Automatic Realtime Counterattack System against Remote Buffer Overflow

Automatic Real-time Counterattack System against Remote Buffer Overflow Attack 許富皓 先進防禦實驗室 資訊 程學系 國立中央大學 1

Some Recently News Titles Downadup worm infects more than 3. 5 million - Published: 2009 -01 -14 Downadup virus exposes millions of PCs to hijack – CNN 16 th Jan. 2009 Microsoft announces $250000 Conficker worm bounty - Network World 2
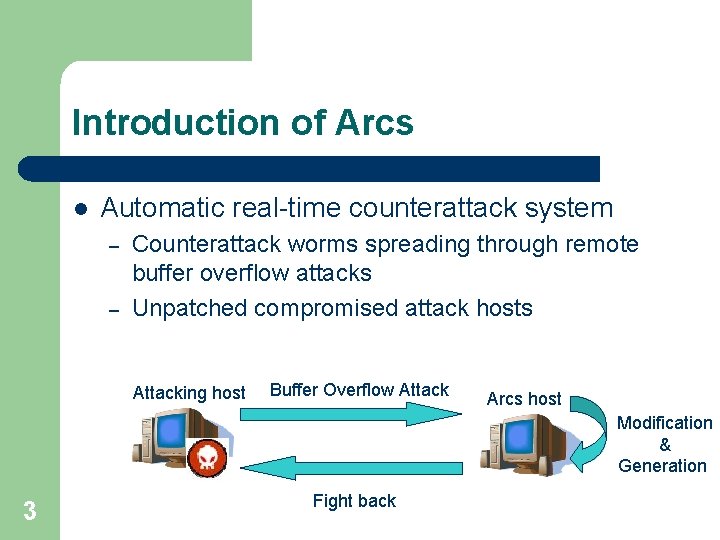
Introduction of Arcs l Automatic real-time counterattack system – – Counterattack worms spreading through remote buffer overflow attacks Unpatched compromised attack hosts Attacking host Buffer Overflow Attack Arcs host Modification & Generation 3 Fight back
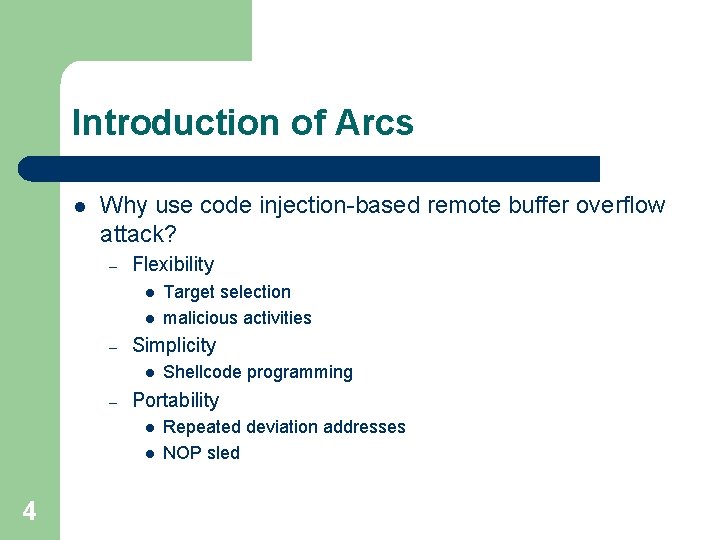
Introduction of Arcs l Why use code injection-based remote buffer overflow attack? – Flexibility l l – Simplicity l – Shellcode programming Portability l l 4 Target selection malicious activities Repeated deviation addresses NOP sled
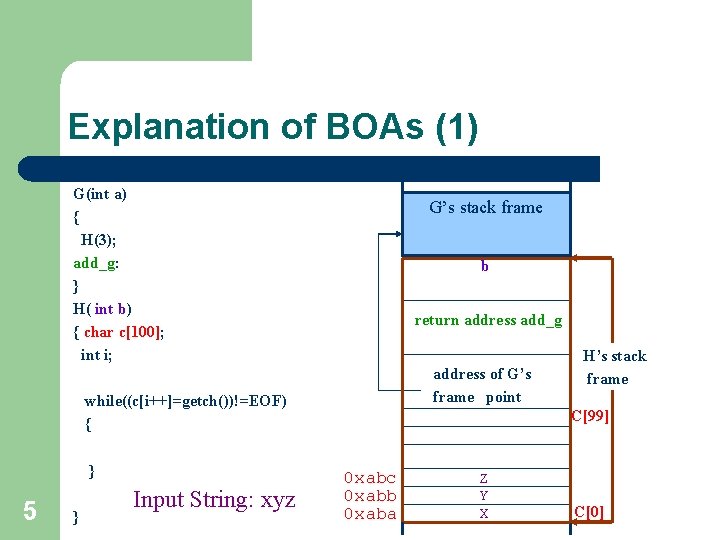
Explanation of BOAs (1) G(int a) { H(3); add_g: } H( int b) { char c[100]; int i; G’s stack frame b return address add_g address of G’s frame point while((c[i++]=getch())!=EOF) { } 5 } Input String: xyz H’s stack frame C[99] 0 xabc 0 xabb 0 xaba Z Y X C[0]
