Automated Web Patrol with Strider Honey Monkeys Y

Automated Web Patrol with Strider Honey Monkeys Y. Wang, D. Beck, S. Chen, S. King, X. Jiang, R. Roussev, C. Verbowski Microsoft Research, Redmond Justin Miller February 27, 2007

Outline l l l Internet Attacks Web Browser Vulnerabilities Honey. Monkey System Experiments Analysis/Future Work 2

Internet Attacks l l Exploit vulnerability of user web browser Install malicious code on machine l l No user interaction required later VM-based honeypots are used to detect these attacks 3

Honey. Monkeys l l OS’s of various patch levels Mimic human web browsing l l Uses Strider. Tracer to catch unauthorized file creation and system configuration changes Discover malicious web sites 4

Honey. Monkeys OS 3 OS 2 OS 1 Malcode 5

Browser vulnerabilities l Code Obfuscation l l Dynamic code injection using document. write() Unreadable, long strings with encoded chars l l l “%28” or “h” Decoded by function script or browser Escapes anti-virus software 6

Browser vulnerabilities l URL Redirection l l l Protocol redirection using HTTP 302 temp redir HTML tags inside <frameset> Script functions l l window. location. replace() or window. open() Redirection is common in non-malicious sites 7

Browser vulnerabilities l Malware Installation l l l l Viruses Backdoor functions Bot programs Trojan downloaders – DL other programs Trojan droppers – delete (drop) files Trojan proxies – redirect network traffic Spyware programs 8

Honey. Monkey System l l Attempts to automatically detect and analyze web sites that exploit web browsers 3 -stage pipeline of virtual machines l l l Stage 1: scalable mode Stage 2: recursive redirection analysis Stage 3: scan fully patched VM’s 9

Honey. Monkey: Stage 1 l l Visit N URLs simultaneously If exploit detected, re-visit each one individually until exploit URL is found VM U 1 U 2 U 4 U 5 VM U 3 U 6 U 2 U 3 10

Honey. Monkey: Stage 2 l l Re-scan exploit URLs Perform recursive redirection analysis l Identify all web pages involved VM U 2 U 3 U 9 U 10 11

Honey. Monkey: Stage 3 l l Re-scan exploit URLs Scan using fully patched VMs l Identify attacks exploiting the latest vulnerabilities VM U 2 U 3 U 9 U 10 VM U 2 U 9 12
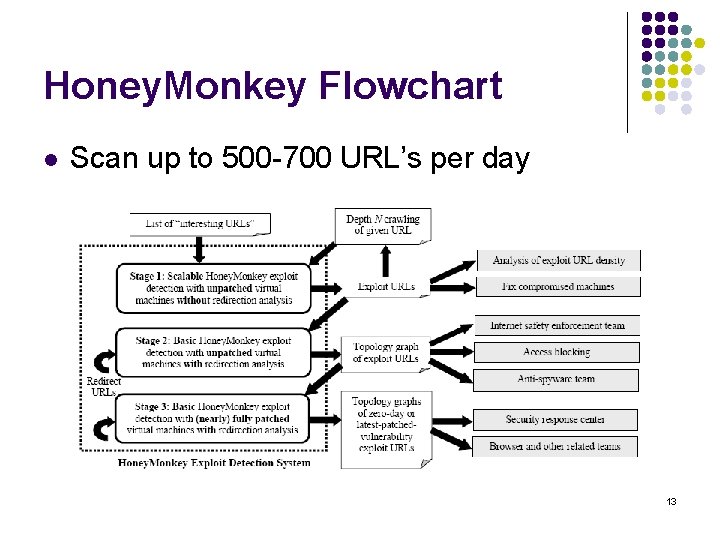
Honey. Monkey Flowchart l Scan up to 500 -700 URL’s per day 13

Web Site Visits l l Monkey program launches URL Wait 2 minutes l l Detect persistent-state changes l l Allow all malicious code to DL New registry entries and. exe files Allows uniform detection of: l l Known vulnerability attack Zero-day exploits 14

Honey. Monkey Report l Generates XML report at end of each visit l l l . exe files created or modified Processes created Registry entries created or modified Vulnerability exploited Redirect-URLs visited Cleanup infected state machine l Monkey Controller 15

