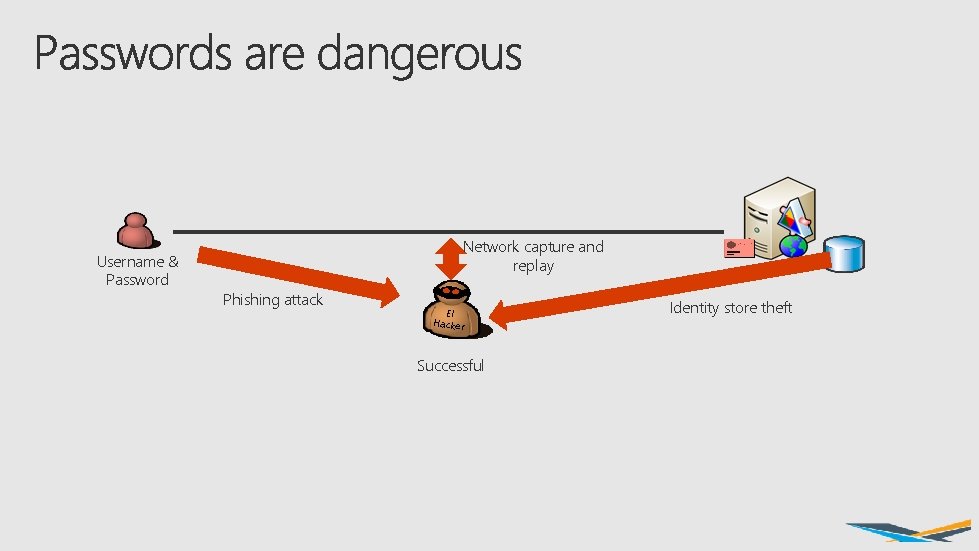
Username & Password Network capture and replay Phishing attack El Hacker Successful Identity store theft

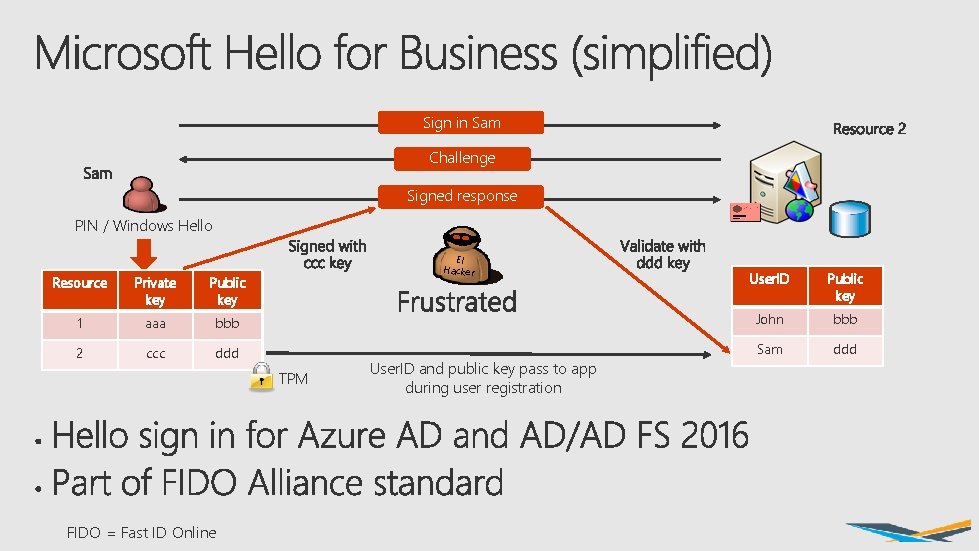
Sign in Sam Challenge Signed response PIN / Windows Hello El Hacker User. ID Public key bbb John bbb ddd Sam ddd Resource Private key Public key 1 aaa 2 ccc TPM FIDO = Fast ID Online User. ID and public key pass to app during user registration

Azure AD sign-in The role of Azure AD Integrating on-premises users • Federation • Password hash synchronization • Pass-through authentication • Seamless SSO Windows 10 SSO Summary