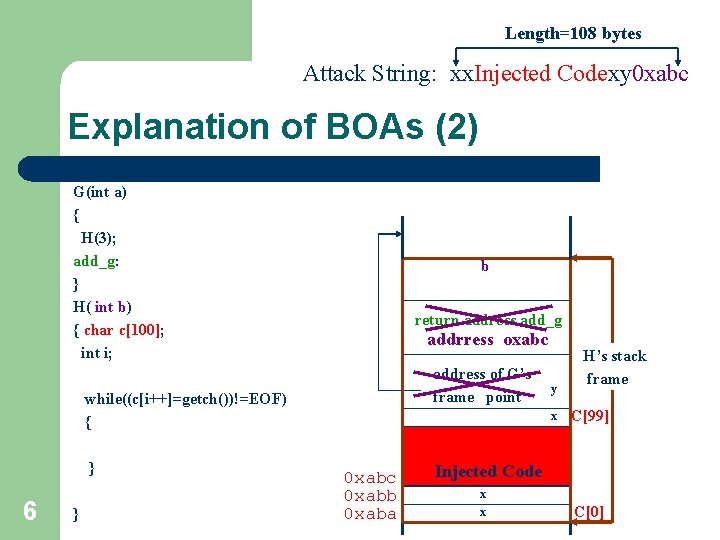
Length=108 bytes Attack String: xx. Injected Codexy 0 xabc Explanation of BOAs (2) G(int a) { H(3); add_g: } H( int b) { char c[100]; int i; b return address add_g addrress oxabc address of G’s frame point while((c[i++]=getch())!=EOF) { } 6 } y x 0 xabc 0 xabb 0 xaba H’s stack frame C[99] Injected Code x x C[0]

Injected Code: l l The attacked programs usually have root privilege; therefore, the injected code is executed with root privilege. The injected code is already in machine instruction form; therefore, a CPU can directly execute it. – l 7 However the above fact also means that the injected code must match the CPU type of the attacked host. Usually the injected code will fork a shell; hence, after an attack, an attacker could have a root shell.
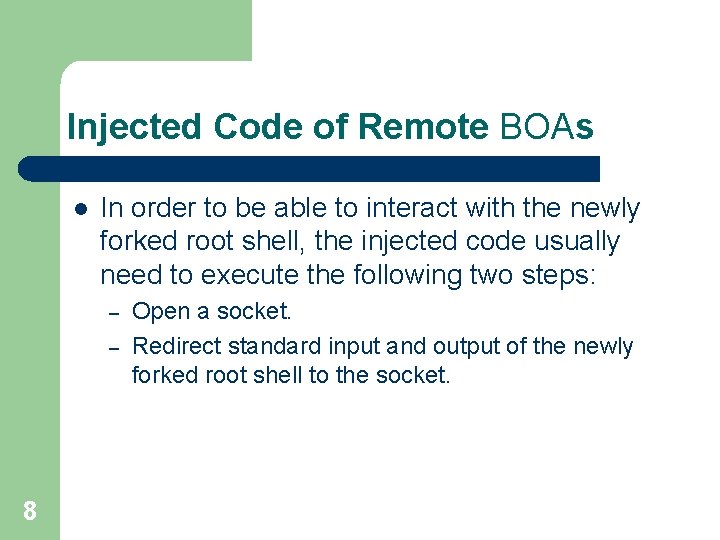
Injected Code of Remote BOAs l In order to be able to interact with the newly forked root shell, the injected code usually need to execute the following two steps: – – 8 Open a socket. Redirect standard input and output of the newly forked root shell to the socket.
