Auditing Networks Perimeters and Systems TimeBased Security and

Auditing Networks, Perimeters and Systems Time-Based Security and STAR Copyright 2001 Marchany 1

Unit 2: TBS & Star – Theory and Practice TBS – Time Based Security STAR – Security Targetting and Analysis of Risk Copyright 2001 Marchany 2

How the day is going to go ¨ Morning – Principles and Theory – Audit Process and Goals – Time Based Security – Putting it all together ¨ Afternoon – Audit in the Real World – Using CIS Rulers to build audit plans – Applying the process to systems – Putting it all together Copyright 2001 Marchany 3

The Course Goals ¨ Construct a Security Checklist for your site. – Unix – NT ¨ Use this methodology to develop a response to your internal auditors. ¨ Have a repeatable method of defining the $$$ cost of implementing security features at your site. – This method can be used over time to show trends ¨ Develop a set of reports/matrices that can be used to quickly identify the security status of a host at your site. Copyright 2001 Marchany 4

The General Audit Process ¨ Audit Planning – Review pertinent background info, research policies, prepare the audit program ¨ Entrance Conference – Meet w/IS group leaders to let them know what is going on and find out if there any specific areas to check. ¨ Fieldwork – Visiting the IS systems and performing the steps listed in the audit program on a sample of systems. Copyright 2001 Marchany 5

The General Audit Process ¨ Preparing the Audit Report – The report should: • • State what was done State the results of these actions Present recommendations Include in the appendices the audit checklists used to collect the data. ¨ The Exit Conference – Meet with the people from step 2 and review the results w/them. This is the time to clear up any misunderstandings. Refine the audit report and prepare the recommendations paper. ¨ Report to Upper Management (CEO, CFO, CIO, VP) – Present a summary report of the audit. Provide recommendation and implementation cost estimates. Copyright 2001 Marchany 6

The Auditor’s Goals ¨ Ensure Assets are protected according to company, local, state and federal regulatory policies. ¨ Determine what needs to be done to ensure the protection of the above assets. ¨ Make life miserable for sysadmins…: -) – Not really. They can save a sysadmin if a problem occurs. Copyright 2001 Marchany 7

The Sysadmin’s Goals ¨ Keep the systems up. ¨ Keep users happy and out of our hair. ¨ Keep auditors at arms’ length. ¨ Get more resources to do the job properly. ¨ Wear jeans or shorts to work when everyone else has to wear suits……. Copyright 2001 Marchany 8

The Sysadmin’s Audit Strategy ¨ Turn a perceived weakness (the audit) into a strength (security checklists). ¨ Develop a set of reporting matrices that can be used as audit reports or justification for security expenditures. ¨ The above info can be used to help develop your incident response plan. Copyright 2001 Marchany 9

Time Base Security ¨ The Time Based Security Model provides: • A methodology that a security officer can use to quantifiably test and measure the effectiveness of security measures. • A set of matrices/reports that can be used by security professionals to assign a $ value to the cost. This figure can be given to mgt. to help them prioritize their security expenditures. • Winn Schwartau’s book describes TBS. The following slides discuss his methodology. Copyright 2001 Marchany 10
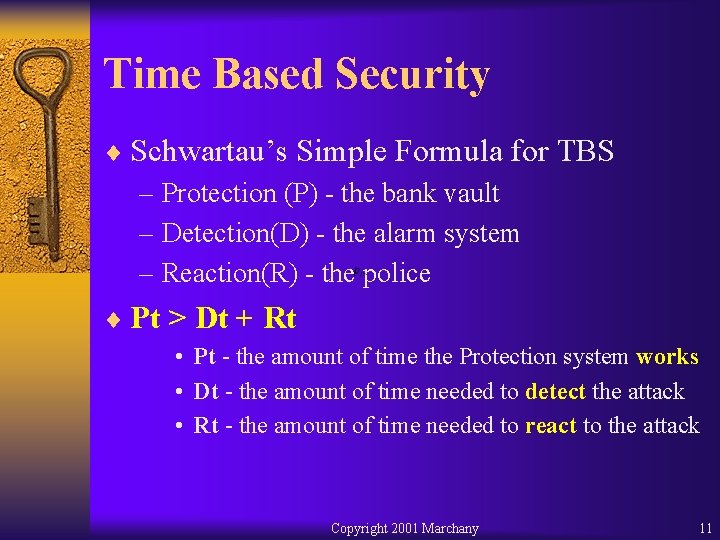
Time Based Security ¨ Schwartau’s Simple Formula for TBS – Protection (P) - the bank vault – Detection(D) - the alarm system – Reaction(R) - the police ¨ Pt > Dt + Rt • Pt - the amount of time the Protection system works • Dt - the amount of time needed to detect the attack • Rt - the amount of time needed to react to the attack Copyright 2001 Marchany 11

