Azure AD Application Proxy Rick Leos u Connect






- Slides: 22

Azure AD Application Proxy Rick Leos u. Connect Administrator IET - Enterprise Applications and Infrastructure Services University of California, Davis rmleos@ucdavis. edu (530) 752 -1161

Business Intelligence Office Tableau Requirements: • Authentication utilizing Active Directory • Authorization utilizing Active Directory Groups • Must use Multi-factor authentication • Must use reverse web proxy

Business Intelligence Office Tableau Deployment option 1: Active Directory connection provides Auth. N & Auth. Z but no MFA Deployment option 2: SAML provides Auth. N & MFA but no Auth. Z application can not use groups claims in SAML ticket. Requires custom process to sync AD groups to internal roles in Tableau Additional infrastructure for reverse web proxy Disadvantage: Option 1: would require users to connect to VPN with MFA to gain access to application Option 2: Custom process needed to maintain sync of AD groups to internal Tableau roles.

Business Intelligence Office Tableau How do we get all the benefits of option 1 & 2 without any of the disadvantages?

Azure AD Application Proxy • Cloud-scale reverse proxy • Secure remote access for web applications hosted on-premises with pre-auth, conditional access and two-step verification. • Capable of providing Single sign-on experience. Using Integrated Windows Authentication, Linked sign-on (ADFS to ADFS), Headerbased sign-on, Password-based sign-on (requires browser extension ) • No inbound connections through your firewall, VPN, DMZs, edge servers, or other complex infrastructures. • Pass-through proxy mode available, non default.

Azure AD Application Proxy • What kind of applications work with Application Proxy? • Web applications that use Integrated Windows Authentication for authentication • Web applications that use form-based or header-based access • Web APIs that you want to expose to rich applications on different devices • Applications hosted behind a Remote Desktop Gateway • Rich client apps that are integrated with the Active Directory Authentication Library (ADAL)

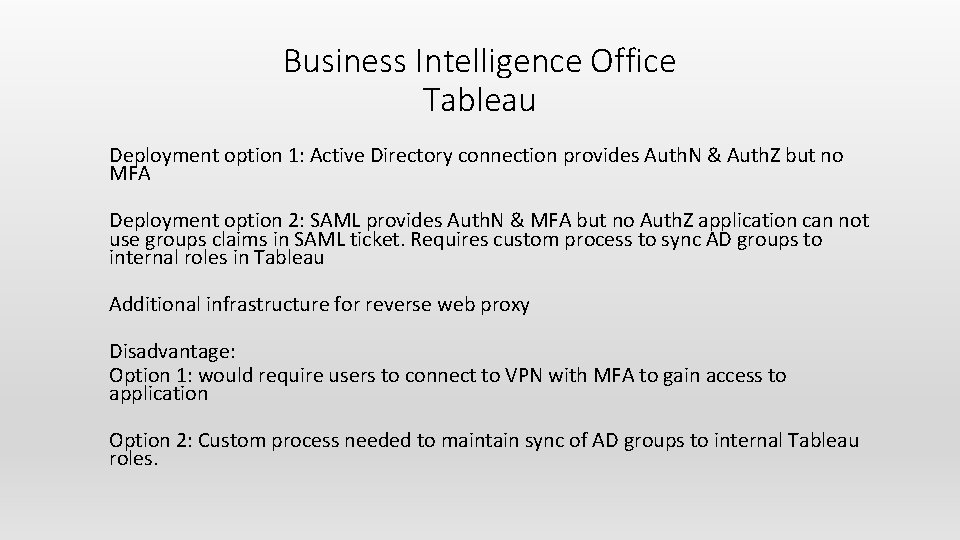
On-Premises Internal Network 1. User goes to site. Microsoft Azure AD Application Proxy Service On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu (CNAME aggiedash-dev-ucdavis 365. msappproxy. net) Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

