Automatic Noninterference Lemmas for Parameterized Model Checking Jesse


![Transition relation syntax l atoms l l l w (w : Bool ) x[p] Transition relation syntax l atoms l l l w (w : Bool ) x[p]](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-14.jpg)
![Views [Chou et al 04] l a view only includes info regarding a small Views [Chou et al 04] l a view only includes info regarding a small](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-16.jpg)

![Case Studies (1/3) l GERMAN [German 00] l l “hello world” for parameterized verification Case Studies (1/3) l GERMAN [German 00] l l “hello world” for parameterized verification](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-22.jpg)
![Case Studies (2/3) l FLASH [Kuskin et al 94] l l l “…if [a Case Studies (2/3) l FLASH [Kuskin et al 94] l l l “…if [a](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-23.jpg)

![Views abstract domain is sets of views [Chou et al 04], which are assignments Views abstract domain is sets of views [Chou et al 04], which are assignments](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-42.jpg)

- Slides: 46

Automatic Non-interference Lemmas for Parameterized Model Checking Jesse Bingham, Intel DEG FMCAD 2008 1

Classic CMP Approach l CMP approach [Mc. Millan 99/01, Chou et al. 04, Krstic 05, Lv et al 07, Li 07, Talupur & Tuttle 08] l l human writes non-interference lemmas from counterexamples system is iteratively strengthened with lemmas until all lemmas and property hold 2

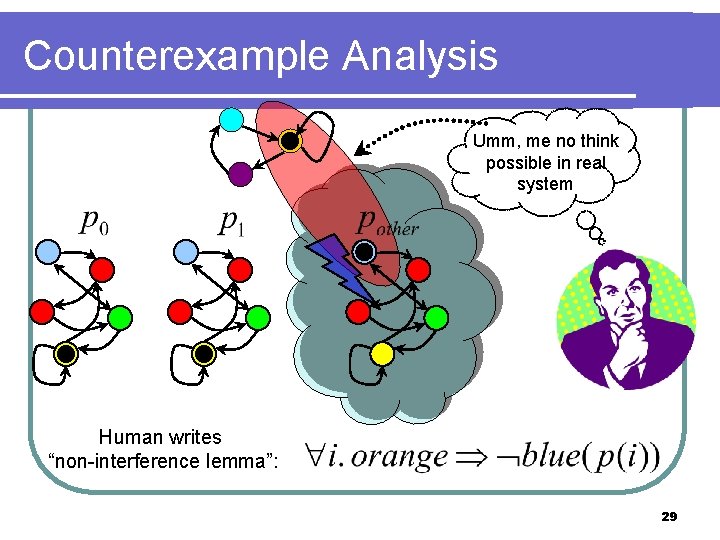
CMP requires human to write lemmas Umm, me no think possible in real system Human writes “non-interference lemma”: 3

What we do l our approach removes lemma-writing burden of human’s shoulders l l l start with “non-interference conjecture” False abstract strengthened system compute abstract reachability fixpoint iterate, with concretized fixpoint as new conjecture our contributions l l general theory based on abstract interpretation instantiation of theory for class of parameterized protocols using BDDs & prototype tool 4

Roadmap l General Theory l Symmetric Parameterized Protocols l Case Studies/Final Thoughts 5

Theory concrete transition system (C, I, T) l C is the set of (concrete) states l I C are the initial states l T C C is the transition relation l Reach(C, I, T) denotes set of reachable states l p C is called an invariant if Reach(C, I, T) p l for C define post[T]( ) = {y | x. (x, y) T and x } l 6

Strengthening For C, the strengthening of (C, I, T) by , is the transition system (C, I, T ( C)). We denote the strengthening by T # . Strengthen with = blue states Theorem. is an invariant of (C, I, T) if and only if is an invariant of T # . 7

Abstraction l finite abstract domain A along with partial order ⊑ , forming a lattice (A, ⊑) l l Think of ⊑ as subset ordering on represented sets galois connection ( , ) defines association between concrete states and abstract domain l : 2 C A l : A 2 C l and are order preserving l other technical properties 8

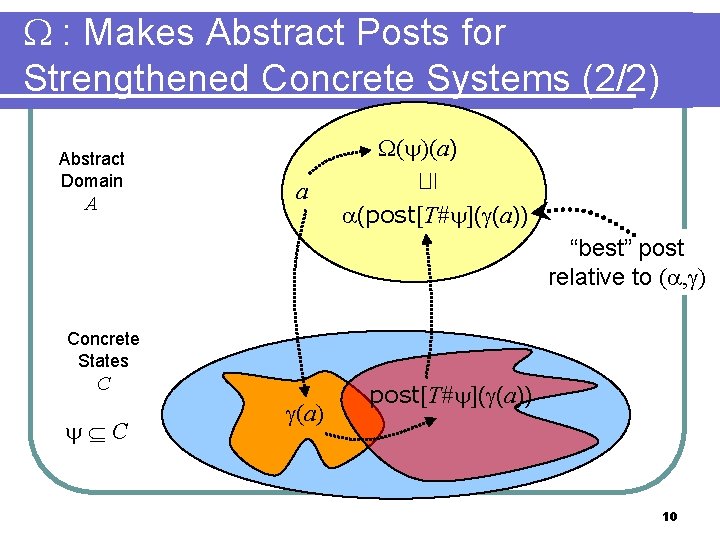
: Makes Abstract Posts for Strengthened Concrete Systems (1/2) set of concrete states ( ) : A A Abstract post (a. k. a abstract interpretation) of post[T # ] 9

: Makes Abstract Posts for Strengthened Concrete Systems (2/2) A ( )(a) a ⊑ Abstract Domain (post[T# ]( (a)) “best” post relative to ( , ) Concrete States C C (a) post[T# ]( (a)) 10

