Authentication and Authorization Authentication is the process of











- Slides: 21

Authentication and Authorization • Authentication is the process of verifying a principal’s identity (but how to define “identity”? ) – Who the person is – Or, what the person is • Authorization is the process of determining whether a principal can perform certain actions – What the person can do – Typically based on authentication result 1

Authentication in Cyber Space • Authentication based on what you know. – If you know a secret, then you are linked to an “identity” – The secret needs to be associated with the identity beforehand (authentication state) • Authentication protocol is the process of proving that one knows the secret, a. k. a “credential. ” 2

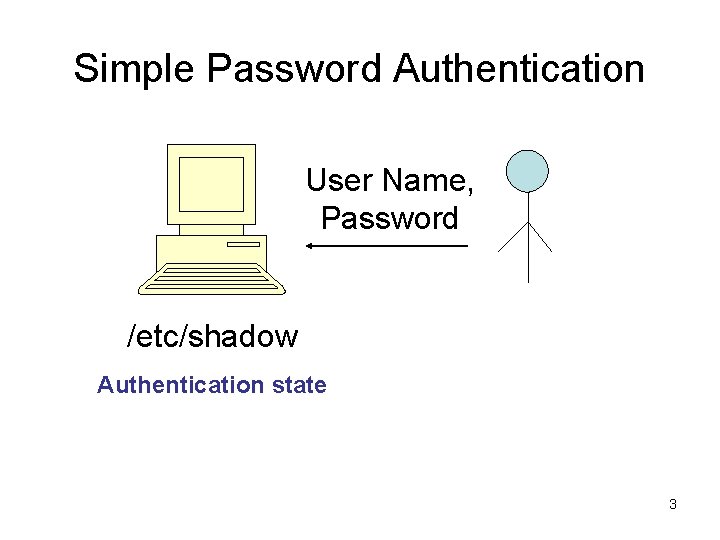
Simple Password Authentication User Name, Password /etc/shadow Authentication state 3

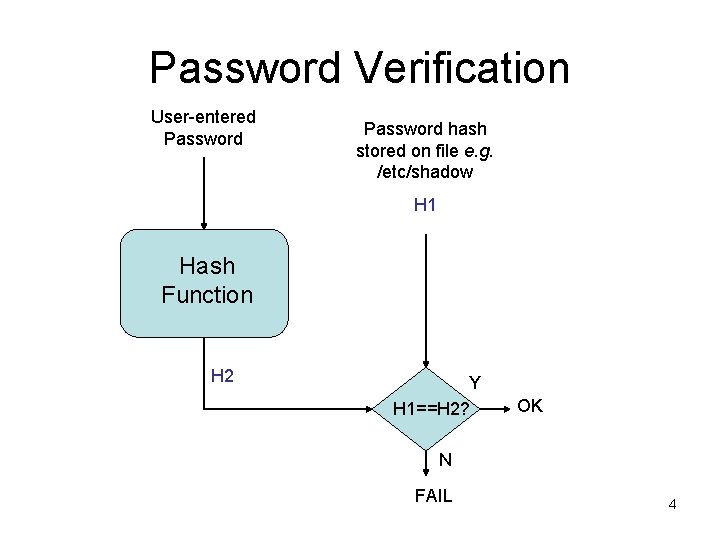
Password Verification User-entered Password hash stored on file e. g. /etc/shadow H 1 Hash Function H 2 Y H 1==H 2? OK N FAIL 4

