Automatically Validating Temporal Safety Properties of Interfaces Overview

![BEBOP § Reachability analysis of boolean programs § Symbolic version of [Reps-Horwitz-Sagiv, POPL’ 95] BEBOP § Reachability analysis of boolean programs § Symbolic version of [Reps-Horwitz-Sagiv, POPL’ 95]](https://slidetodoc.com/presentation_image/56f80ac5e7275286f6a9b025a82e22ea/image-20.jpg)


- Slides: 23

Automatically Validating Temporal Safety Properties of Interfaces - Overview of SLAM Parts of the slides are from http: //research. microsoft. com/slam/presentations/spin 2001. ppt 1

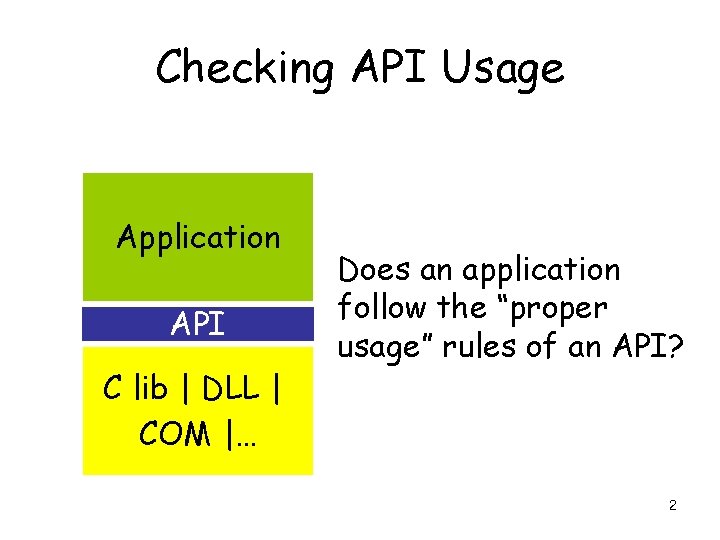
Checking API Usage Application API C lib | DLL | COM |… Does an application follow the “proper usage” rules of an API? 2

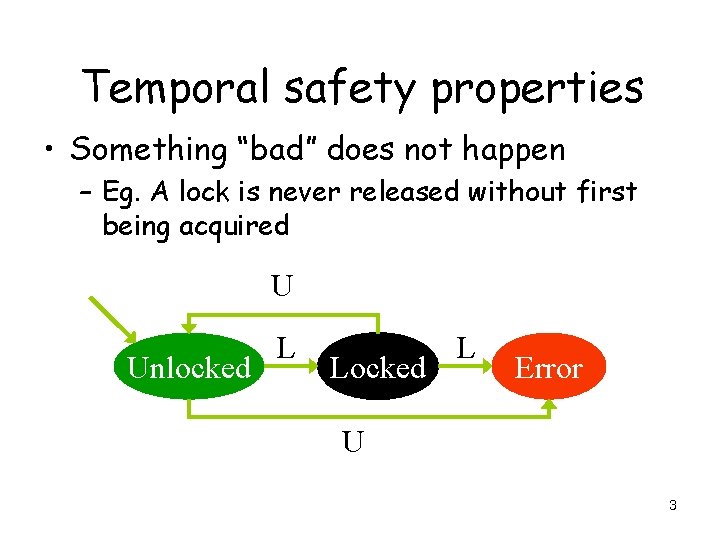
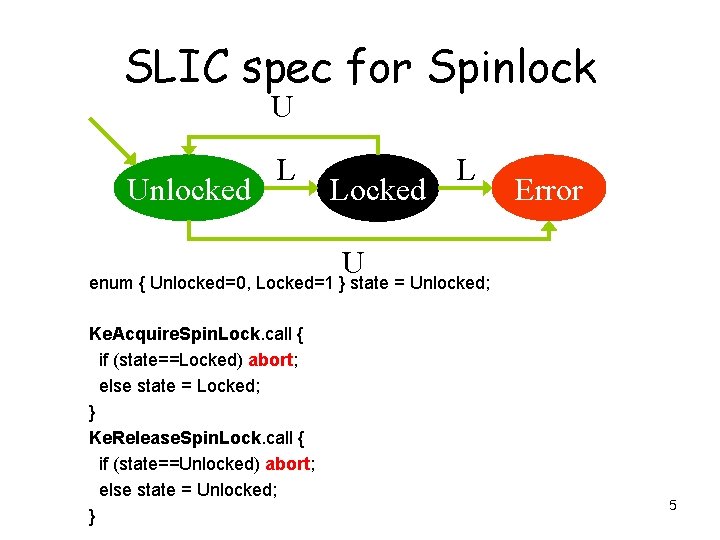
Temporal safety properties • Something “bad” does not happen – Eg. A lock is never released without first being acquired U Unlocked L Locked L Error U 3