Time Based Security ¨ Pt > Dt + Rt (TBS Law) – If the amount of protection time (Pt) you offer is greater than the sum of the detection time (Dt) and reaction time (Rt), then your systems can be considered secure. – If the detection & reaction times are very fast then you don’t need as strong a Protection mechanism. ¨ KEY: detect anomalous activity and respond ASAP! Copyright 2001 Marchany 12

Time Based Security ¨ TBS Corollary –P<D+R ¨ If it takes longer to detect and respond to an intrusion than the amount of protection time afforded by the protection device, P, then effective security is impossible. ¨ Look at specs for each of the components in your network architecture. Copyright 2001 Marchany 13

Time Based Security ¨ If Pt = Dt + Rt, then Pt implies an Exposure Time, E. – E=D+R ¨ You want D+R -> 0. As your detection & reaction speeds increase, the need for strong Protection decreases. Hmmm…. . . ¨ Fortress mentality dictates that P must be extremely high because D+R is really slow or non-existent. Copyright 2001 Marchany 14

Measuring Security ¨ Measure D+R (sec/min/hrs/day) ¨ Assume the best: active logging, good AUP (Acceptable Usage Policy), decent IRP (Incident Response Policy) • How long does it take to detect an event? (D=x) • How long to notify affected parties? How long for them to analyze and respond? (R=y) Out of office? Out to lunch? How long to answer page? – How much damage could be done in D+R time? Copyright 2001 Marchany 15
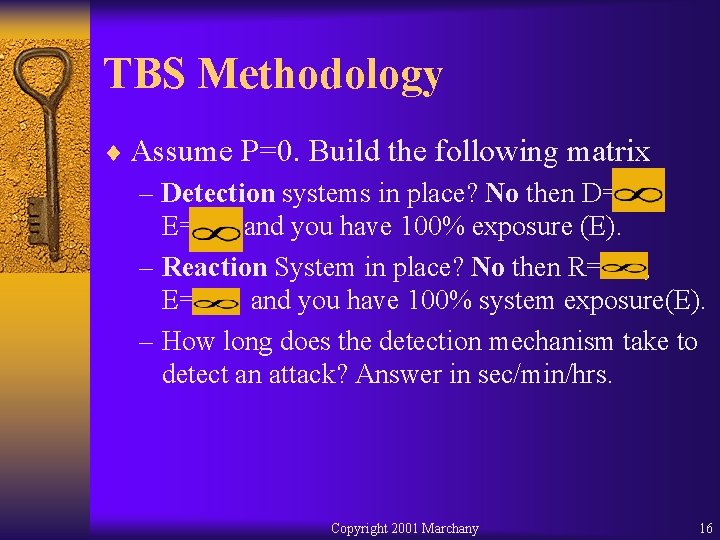
TBS Methodology ¨ Assume P=0. Build the following matrix – Detection systems in place? No then D= , E= and you have 100% exposure (E). – Reaction System in place? No then R= , E= and you have 100% system exposure(E). – How long does the detection mechanism take to detect an attack? Answer in sec/min/hrs. Copyright 2001 Marchany 16

TBS Methodology - Detection – Once an attack is detected, how are you notified? Logs? Pager? Phone? Future audit trails? – How long does the above take? (sec/min/hr/day) • • • Sitting at your desk: _____ When you’re at lunch: _______ Break time: _______ Headed home: _______ Sleeping: _______ At the movies: _______ Copyright 2001 Marchany 17

TBS Methodology - Reaction – Once notified, how long does it take to do something about it? (sec/min/hrs/day) • • • Sitting at your desk: _______ At lunch: _______ On break: _______ Headed home: _______ Sleeping: _______ – How long does it take to determine the cause/effect/solution? Include other folks • Onsite: _____ Offsite: Copyright 2001 Marchany _____ 18