![Example of Injected Code for X 86 Architecture : Shell Code l char shellcode[] Example of Injected Code for X 86 Architecture : Shell Code l char shellcode[]](http://slidetodoc.com/presentation_image_h2/d9d948aec9ccff837ec50f0489c62a2f/image-9.jpg)
Example of Injected Code for X 86 Architecture : Shell Code l char shellcode[] = "xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 07x 89x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcd x 80x 31xdbx 89xd 8x 40xcdx 80xe 8xdcxffxff/ bin/sh"; 9

Two Factors for A Successful Buffer Overflow-style Attack(1) l 10 A successful buffer overflow-style attack should be able to overflow the right place (e. g. the place to hold a return address with the correct value (e. g. the address of injected code entry point)).
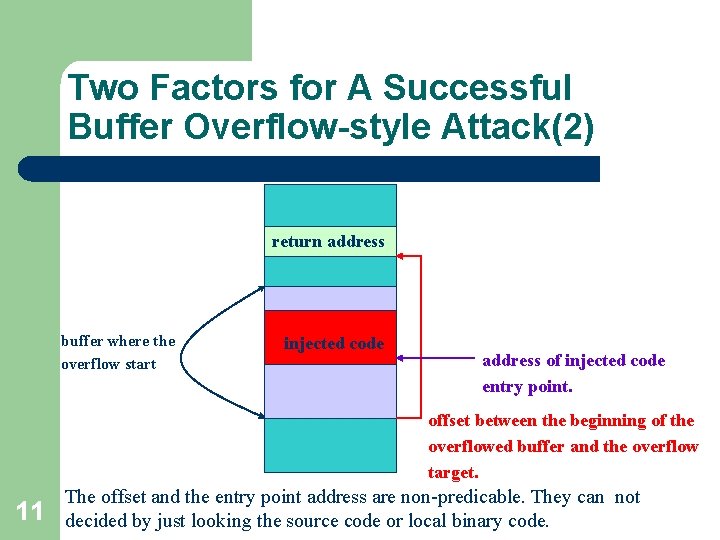
Two Factors for A Successful Buffer Overflow-style Attack(2) return address buffer where the overflow start injected code address of injected code entry point. offset between the beginning of the overflowed buffer and the overflow target. 11 The offset and the entry point address are non-predicable. They can not decided by just looking the source code or local binary code.
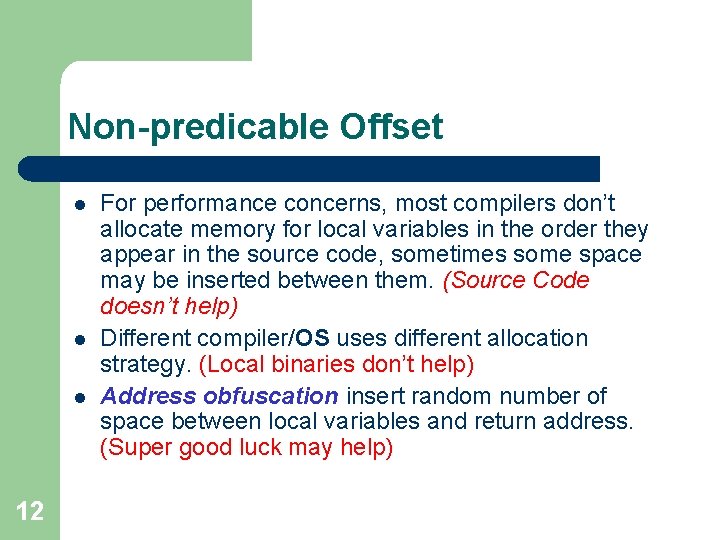
Non-predicable Offset l l l 12 For performance concerns, most compilers don’t allocate memory for local variables in the order they appear in the source code, sometimes some space may be inserted between them. (Source Code doesn’t help) Different compiler/OS uses different allocation strategy. (Local binaries don’t help) Address obfuscation insert random number of space between local variables and return address. (Super good luck may help)
![Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment](http://slidetodoc.com/presentation_image_h2/d9d948aec9ccff837ec50f0489c62a2f/image-13.jpg)
Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment variables argument strings env pointers argc Function main()’s stack frame 13 command line arguments and environment variables

Strategies Used by Attackers to Increase Their Success Chance l l 14 Repeat address patterns. Insert NOP (0 x 90) operations before the entry point of injected code.