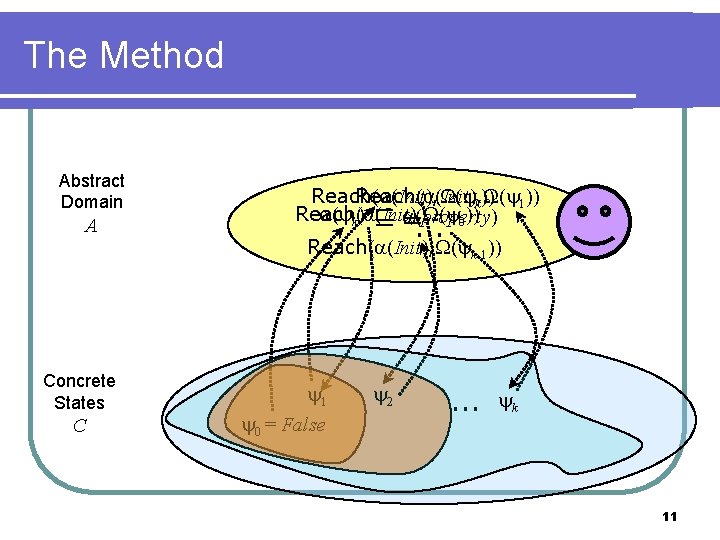
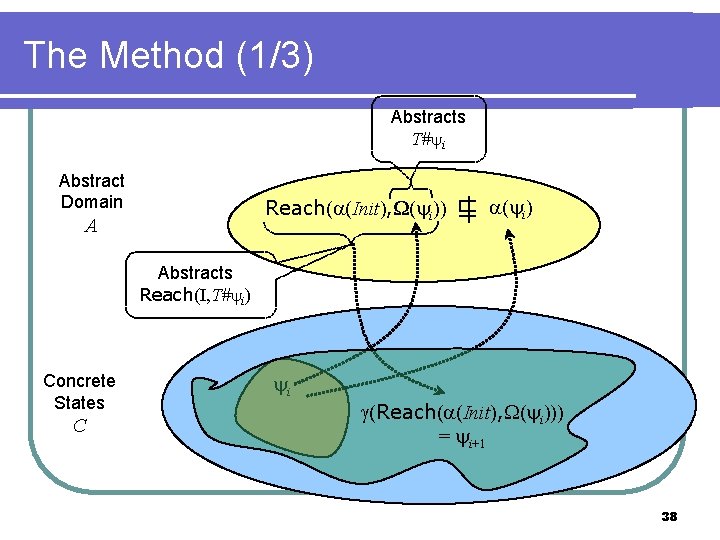
The Method Abstract Domain A Concrete States C Reach( (Init), ( k)) 1)) Reach( (Init), ( ( k) ⊑ = (property) 0)) … Reach( (Init), ( 1 0 = False 2 k-1)) … k 11

Roadmap l General Theory l Parameterized Protocols l Case Studies/Final Thoughts 12

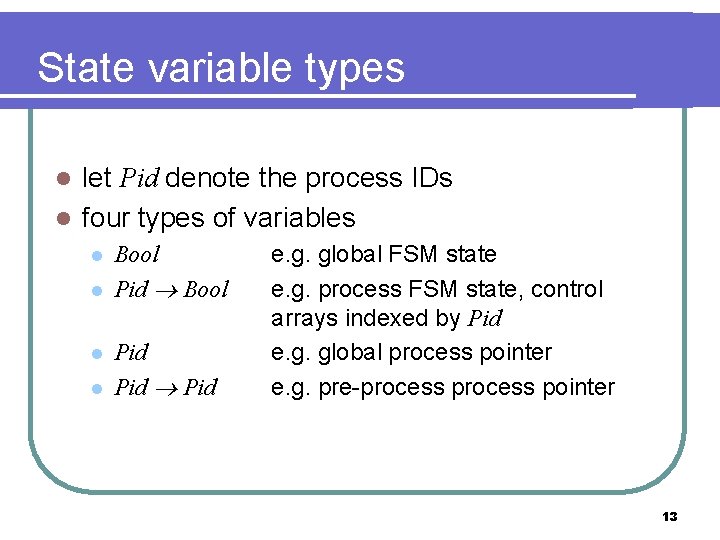
State variable types let Pid denote the process IDs l four types of variables l l l Bool Pid Pid e. g. global FSM state e. g. process FSM state, control arrays indexed by Pid e. g. global process pointer e. g. pre-process pointer 13
![Transition relation syntax l atoms l l l w w Bool xp Transition relation syntax l atoms l l l w (w : Bool ) x[p]](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-14.jpg)
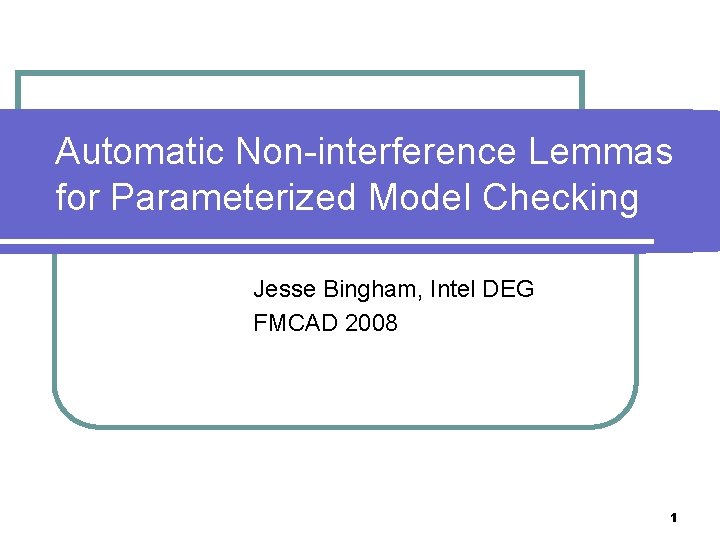
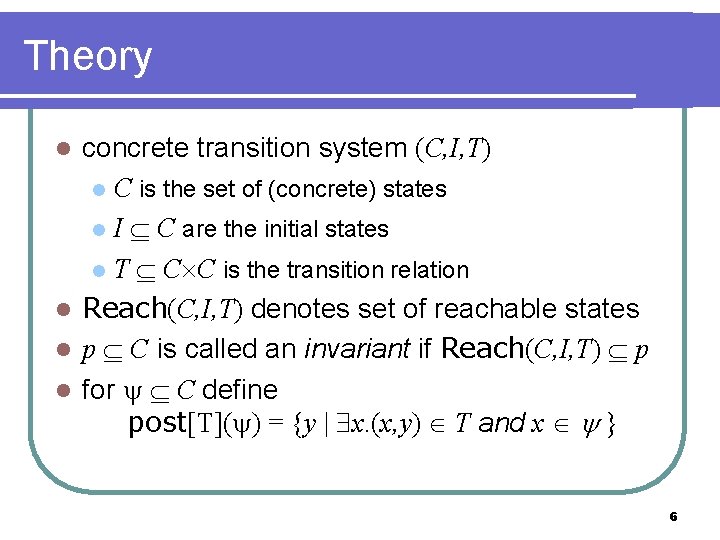
Transition relation syntax l atoms l l l w (w : Bool ) x[p] (x : Pid Bool and quantifed var p ) y=p (y : Pid and quantifed var p ) z[p]=q (z : Pid and quant vars p & q) plus any of the above with priming transition formula syntax: where 0 and 1 are (restricted) boolean combinations of atoms 14