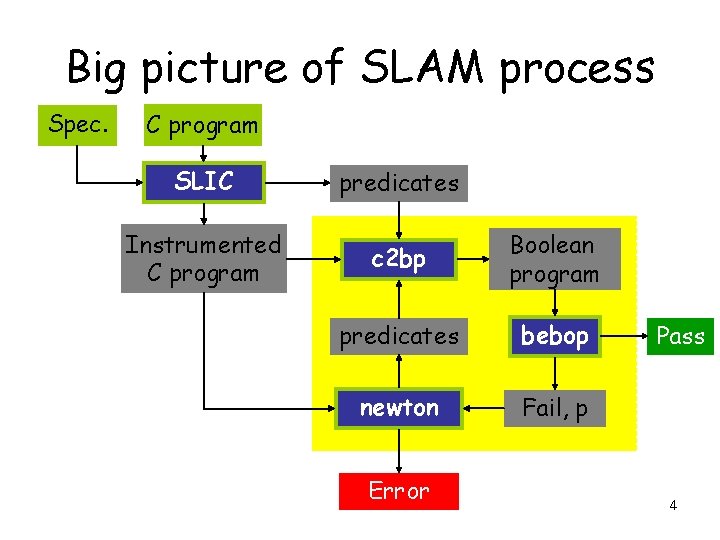
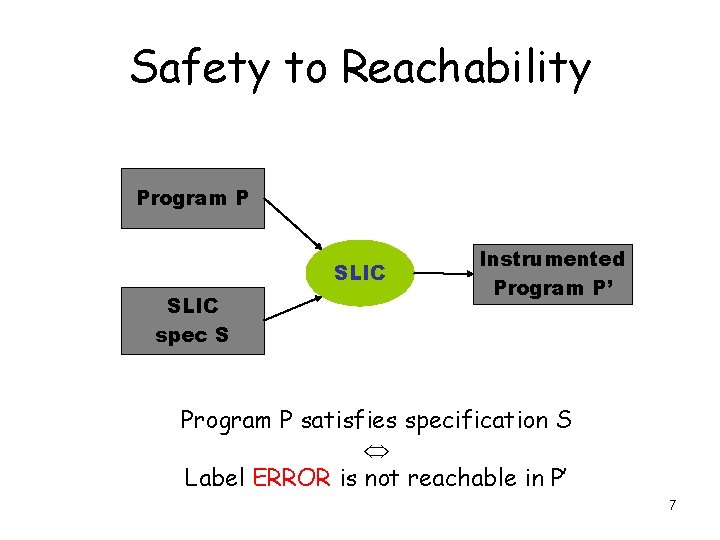
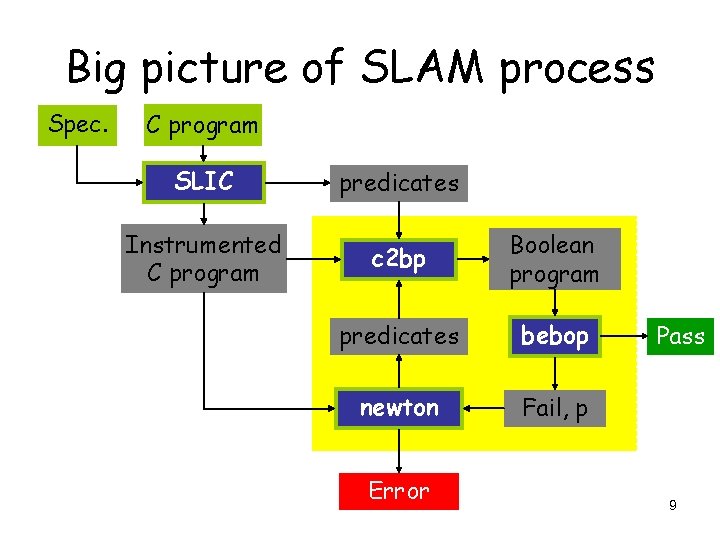
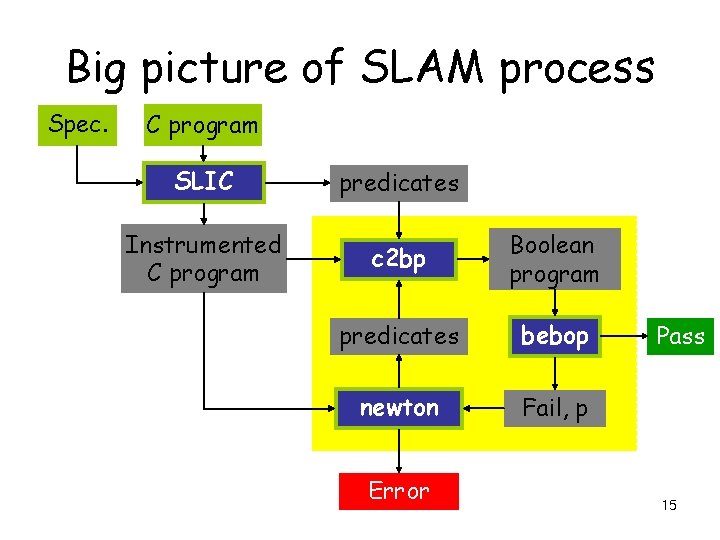
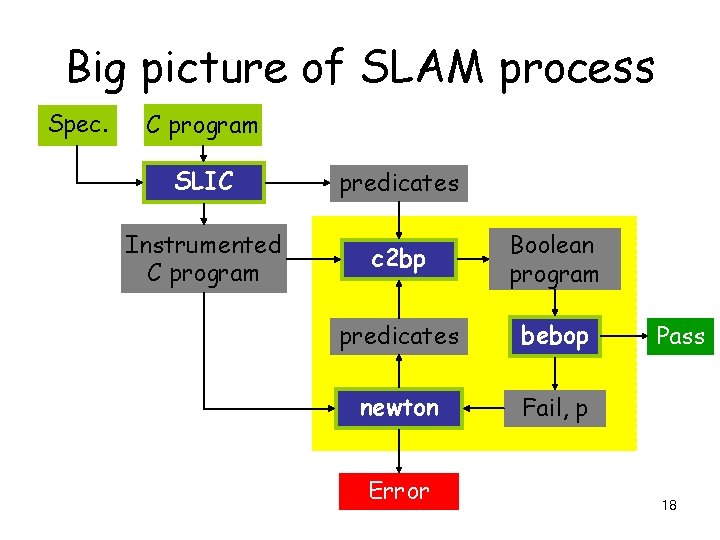
Big picture of SLAM process Spec. C program SLIC predicates Instrumented C program c 2 bp Boolean program predicates bebop newton Fail, p Error Pass 4