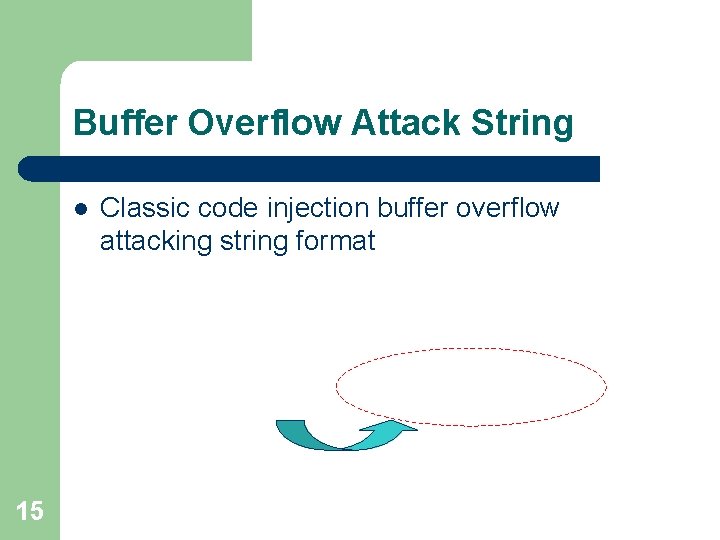
Buffer Overflow Attack String l 15 Classic code injection buffer overflow attacking string format
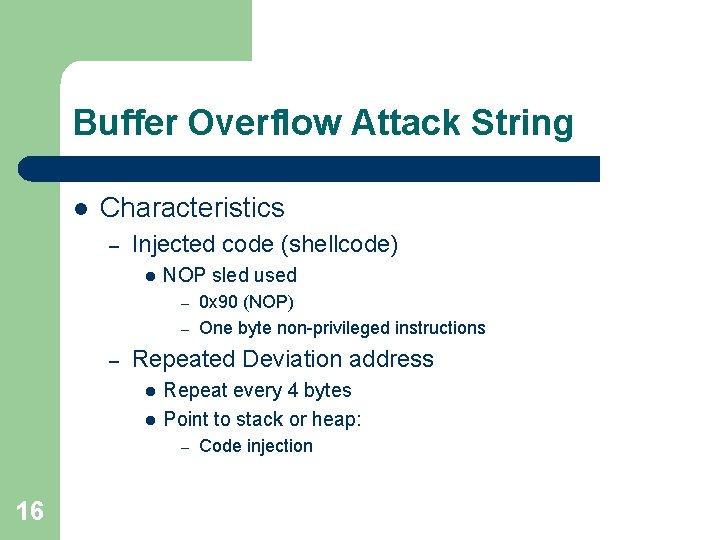
Buffer Overflow Attack String l Characteristics – Injected code (shellcode) l NOP sled used 0 x 90 (NOP) – One byte non-privileged instructions – – Repeated Deviation address l l Repeat every 4 bytes Point to stack or heap: – 16 Code injection
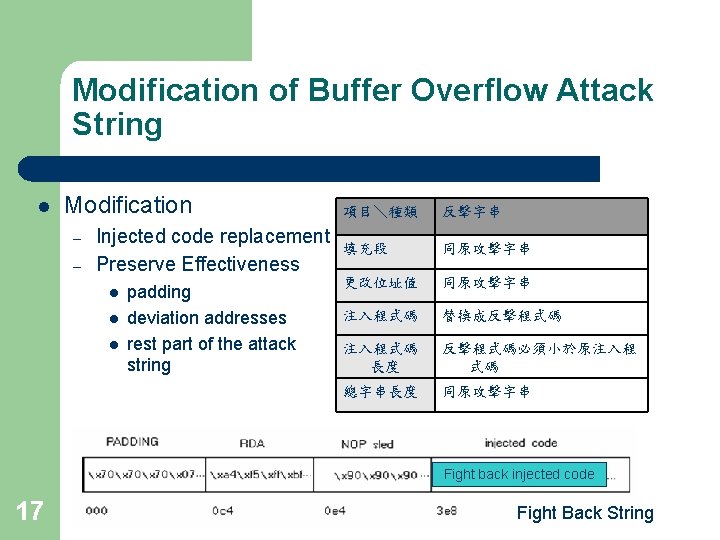
Modification of Buffer Overflow Attack String l Modification – – Injected code replacement Preserve Effectiveness l l l padding deviation addresses rest part of the attack string 項目\種類 反擊字串 填充段 同原攻擊字串 更改位址值 同原攻擊字串 注入程式碼 替換成反擊程式碼 注入程式碼 長度 反擊程式碼必須小於原注入程 式碼 總字串長度 同原攻擊字串 Fight back injected code 17 Fight Back String
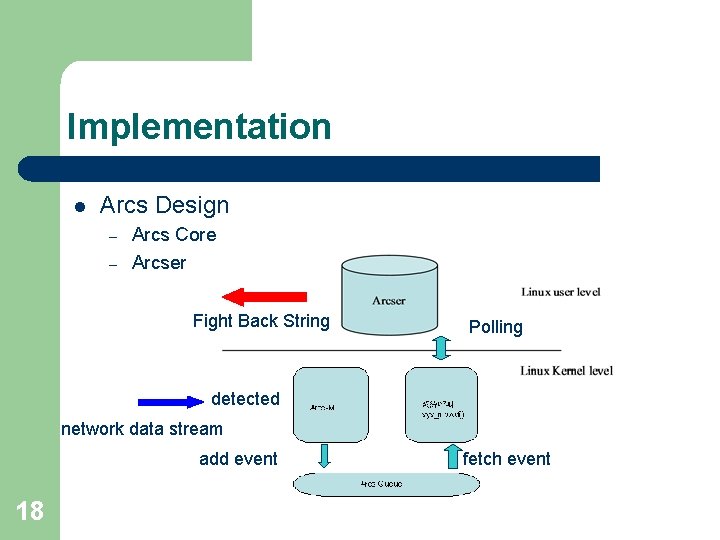
Implementation l Arcs Design – – Arcs Core Arcser Fight Back String Polling detected network data stream add event 18 fetch event