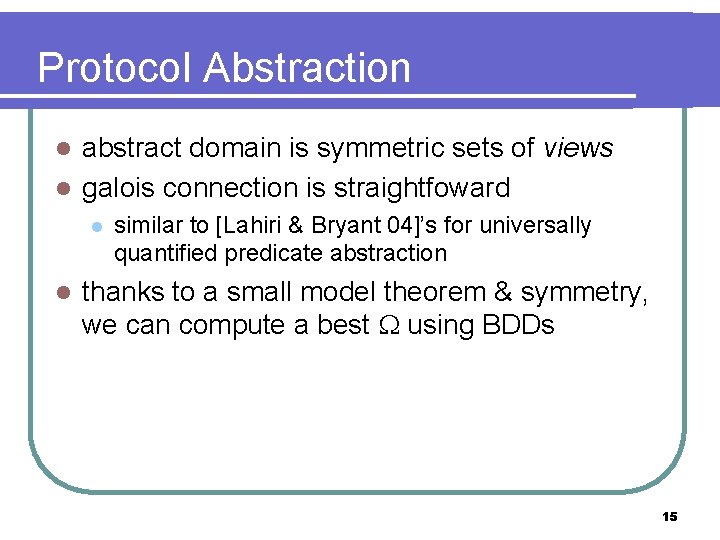
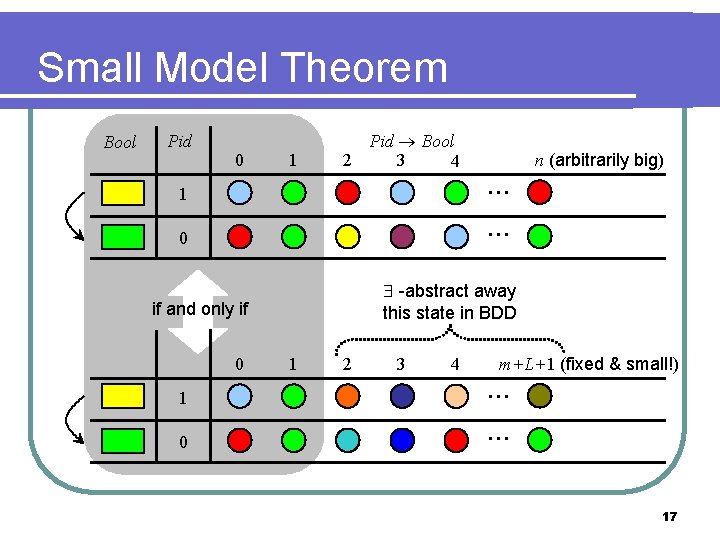
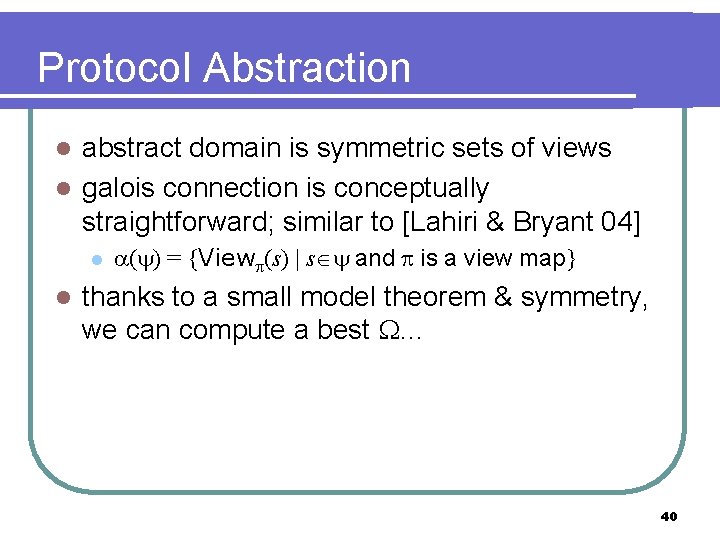
Protocol Abstraction abstract domain is symmetric sets of views l galois connection is straightfoward l l l similar to [Lahiri & Bryant 04]’s for universally quantified predicate abstraction thanks to a small model theorem & symmetry, we can compute a best using BDDs 15
![Views Chou et al 04 l a view only includes info regarding a small Views [Chou et al 04] l a view only includes info regarding a small](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-16.jpg)
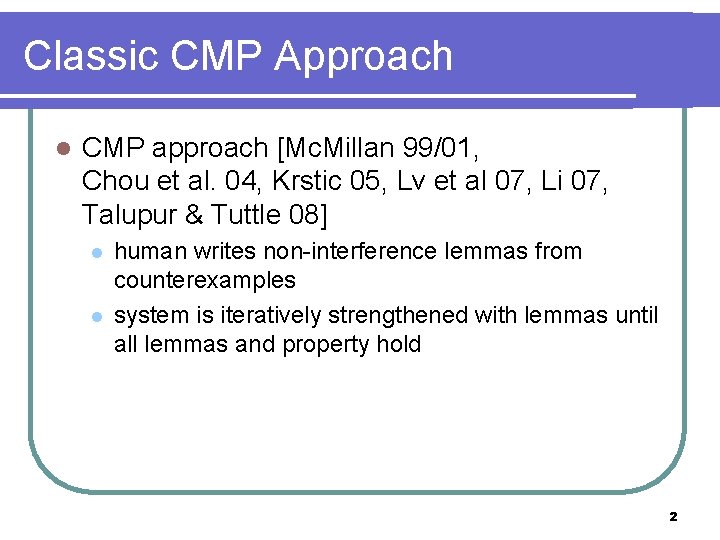
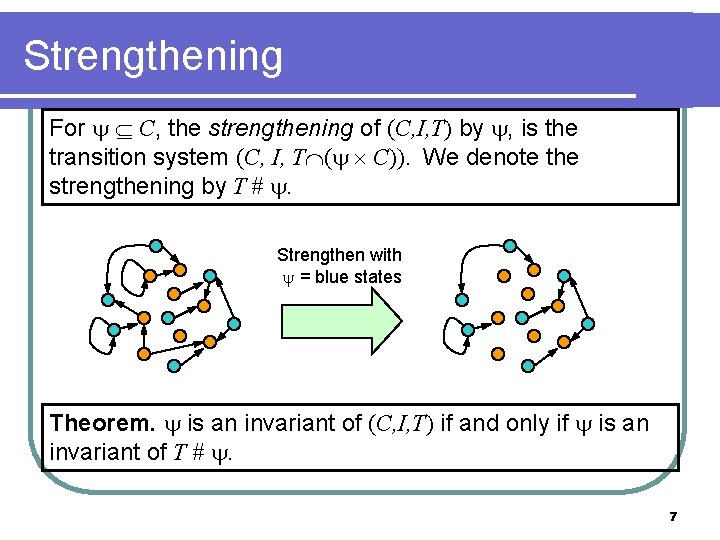
Views [Chou et al 04] l a view only includes info regarding a small number m of processes; Pid vars take values from {0, …, m-1, other} Bool 3 0 Pid Bool 1 2 3 1 View (m=2) Bool View (m=2) 0 Pid Bool 1 2 1 Concrete state Pid 3 other 16