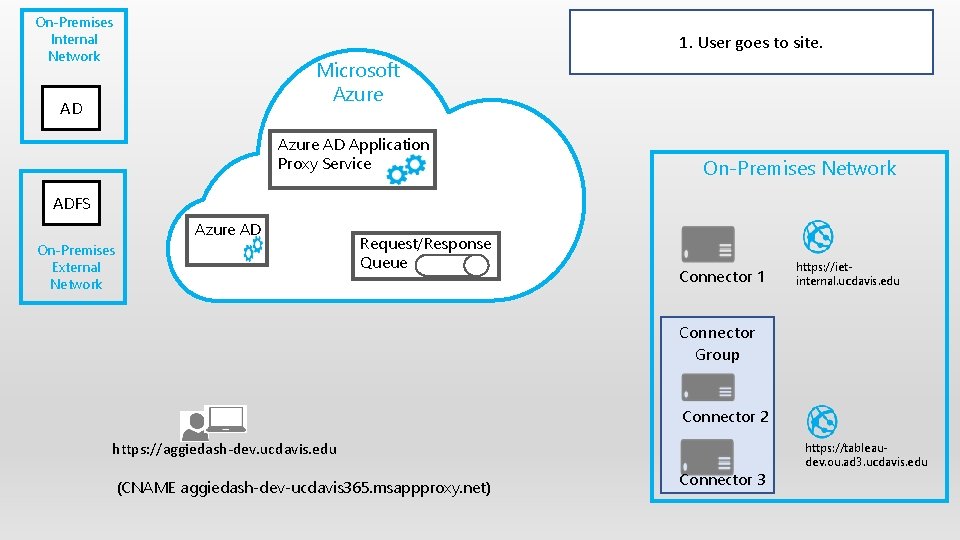
On-Premises Internal Network 2. User provides email address/ UPN Microsoft Azure AD Application Proxy Service On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

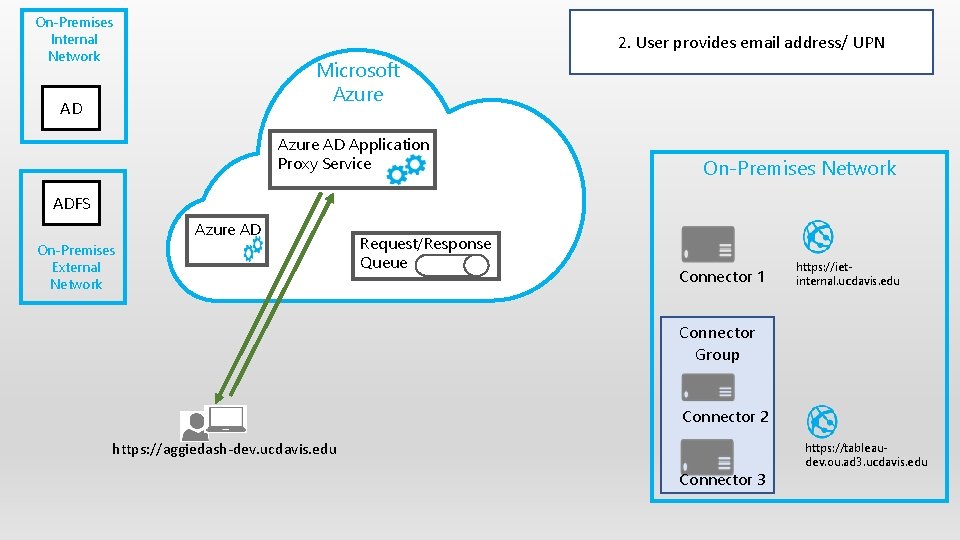
On-Premises Internal Network 3. Proxy forwards user request to Azure AD Microsoft Azure AD Application Proxy Service On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