TBS Methodology - D+R – Severe Attacks: How long does it take to get permission to take any/all steps to protect the net/assets including shutting them down? _____ ¨ Add the best-case numbers: ______ s/m/h ¨ Add the worst-case numbers: _____ s/m/h ¨ Exposure Time (E) = ______ to _____ best case Copyright 2001 Marchany worst case 19

Measure Exposure Time - E ¨ Rule of Thumb: Bw/10/bits = Bw/bytes • Example: T-1: 1. 54 Mb/s -> 154 KB/s=9. 2 MB/m ¨ This gives: File Size/Bandwidth=Req. Attack Time or MB/Mb/S=(Attack Time) or F/Bw = T= E (Exposure Time) ¨ If the goal is file theft, the size of the target file F divided by the max. bandwidth of the network path Bw determines the amount of time T needed to get the info. Copyright 2001 Marchany 20

Measure Exposure Time - E ¨ This is 1 measure of risk. Info theft can be measured using T + intrinsic value of info. Remember Bw could be data transfer rates of floppy or tape drives. ¨ Example: A net has Exposure Time, E=(D+R) = 10 minutes and a tape drive with a xfer rate of 6 GB/hr. • T = 10 minutes = 1/6 hr, Bw = 6 GB/hr, F=Bw*T= 1 GB of data could be stolen before detection/reaction kills the attack. Copyright 2001 Marchany 21

Measure Exposure - External ¨ Bandwidth limiting is an effective response method. ¨ Data Padding: pad the critical files so their size exceeds E. Using the previous example: – E=10 min, Bw=6 Gb/hr. • File Size = (1/6 hr)/ (6 Gb/hr) = 1 GB=F • All critical files should be padded to 1 Gb. Copyright 2001 Marchany 22
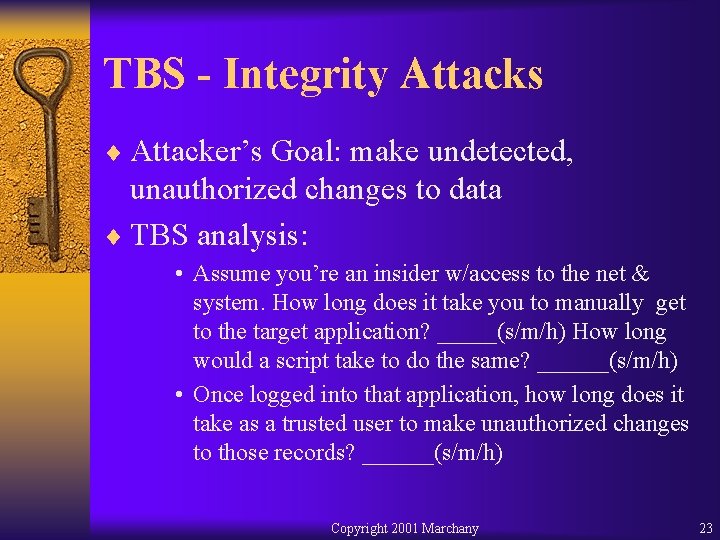
TBS - Integrity Attacks ¨ Attacker’s Goal: make undetected, unauthorized changes to data ¨ TBS analysis: • Assume you’re an insider w/access to the net & system. How long does it take you to manually get to the target application? _____(s/m/h) How long would a script take to do the same? ______(s/m/h) • Once logged into that application, how long does it take as a trusted user to make unauthorized changes to those records? ______(s/m/h) Copyright 2001 Marchany 23

TBS - Integrity Attacks (cont) • What steps would a knowledgeable user take to cover their tracks? How long does it take to effect those changes? _______ (s/m/h) • Add up the times for manual & automatic navigation. – This gives a target maximum value for E and provides a target guideline for D+R. Copyright 2001 Marchany 24

TBS - Measure the $ Damage ¨ Two Formulas: E=D+R, F/Bw=T • If we know E, we can get F if E=T. • If we know T, we can get E and D+R. ¨ Coordinate w/Auditors & Mgt. and ask: • If a critical file gets out, what would be the financial effect on the company? • Do. S attacks could cripple the company nets. What is the hourly/daily cost to the company if this happens? • What is our legal liability if client records or employee records are compromised? Copyright 2001 Marchany 25