SLIC spec for Spinlock U Unlocked L Locked L Error U enum { Unlocked=0, Locked=1 } state = Unlocked; Ke. Acquire. Spin. Lock. call { if (state==Locked) abort; else state = Locked; } Ke. Release. Spin. Lock. call { if (state==Unlocked) abort; else state = Unlocked; } 5

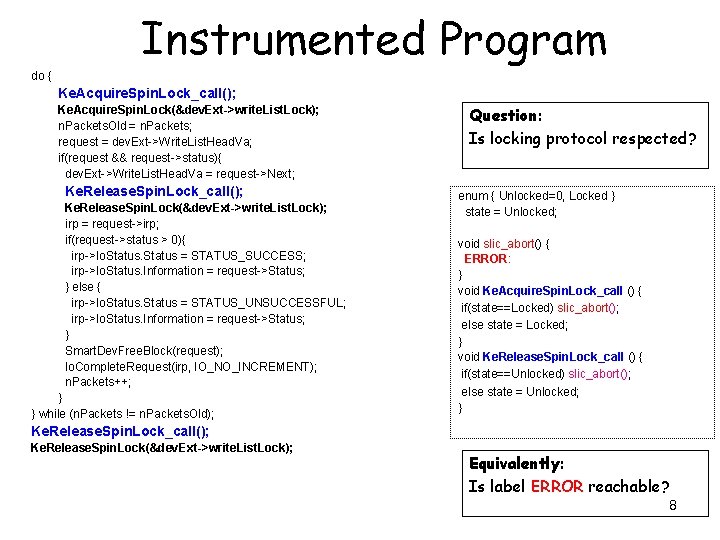
do { Target program to validate Ke. Acquire. Spin. Lock(&dev. Ext->write. List. Lock); n. Packets. Old = n. Packets; request = dev. Ext->Write. List. Head. Va; if(request && request->status){ dev. Ext->Write. List. Head. Va = request->Next; Question: Is locking protocol respected? Ke. Release. Spin. Lock(&dev. Ext->write. List. Lock); irp = request->irp; if(request->status > 0){ irp->Io. Status = STATUS_SUCCESS; irp->Io. Status. Information = request->Status; } else{ irp->Io. Status = STATUS_UNSUCCESSFUL; irp->Io. Status. Information = request->Status; } Smart. Dev. Free. Block(request); Io. Complete. Request(irp, IO_NO_INCREMENT); n. Packets++; } } while (n. Packets != n. Packets. Old); Ke. Release. Spin. Lock(&dev. Ext->write. List. Lock); 6

