Automatic Vulnerability Checking of IEEE 802 16 Wi

Automatic Vulnerability Checking of IEEE 802. 16 Wi. MAX Protocols through TLA+ Prasad Narayana, Ruiming Chen, Yao Zhao, Yan Chen and Hai Zhou Northwestern University, Evanston IL, USA Z. Judy Fu Motorola Labs, Schaumburg IL, USA

Outline • • • Motivation Our approach Background on TLA+ General methods and challenges Results on Wi. MAX initial ranging and authentication • Conclusions and future work

Motivation • High-speed Wireless Metropolitan Area Networks (MAN) poised to become the Next Big Thing • IEEE 802. 16 (Wi. MAX) with enormous backing from the industry is set to lead the broadband wireless network space • Security, as always, is key for its functioning and growth • However, security Analysis of the IEEE 802. 16 protocol largely confined to manual analysis – Incomplete – Inaccurate

Motivation (II) • Formal methods for automatic vulnerability checking highly desirable – With completeness and correctness guarantees • Previous studies focus on security protocols and security properties only – CSP and FDR [Lowe 96], MurØ [Shmatikov 98], Symbolic traces and PS-LTL [Corin 06] • Non-security protocol analysis focus on resource exhaustion Do. S attacks and ignore protocol malfunction attacks ! – [Yu 88], [Meadow 99], and [Meadow 02]
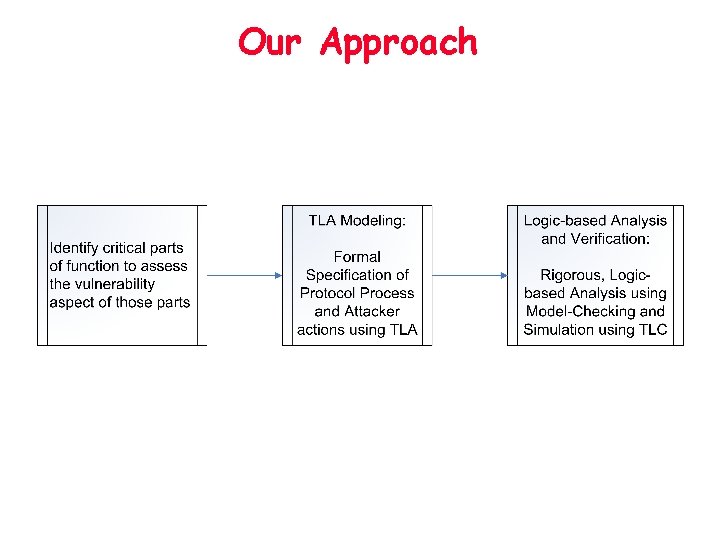
Our Approach • Vulnerability analysis of 802. 16 e specs and Wi. MAX standards – Systematic and automatic checking through formal methods. – First specify the specs and potential capabilities of attackers in a formal language TLA+ (the Temporal Logic of Actions) – Then model check for any possible attacks – The formal analysis can also help guide fixing of the flaws

Outline • • • Motivation Our approach Background on TLA+ General methods and challenges Results on Wi. MAX initial ranging and authentication • Conclusions and future work
TLA+ • TLA: a logic designed for specifying and reasoning about concurrent systems. – TLA+: a complete spec language based on TLA • First translate the natural language spec into a TLA+ spec, sys – Correctness request postulated as a TLA+ property, prop • Then to verify the correctness, prove sys → prop – Proof done automatically by model checker, TLC
Intro to TLA+ • TLA+ is a simple extension of linear temporal logic – With primed variable (x’) for next state – Temporal operations: []—forever • A system is specified as Init / [] [Next]x − system satisfies Init initially and satisfies Next for all transitions