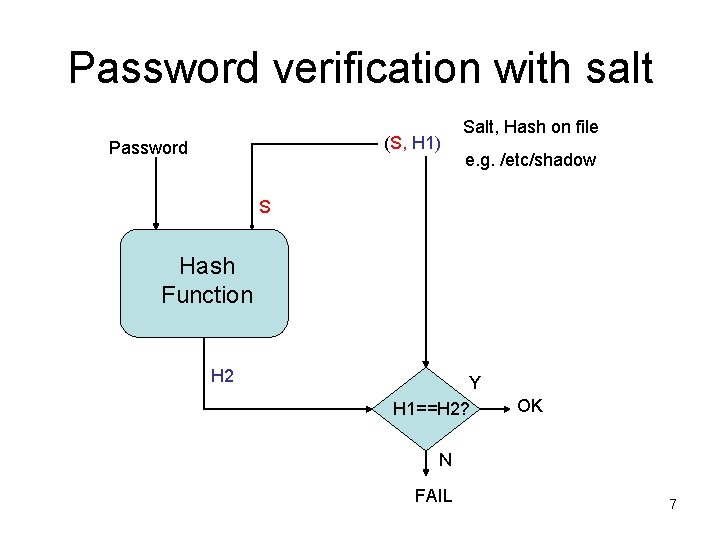
Hash function and salt • A “salt” is used to increase the input space of a hash function – Even though a cryptographic function H is hard to invert, if the number of possible inputs to H is small, a brute-force search can easily find the pre-image from a given hash – If we append the input string with a salt and apply H on the whole string, then the number of possible inputs to the hash function is increased S fold where S is the number of all possible salts. – For password hash, the salt is used to mitigate dictionary attack 5

What is a dictionary attack? • Pre-compute the hash of commonly used passwords • Looking up a password from the hash takes only constant time if the password falls into the dictionary 6

Password verification with salt (S, H 1) Password Salt, Hash on file e. g. /etc/shadow S Hash Function H 2 Y H 1==H 2? OK N FAIL 7

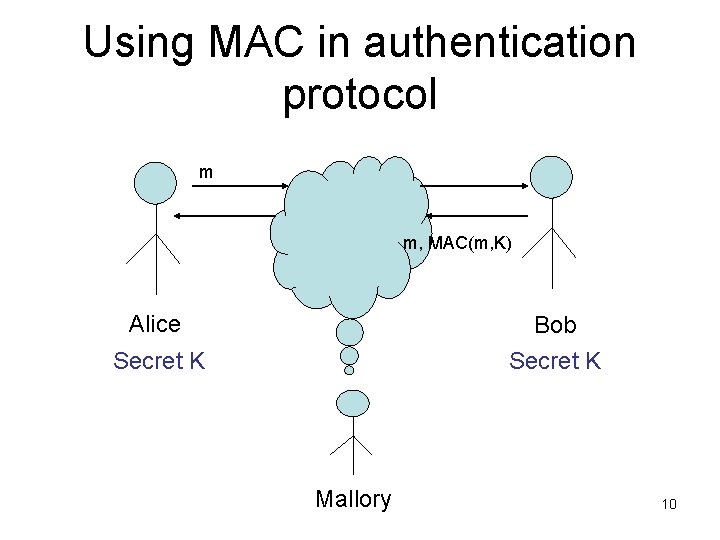
Challenge-Response Protocol • Objective: Bob (prover) convinces Alice (verifier) that he knows the secret, while not leaking the secret to anyone (including Alice) • Threat model: insecure communication channel – Cryptographic primitives unbreakable – Attacker can do anything else: • • • Intercept messages Replace messages Inject messages Re-order messages Encrypt/decrypt a message if he knows the keys 8

Challenge-Response Protocol • General process – Verifier picks a challenge message and send it to prover. – Prover produces a response using the secret and sends the response back to the verifier – Verifier checks whether the response is valid • Requirements – Protect Verifier: if Bob does not know the secret, the protocol shall fail – Protect Prover: the secret shall not be revealed in the process, not even to the verifier (computationally infeasible to infer) 9

Using MAC in authentication protocol m m, MAC(m, K) Alice Bob Secret K Mallory 10

Authentication based on symmetric encryption Alice Bob Secret key K Mallory 11

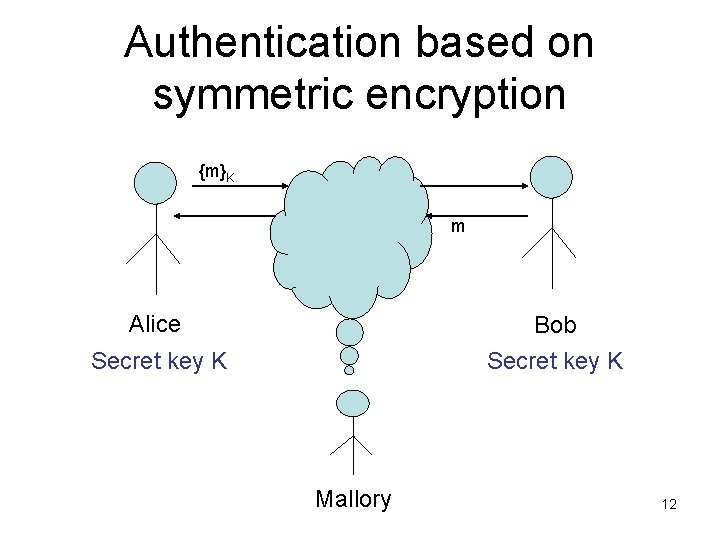
Authentication based on symmetric encryption {m}K m Alice Bob Secret key K Mallory 12