Safety to Reachability Program P SLIC spec S Instrumented Program P’ Program P satisfies specification S Label ERROR is not reachable in P’ 7

Instrumented Program do { Ke. Acquire. Spin. Lock_call(); Ke. Acquire. Spin. Lock(&dev. Ext->write. List. Lock); n. Packets. Old = n. Packets; request = dev. Ext->Write. List. Head. Va; if(request && request->status){ dev. Ext->Write. List. Head. Va = request->Next; Ke. Release. Spin. Lock_call(); Ke. Release. Spin. Lock(&dev. Ext->write. List. Lock); irp = request->irp; if(request->status > 0){ irp->Io. Status = STATUS_SUCCESS; irp->Io. Status. Information = request->Status; } else { irp->Io. Status = STATUS_UNSUCCESSFUL; irp->Io. Status. Information = request->Status; } Smart. Dev. Free. Block(request); Io. Complete. Request(irp, IO_NO_INCREMENT); n. Packets++; } } while (n. Packets != n. Packets. Old); Question: Is locking protocol respected? enum { Unlocked=0, Locked } state = Unlocked; void slic_abort() { ERROR: } void Ke. Acquire. Spin. Lock_call () { if(state==Locked) slic_abort(); else state = Locked; } void Ke. Release. Spin. Lock_call () { if(state==Unlocked) slic_abort(); else state = Unlocked; } Ke. Release. Spin. Lock_call(); Ke. Release. Spin. Lock(&dev. Ext->write. List. Lock); Equivalently: Is label ERROR reachable? 8

Big picture of SLAM process Spec. C program SLIC predicates Instrumented C program c 2 bp Boolean program predicates bebop newton Fail, p Error Pass 9

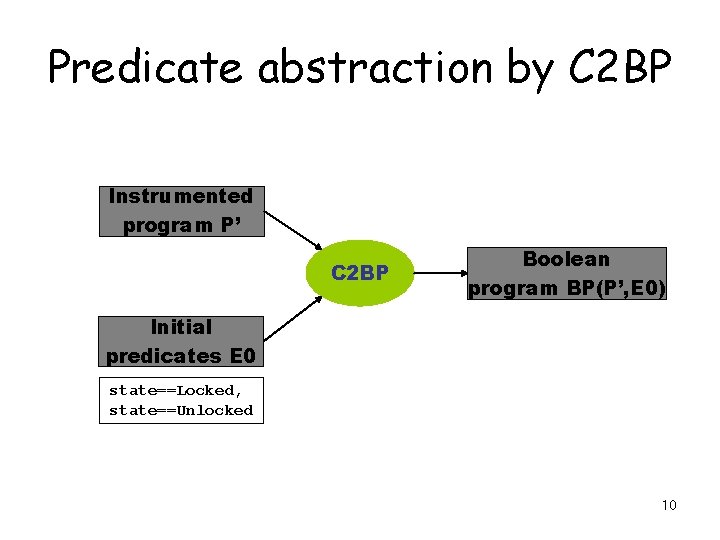
Predicate abstraction by C 2 BP Instrumented program P’ C 2 BP Boolean program BP(P’, E 0) Initial predicates E 0 state==Locked, state==Unlocked 10