TLA+ for Security • A protocol can be specified as one monolithic system • Or it can be specified as a composition of many components: – Comp. A / Comp. B / A i: Comp(i) • An attacker can be specified and composed with a protocol – System == Protocol / Attacker • Check security by – System => Properties
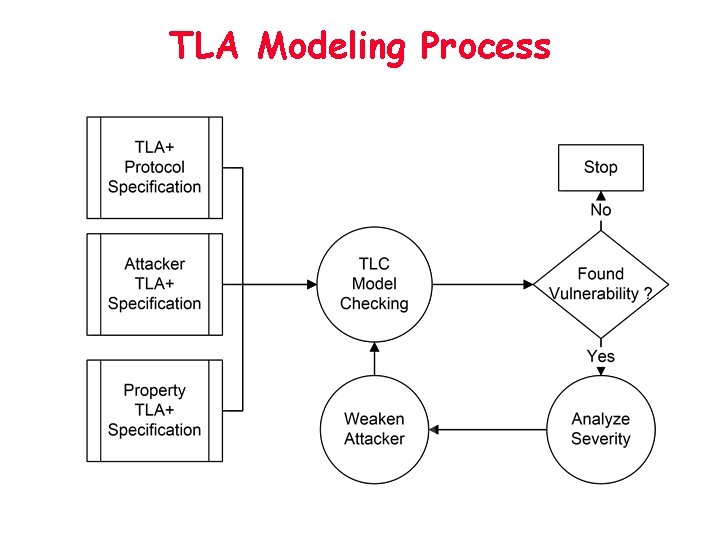
TLA Modeling Process
TLA+ Protocol Specification • Protocol specification in TLA+ can be easy or difficult – FSM easily translate to TLA+ – Tricky from English description to TLA+ spec: ambiguity, re-design, etc. • Process of protocol specification: – Identify principals – Modularize principal behavior using TLA+ – Compose a series of states and transitions for each principal – Specify flow of control between principals

Outline • • • Motivation Our approach Background on TLA+ General methods and challenges Results on Wi. MAX initial ranging and authentication • Conclusions and future work

TLA+ Protocol Specification – Challenges (I) • Vagueness in English specification and the correctness in its translation to TLA+. • Solutions – No good solution exists! – Better having protocols in TLA+ – Consult standards committee, product implementation teams among other things
TLA+ Protocol Specification – Challenges (II) • State space explosion • Solutions – Combine similar states without loss of functionality into one state – Replace some random variables with constants with some additional properties to simulate the effects of randomness – Define principals symmetric, which will treat the different states as one common state.

Attacker Model • Attacker capability model similar to Dolev -Yao model • Basically, attackers can: – Eavesdrop on and store messages. – Replay old messages. – Inject or spoof unprotected messages. – Corrupt messages on the channel by causing collisions. • We also assume the ideal cryptography, which means unforgeable signatures, safe encryption and safe digest

Attacker Model - Challenges • Challenge: How to find realistic attacks under such an attacker model ? • Our solution: – Start with a very strong attacker model » TLC model-checks may yield unrealistic attacks. – Then weaken the attacker model » E. g. : the attacker can continuously corrupt a response from the BS. » Since we are only interested in realistic attacks, we put restrictions on attacker behavior to remove such attacks. • This dynamic modification of attacker model will end up with – a complete robustness proof OR – a report of a realistic attack

Property Specification • Focus on Denial of Service (Do. S) currently – Client may reach a termination <>[] (A iin Party. Set: Party[i]. state=Obj. State – Client may not terminate []<>(A in Party. Set: Party[i]. state=Obj. State)
Model Checking with TLC • TLC is a model checker for TLA+ • Has both simulation mode and model checking mode – We run simulations before a complete model checking • Since TLA+ is very expressive, TLC currently can only check safety properties