TBS Asset Organization ¨ Information Value – Some info loses value over time. Example: advance notification, Product announcements – Some info’s value is still changing. Example: idea before its time. ¨ 4 Categories of Info Assets • Company Proprietary - product designs, pricing strategies, patents, source code, customer lists • Private Employee - HR records, perf reviews, SSN Copyright 2001 Marchany 26

TBS Information Assets ¨ Information Asset Categories (cont) • Customer Private - pricing info, purchase history, non-disclosure info • Partner/Gov’t - info assets that don’t fit into the other categories ¨ Risk Categories • Critical - if it gets out, we’re out of business • Essential - Survivable but a major hit. It’ll hurt but we can spin back to normal • Normal - may be embarrassing, disruptive only Copyright 2001 Marchany 27

TBS Info Asset Matrices ¨ Prepare matrices listing each asset and risk. ¨ Use the matrices to build an affordable, workable and maintainable security environment. ¨ Prepare separate matrices for criticality (like above), integrity and availability. Copyright 2001 Marchany 28

TBS Review Process ¨ Identify and categorize the Info assets ¨ Specify the logical locations of the assets ¨ Identify the physical locations of the assets ¨ The above info tells us: • If critical assets are all over the place then your defenses are spread out and cost more • If you have a single point of failure. • Negligible info is mixed in with Critical info. ¨ Some info has no place being on the net! Copyright 2001 Marchany 29
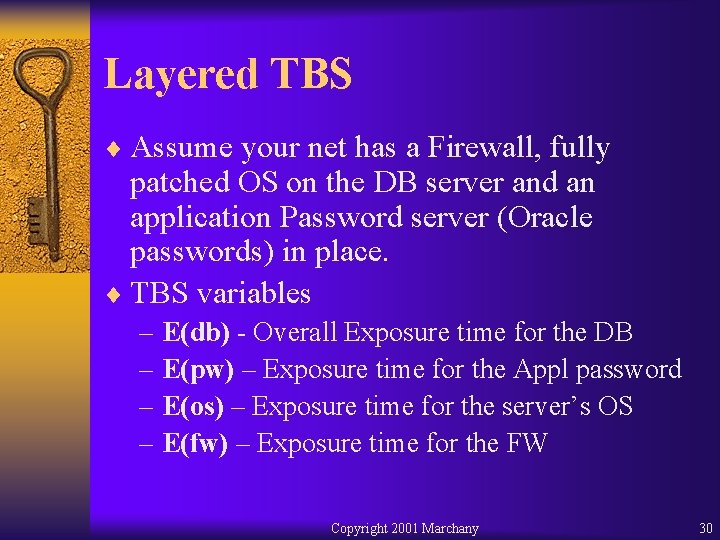
Layered TBS ¨ Assume your net has a Firewall, fully patched OS on the DB server and an application Password server (Oracle passwords) in place. ¨ TBS variables – E(db) - Overall Exposure time for the DB – E(pw) – Exposure time for the Appl password – E(os) – Exposure time for the server’s OS – E(fw) – Exposure time for the FW Copyright 2001 Marchany 30
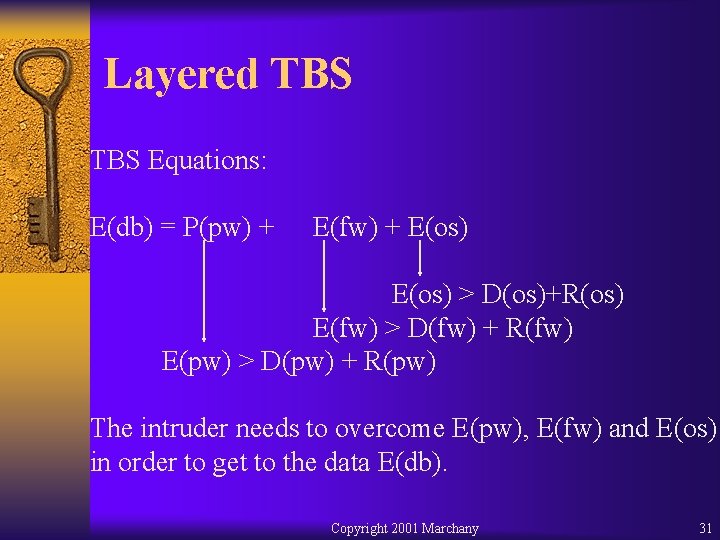
Layered TBS Equations: E(db) = P(pw) + E(fw) + E(os) > D(os)+R(os) E(fw) > D(fw) + R(fw) E(pw) > D(pw) + R(pw) The intruder needs to overcome E(pw), E(fw) and E(os) in order to get to the data E(db). Copyright 2001 Marchany 31