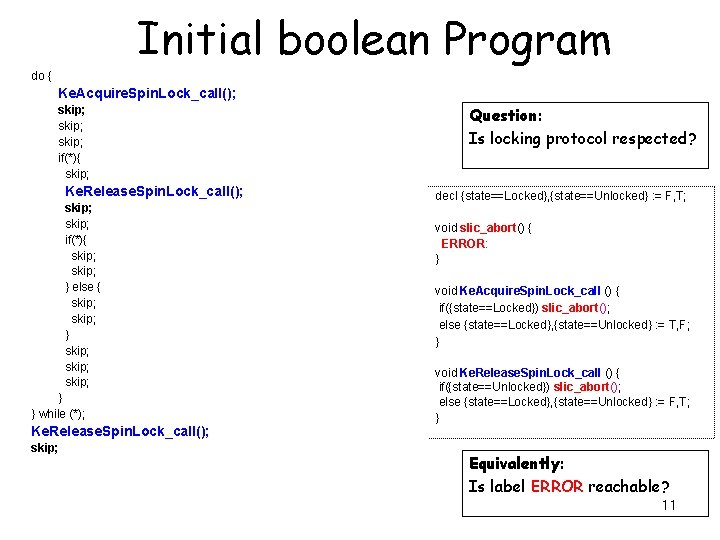
Initial boolean Program do { Ke. Acquire. Spin. Lock_call(); skip; if(*){ skip; Ke. Release. Spin. Lock_call(); skip; if(*){ skip; } else { skip; } skip; } } while (*); Ke. Release. Spin. Lock_call(); skip; Question: Is locking protocol respected? decl {state==Locked}, {state==Unlocked} : = F, T; void slic_abort() { ERROR: } void Ke. Acquire. Spin. Lock_call () { if({state==Locked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = T, F; } void Ke. Release. Spin. Lock_call () { if({state==Unlocked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = F, T; } Equivalently: Is label ERROR reachable? 11

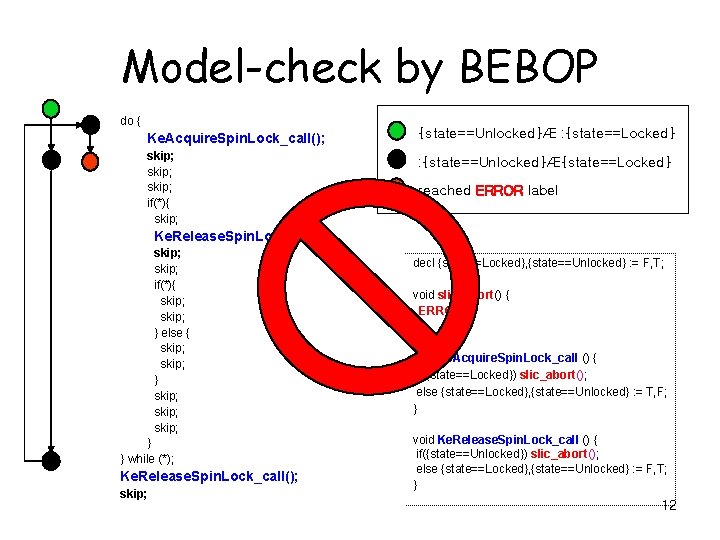
Model-check by BEBOP do { Ke. Acquire. Spin. Lock_call(); {state==Unlocked}Æ : {state==Locked} skip; if(*){ skip; : {state==Unlocked}Æ{state==Locked} reached ERROR label Ke. Release. Spin. Lock_call(); skip; if(*){ skip; } else { skip; } skip; } } while (*); Ke. Release. Spin. Lock_call(); skip; decl {state==Locked}, {state==Unlocked} : = F, T; void slic_abort() { ERROR: } void Ke. Acquire. Spin. Lock_call () { if({state==Locked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = T, F; } void Ke. Release. Spin. Lock_call () { if({state==Unlocked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = F, T; } 12