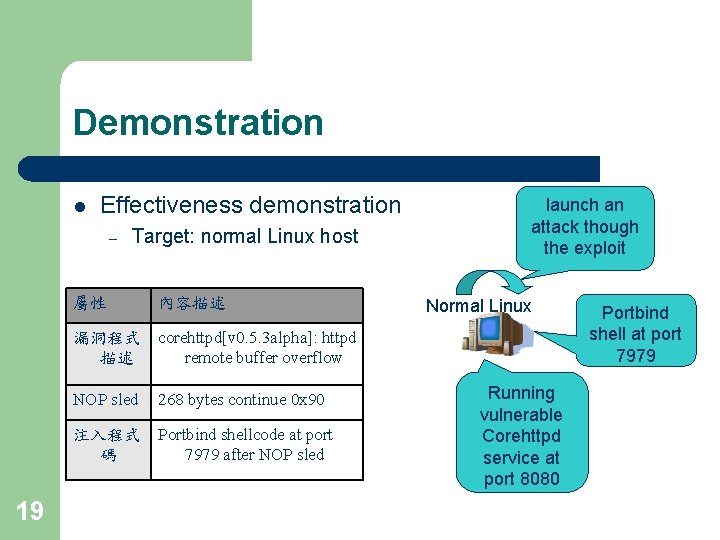
Demonstration l Effectiveness demonstration – Target: normal Linux host 屬性 內容描述 launch an attack though the exploit Normal Linux 漏洞程式 corehttpd[v 0. 5. 3 alpha]: httpd 描述 remote buffer overflow NOP sled 268 bytes continue 0 x 90 注入程式 Portbind shellcode at port 碼 7979 after NOP sled 19 Running vulnerable Corehttpd service at port 8080 Portbind shell at port 7979
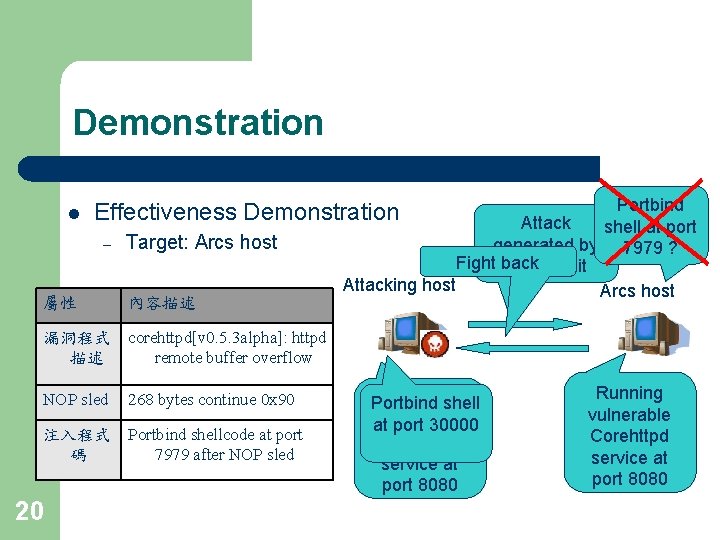
Demonstration l Portbind Attack shell at port generated by 7979 ? Fight back the exploit Attacking host Arcs host Effectiveness Demonstration – 屬性 Target: Arcs host 內容描述 漏洞程式 corehttpd[v 0. 5. 3 alpha]: httpd 描述 remote buffer overflow NOP sled 268 bytes continue 0 x 90 注入程式 Portbind shellcode at port 碼 7979 after NOP sled 20 Running Portbind shell vulnerable at port 30000 Corehttpd service at port 8080 Running vulnerable Corehttpd service at port 8080