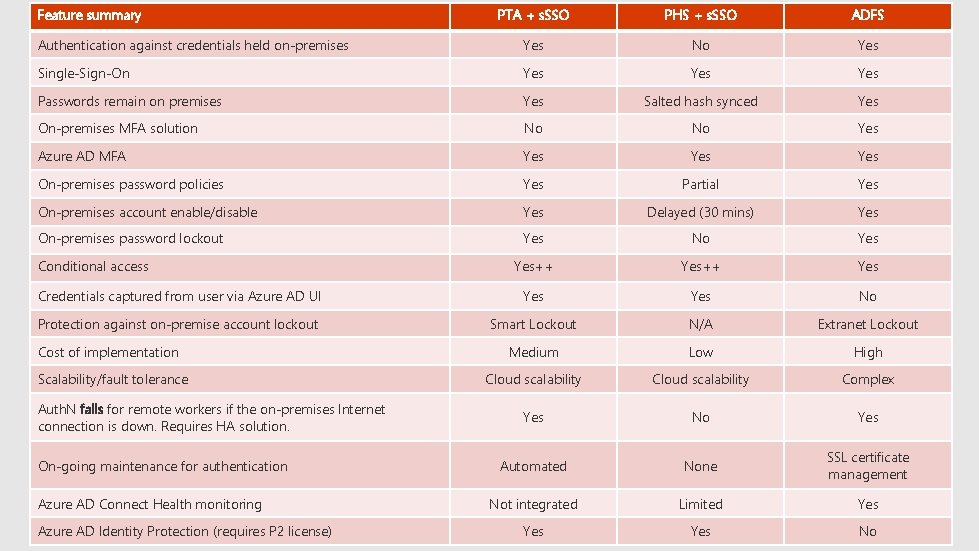
Feature summary PTA + s. SSO PHS + s. SSO ADFS Authentication against credentials held on-premises Yes No Yes Single-Sign-On Yes Yes Passwords remain on premises Yes Salted hash synced Yes On-premises MFA solution No No Yes Azure AD MFA Yes Yes On-premises password policies Yes Partial Yes On-premises account enable/disable Yes Delayed (30 mins) Yes On-premises password lockout Yes No Yes++ Yes Credentials captured from user via Azure AD UI Yes No Protection against on-premise account lockout Smart Lockout N/A Extranet Lockout Medium Low High Cloud scalability Complex Yes No Yes Automated None SSL certificate management Not integrated Limited Yes Yes No Conditional access Cost of implementation Scalability/fault tolerance Auth. N fails for remote workers if the on-premises Internet connection is down. Requires HA solution. On-going maintenance for authentication Azure AD Connect Health monitoring Azure AD Identity Protection (requires P 2 license)




John Craddock Infrastructure and security Architect XTSeminars Ltd John has designed and implemented computing systems ranging from high-speed industrial controllers through to distributed IT systems with a focus on security and high-availability. A key player in many IT projects for industry leaders including Microsoft, the UK Government and multi-nationals that require optimized IT systems. Developed technical training courses that have been published worldwide, co-authored a highly successful book on Microsoft Active Directory Internals, presents regularly at major international conferences including Tech. Ed, IT Forum and European summits. John can be engaged as a consultant or booked for speaking engagements through XTSeminars. www. xtseminars. co. uk

https: //myignite. microsoft. com/evaluations https: //aka. ms/ignite. mobileapp

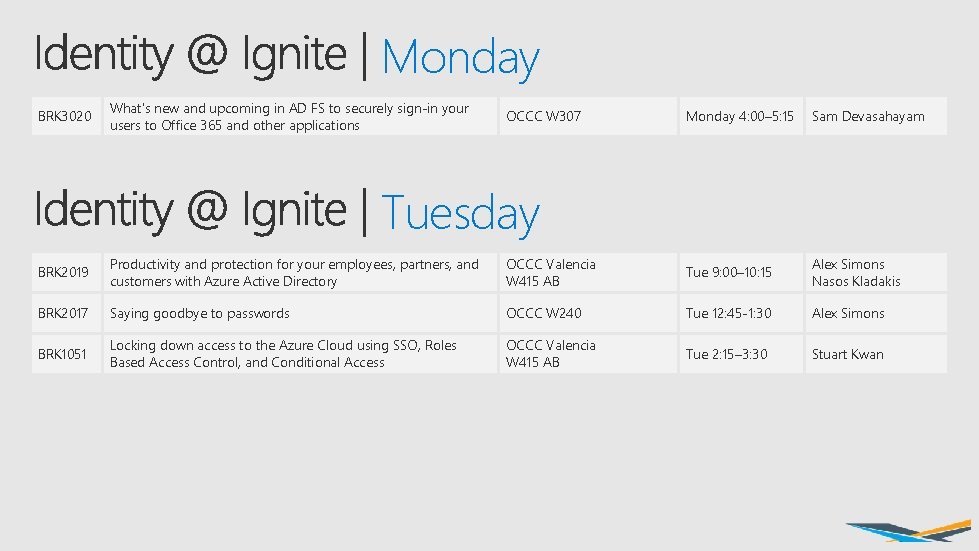
Monday BRK 3020 What's new and upcoming in AD FS to securely sign-in your users to Office 365 and other applications OCCC W 307 Monday 4: 00– 5: 15 Sam Devasahayam Tuesday BRK 2019 Productivity and protection for your employees, partners, and customers with Azure Active Directory OCCC Valencia W 415 AB Tue 9: 00– 10: 15 Alex Simons Nasos Kladakis BRK 2017 Saying goodbye to passwords OCCC W 240 Tue 12: 45 -1: 30 Alex Simons BRK 1051 Locking down access to the Azure Cloud using SSO, Roles Based Access Control, and Conditional Access OCCC Valencia W 415 AB Tue 2: 15– 3: 30 Stuart Kwan