Small Model Theorem Bool Pid 0 1 Pid Bool 2 3 4 1 0 -abstract away this state in BDD if and only if 0 1 0 … … n (arbitrarily big) 1 2 3 4 m+L+1 (fixed & small!) … … 17

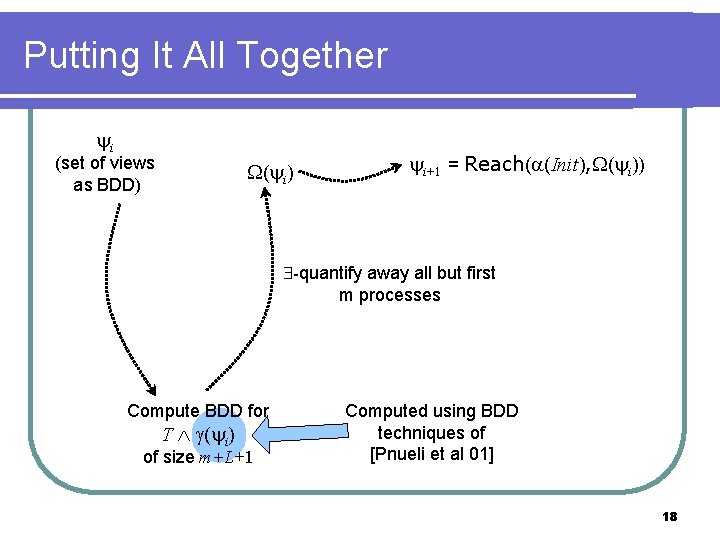
Putting It All Together i (set of views as BDD) ( i) i+1 = Reach( (Init), ( i)) -quantify away all but first m processes Compute BDD for T ( i) of size m+L+1 Computed using BDD techniques of [Pnueli et al 01] 18

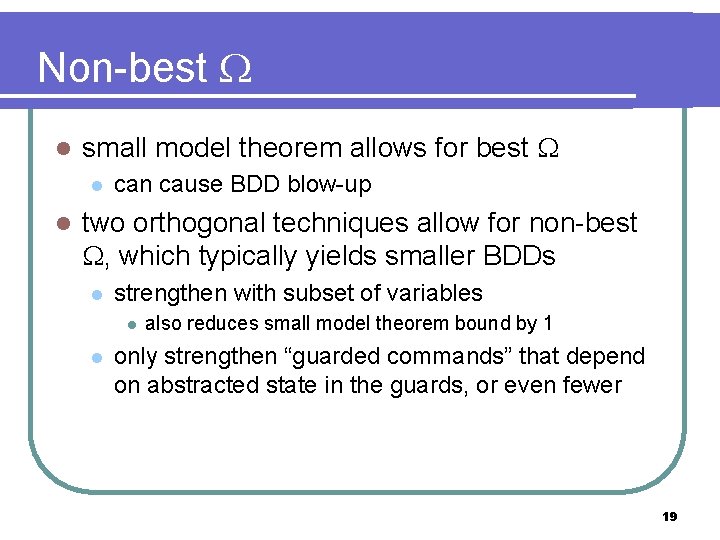
Non-best l small model theorem allows for best l l can cause BDD blow-up two orthogonal techniques allow for non-best , which typically yields smaller BDDs l strengthen with subset of variables l l also reduces small model theorem bound by 1 only strengthen “guarded commands” that depend on abstracted state in the guards, or even fewer 19

Roadmap l General Theory l Symmetric Parameterized Protocols l Case Studies/Final Thoughts 20

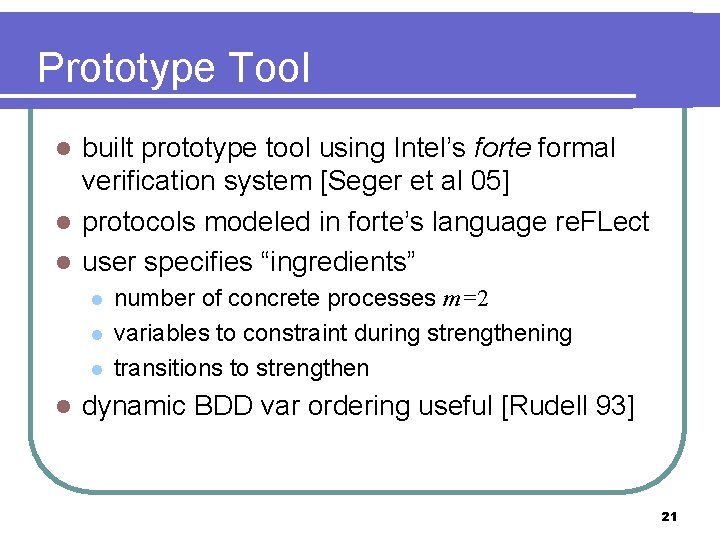
Prototype Tool built prototype tool using Intel’s forte formal verification system [Seger et al 05] l protocols modeled in forte’s language re. FLect l user specifies “ingredients” l l l number of concrete processes m=2 variables to constraint during strengthening transitions to strengthen dynamic BDD var ordering useful [Rudell 93] 21
![Case Studies 13 l GERMAN German 00 l l hello world for parameterized verification Case Studies (1/3) l GERMAN [German 00] l l “hello world” for parameterized verification](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-22.jpg)
Case Studies (1/3) l GERMAN [German 00] l l “hello world” for parameterized verification just one Pid var; no Pid vars control & data properties verified totally automatically with “best” GERMAN 2004 l l more complex than GERMAN has Pid vars (network) previously verified by [Lv et al 07], who needed human to add history vars we verified the control property with non-best 22
![Case Studies 23 l FLASH Kuskin et al 94 l l l if a Case Studies (2/3) l FLASH [Kuskin et al 94] l l l “…if [a](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-23.jpg)
Case Studies (2/3) l FLASH [Kuskin et al 94] l l l “…if [a parameterized verification method] works on FLASH, then there is a good chance that it will also work on many real-world cache coherence protocols. ” [Chou et al 04] first automatically verified by [Lv et al 07] we verified the control property using non-best 23