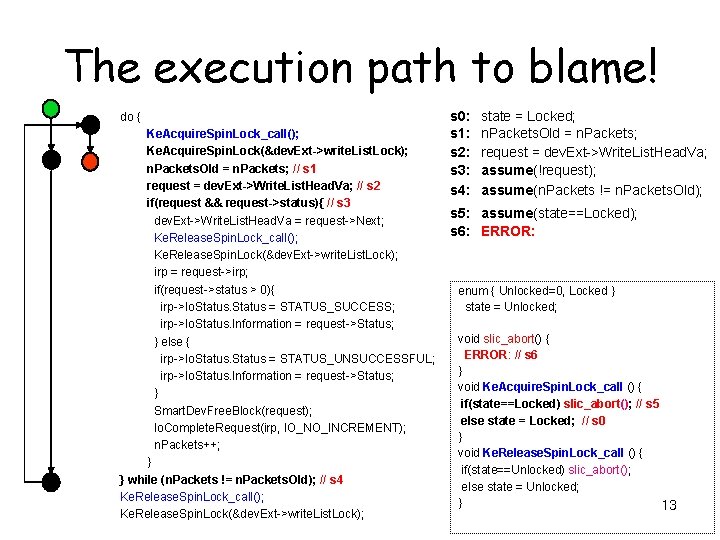
The execution path to blame! do { Ke. Acquire. Spin. Lock_call(); Ke. Acquire. Spin. Lock(&dev. Ext->write. List. Lock); n. Packets. Old = n. Packets; // s 1 request = dev. Ext->Write. List. Head. Va; // s 2 if(request && request->status){ // s 3 dev. Ext->Write. List. Head. Va = request->Next; Ke. Release. Spin. Lock_call(); Ke. Release. Spin. Lock(&dev. Ext->write. List. Lock); irp = request->irp; if(request->status > 0){ irp->Io. Status = STATUS_SUCCESS; irp->Io. Status. Information = request->Status; } else { irp->Io. Status = STATUS_UNSUCCESSFUL; irp->Io. Status. Information = request->Status; } Smart. Dev. Free. Block(request); Io. Complete. Request(irp, IO_NO_INCREMENT); n. Packets++; } } while (n. Packets != n. Packets. Old); // s 4 Ke. Release. Spin. Lock_call(); Ke. Release. Spin. Lock(&dev. Ext->write. List. Lock); s 0: s 1: s 2: s 3: s 4: state = Locked; n. Packets. Old = n. Packets; request = dev. Ext->Write. List. Head. Va; assume(!request); assume(n. Packets != n. Packets. Old); s 5: assume(state==Locked); s 6: ERROR: enum { Unlocked=0, Locked } state = Unlocked; void slic_abort() { ERROR: // s 6 } void Ke. Acquire. Spin. Lock_call () { if(state==Locked) slic_abort(); // s 5 else state = Locked; // s 0 } void Ke. Release. Spin. Lock_call () { if(state==Unlocked) slic_abort(); else state = Unlocked; } 13

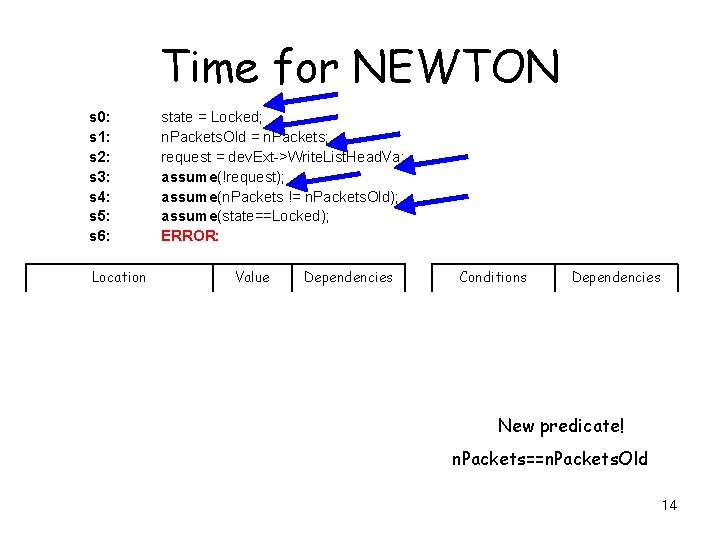
Time for NEWTON s 0: s 1: s 2: s 3: s 4: s 5: s 6: state = Locked; n. Packets. Old = n. Packets; request = dev. Ext->Write. List. Head. Va; assume(!request); assume(n. Packets != n. Packets. Old); assume(state==Locked); ERROR: Location Value Dependencies Conditions Dependencies 0. state Locked () !( ) 5 1. n. Packets () ( != ) 1, 2 2. n. Packets. Old 1 3. dev. Ext () 4. ->Write. List. Head. Va 3 5. request 3, 4 New predicate! n. Packets==n. Packets. Old 14

Big picture of SLAM process Spec. C program SLIC predicates Instrumented C program c 2 bp Boolean program predicates bebop newton Fail, p Error Pass 15