Outline • • • Motivation Our approach Background on TLA+ General methods and challenges Results on Wi. MAX initial ranging and authentication • Conclusions and future work
Case Studies • Initial Ranging • Authentication processes • Choices based on the criticality of function and the probability of vulnerability
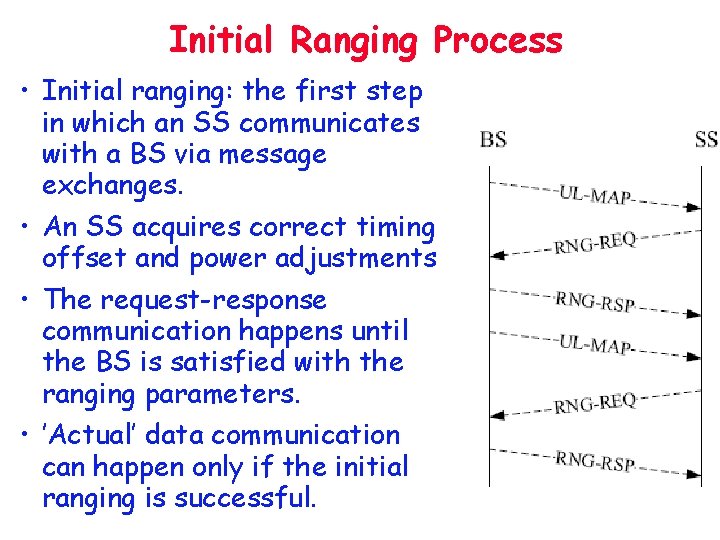
Initial Ranging Process • Initial ranging: the first step in which an SS communicates with a BS via message exchanges. • An SS acquires correct timing offset and power adjustments • The request-response communication happens until the BS is satisfied with the ranging parameters. • ’Actual’ data communication can happen only if the initial ranging is successful.
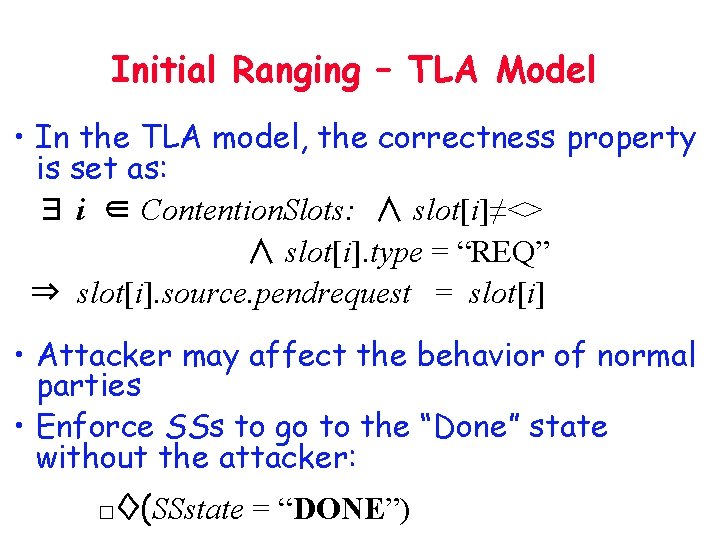
Initial Ranging – TLA Model • In the TLA model, the correctness property is set as: ∃ i ∈ Contention. Slots: ∧ slot[i]≠<> ∧ slot[i]. type = “REQ” ⇒ slot[i]. source. pendrequest = slot[i] • Attacker may affect the behavior of normal parties • Enforce SSs to go to the “Done” state without the attacker: □◊(SSstate = “DONE”)
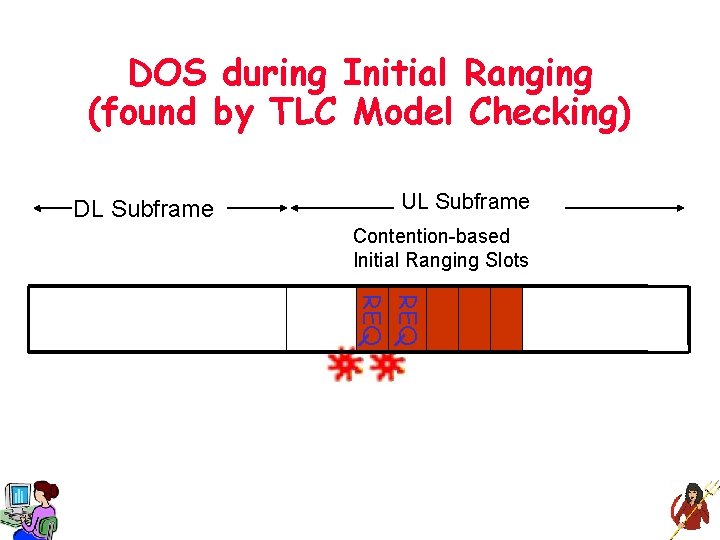
DOS during Initial Ranging (found by TLC Model Checking) DL Subframe UL Subframe Contention-based Initial Ranging Slots REQ
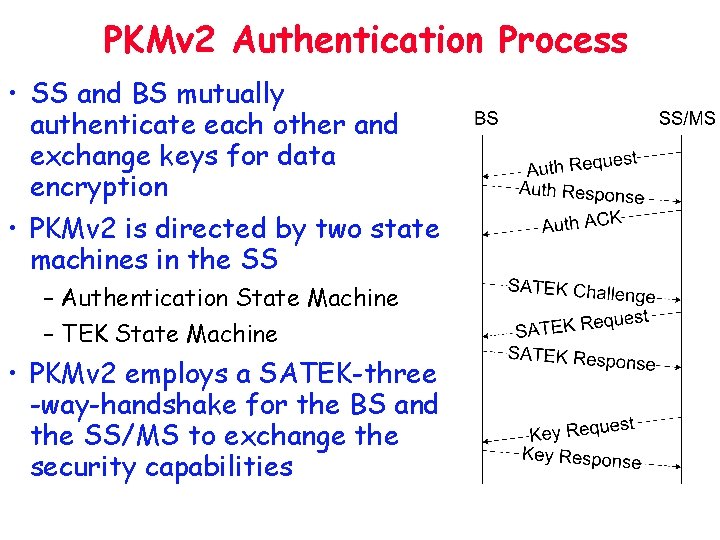
PKMv 2 Authentication Process • SS and BS mutually authenticate each other and exchange keys for data encryption • PKMv 2 is directed by two state machines in the SS – Authentication State Machine – TEK State Machine • PKMv 2 employs a SATEK-three -way-handshake for the BS and the SS/MS to exchange the security capabilities
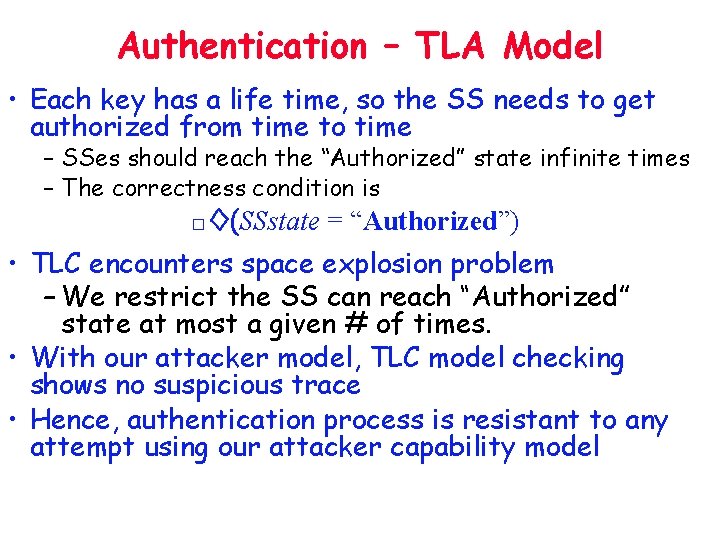
Authentication – TLA Model • Each key has a life time, so the SS needs to get authorized from time to time – SSes should reach the “Authorized” state infinite times – The correctness condition is □◊(SSstate = “Authorized”) • TLC encounters space explosion problem – We restrict the SS can reach “Authorized” state at most a given # of times. • With our attacker model, TLC model checking shows no suspicious trace • Hence, authentication process is resistant to any attempt using our attacker capability model