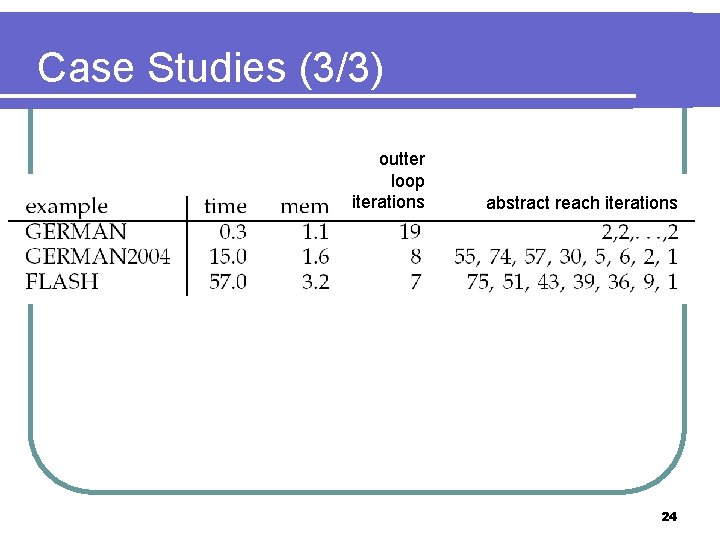
Case Studies (3/3) outter loop iterations abstract reach iterations 24

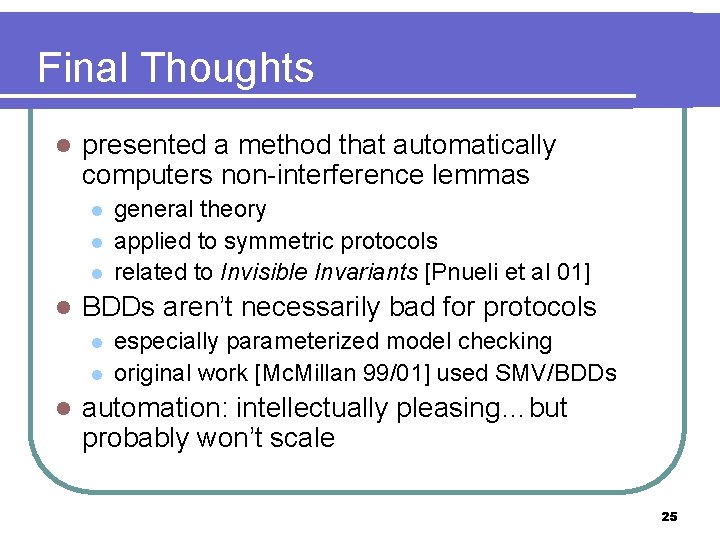
Final Thoughts l presented a method that automatically computers non-interference lemmas l l BDDs aren’t necessarily bad for protocols l l l general theory applied to symmetric protocols related to Invisible Invariants [Pnueli et al 01] especially parameterized model checking original work [Mc. Millan 99/01] used SMV/BDDs automation: intellectually pleasing…but probably won’t scale 25

Foil graveyard… 26

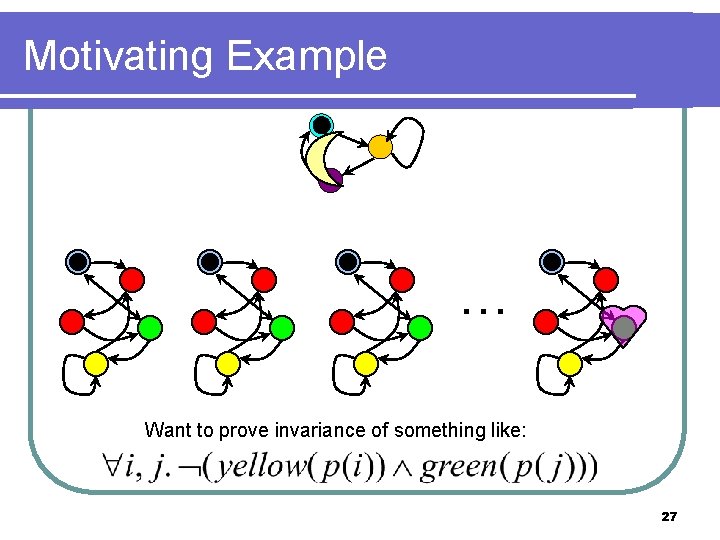
Motivating Example … Want to prove invariance of something like: 27

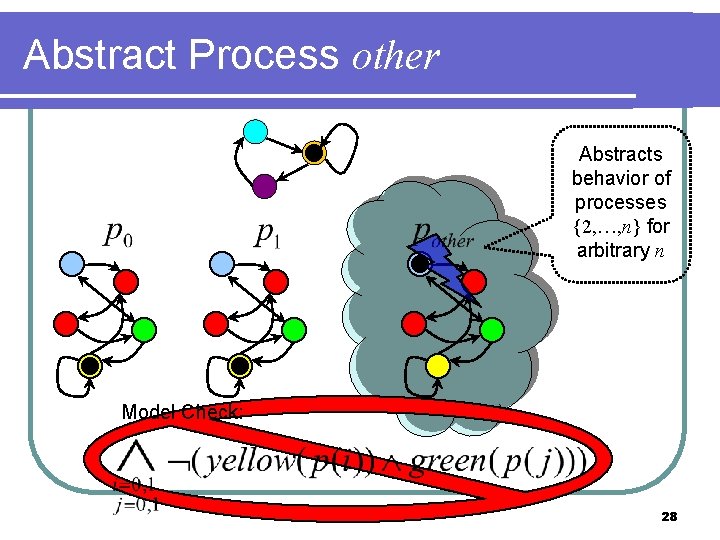
Abstract Process other Abstracts behavior of processes {2, …, n} for arbitrary n Model Check: 28