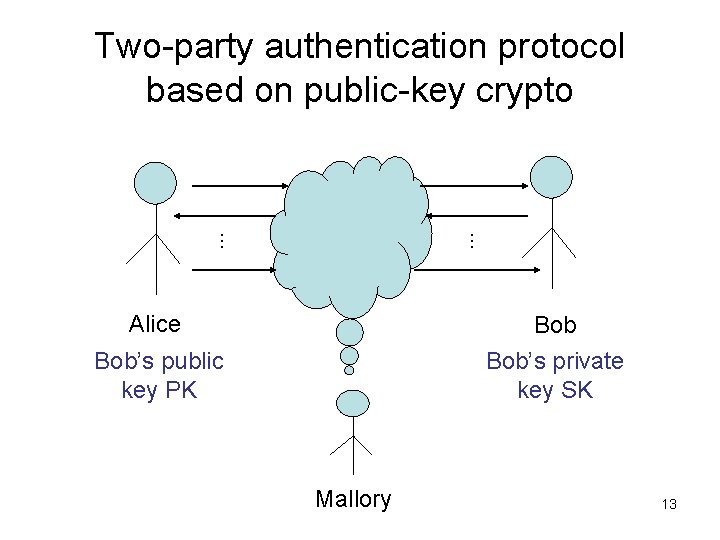
Two-party authentication protocol based on public-key crypto … … Alice Bob’s private key SK Bob’s public key PK Mallory 13

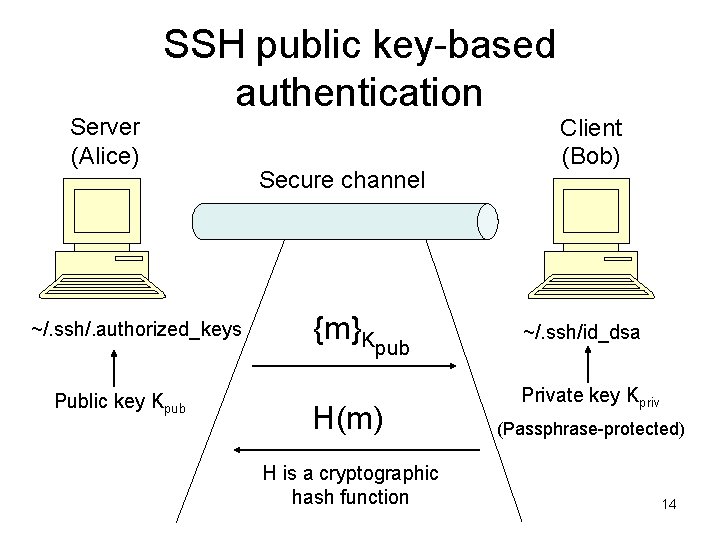
Server (Alice) SSH public key-based authentication ~/. ssh/. authorized_keys Public key Kpub Secure channel {m}Kpub H(m) H is a cryptographic hash function Client (Bob) ~/. ssh/id_dsa Private key Kpriv (Passphrase-protected) 14

SSH Public Key-based Authentication • What is a secure channel? – Messages sent are encrypted by a shared secret key – Messages are authenticated using MAC – The SSH public key-based authentication is used by the server to authenticate the user at the other end of the secure channel – SSH also supports other kinds of authentication, such as password authentication, which needs a secure channel. • This challenge-response protocol is better than asking the client to sign a challenge message – Server gains zero knowledge – The hash function is to protect the private key from a chosen-ciphertext attack 15