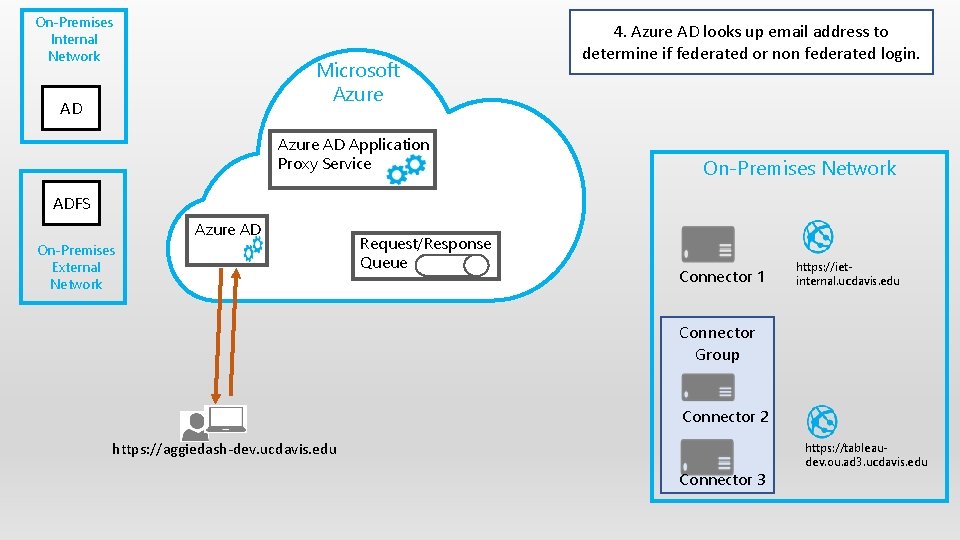
On-Premises Internal Network Microsoft Azure AD Application Proxy Service 4. Azure AD looks up email address to determine if federated or non federated login. On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

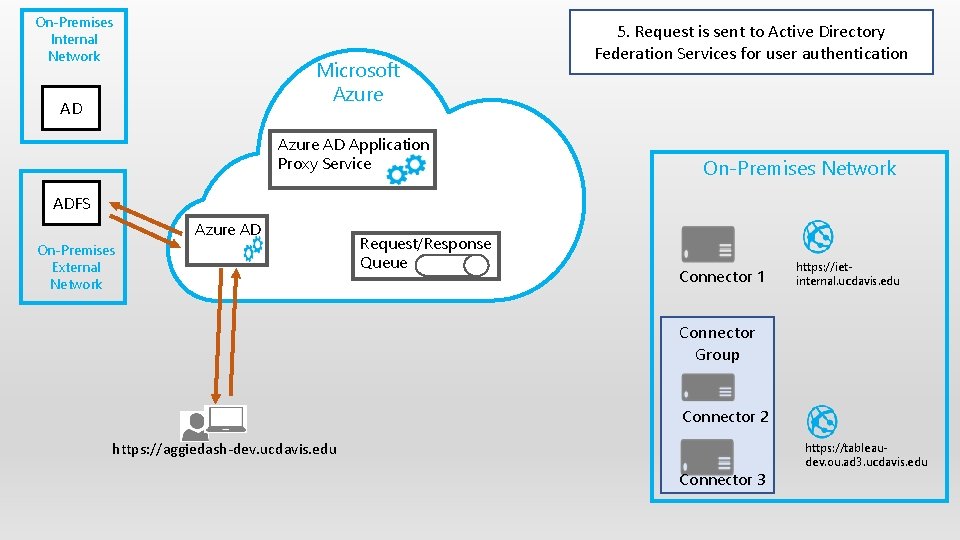
On-Premises Internal Network Microsoft Azure AD Application Proxy Service 5. Request is sent to Active Directory Federation Services for user authentication On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

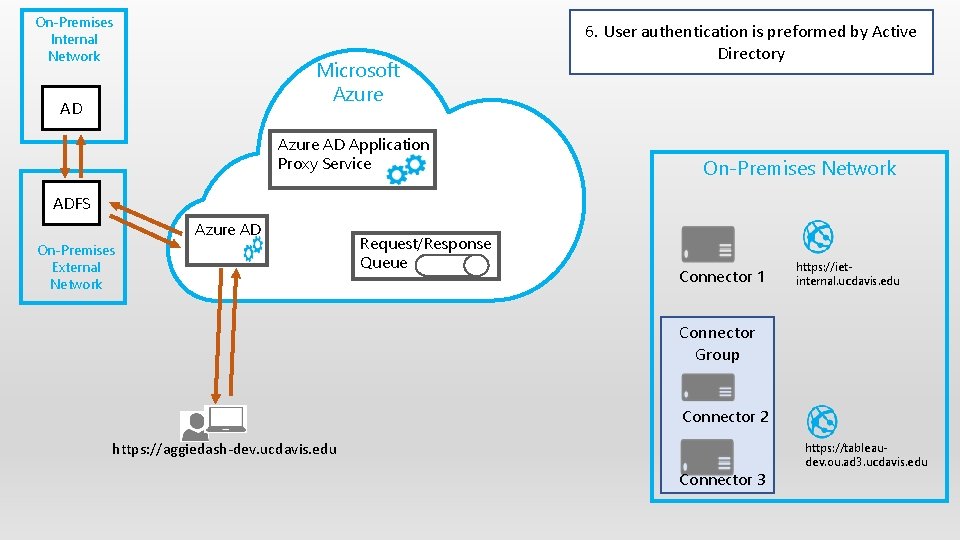
On-Premises Internal Network Microsoft Azure AD Application Proxy Service 6. User authentication is preformed by Active Directory On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