Counterexample Analysis Umm, me no think possible in real system Human writes “non-interference lemma”: 29

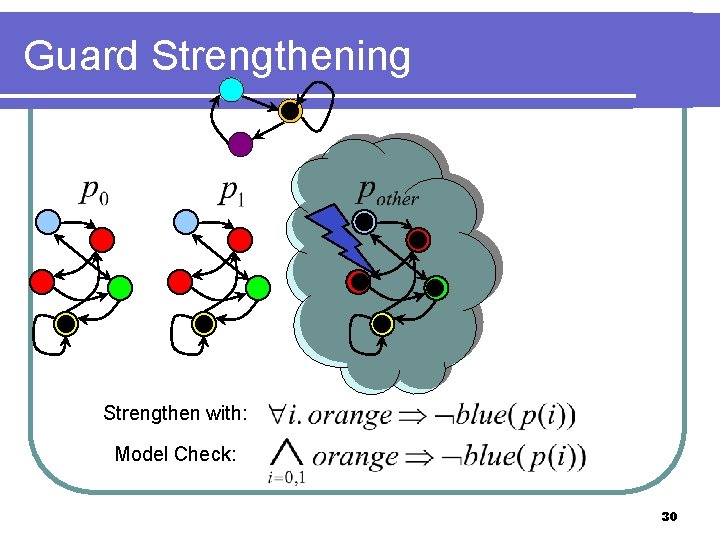
Guard Strengthening Strengthen with: Model Check: 30

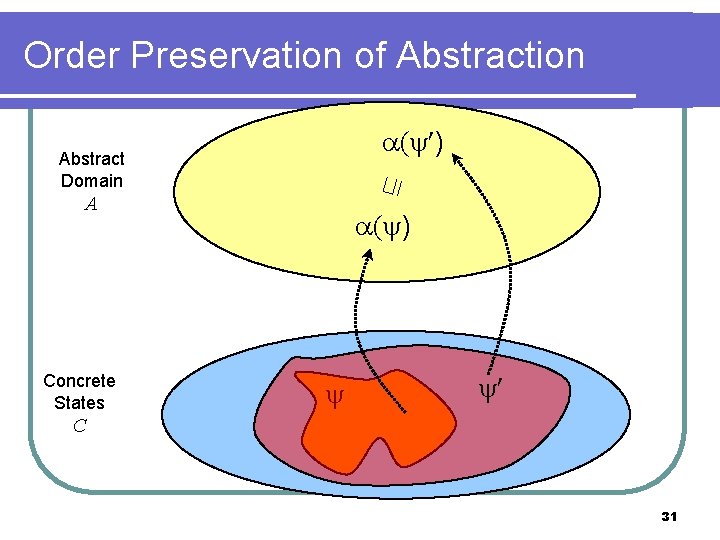
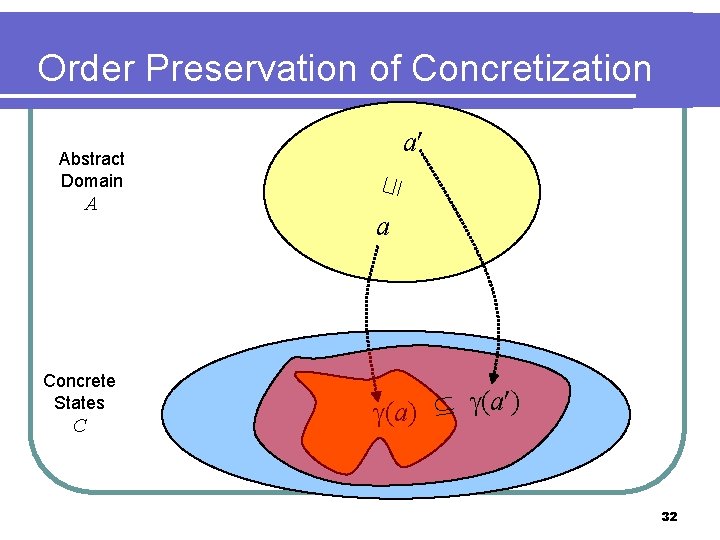
Order Preservation of Abstraction ( ) ⊑ Abstract Domain A Concrete States ( ) C 31

Order Preservation of Concretization A Concrete States C ⊑ Abstract Domain a a (a) (a ) 32

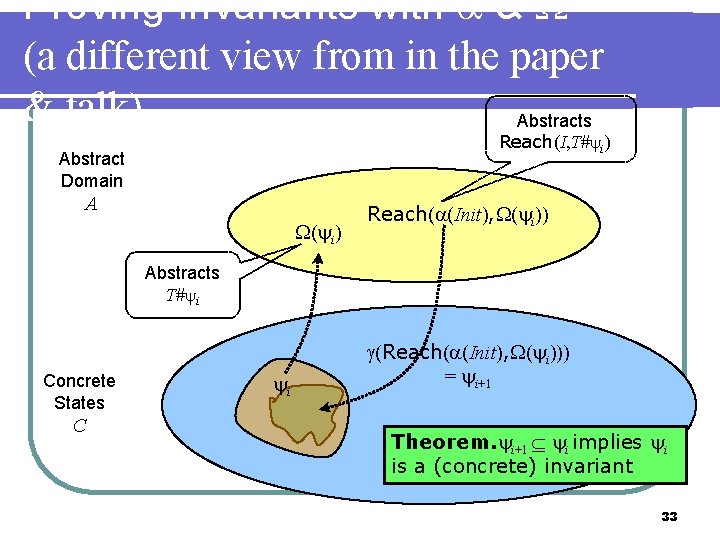
Proving Invariants with & (a different view from in the paper & talk) Abstracts Reach(I, T# i) Abstract Domain A ( i) Reach( (Init), ( i)) Abstracts T# i Concrete States C i (Reach( (Init), ( i))) = i+1 Theorem. i+1 i implies i is a (concrete) invariant 33