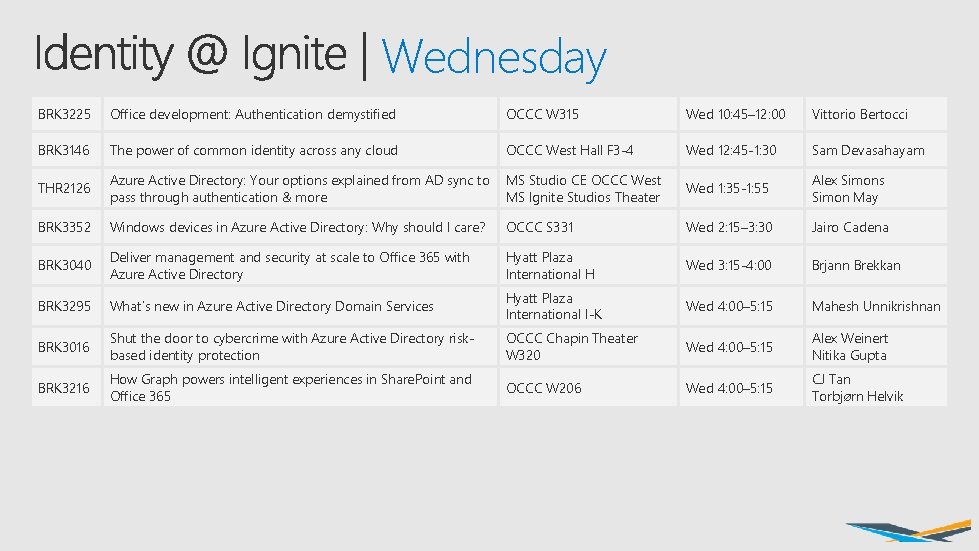
Wednesday BRK 3225 Office development: Authentication demystified OCCC W 315 Wed 10: 45– 12: 00 Vittorio Bertocci BRK 3146 The power of common identity across any cloud OCCC West Hall F 3 -4 Wed 12: 45 -1: 30 Sam Devasahayam THR 2126 Azure Active Directory: Your options explained from AD sync to pass through authentication & more MS Studio CE OCCC West MS Ignite Studios Theater Wed 1: 35 -1: 55 Alex Simons Simon May BRK 3352 Windows devices in Azure Active Directory: Why should I care? OCCC S 331 Wed 2: 15– 3: 30 Jairo Cadena BRK 3040 Deliver management and security at scale to Office 365 with Azure Active Directory Hyatt Plaza International H Wed 3: 15 -4: 00 Brjann Brekkan BRK 3295 What’s new in Azure Active Directory Domain Services Hyatt Plaza International I-K Wed 4: 00– 5: 15 Mahesh Unnikrishnan BRK 3016 Shut the door to cybercrime with Azure Active Directory riskbased identity protection OCCC Chapin Theater W 320 Wed 4: 00– 5: 15 Alex Weinert Nitika Gupta BRK 3216 How Graph powers intelligent experiences in Share. Point and Office 365 OCCC W 206 Wed 4: 00– 5: 15 CJ Tan Torbjørn Helvik