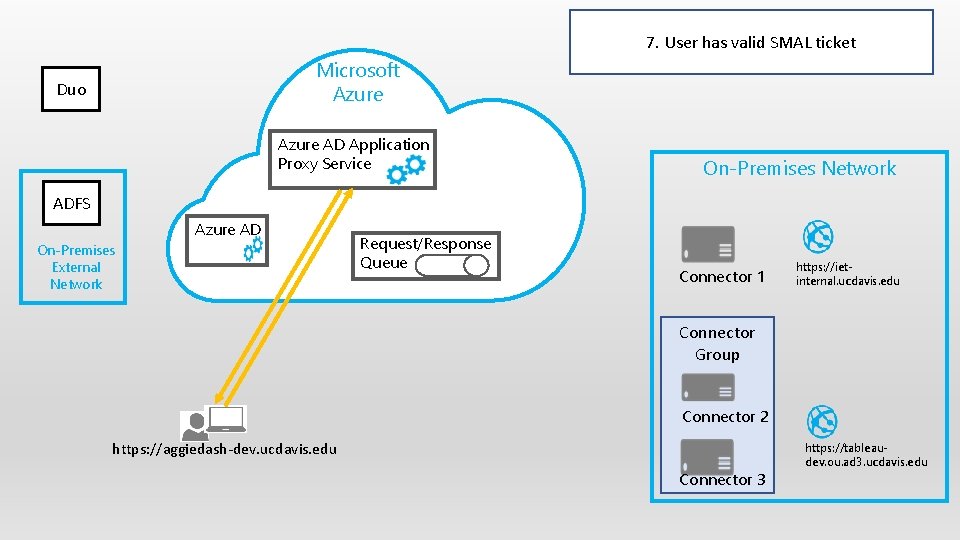
7. User has valid SMAL ticket Microsoft Azure Duo Azure AD Application Proxy Service On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

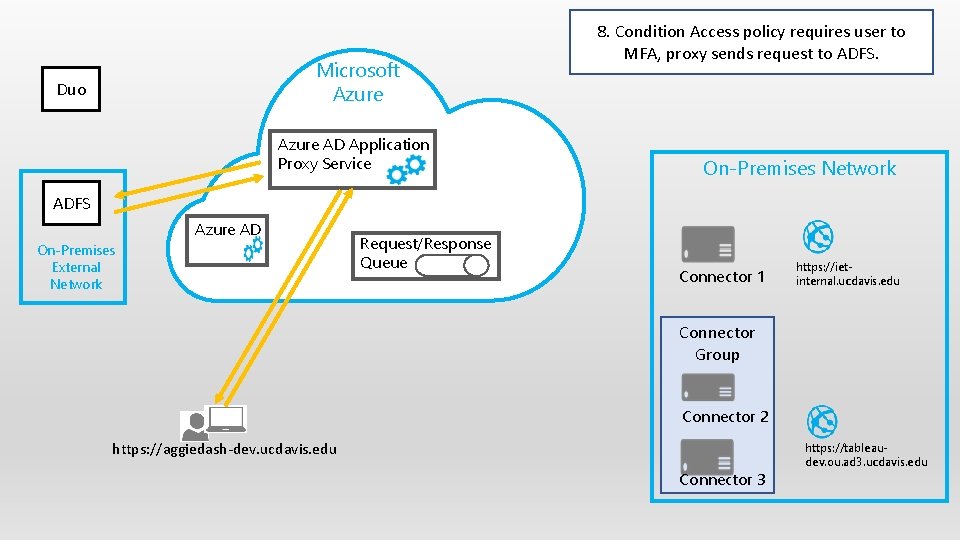
Microsoft Azure Duo Azure AD Application Proxy Service 8. Condition Access policy requires user to MFA, proxy sends request to ADFS. On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