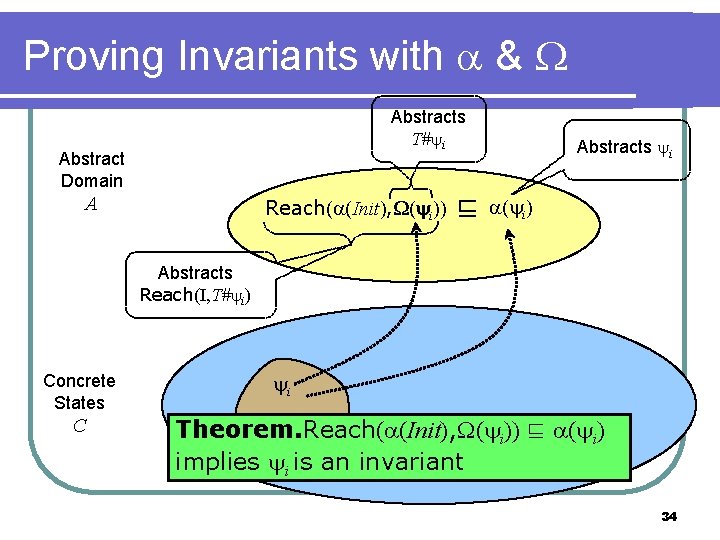
Proving Invariants with & Abstracts T# i Abstract Domain A Reach( (Init), ( ( i))) ⊑ Abstracts i ( i) Abstracts Reach(I, T# i) Concrete States C i Theorem. Reach( (Init), ( i)) ⊑ ( i) implies i is an invariant 34

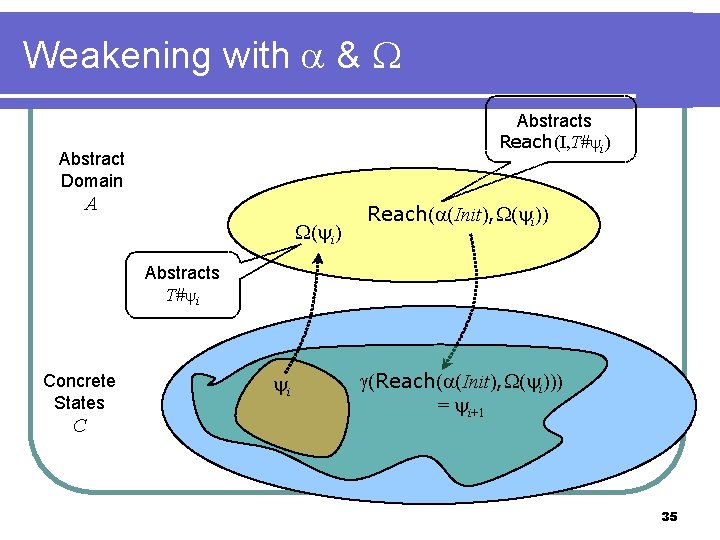
Weakening with & Abstracts Reach(I, T# i) Abstract Domain A ( i) Reach( (Init), ( i)) Abstracts T# i Concrete States C i (Reach( (Init), ( i))) = i+1 35

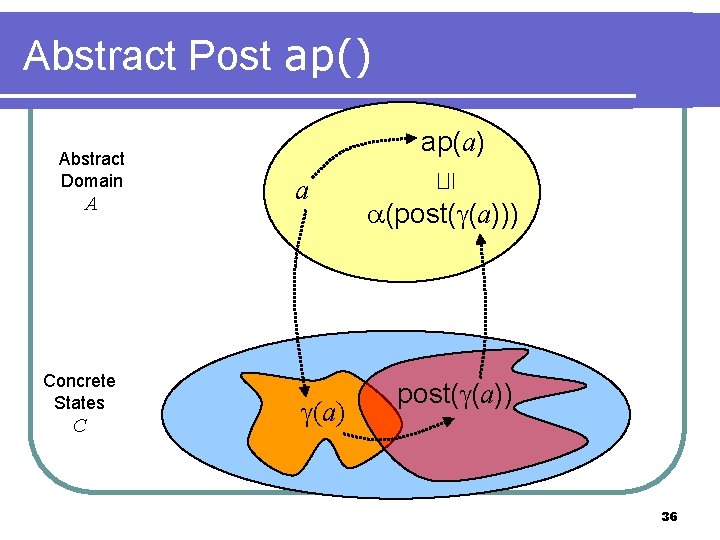
Abstract Post ap() A Concrete States C a (a) ⊑ Abstract Domain ap(a) (post( (a))) post( (a)) 36

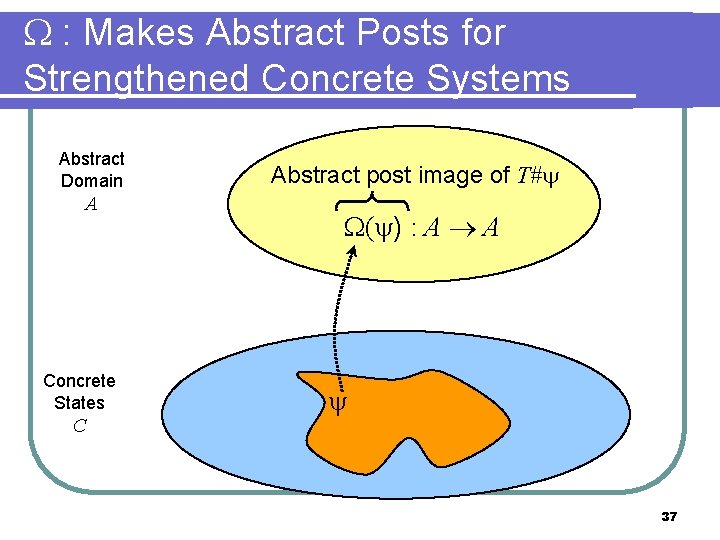
: Makes Abstract Posts for Strengthened Concrete Systems Abstract Domain A Concrete States C Abstract post image of T# ( ) : A A 37

The Method (1/3) Abstracts T# i Abstract Domain Reach( (Init), ( ( i))) A ⊑ | ( i) Abstracts Reach(I, T# i) Concrete States C i (Reach( (Init), ( i))) = i+1 38

The Method start with 0 = False; iteratively compute 1, 2, 3, … until a provable invariant is found l this is the strongest provable invariant l l l provable is relative to and if we use that is “best” then is the strongest invariant provable using 39

Protocol Abstraction abstract domain is symmetric sets of views l galois connection is conceptually straightforward; similar to [Lahiri & Bryant 04] l l l ( ) = {View (s) | s and is a view map} thanks to a small model theorem & symmetry, we can compute a best … 40