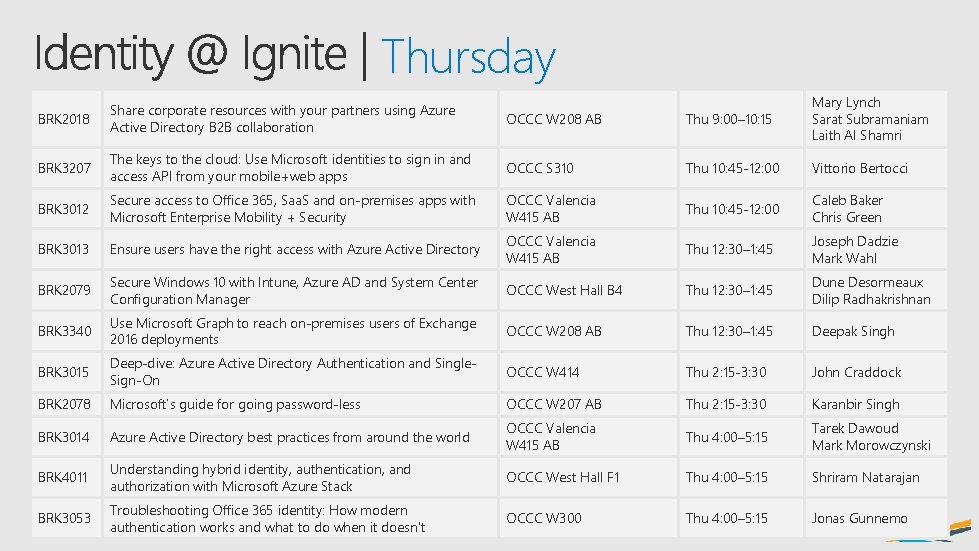
Thursday BRK 2018 Share corporate resources with your partners using Azure Active Directory B 2 B collaboration OCCC W 208 AB Thu 9: 00– 10: 15 Mary Lynch Sarat Subramaniam Laith Al Shamri BRK 3207 The keys to the cloud: Use Microsoft identities to sign in and access API from your mobile+web apps OCCC S 310 Thu 10: 45 -12: 00 Vittorio Bertocci BRK 3012 Secure access to Office 365, Saa. S and on-premises apps with Microsoft Enterprise Mobility + Security OCCC Valencia W 415 AB Thu 10: 45 -12: 00 Caleb Baker Chris Green BRK 3013 Ensure users have the right access with Azure Active Directory OCCC Valencia W 415 AB Thu 12: 30– 1: 45 Joseph Dadzie Mark Wahl BRK 2079 Secure Windows 10 with Intune, Azure AD and System Center Configuration Manager OCCC West Hall B 4 Thu 12: 30– 1: 45 Dune Desormeaux Dilip Radhakrishnan BRK 3340 Use Microsoft Graph to reach on-premises users of Exchange 2016 deployments OCCC W 208 AB Thu 12: 30– 1: 45 Deepak Singh BRK 3015 Deep-dive: Azure Active Directory Authentication and Single. Sign-On OCCC W 414 Thu 2: 15 -3: 30 John Craddock BRK 2078 Microsoft’s guide for going password-less OCCC W 207 AB Thu 2: 15 -3: 30 Karanbir Singh BRK 3014 Azure Active Directory best practices from around the world OCCC Valencia W 415 AB Thu 4: 00– 5: 15 Tarek Dawoud Mark Morowczynski BRK 4011 Understanding hybrid identity, authentication, and authorization with Microsoft Azure Stack OCCC West Hall F 1 Thu 4: 00– 5: 15 Shriram Natarajan BRK 3053 Troubleshooting Office 365 identity: How modern authentication works and what to do when it doesn't OCCC W 300 Thu 4: 00– 5: 15 Jonas Gunnemo

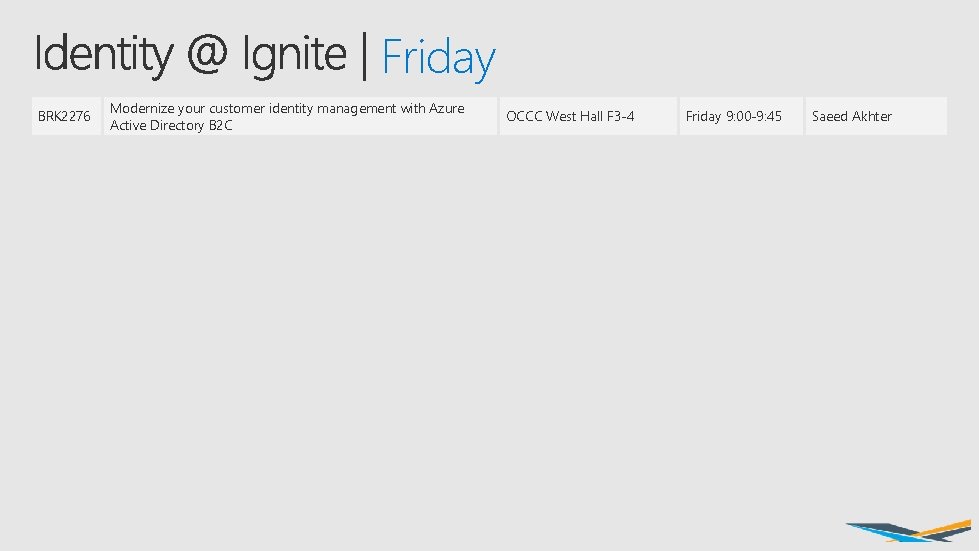
Friday BRK 2276 Modernize your customer identity management with Azure Active Directory B 2 C OCCC West Hall F 3 -4 Friday 9: 00 -9: 45 Saeed Akhter
