Auth for Encrypted Services with Server Side APT















- Slides: 22

Auth for Encrypted Services with Server Side APT Steve “Sc 00 bz” Thomas

Who is This Talk For?

Where are the Keys? • “Brain wallet” • “Key file” • “Key service”

Pre-Authentication • Run the PW-KDF once • Generate two keys – Authentication key – Encryption key • Caveat – PBKDF 2

Crypho (Fixed) • Send 6 digit 2 FA • Receive password encrypted private key

Proton. Mail • Two passwords – Authentication sent to the server as is – Decrypt PGP key • Most users will use the same password

Mega • KDF is “Do stupid shit with AES 65536 times” • Auth key is encrypt email 16384 times with password key

Nigori (Google Sync)

Crypton

PAKE • Password Authenticated Key Exchange – Diffie-Hellman – Eve and Mallory proof

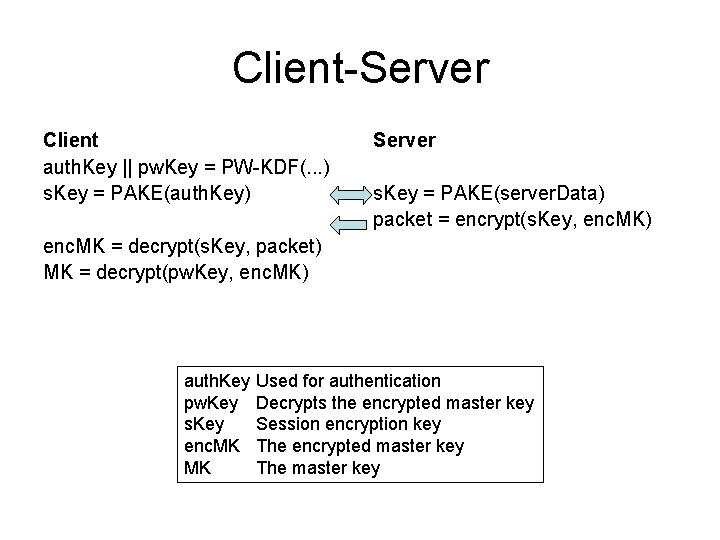
Client-Server Client auth. Key || pw. Key = PW-KDF(. . . ) s. Key = PAKE(auth. Key) Server s. Key = PAKE(server. Data) packet = encrypt(s. Key, enc. MK) enc. MK = decrypt(s. Key, packet) MK = decrypt(pw. Key, enc. MK) auth. Key pw. Key s. Key enc. MK MK Used for authentication Decrypts the encrypted master key Session encryption key The encrypted master key The master key

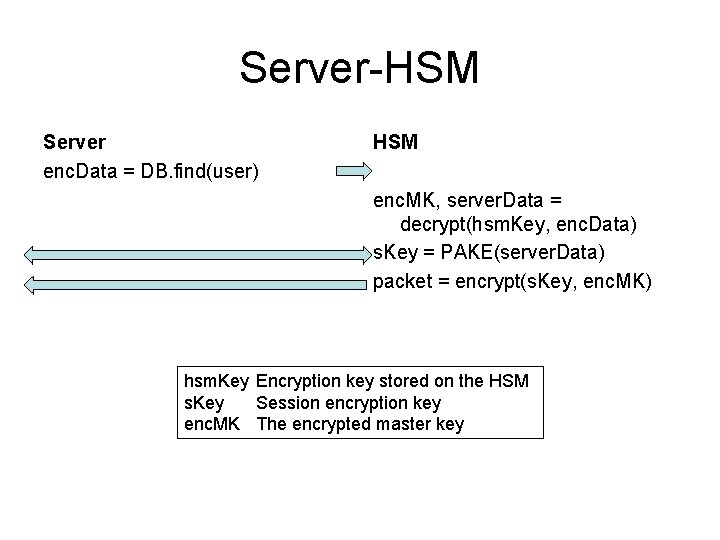
Server-HSM Server enc. Data = DB. find(user) HSM enc. MK, server. Data = decrypt(hsm. Key, enc. Data) s. Key = PAKE(server. Data) packet = encrypt(s. Key, enc. MK) hsm. Key Encryption key stored on the HSM s. Key Session encryption key enc. MK The encrypted master key