Web Site Redirection URL 1 URL 2 Redirect Data collected URL 3 Redirect data 16
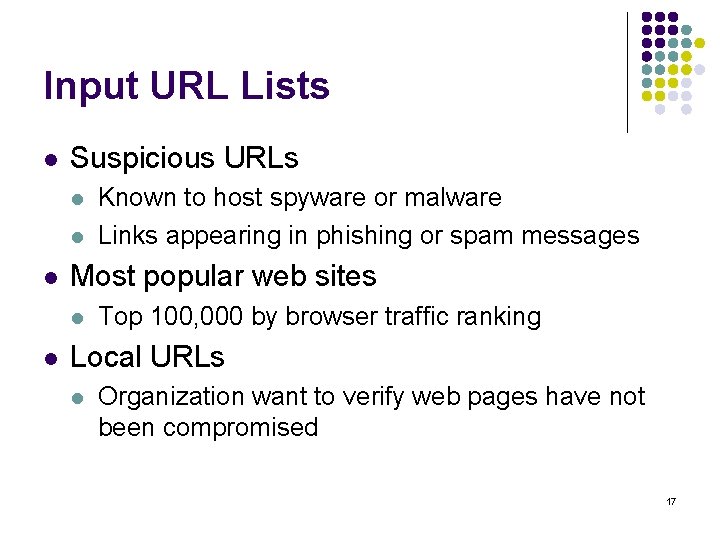
Input URL Lists l Suspicious URLs l l l Most popular web sites l l Known to host spyware or malware Links appearing in phishing or spam messages Top 100, 000 by browser traffic ranking Local URLs l Organization want to verify web pages have not been compromised 17

Output URL Data l Exploit URLs l l Topology Graphs l l l Measures risk of visiting similar web sites Several URLs shut down Provide leads for anti-spyware research Zero-day exploits l Monitors URL “upgrades” 18

Experimental Results l Collected 16, 000+ URLs l l Web search of “known-bad” web sites Web search for Windows “hosts” files Depth-2 crawling of previous URLs 207/16, 190 = 1. 28% of web sites 19

Experimental Results l All tests done using IEv 6 20
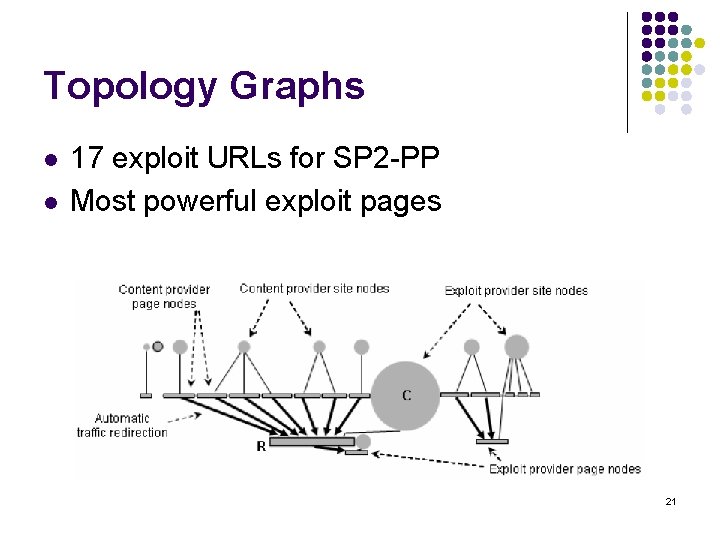
Topology Graphs l l 17 exploit URLs for SP 2 -PP Most powerful exploit pages 21