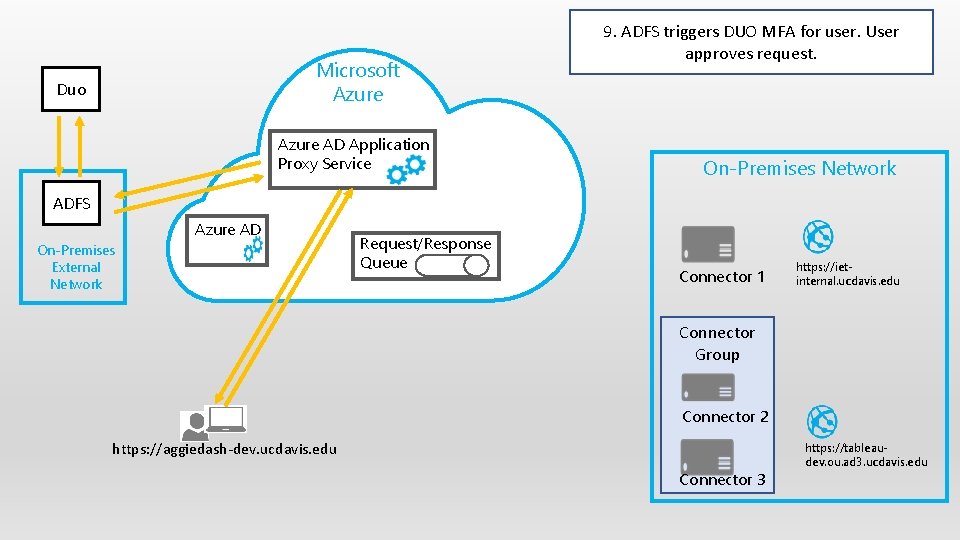
Microsoft Azure Duo Azure AD Application Proxy Service 9. ADFS triggers DUO MFA for user. User approves request. On-Premises Network ADFS Azure AD On-Premises External Network Request/Response Queue Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

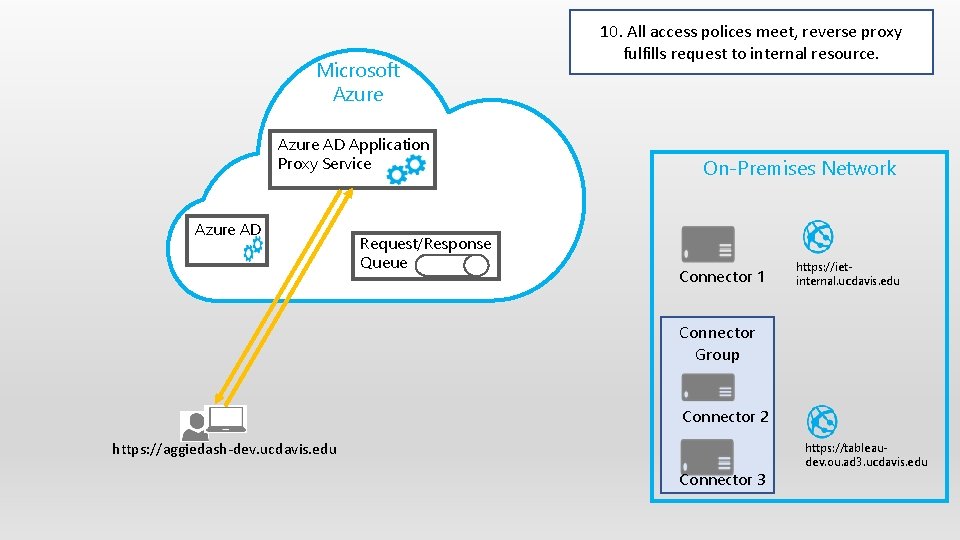
Microsoft Azure AD Application Proxy Service Azure AD Request/Response Queue 10. All access polices meet, reverse proxy fulfills request to internal resource. On-Premises Network Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