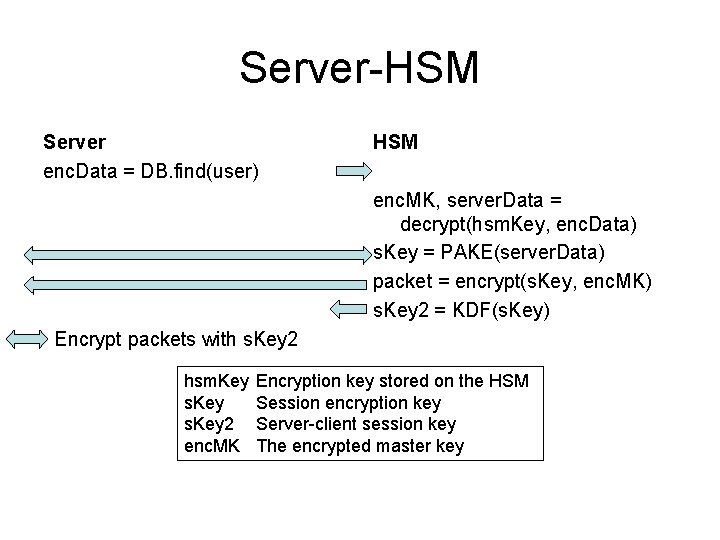
Server-HSM Server HSM enc. Data = DB. find(user) enc. MK, server. Data = decrypt(hsm. Key, enc. Data) s. Key = PAKE(server. Data) packet = encrypt(s. Key, enc. MK) s. Key 2 = KDF(s. Key) Encrypt packets with s. Key 2 hsm. Key s. Key 2 enc. MK Encryption key stored on the HSM Session encryption key Server-client session key The encrypted master key

Change Password fall 2014 winter 14 spring 15 summer 15

New User

I Can Has 2 FA?

I Can Has 2 FA • Time based • Challenge response • No counters

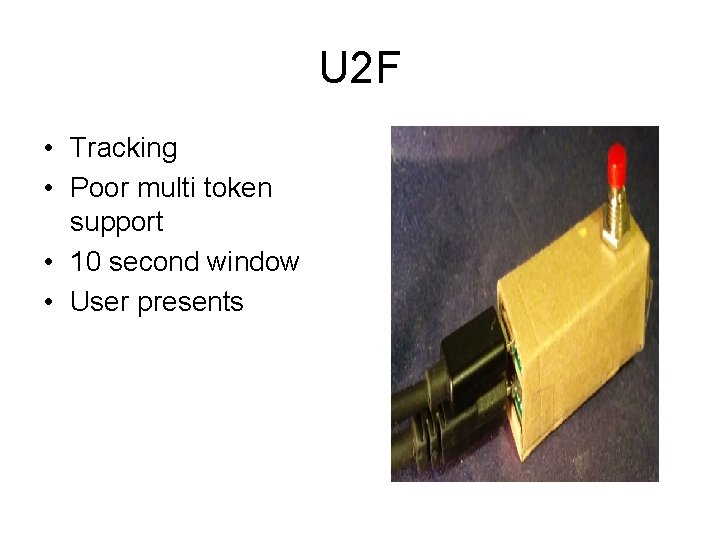
U 2 F • Tracking • Poor multi token support • 10 second window • User presents

U 2 F • BUT it’s the best we got

Teensy. Gap

Teensy. Gap-ed Raspberry Pi

Questions? • Twitter: @Sc 00 bz. T • Git. Hub: Sc 00 bz • Site: tobtu. com