Site Ranking l l Key role in anti-exploit process Determines how to allocate resources l l Monitoring URLs Investigation of URLs Blocking URLs Legal actions against host sites 22
Site Ranking l l 2 types of site ranking, based on: Connection counts l l Links URLs to other malicious URLs Number of hosted exploit-URLs l l Web sites with important internal page hierarchy Includes transient URLs with random strings 23
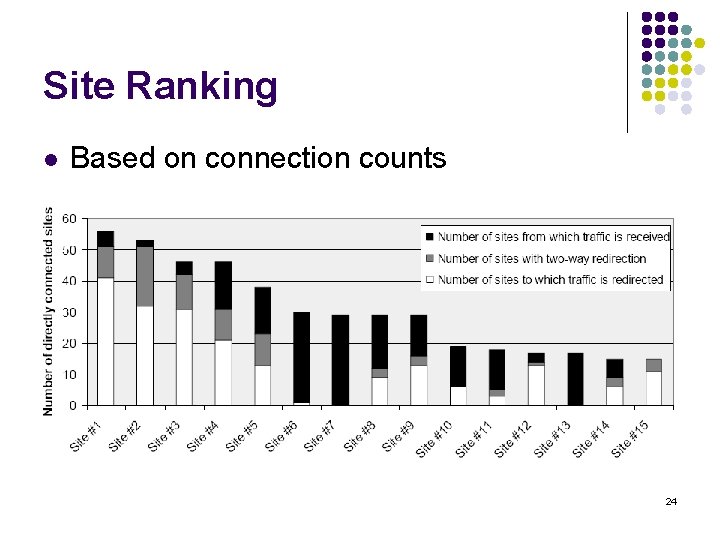
Site Ranking l Based on connection counts 24
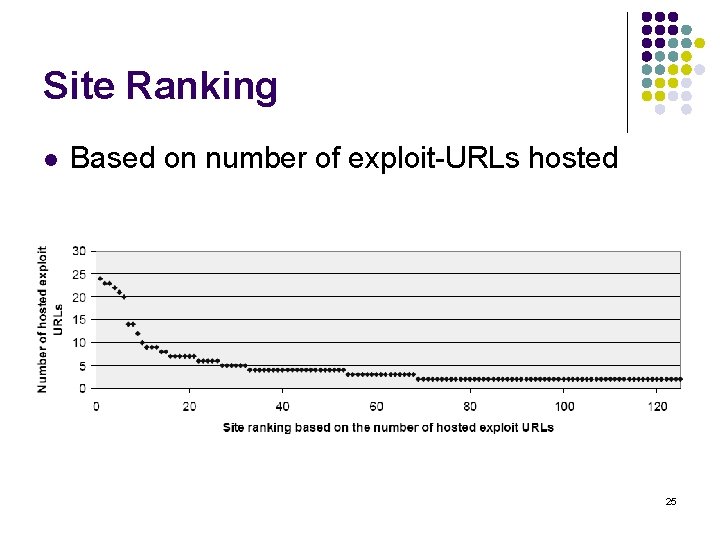
Site Ranking l Based on number of exploit-URLs hosted 25

Effective Monitoring l Easy-to-find exploit URLs l l Content providers with well-known URLs l l Useful for detecting zero day exploits Must maintain these URLs to keep high traffic Highly ranked URLs l More likely to upgrade exploits 26

Scanning Popular URLs 27

Honey. Monkey Evasion l Target IP addresses l l Determine if a human is present l l l Blacklist IP addresses of Honey. Monkey machines Create cookie to suppress future visits One-time dialog pop up box disables cookie Detect VM or Honey. Monkey code l l Test for fully virtualizable machine Becomes less effective as VMs increase 28
Bad Web Site Rankings l l l Celebrity info Song lyrics Wallpapers Video game cheats Wrestling 29

Related Work l Email quarantine l l Shadow honeypots l l l Intercepts every incoming message Diverts suspicious traffic to a shadow version Detects potential attacks, filters out false positives Honeyclient l Tries to identify browser-based attacks 30

Strengths l Honey. Monkey will detect most l l Uniform detection of exploits l l l Trojan viruses Backdoor functions Spyware programs Known vulnerability attack Zero-day exploits Generates XML report for each visit 31
Weaknesses l l Takes time to clean infected machine after each web site visit Code obfuscation escapes anti-virus software Only detects persistent-state changes Honey. Monkey only waits 2 minutes per URL l Delay exploit on web pages 32

Improvements l Run Honey. Monkey with random wait times l l l Combat delayed exploits on web sites Randomize Honey. Monkey attack Vulnerability-specific exploit detector (VSED) l l Insert break points within bad code Stops execution before potentially malicious code 33

- Slides: 34