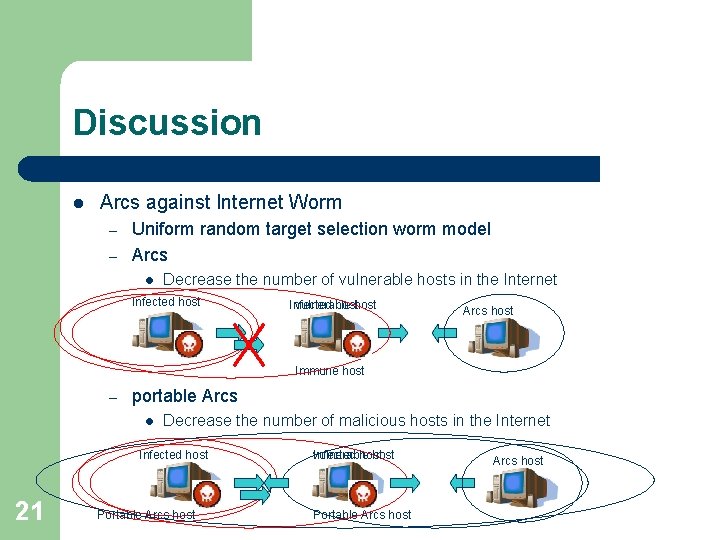
Discussion l Arcs against Internet Worm – – Uniform random target selection worm model Arcs l Decrease the number of vulnerable hosts in the Internet Infected hosthost vulnerable Arcs host Immune host – portable Arcs l Decrease the number of malicious hosts in the Internet Infected host 21 Portable Arcs host vulnerable Infected host Portable Arcs host
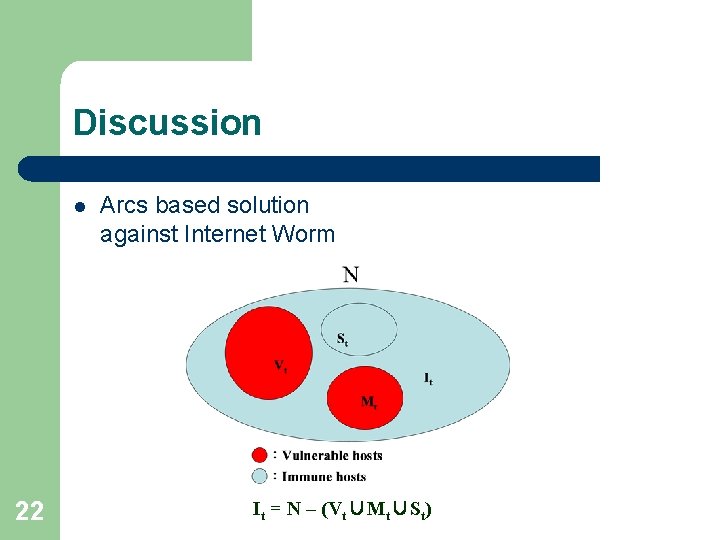
Discussion l 22 Arcs based solution against Internet Worm It = N – (Vt∪Mt∪St)
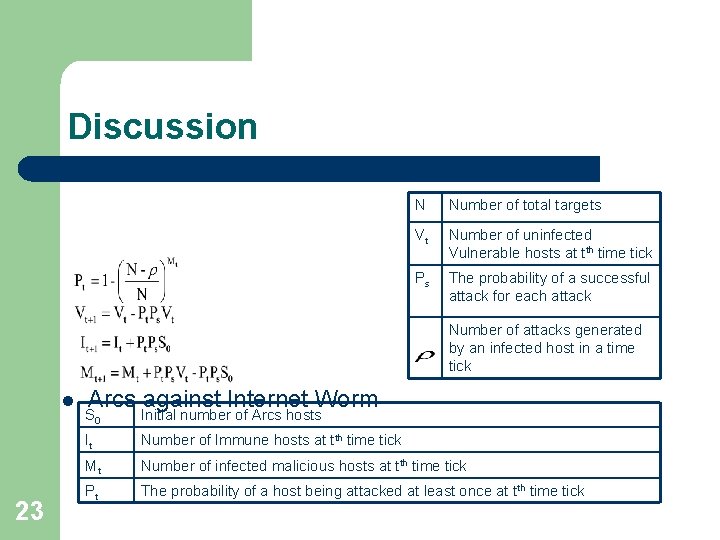
Discussion N Number of total targets Vt Number of uninfected Vulnerable hosts at tth time tick Ps The probability of a successful attack for each attack Number of attacks generated by an infected host in a time tick l 23 Arcs against Internet Worm S 0 Initial number of Arcs hosts It Number of Immune hosts at tth time tick Mt Number of infected malicious hosts at tth time tick Pt The probability of a host being attacked at least once at tth time tick