SSH Agent • The private key must be protected by a passphrase. – The passphrase is used to generate a key to encrypt the private key stored in the file system. • An SSH agent can load the private key into memory and perform the challengeresponse protocol on behalf of the user. 16

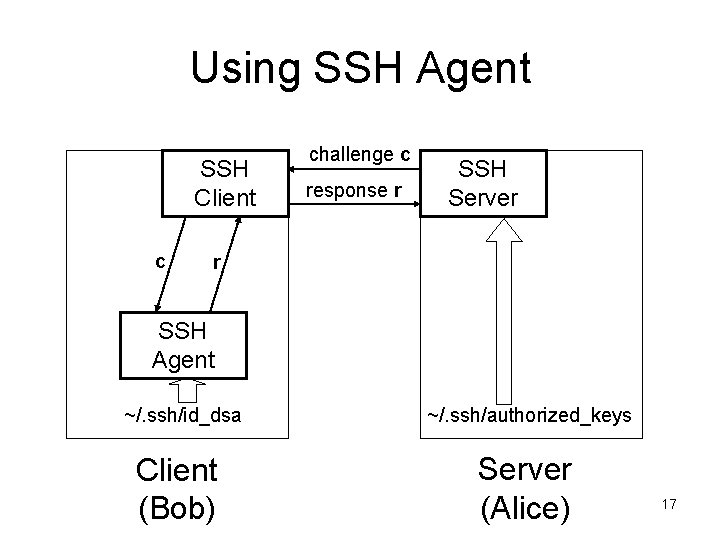
Using SSH Agent SSH Client c challenge c response r SSH Server r SSH Agent ~/. ssh/id_dsa Client (Bob) ~/. ssh/authorized_keys Server (Alice) 17

Using SSH Agent • SSH agent stores private keys in memory and performs crypto calculation – User only needs to enter passphrase when the agent retrieves the private key • Communication between SSH client and agent mediated through file-system protection – An SSH client can only connect to an agent started by the same user, except for user root, who can connect to any user’s agent • Advantage: user does not need to type in passphrase to decrypt the private key every time he wants to log in. 18

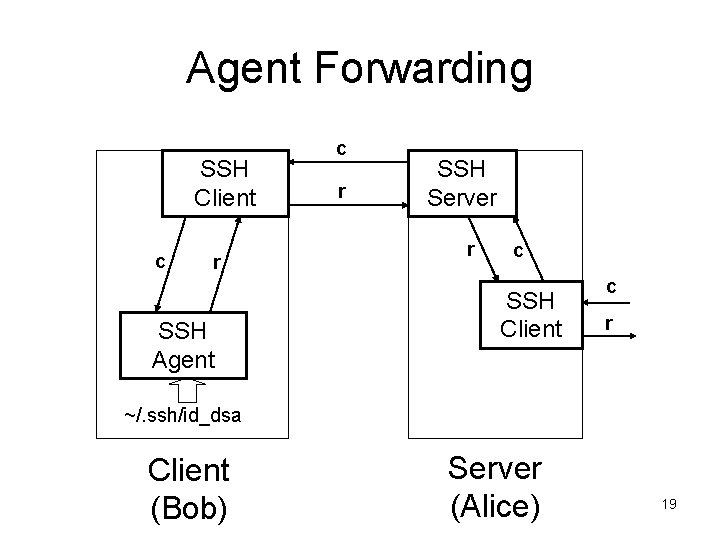
Agent Forwarding SSH Client c r SSH Agent c r SSH Server r c SSH Client c r ~/. ssh/id_dsa Client (Bob) Server (Alice) 19

Agent Forwarding • Alice can contact the SSH agent on Bob through the SSH channel if Bob allows his agent connection to be forwarded to Alice – SSH client on Alice becomes “man in the middle” – Useful when the user on Bob wants to login to other machines from Alice – root user can always connect to forwarded agents – Bob’s private key never leaves his machine; when Bob tears down the connection with Alice, root on Alice will no longer be able to impersonate Bob 20

Exercise after class • Set up public key-based authentication using SSH agent for logging into departmental Linux machines (e. g. , grad. csee. usf. edu). – Generate your public/private key pair – Upload your public key to the server – Figure out how to use SSH agent – Find a clever way to start/connect to your SSH agent 21