Layered TBS Conclusions ¨ All assets are NOT created equal and they do NOT deserve equal protection. ¨ Asset distribution by physical and logical separation is a security process but performed under the network architecture and topology banner ¨ Design the killing zones, in other words. Copyright 2001 Marchany 32
TBS Reaction Matrices ¨ Goal: make D+R as small as possible – A smaller R reduces the reliance on a higher P value. ¨ R Components – Notification - tells someone/something that a detection mechanism was triggered. Schwartau’s 3 am rule: “notify someone” means “tell someone other than the boss who doesn’t want to be bothered at 3 am” which increases the R time. ¨ Fill out the matrix with the target E, R or T times. – This documentation is important since it help mgt. understand the quantitative nature of TBS. ¨ The matrix is based upon AUP, disaster recovery plans, amount of risk the org is willing to take - measured in EXPOSURE TIME - T Copyright 2001 Marchany 33
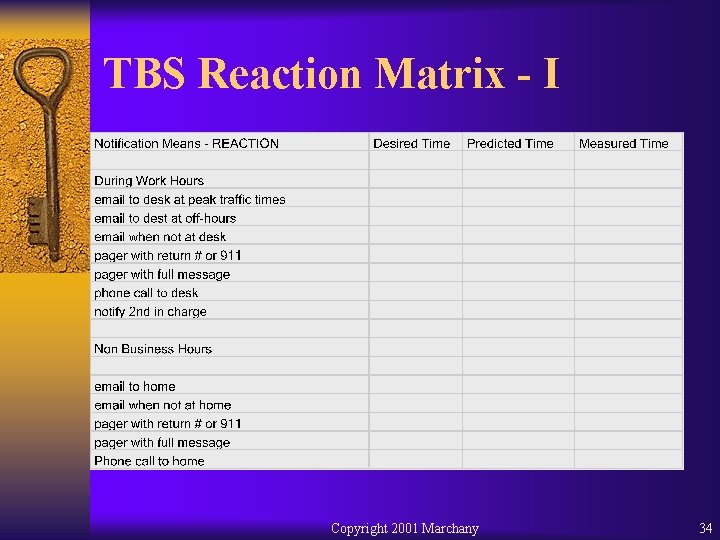
TBS Reaction Matrix - I Copyright 2001 Marchany 34

TBS Reaction Matrix - II The sysadmin represents the greatest room for error by making R unacceptably high. Why? People hesitate to make tough decisions like shut down part of a net. The “sacrifice the pawn to save the king” strategy can be very risky if you don’t have policies in place and MGT support. Automated responses can eliminate this BUT I saw “Colossus: The Forbin Project”…: -) Copyright 2001 Marchany 35

TBS Reaction Matrix ¨ Questions the Reaction Matrix should answer: • • • Is the attack real? What was the goal? Is it ongoing? Did the R-matrix come to the proper conclusion? Was the attack thwarted? Post-mortem analysis? What further steps are needed? Who did it? ¨ Must be empowered by mgt. and policy to limit R. Necessary for TBS to work. Copyright 2001 Marchany 36
TBS - Evaluating Protection ¨ Previous slides used TBS to evaluate D+R. ¨ Applying E=D+R to Access Control (User Logins) – E = max. amt. of time needed to accomplish proper authentication. – D = time needed to detect the authentication request and determine its authenticity. – R = time needed for the detection module to trigger a PROCEED or STOP reaction. ¨ Applying E=D+R to Enterprise Audit Trails – D = time needed for an audit tool to record, analyze, transmit data. – R = time it takes for the detection tool to trigger the reaction and how long the reaction takes. Copyright 2001 Marchany 37

Course Revision History Copyright 2001 Marchany 38
- Slides: 38