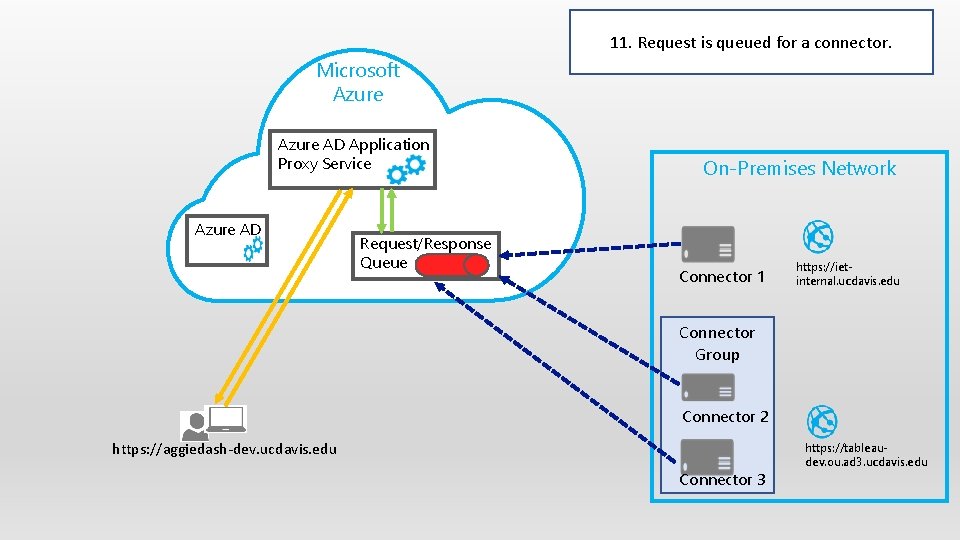
11. Request is queued for a connector. Microsoft Azure AD Application Proxy Service Azure AD Request/Response Queue On-Premises Network Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

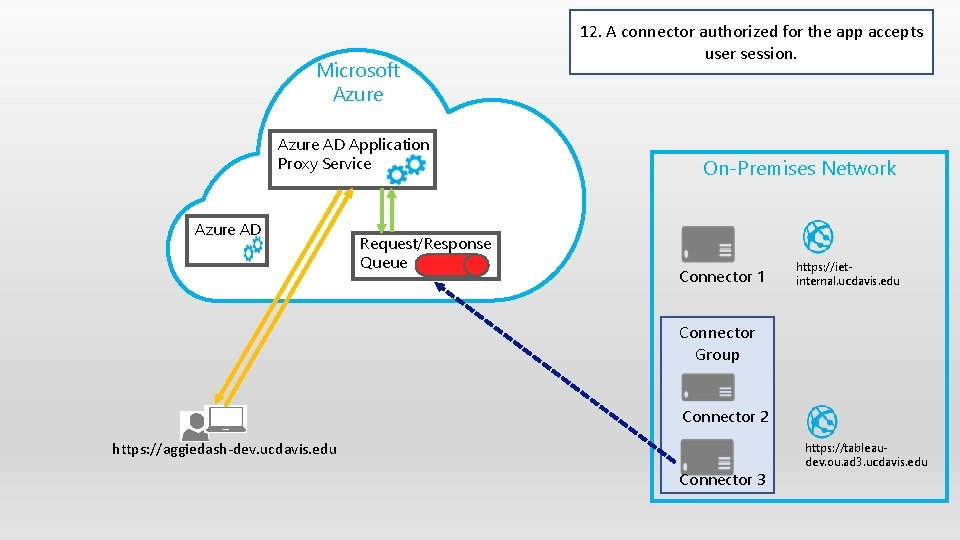
Microsoft Azure AD Application Proxy Service Azure AD Request/Response Queue 12. A connector authorized for the app accepts user session. On-Premises Network Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