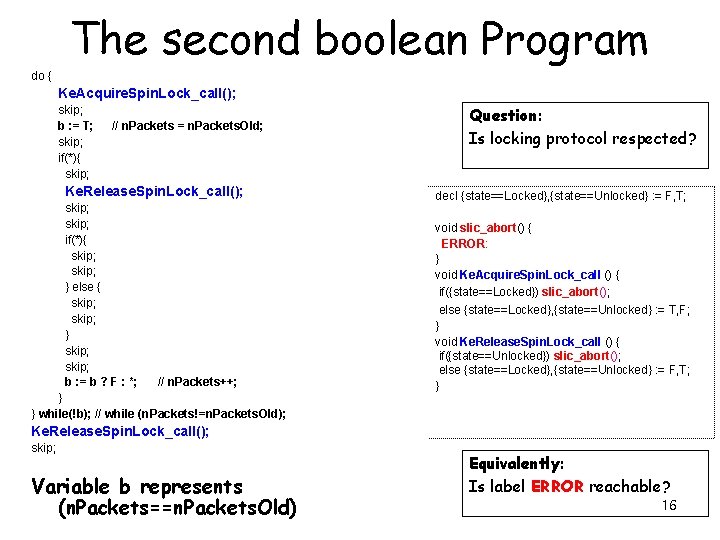
The second boolean Program do { Ke. Acquire. Spin. Lock_call(); skip; b : = T; skip; if(*){ skip; // n. Packets = n. Packets. Old; Ke. Release. Spin. Lock_call(); skip; if(*){ skip; } else { skip; } skip; b : = b ? F : *; // n. Packets++; } } while(!b); // while (n. Packets!=n. Packets. Old); Question: Is locking protocol respected? decl {state==Locked}, {state==Unlocked} : = F, T; void slic_abort() { ERROR: } void Ke. Acquire. Spin. Lock_call () { if({state==Locked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = T, F; } void Ke. Release. Spin. Lock_call () { if({state==Unlocked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = F, T; } Ke. Release. Spin. Lock_call(); skip; Variable b represents (n. Packets==n. Packets. Old) Equivalently: Is label ERROR reachable? 16

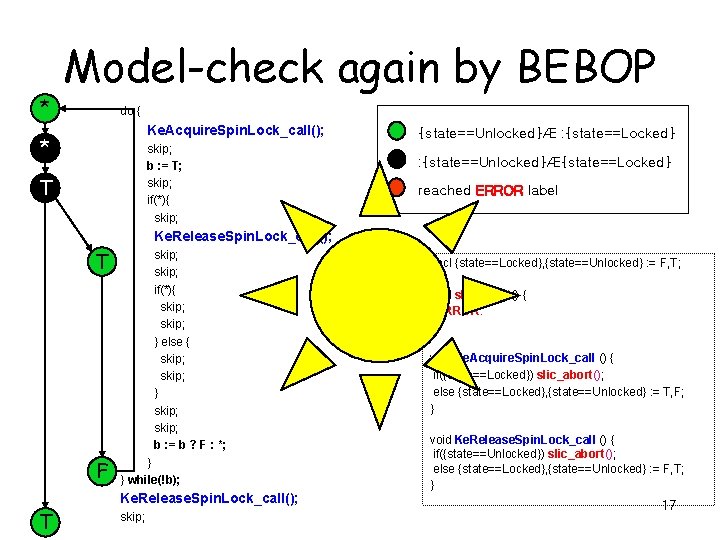
* Model-check again by BEBOP do { Ke. Acquire. Spin. Lock_call(); * skip; b : = T; skip; if(*){ skip; T {state==Unlocked}Æ : {state==Locked} : {state==Unlocked}Æ{state==Locked} reached ERROR label Ke. Release. Spin. Lock_call(); T F skip; if(*){ skip; } else { skip; } skip; b : = b ? F : *; } } while(!b); Ke. Release. Spin. Lock_call(); T skip; decl {state==Locked}, {state==Unlocked} : = F, T; void slic_abort() { ERROR: } void Ke. Acquire. Spin. Lock_call () { if({state==Locked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = T, F; } void Ke. Release. Spin. Lock_call () { if({state==Unlocked}) slic_abort(); else {state==Locked}, {state==Unlocked} : = F, T; } 17