Outline • • • Motivation Our approach Background on TLA+ General methods and challenges Results on Wi. MAX initial ranging and authentication • Conclusions and future work

Conclusions • First step towards automatic vulnerability checking of any network protocols with completeness and correctness guarantees • Use TLA+/TLC to model all Do. S attacks – Avoid state space explosion in property checking – Model attackers’ capabilities for finding realistic attacks • Study the initial ranging and authentication processes in 802. 16 protocols

Future Work • Development of a rigorous process in protocol specification using TLA+ language • Modeling of inter-relationships of processes/components • Check vulnerabilities in other parts of 802. 16 standards such as mobility support and handoff procedures.

Backup Slides
Our Approach
Related Work (2) • Automatically check with formal language – For security network protocols » CSP and FDR [Lowe 96] » MurØ [Shmatikov 98] » Symbolic traces and PS-LTL [Corin 06] – For Do. S attack » “A formal specification and verification method for the prevention of denial of service” [Yu 88] » “Game-based analysis of denial-of-service prevention protocols” [Mahimkar 05]
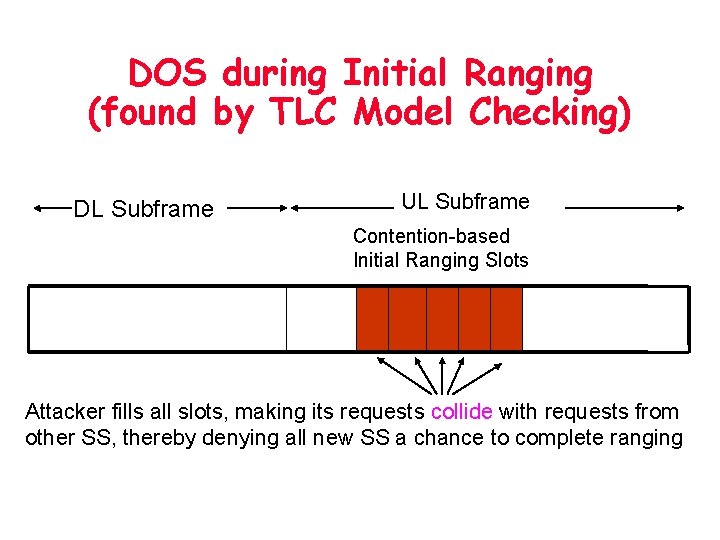
DOS during Initial Ranging (found by TLC Model Checking) DL Subframe UL Subframe Contention-based Initial Ranging Slots Attacker fills all slots, making its requests collide with requests from other SS, thereby denying all new SS a chance to complete ranging
- Slides: 32