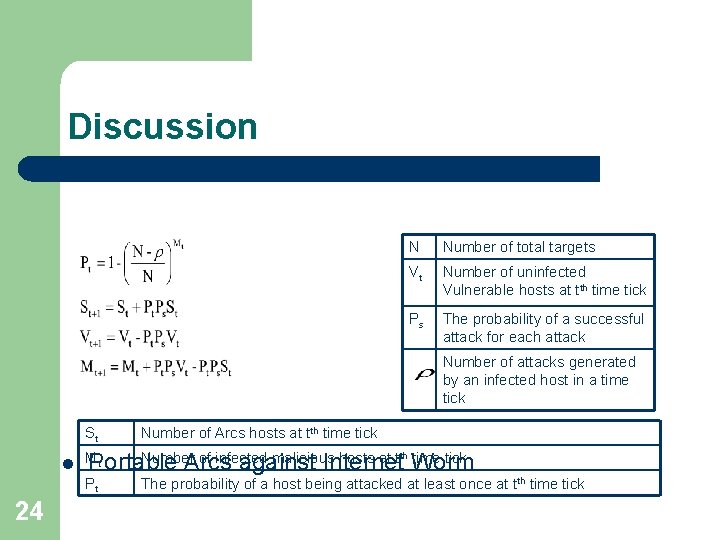
Discussion N Number of total targets Vt Number of uninfected Vulnerable hosts at tth time tick Ps The probability of a successful attack for each attack Number of attacks generated by an infected host in a time tick St Number of Arcs hosts at tth time tick Number of infected malicious hosts at tth Worm time tick t l M Portable Arcs against Internet Pt 24 The probability of a host being attacked at least once at tth time tick
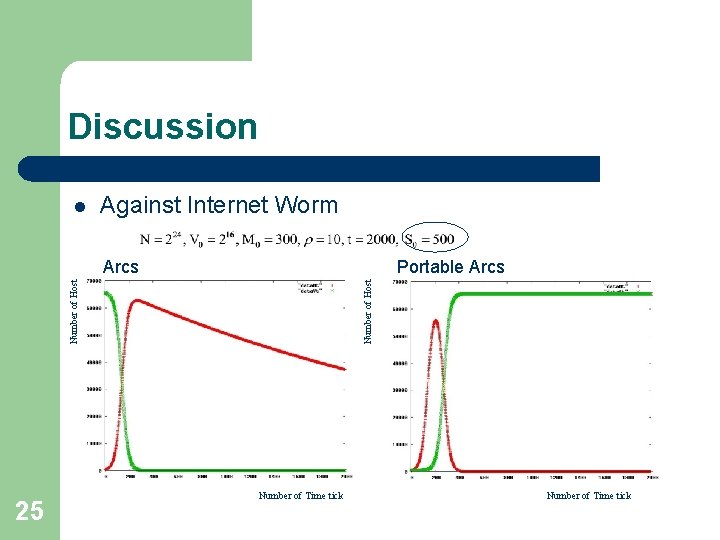
Discussion l Against Internet Worm 25 Number of Host Portable Arcs Number of Host Arcs Number of Time tick
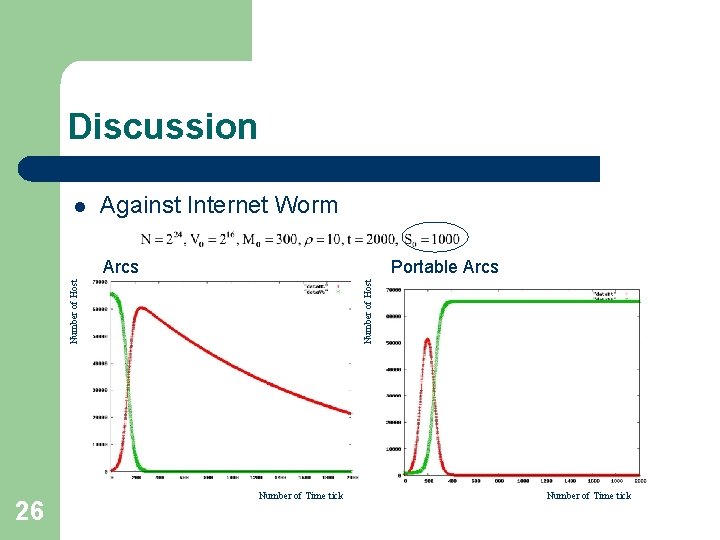
Discussion l Against Internet Worm 26 Number of Host Portable Arcs Number of Host Arcs Number of Time tick
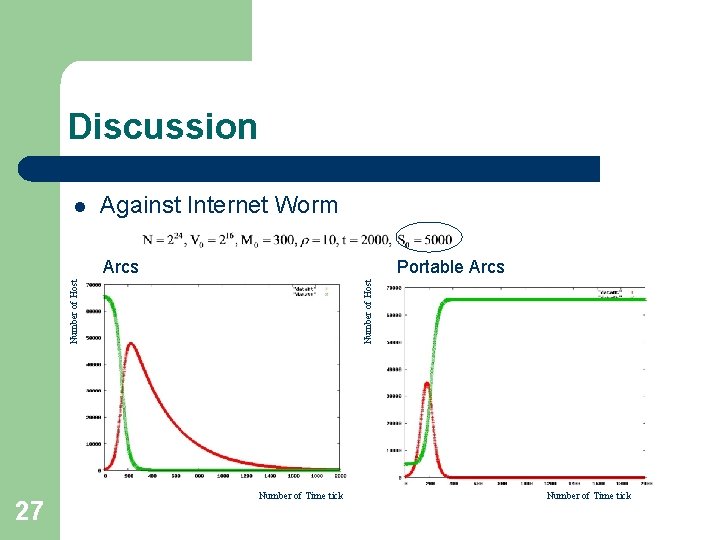
Discussion l Against Internet Worm 27 Number of Host Portable Arcs Number of Host Arcs Number of Time tick
Discussion l Limitations – Detection l – Modification l l 28 NON-repeated deviation address Multiple NOP sleds Extremely small injected code

Discussion l Counterattack risk – – 29 Legal or illegal Arcs attacks Arcs

Discussion l Deployment strategies – – l Future work – 30 As Honeypot As important server protection Both of above. Depending on managers’ requirements Arcs-based worm auto cleaning system

Related work l Worm – – 31 White Worm Watertight compartment Vaccination Detection and monitoring
Conclusion l Automatic buffer overflow attacking string modification – – l Arcs – – – l Automatic real-time counterattack system Flexible deployment Remote buffer overflow attack deterrence Arcs-based applications – – 32 Injected code replacement Effectiveness preserved Cleaning worm Detecting and identifying Botnet

Q&A 33
- Slides: 33