Big picture of SLAM process Spec. C program SLIC predicates Instrumented C program c 2 bp Boolean program predicates bebop newton Fail, p Error Pass 18

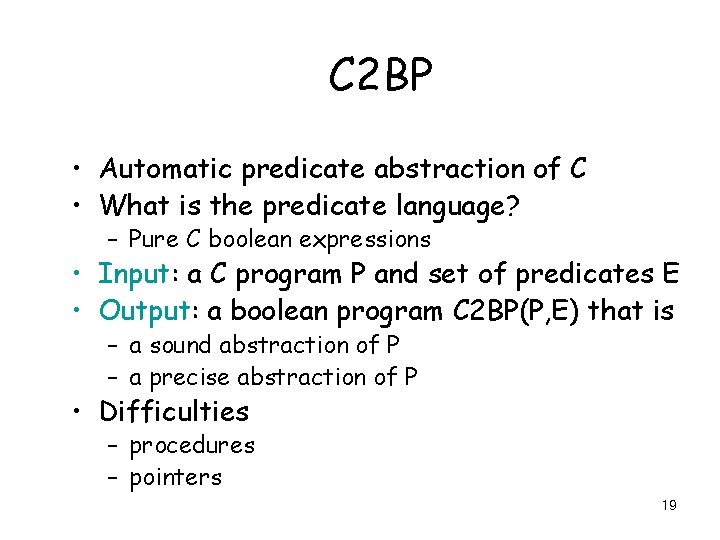
C 2 BP • Automatic predicate abstraction of C • What is the predicate language? – Pure C boolean expressions • Input: a C program P and set of predicates E • Output: a boolean program C 2 BP(P, E) that is – a sound abstraction of P – a precise abstraction of P • Difficulties – procedures – pointers 19
![BEBOP Reachability analysis of boolean programs Symbolic version of RepsHorwitzSagiv POPL 95 BEBOP § Reachability analysis of boolean programs § Symbolic version of [Reps-Horwitz-Sagiv, POPL’ 95]](https://slidetodoc.com/presentation_image/56f80ac5e7275286f6a9b025a82e22ea/image-20.jpg)
BEBOP § Reachability analysis of boolean programs § Symbolic version of [Reps-Horwitz-Sagiv, POPL’ 95] interprocedural data flow analysis § § Explicit representation of control flow Implicit representation of reachable states via BDDs 20

NEWTON • Symbolically executes (interprocedural) path in C program • Checks for path infeasibility using decision procedures (theorem provers: Simplify, Vampyre) • If infeasibility detected – Find weak(est) condition implying the infeasibility – Obtains new predicates 21

Contributions • Use of boolean programs for program abstractions • C 2 BP : the first automatic predicate abstraction tool for a full-scale language • BEBOP : the first model checker to handle procedure calls using inter-procedural DFA • Global analysis only on the boolean program abstractions : scalable…? 22

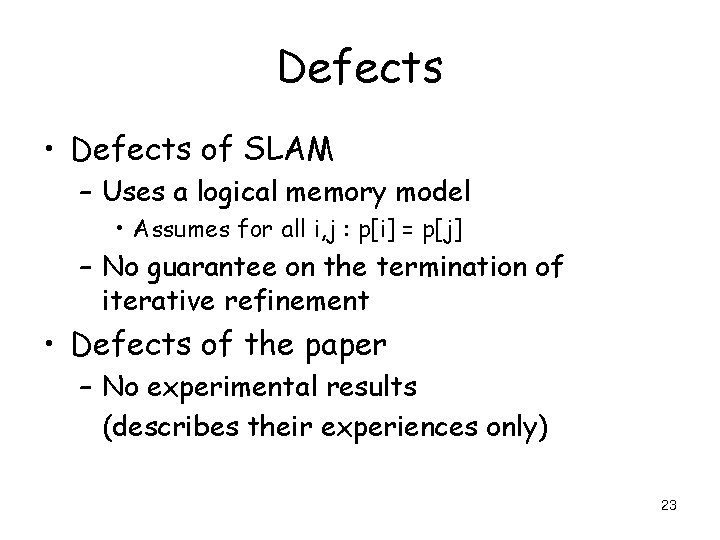
Defects • Defects of SLAM – Uses a logical memory model • Assumes for all i, j : p[i] = p[j] – No guarantee on the termination of iterative refinement • Defects of the paper – No experimental results (describes their experiences only) 23