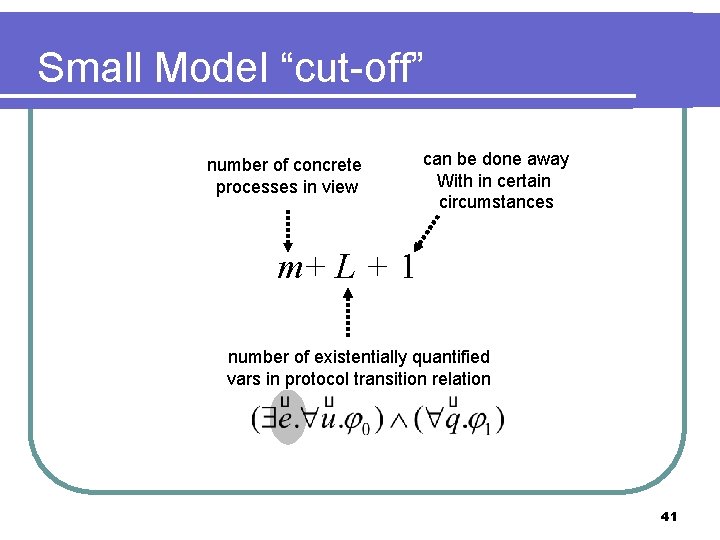
Small Model “cut-off” number of concrete processes in view can be done away With in certain circumstances m+ L + 1 number of existentially quantified vars in protocol transition relation 41
![Views abstract domain is sets of views Chou et al 04 which are assignments Views abstract domain is sets of views [Chou et al 04], which are assignments](https://slidetodoc.com/presentation_image/6cb191584d038d34a7615a35b3b674cf/image-42.jpg)
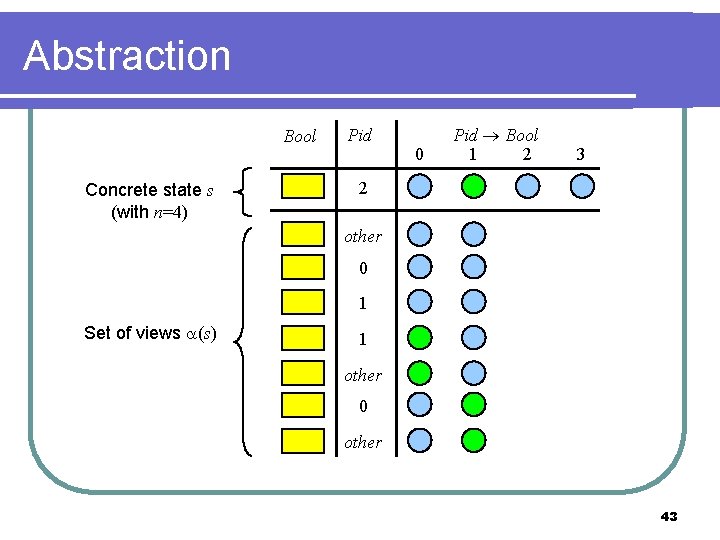
Views abstract domain is sets of views [Chou et al 04], which are assignments to protocol vars with different typing m a small constant (typically 2) Pidm = {0, …, m-1} Pidother = Pidm {other} type in protocol Bool type in view Bool Pid Pidm Bool Pidmother Pid Pidmother 42

Abstraction Bool Concrete state s (with n=4) Pid 0 Pid Bool 1 2 3 2 other 0 1 Set of views (s) 1 other 0 other 43

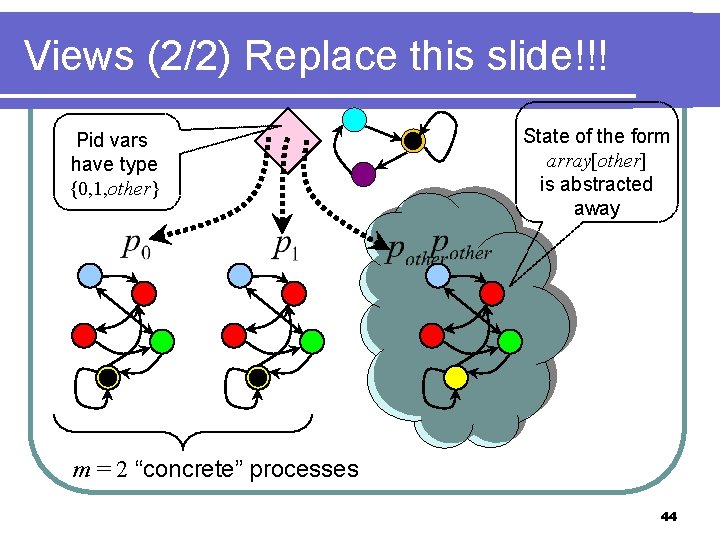
Views (2/2) Replace this slide!!! Pid vars have type {0, 1, other} State of the form array[other] is abstracted away m = 2 “concrete” processes 44

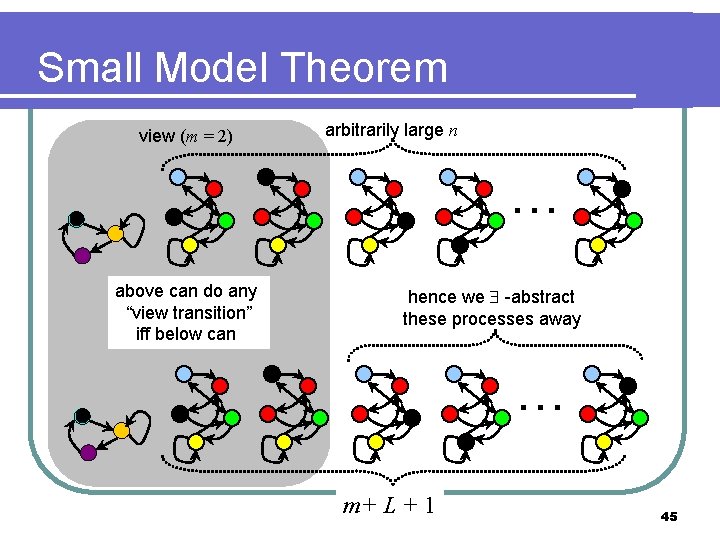
Small Model Theorem view (m = 2) arbitrarily large n … above can do any “view transition” iff below can hence we -abstract these processes away … m+ L + 1 45

TODO… 46