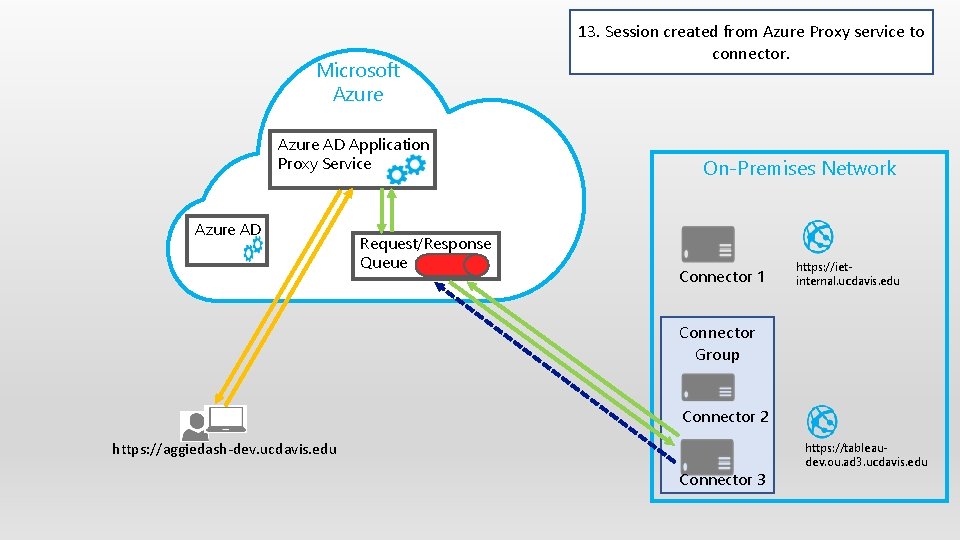
Microsoft Azure AD Application Proxy Service Azure AD Request/Response Queue 13. Session created from Azure Proxy service to connector. On-Premises Network Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

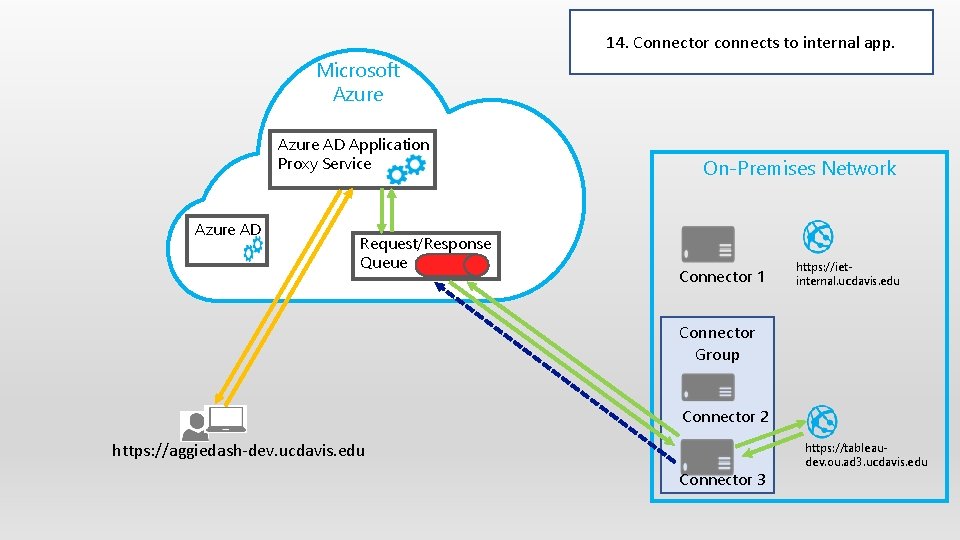
14. Connector connects to internal app. Microsoft Azure AD Application Proxy Service Azure AD Request/Response Queue On-Premises Network Connector 1 https: //ietinternal. ucdavis. edu Connector Group Connector 2 https: //aggiedash-dev. ucdavis. edu Connector 3 https: //tableaudev. ou. ad 3. ucdavis. edu

How do user access the app? 1. Directly going to proxy external url 2. myapps. microsoft. com 3. Installing the “My Apps” from Google Play or i. Tunes 4. office 365. ucdavis. edu or and clicking the titles icon top left.

Demo